This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
Proxy server identification and registration in Surface Hub
With the Windows 10 May 28, 2019 update (KB4499162), Surface Hubs now have improved logic, and the ability to save the FQDNs of proxy servers that are discovered as part of the regularly occurring network ping.
Over the course of regular cleanups, Surface Hub will eventually store every single proxy server in the organization.
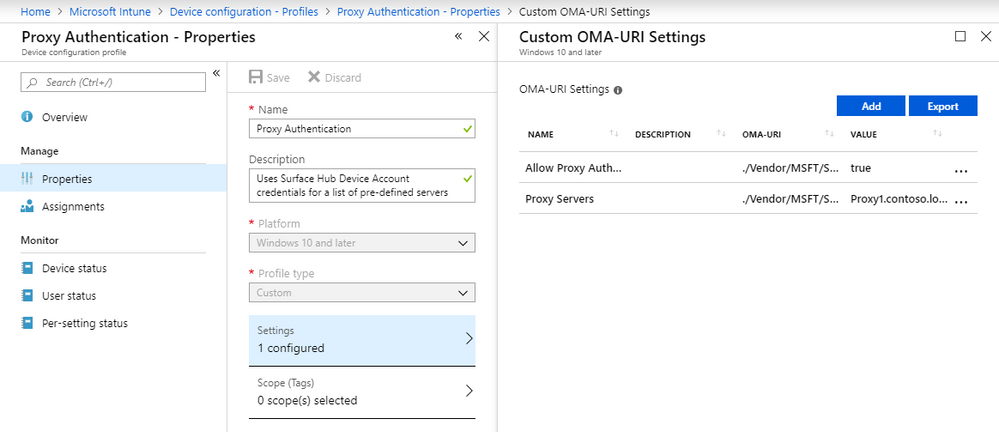
Surface Hub proxy list via Intune
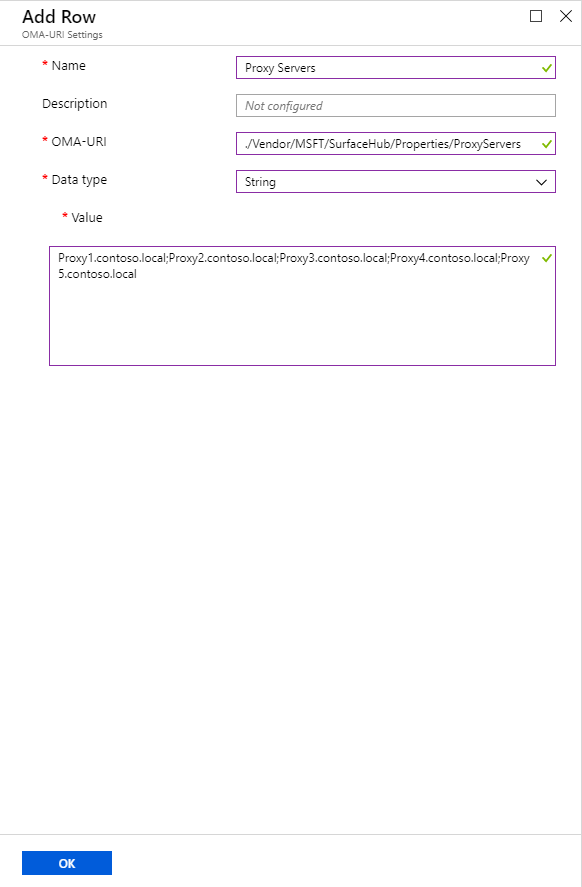
./Vendor/MSFT/SurfaceHub/Properties/ProxyServersProxySRV1.corp.contoso.local, ProxySRV1)And should not include additional prefixes (
https://ProxySRV1, http://ProxySrv2, etc.)Proxy1.contoso.local;Proxy2.contoso.local;Proxy3.contoso.local;Proxy4.contoso.local
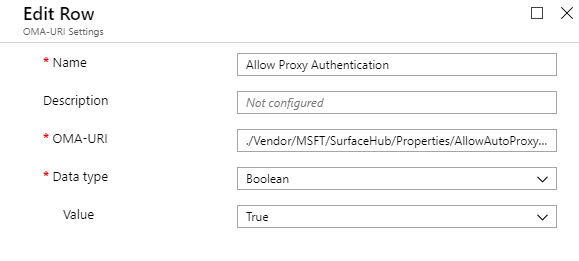
Preferably, The Intune Device Configuration Profile should also contain the ./Vendor/MSFT/SurfaceHub/Properties/AllowAutoProxyAuth OMA-URI to ensure the Device Account credentials are being used: