This post has been republished via RSS; it originally appeared at: Intune Customer Success articles.
Hi everyone, today we have another post from Intune Support Engineer and resident Jamf expert Shonda Hodge. Shonda already published detailed steps on getting Jamf integration configured here, and today she follows that up with an article on how to troubleshoot integration if you encounter any issues. Special thanks to Bryce Carlson (Sr. Support Engineer @Jamf), Camden Webster (Sr. Support Engineer @Jamf), Lucas Lenard (Support Engineer I @Jamf) and Geoff Root (Test Engineer I @Jamf) who worked closely with Shonda to get this article created.
=====
If your organization uses Jamf Pro to manage macOS devices, you can use Microsoft Intune compliance policies with Azure Active Directory conditional access to ensure that devices in your organization are compliant before accessing company resources. Jamf does this by allowing admins to sync their Mac inventory data with Intune and the Microsoft Cloud. This inventory data can then be analyzed by Intune’s compliance engine to generate a report, then combined with intelligence about the user’s identity, enforce conditional access via EMS. If the Mac device is compliant with the conditional access policies configured, it will be allowed access to the protected company resources.
Device registration explained
Device registration is the process in which a device’s identity is established in AAD. It uses the public-private key infrastructure, and on the device/client side it’s referred to as workplace joined (WPJ)/domain-joined (DJ)/Azure AD-joined (AADJ) whereas on the server side it is referred to as Azure Device Registration Service (ADRS or simply DRS). This device identity is needed for Intune registration.
Notes on MacOS authentication and registration
- The WPJ state is stored in Login keychain.
- Login keychain access is needed to complete device authentication on MacOS.
- Login keychain typically has the same password as the MacOS sign-in password, however it could also have a different password.
- The Intune Company Portal app is required to do device registration, which occurs during JamF
- There is no broker on MacOS. All client apps using ADAL (Azure Active Directory Authentication Library) can do device AuthN, but users will see KeyChainaccess password prompts.
NOTE: AuthN primarily deals with user identity: who is this person? Is she who she says she is?
Troubleshooting Intune Registration for Jamf-managed devices
It’s important to note that the Intune Company Portal app must be launched from the Jamf Self Service app; if not the device will not be properly registered. When troubleshooting registration issues, start by gathering the following information:
- Azure AD Device ID
- Company Portal logs (instructions are here)
- The sysdiagnose log archive from macOS (will contain jamfAAD process logs). To generate a sysdiagnose, run the following command from the enrolled Mac device with your desired save location (e.g. /Desktop for the logged in users’ desktop):
sudo sysdiagnose -f /path/to/desired/save/location
- To view just jamfAAD logs on a Mac for quick troubleshooting, run this command on the Mac to get the last 30 minutes of data:
log show --predicate 'subsystem CONTAINS "jamfAAD"' --last 30m
Here’s an example of a Company Portal log showing successful Intune registration:
2019-01-23 17:32:15.119 INFO com.microsoft.ssp.workplaceJoinSdk TID=27 WorkplaceJoinManager.swift: 796 (workplaceClient(_:logMessage:)) INFO: -[WorkPlaceJoin saveWorkplaceJoinStateToDevice:certificatePerferredPaths:correlationId:error:] [Line 1519][2019-01-23 17:32:15 +0000]Successfully completed device registration
2019-01-23 17:32:15.120 INFO com.microsoft.ssp.workplaceJoin TID=27 WorkplaceJoinManager.swift: 475 (didCompleteJoin()) In-app workplace join succeeded.
2019-01-23 17:32:15.159 INFO com.microsoft.ssp.enrollment TID=1 EnrollmentInProgressPaneViewController.swift: 111 (handleEnrollmentStateChange()) WPJ only enrollment complete, go to checklist page
"[\"ChassisType\": \"Desktop\", \"IsExchangeActivated\": \"0\", \"PartnerLocalizedSelfServicePortalName\": \"SelfService\", \"odata.editLink\": \"https://fef.msua06.manage.microsoft.com/StatelessIWService/Devices(guid'8253763b-8b89-4240-bebe-ef60cccf6e8b')\", \"ExchangeActivationItemEasId\": \"\", \"PartnerName\": \"Jamf\", \"ManagementAgent\": \"JamfClient\", \"LastContact\": \"2019-01-23T17:28:28\", \"Manufacturer\": \"Apple\", \"Nickname\": \"Rechelle\U2019s MacBook Air\", \"OwnerType\": \"0\", \"ApplicationState\": \"https://fef.msua06.manage.microsoft.com/StatelessIWService/Devices(guid'xxxxxxxx-8b89-4240-bebe-ef60cccf6e8b')/ApplicationState\", \"SetHeartBeat\": \"[\"target\": \"https://fef.msua06.manage.microsoft.com/StatelessIWService/Devices(guid'xxxxxxxx-8b89-4240-bebe-ef60cccf6e8b')/SetHeartBeat\"]\", \"Key\": \"xxxxxxxx-8b89-4240-bebe-ef60cccf6e8b\", \"SetRD\": \"[\"target\": \"https://fef.msua06.manage.microsoft.com/StatelessIWService/Devices(guid'xxxxxxxx-8b89-4240-bebe-ef60cccf6e8b')/SetRD\"]\", \"ComplianceState\": \"Compliant\", \"CategorySetByEndUser\": \"0\", \"Model\": \"MacBook Air (13-inch Early 2015)\", \"LastContactNotification\": \"0001-01-01T00:00:00\", \"PartnerSelfServicePortalUrl\": \"jamfselfservice://\", \"CategoryId\": \"[null]\", \"SetOptIn\": \"[\"target\": \"https://fef.msua06.manage.microsoft.com/StatelessIWService/Devices(guid'xxxxxxxx-8b89-4240-bebe-ef60cccf6e8b')/SetOptIn\"]\", \"DeviceHWId\": \"10:94:BB:C7:3E:70\", \"AadId\": \"xxxxxxxx-8b89-4240-bebe-ef60cccf6e8b\", \"GetManagementState\": \"[\"target\": \"https://fef.msua06.manage.microsoft.com/StatelessIWService/Devices(guid'xxxxxxxx-8b89-4240-bebe-ef60cccf6e8b')/GetManagementState\"]\", \"AppWrapperCertSN\": \"[null]\", \"CreatedDate\": \"2019-01-23T17:37:03.9872113\", \"PartnerRemediationUrl\": \"jamfselfservice://remediate\", \"RemoteSessionUri\": \"[null]\", \"ManagementType\": \"JamfClient\", \"odata.readLink\": \"https://fef.msua06.manage.microsoft.com/StatelessIWService/Devices(guid'8253763b-8b89-4240-bebe-ef60cccf6e8b')\", \"IsPartnerManaged\": \"1\", \"OfficialName\": \"Rechelle\U2019s MacBook Air\", \"NoncompliantRules\": \"[]\", \"OperatingSystem\": \"Mac OS X\"]"
Tips for troubleshooting registration
- Ensure that the Company Portal app is being launched from the Jamf Self-Service app. If the Company Portal upgrade dialog box pops up, finish the upgrade and quit the app, then re-launch the Company Portal app from JSS.
- Check Enterprise Applications permissions for Jamf in Azure AD. Ensure that only the single permission is listed.
- Check to make sure that the Jamf MacOS connector is listed under Enterprise Applications in Azure AD. If not, log in to the Jamf console and complete the administrator consent.
- For Macs previously enrolled into Intune, if you want to have them managed by Jamf complete the following:
- Unenroll from Intune.
- Clean up the device from the Azure portal by ensuring that the device is no longer listed under “All Devices” and “Azure AD Devices”.
- Clean up the Mac by removing all workplace join-related certificates from the Key Chain before switching device management providers.
- For Macs previously managed by Jamf and registered with Intune, it is recommended that you clean up the device by following steps documented here: https://www.jamf.com/jamf-nation/articles/153/removing-jamf-components-from-computers. Be sure to confirm that the device is no longer seen in the Azure portal before enrolling back into the Jamf Pro server and attempting Intune registration again.
- If a Mac device shows Not registered in the Company Portal app, uninstall and register the device by allowing Jamf to launch the Company Portal app via policy or Self Service policy. In this case you will also see the following in the Company Portal log:
INFO com.microsoft.ssp.application TID=1 WelcomeViewController.swift: 253 (startLogin()) Portal launched without WPJ only arg while account is under partner management
How compliance is evaluated
Jamf Pro sends the inventory attributes listed below to Intune for the purposes of compliance evaluation. Be aware that there are more attributes that Jamf Pro sends, however for the purposes of this guide we’ve only listed those that are used to evaluate compliance. For a complete list of attributes that Jamf Pro sends to Intune, see Jamf Inventory information.
- Jamf Inventory State
- OS Version
- User AAD ID
- # of previous password to prevent reuse
- Encrypted (File Vault 2)
- Minimum # of character sets
- Password expiration (days)
- Password Type
- Prevent Auto Login
- Required Passcode Length
- Start screensaver after inactivity
- System Integrity Protection
NOTE: If Mac computers have network accounts (or Mobile Home Folder AD accounts), compliance policies dealing with password complexity should not be used within Microsoft Intune as they cannot be reported correctly from Jamf Pro. Password complexity is enforced by the network account server.
Jamf Pro enforces compliance via the configuration profiles scoped to the macOS device and reports to Intune if the computer is managed based on the local attributes of the device at the time check-in. Intune’s compliance engine evaluates inventory data from JamfPro and generates a report and enforces conditional access via Azure AD.
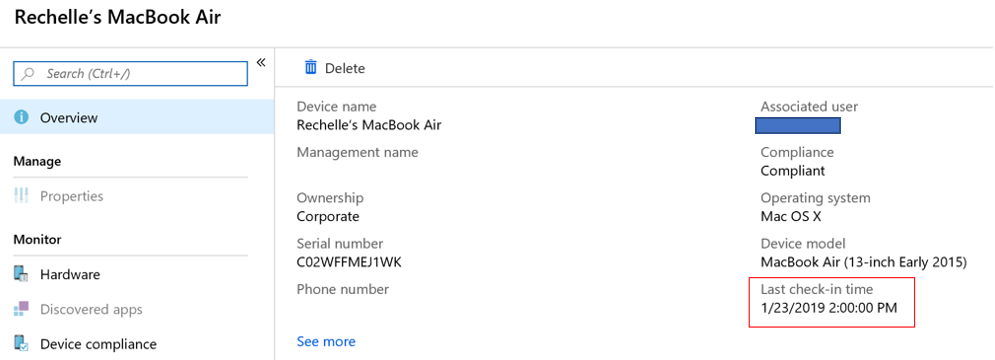
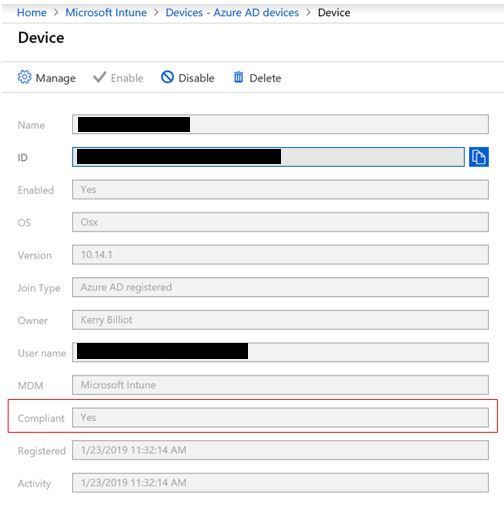
Fields in Azure that displays compliance information
In Azure -> Microsoft Intune – All Devices, you will see the last check-in time. Be aware that current last check-in time is the time Intune received related device inventory data time, not actual MacOS check-in time to Jamf. This corresponds to what’s in the Company Portal app.
Under Azure AD devices, the Compliant field is used to determine whether access to resources will be granted. If the compliant state is No, users will be blocked from protected company resources.
NOTE: In Azure -> Microsoft Intune -> Azure AD devices, the Activity field for a device does not have significance for Jamf/Intune compliance evaluation.
Device check-in and compliance
By default, devices check-in with Jamf Pro every 15 minutes. This is configurable in the Jamf Pro console and you can read more on that here. If a device doesn’t check-in within a 24-hour period, Jamf will mark the device as unresponsive. If a device is marked unresponsive, Jamf will send that status to Intune and the device will be marked as non-compliant once Intune gets that data. Every registered device also has an Azure token. This token is refreshed every 12 hours, and if the token is not able to be refreshed for 24 hours or more, Jamf will mark the device as unresponsive and send that status to Intune.
NOTE: Enrolled users must log on to correct a non-responsive state. It must be the user who has work-placed joined the account as this is the user that has the identity from Intune in their login keychain.
Best practices for compliance
- To keep Mac computers in compliance, it is recommended that you deploy a configuration profile or a policy in Jamf Pro for each compliance policy created in Microsoft Intune.
- Ensure that the Intune compliance policy aligns with the inventory policy in Jamf.
- On the Jamf side, the admin should add an Inventory policy that end users can use in Self-Service to trigger Jamf Pro to send updated information to Intune on the fly.
- Check if the device shows up in Intune, or when the last check-in time was updated. If hasn’t checked in for a long time, check the last device inventory update on the Jamf Pro side and ensure that the data has been sent to Intune. You can read more on this at the bottom of the following page: http://docs.jamf.com/jamf-pro/administrator-guide/Viewing_the_History_for_a_Computer.html.
Tips to bring devices back into compliance
- If it has been over 24 hours since the user has logged into the Mac, simply have them log in. You can also run the following command on the Mac device with the registered user session present:
/usr/local/jamf/bin/jamfAAD gatherAADInfo
- Ensure that the device meets the criteria set in the compliance policy (e.g. password requirements/encryption required). If a device is out of compliance due to encryption requirements, the Company Portal log will contain the following message:
"CreatedDate": "xxxx-xx-xxxx:42:09.7465954", "PartnerRemediationUrl": "jamfselfservice://remediate", "RemoteSessionUri": "[[mobile]]", "ManagementType": "JamfClient", "odata.readLink": "https://fef.msua05.manage.microsoft.com/StatelessIWService/Devices(guid'xxxx')", "IsPartnerManaged": "1", "UserApprovedEnrollment": "0", "OfficialName": "[[OfficialName]]", "NoncompliantRules": "[[SettingID": "Device_Encryption_FileVault2Encrypted", "ExpectedValue": "True", "Title": "Turn on device encryption", "MoreInfoUri": "https://go.microsoft.com/fwlink/?linkid=851949", "Description": "You must enable full-disk encryption for this device, which wraps your information in a layer of protective code to keep unauthorized people from accessing it. We recommend you contact your company support to enable it.", "RemediationOwner": " user"]"]", "OperatingSystem": "Mac OS X", "RegisterForAppPushNotifications": "["target": "https://fef.msua05.manage.microsoft.com/StatelessIWService/Devices(guid'xxx')/RegisterForAppPushNotifications"
FAQ
Under Azure AD Devices the Mac shows Non-compliant, but under All Devices it shows to be compliant. Which one is accurate?
- The status displayed under Azure AD Devices will be used for determining access to protected company resources.
My Macs have a password set and my compliance policy requires a passcode, but my devices are still not compliant?
- Do you have auto-login set on the Mac (more on that here: https://support.apple.com/en-us/HT201476 )? If so that may be why as the Mac is not actually secure in spite of having a password set.
Why do I see the device in the Azure AD blade but not in Intune?
- If the device shows up in the Azure AD blade and not Intune, that means Jamf probably didn’t get the AAD Device ID. You should see the AAD device ID in the Jamf Pro console. If you do not, that likely means that the Jamf AAD app wasn’t successfully run (or didn’t complete successfully) so the user should run the device registration policy from Jamf Self Service again.
If I have a blank compliance policy assigned to my Mac devices, how does Intune evaluate compliance?
- Blank compliance policy (a policy that has no setting) is not being calculated as of now. The device will remain as Unknown.
If a device has not communicated Jamf in over 24 hours, how do I bring it back into compliance?
- Log into the Mac as the user who registered with Intune. The user’s login keychain contains the identity needed to confirm compliance. You can also trigger the following command from the Mac device with the registered user session present to expedite that process:
/usr/local/jamf/bin/jamfAAD gatherAADInfo
How long does a device have to remain in an unresponsive state before Jamf codes it as Unmanaged?
- A device that remains in an unresponsive state for over 30 days will be marked as unmanaged by Jamf.
Can you force device check-in from Intune? If so, how do you do it?
- Currently this is not possible as Jamf is responsible for providing the state of the device. Users should use the Self- Service app for device check-in via an Inventory policy for immediate results.
What ports need to be open for Jamf and Intune to work properly?
- Intune: Port 443
- Apple: Ports 2195/2196/5223 (for Push notifications to Intune)
- Jamf: Port 80, 5223
NOTE: Be sure to allow outbound connections to, and redirects from, Apple’s 17.0.0.0/8 block over TCP port 5223 / 443 from all client networks, and on ports 2195 and 2196 from Jamf Pro servers to make sure APNS will function correctly on your network.
Intune reference: https://docs.microsoft.com/en-us/intune/network-bandwidth-use
Jamf reference: https://www.jamf.com/jamf-nation/articles/34/network-ports-used-by-jamf-pro
What causes an Azure AD ID to be reflected as “Deactivated” in Jamf?
- Typically you will see this after 30 days of inactivity.
If I have an on-premise instance of Jamf and I want to add a cloud instance of Jamf, can I have both linked to Azure at the same time?
- No. Intune only supports one Jamf connector per tenant in Azure.
If I encounter an issue with my Jamf-managed device registered with Intune and I need assistance, what should I do?
- If you encounter issues with the integration of Jamf and Intune, please open a ticket with Jamf first. They will advise whether a case needs to be opened with Microsoft. If a case needs to be open with Microsoft, please have the following information available:
-
The UPN of the affected user(s)
-
The AAD Device ID
-
Company Portal logs
-
Screenshots of compliance/conditional access policies from Intune and screenshots of Jamf configuration profiles (compliance settings specifically)
-
Known issues/solutions
When configuring Jamf with Intune, the following error message appears when trying to confirm settings from the Jamf console:
Graph API Access Token cannot be retrieved
This typically occurs is there is a proxy or firewall blocking required ports. Check the ports listed above.
When configuring Jamf with Intune, the following error message appears:
Graph API Access Token cannot be retrieved
The Jamf Pro Server log also contains a 401 error when the connection to Graph is attempted:
[ConditionalAccessHTMLResponse] - Could not enable provisioning
com.jamfsoftware.conditionalaccess.provisioning.InvalidResponseStatusException: Status code 401
This can occur if you did not input your App ID correctly on the Device compliance - Partner device management page. Input and save the correct App ID to resolve this issue.
When trying to register a Jamf enrolled device with Intune, the following message is seen after signing into the Company Portal app:
Invalid command line input. Registration-only command line flag (-r) can only be used when partner management is enabled in Intune. Please contact your IT admin.
This will occur if Intune integration is turned off. The Jamf Pro server sends a pulse to the Intune servers when this is unchecked, telling Intune that the integration is disabled. To resolve this issue, re-enable Intune integration in Jamf Pro
When trying to register a Jamf enrolled device with Intune via Jamf Self Service, the Company Portal does not launch and the following error is generated:
The operation couldn’t be completed. (Com.jamfsoftware.task.errors 1.) [com.jamfsoftware.task.errors code=1}
This occurs if the user shell for your macOS user account is not set to a working directory such as /bin/bash. Set the user shell for your user account to a working directory to resolve the issue.
Shonda Hodge
Intune Support Engineer
Microsoft