Effectively identifying, assessing, and remediating endpoint weaknesses is pivotal in running a healthy security program and reducing organizational risk. Today, we are happy to introduce Microsoft Intune security tasks, a new one-click remediation capability in Microsoft 365 that bridges security stakeholders—security administrators, security operations, and IT administrators—by allowing them to collaborate and seamlessly remediate threats. This capability will extend the newly announced Microsoft Defender Threat & Vulnerability Management (TVM), a new component of Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP, previously Windows Defender ATP) that uses a risk-based approach to the discovery, prioritization, and remediation of endpoint vulnerabilities and misconfigurations.
Rapid response to detect and remediate security incidents among billions of events is essential for IT security because adversaries present a danger every minute they are in your environment. Communication cycles and distribution of tasks between Security Operations, Security Admins and IT Admins often allow security breaches to spread over time or even linger unattended. Microsoft Defender ATP and Microsoft Intune create a task pipeline to eliminate lengthy delays between security-driven threat detection and IT-driven threat remediation. The status of the remediation task is synchronized back to the Microsoft Defender ATP console to keep Security Operations or Security Admins updated on the progress.
Some examples of security tasks to remediate your security posture would be to update a vulnerable app, uninstalling a vulnerable app, updating an OS, or changing a device configuration. Let us walk through one such security task, as an example.
How to update a vulnerable app with Microsoft Intune
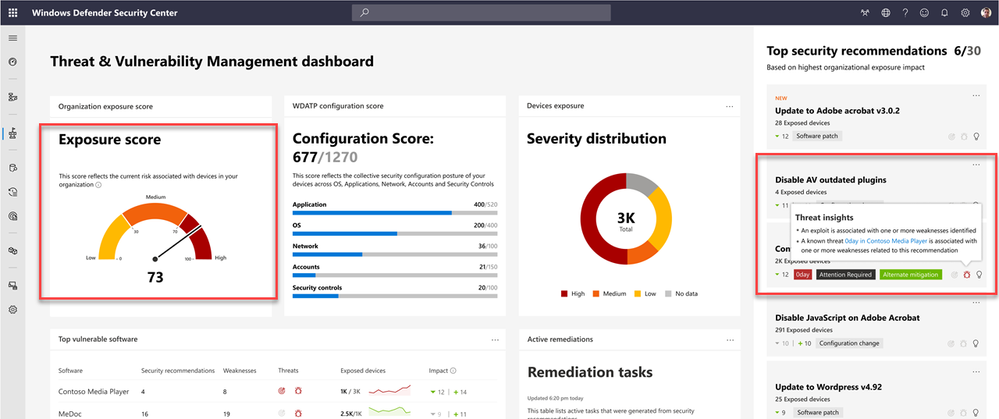
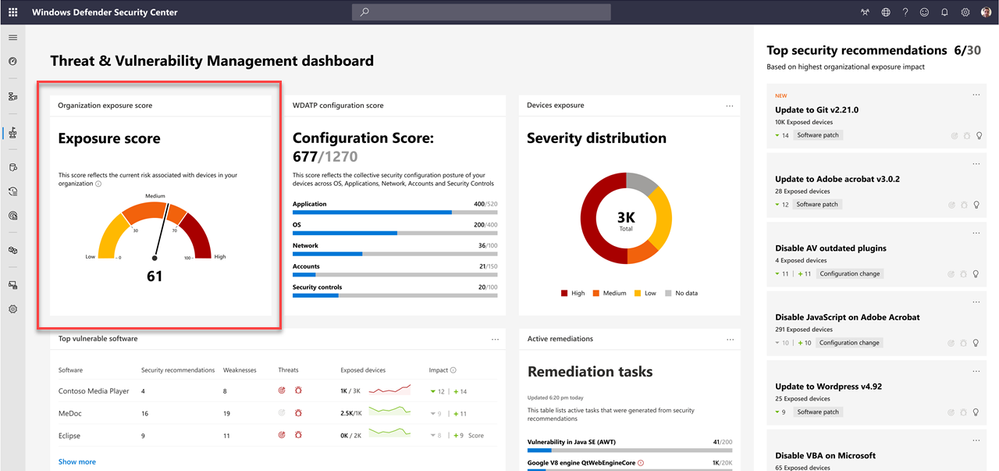
In this example, we will use Microsoft Intune for remediation when Microsoft Defender ATP detects a vulnerable app and recommends an update to a new version. Note the risk exposure score is high according to the dashboard.
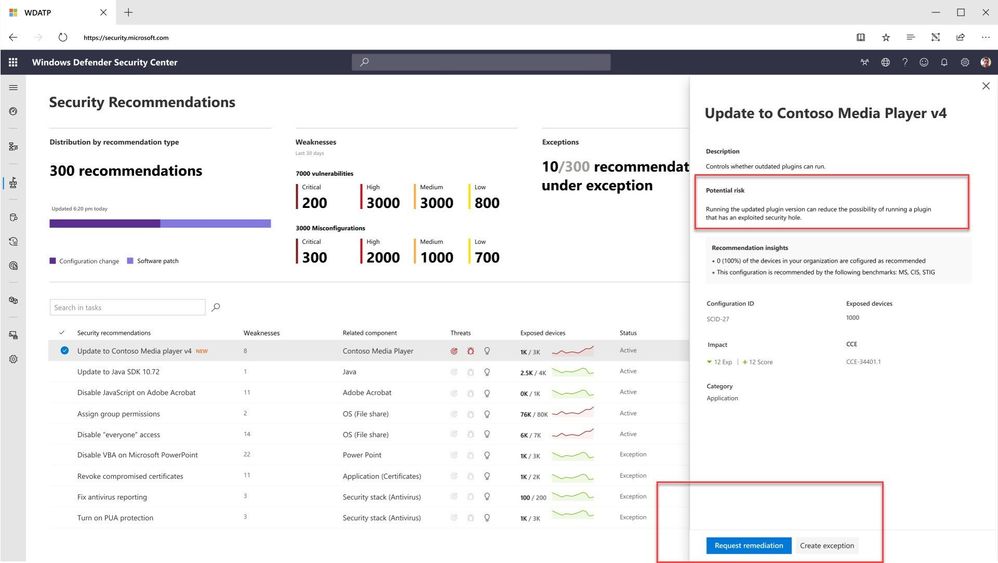
The Security Admin acts upon this recommendation by putting in a request to their IT department to remediate the vulnerable app.
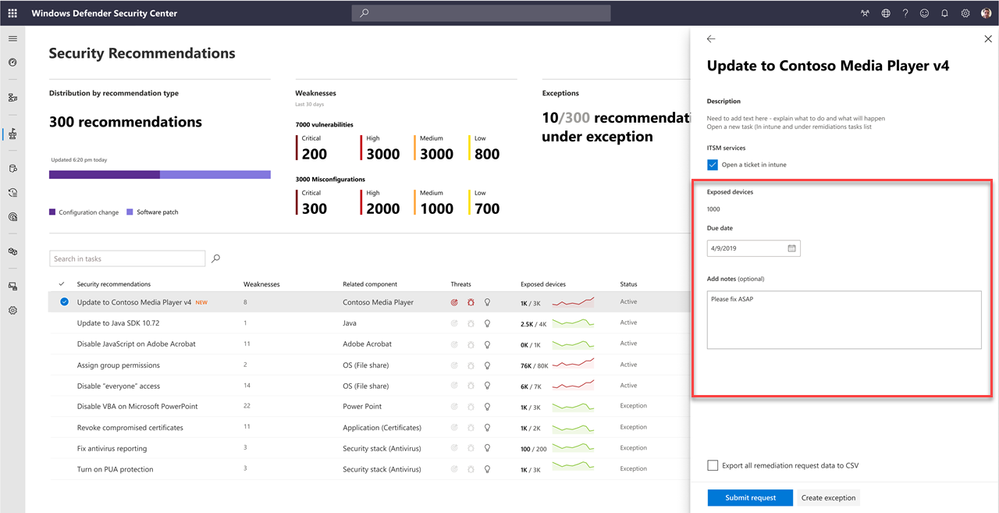
They may add a due date to complete the security task and add notes, before passing this information to the IT admin in Microsoft Intune
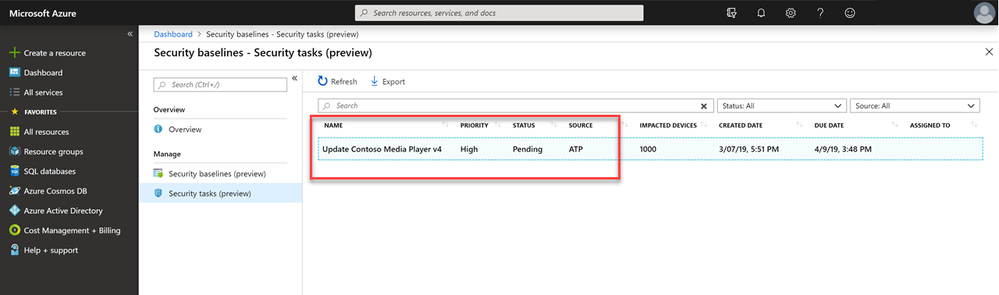
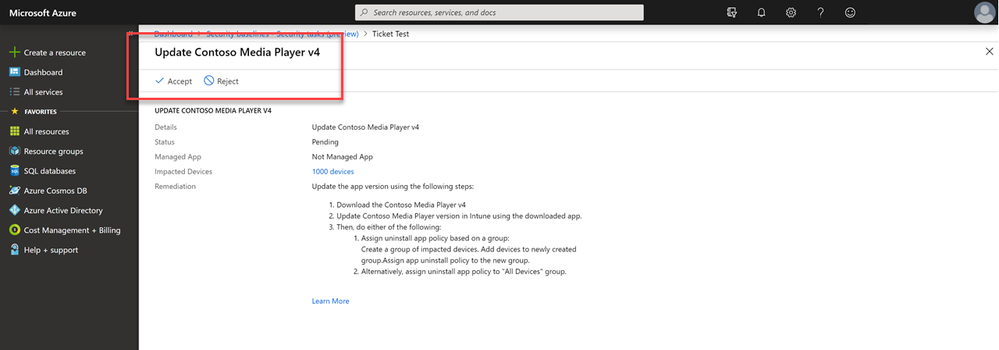
Over in the Microsoft Intune console, the IT admin can see all requests from the security department in the new Security tasks node, with a ‘pending’ status, due date, and number of impacted devices.
From here, the IT admin can Accept or Reject the task. To help facilitate this decision, Microsoft Defender ATP provides insights into the security recommendation. Microsoft Intune security tasks can identify and remediate vulnerable apps on devices managed by both Intune and Configuration Manager.
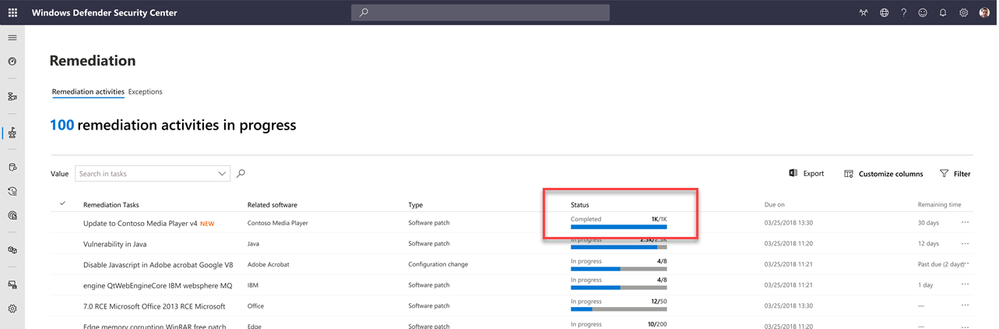
The IT admin can directly open the vulnerable app from the task and take care of the update. Once complete, they can close the task and the threat is mitigated.
When this vulnerability is remediated, the risk exposure score drops to medium on the dashboard.
As the security stakeholders work together to complete the remaining security tasks, it continues to harden the organization’s security posture.
Preview available soon
Security tasks are simply the latest innovation in strengthening the existing integration between Microsoft Intune, Azure Active Directory and Microsoft Defender ATP. Together, the Microsoft 365 security management platform continues to evolve to help organizations easily block attackers from spreading if any machine is compromised. This integration has already proven successful in detecting and remediating new cyber-attacks using device risk score to drive conditional access. The new capabilities will be available for preview within the next month.
Learn how to get started with Microsoft Intune with our detailed technical documentation. Don’t have Microsoft Intune? Start a free trial or buy a subscription today!
Follow @MSIntune on Twitter
(This post is co-authored by Joey Glocke, Senior Program Manager, Microsoft Intune and Mayunk Jain, Product Manager, Microsoft 365 Security)