First published on CloudBlogs on Jan 10, 2018
At Microsoft Ignite 2017, we shared the upcoming new integration between Azure Information Protection and Microsoft Cloud App Security for providing enhanced data protection in the cloud apps and we received very positive feedback from our customers and partners regarding this key capability. Today, we are excited to announce this new feature is now in
public preview.
Microsoft Cloud App Security and Azure Information Protection integration
With the rising number of cybersecurity attacks and key regulations on privacy, controlling and protecting sensitive data – at all times – is top of mind.
Azure Information Protection
provides persistent data protection by identifying sensitive data, classifying, labeling and protecting at the time of creation or modification based on source, context and content.
With growing number of cloud apps used in your environment, you may have personal data stored and processed in cloud apps. In order to have a holistic information protection strategy, it is important to take into consideration all the different locations the data travels. To that extent, at Ignite 2016, we announced the
first level of the integration
between Microsoft Cloud App Security and Azure Information Protection where we extended the visibility into sensitive data as it moved to cloud apps. With this integration, Cloud App Security admins gained the control to configure policies to read Azure Information Protection labels and take appropriate actions or raise alerts.
Now, we are taking these capabilities to the next level by providing the capability of scanning cloud apps for sensitive data and automatically applying
Azure Information Protection labels
through policies – including encryption and rights management capabilities such as block forwarding, printing, copying etc.
How to create a policy for automatically detecting, classifying and protecting data in cloud apps
We will get started by setting a policy for automatic detection, classification and protection of sensitive data in the cloud apps. For this example, we will create a policy that searches for credit card numbers in files stored in Box. When such a file is detected, the policy will automatically apply an Azure Information Protection label.
Steps
1. On the
Control tab
, click
Policies.
2. Click
Create policy
and select
File policy
.

Figure 1. Create a file policy
3. Call the policy
Box data protection
4. Select
Policy Severity
.
5. Under
Create a filter for the files this policy will act on
, select
App
equals Box.
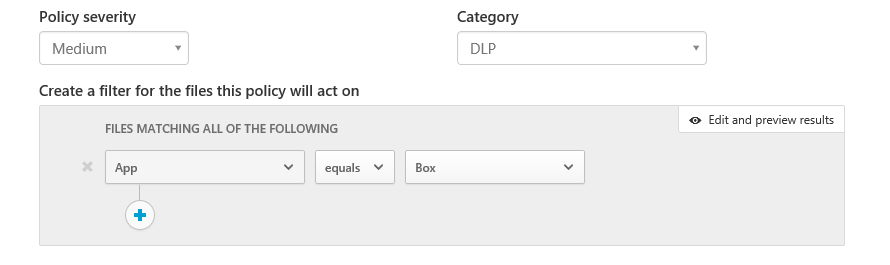
Figure 2. Policy filters
6. Within that app, look for files that contain Credit Card information as follows: Under
Content inspection method
select
Built-in DLP
and then select
Include files that match a preset expression and select All countries:Finance:Credit card number.

Figure 3. Policy – content inspection rules
Under
Governance,
open the
Box
section and select
Apply classification label
. Select the label you wish to apply. Through
the integration between Cloud App Security and Azure Information Protection
, you can select from your existing list of classification labels. If you haven’t created Azure Information Protection labels yet,
click here to learn more here
.

Figure 4. Policy governance action
7. Click
Create
.
And that is it! All documents that are scanned and found to include credit card data will have the specified classification label applied, and now are protected.
How to detect files with classifications labels
If you would like to detect all files in your cloud apps using a specific classification label, follow these steps:
On the
Investigate
tab click
Files
.
Click
Advanced
.
Select
Classification label
, and choose the specific label you’d like to use for this investigation.

Figure 5. Investigate by file type
You will see that all files with that label will show up instantly.
Learn more
If you have Cloud App Security deployed, you will see these preview features already enabled in your tenant. If not, you can
try Cloud App Security for 90-days
with no additional cost and see how this service helps you with providing visibility, data control and threat protection to your cloud apps.
Our goal in the Cloud App Security engineering team is to continuously innovate to provide a top-notch user experience, visibility, data control and threat protection to your cloud apps.
If you would like to learn more, visit Microsoft Cloud App Security
technical documentation page
and
Azure Information Protection Quick start tutorial
.
We love hearing your feedback. Get started with Cloud App Security today, give these new features a try and let us know what you think at
Microsoft Cloud App Security Tech Community
.
