This post has been republished via RSS; it originally appeared at: Intune Customer Success articles.
Hello everyone, today we have a great article from Intune Support Engineer Mohammed Abudayyeh. In this article, Mohammed walks through the process of ingesting Office ADMX files and creating ADMX-backed policies for Win32 and Desktop Bridge apps using Windows 10 MDM.
Please note that we recently released ADMX-backed administrative templates in public preview for Intune. The preview allows a templated access of select Group Policy administrative templates (ADMX-backed policies) for Windows PCs via the Policy configuration service provider (CSP). If the policy you're wanting to implement is available in these administrative templates then that would be the recommended method to use vs ADMX ingestion as discussed here. You can read more about this here: https://docs.microsoft.com/intune/administrative-templates-windows.
As always, if you have any feedback please leave us a comment below.
=====
Introduction
Starting with Windows 10 version 1703, we can now import ADMX files (aka ADMX ingestion) and set ADMX-backed policies for Win32 and Desktop Bridge apps using Windows 10 Mobile Device Management (MDM). In this scenario, the ADMX files that define the policy information are delivered to your devices using the Policy CSP URI ./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall and then the ingested ADMX files are processed into MDM policies. This post covers the following topics:
- The Registry keys used
- The steps to ingest ADMX files
- Reviewing the settings after deployment
- An example using PowerPoint
Registry Keys
When the ADMX policies are imported, the registry keys to which each policy is written are checked so that known system registry keys, or registry keys that are used by existing inbox policies or system components, are not overwritten. This precaution helps to avoid security concerns over opening the entire registry. Currently, the ingested policies are not allowed to write to locations within the System, Software\Microsoft, and Software\Policies\Microsoft keys, except for the following locations:
- Software\Policies\Microsoft\Office\
- Software\Microsoft\Office\
- Software\Microsoft\Windows\CurrentVersion\Explorer\
- Software\Microsoft\Internet Explorer\
- software\policies\microsoft\shared tools\proofing tools\
- software\policies\microsoft\imejp\
- software\policies\microsoft\ime\shared\
- software\policies\microsoft\shared tools\graphics filters\
- software\policies\microsoft\windows\currentversion\explorer\
- software\policies\microsoft\softwareprotectionplatform\
- software\policies\microsoft\officesoftwareprotectionplatform\
- software\policies\microsoft\windows\windows search\preferences\
- software\policies\microsoft\exchange\
- software\microsoft\shared tools\proofing tools\
- software\microsoft\shared tools\graphics filters\
- software\microsoft\windows\windows search\preferences\
- software\microsoft\exchange\
- software\policies\microsoft\vba\security\
- software\microsoft\onedrive
Steps to ingest ADMX files
Step 1 - Download the ADMX files
The first thing we need to do is download the ADMX files for Office 16 to your computer. They can be found at https://www.microsoft.com/en-us/download/details.aspx?id=49030. You will notice that each product under Microsoft office has its own ADMX-Backed Policies.
Step 2 - Create the OMA-URI custom policy
Now we need to deliver these ADMX policies to the computers you want to manage:
1. In the Azure portal, select All services, filter on Intune, then select Microsoft Intune.
2. Select Device configuration -> Profiles -> Create profile.
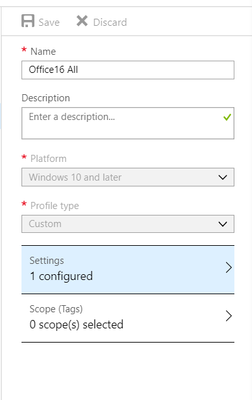
3. Enter the following settings:
- Name: Enter a name for the profile, such as Office 16 custom profile.
- Description: Enter a description for the profile.
- Platform: Choose Windows 10 and later.
- Profile type: Choose Custom.
4. Under Custom OMA-URI Settings click Add and enter the following settings:
- Name: Enter a unique name for the OMA-URI setting to help you identify it in the list of settings.
- Description: Enter a description that gives an overview of the setting, and any other important details.
- OMA-URI (this is case sensitive): Enter the OMA-URI you want to use as a setting ./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/Office16/Policy/Office16Policy
- Data type: Choose the data type you'll use for this OMA-URI setting. Select String.
- Value: Enter the data value you want to associate with the OMA-URI you entered. In our case we will put the content of Office16 ADMX file into the Value field.
The table below shows the OMA-URI, Data Type and Value for the rest of the Office apps.
| Office Application | OMA-URI | Data Type | Value |
| Microsoft Access 2016 | ./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/Office16/Policy/Access16 | String | The content inside access16.admx |
| Microsoft Excel 2016 | ./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/Office16/Policy/Excel16 | String | The content inside excel16.admx |
| Microsoft Lync 2016 | ./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/Office16/Policy/lync16 | String | The content inside lync16.admx |
| Microsoft OneNote 2016 | ./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/Office16/Policy/Onenote | String | The content inside onent16.admx |
| Microsoft Outlook 2016 | ./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/Office16/Policy/Outlook16 | String | The content inside outlk16.admx |
| Microsoft PowerPoint 2016 | ./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/Office16/Policy/Powerpoint16 | String | The content inside ppt16.admx |
| Microsoft Project 2016 | ./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/Office16/Policy/Project16 | String | The content inside proj16.admx |
| Microsoft Publisher 2016 | ./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/Office16/Policy/Publisher16 | String | The content inside pub16.admx |
| Microsoft Visio 2016 | ./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/Office16/Policy/Visio16 | String | The content inside visio16.admx |
| Microsoft Word 2016 | ./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/Office16/Policy/Word16 | String | The content inside word16.admx |
Note that you can put all application settings in one profile by repeating step 4 for each.
5. Select OK to save your changes. Continue to add more settings as needed.
6. When finished, choose OK and then Create to create the Intune profile.
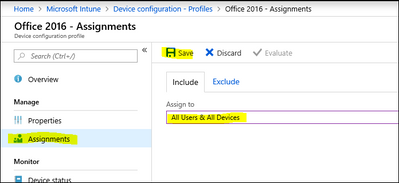
Step 3 - Assign the policy to users
1. Click Assignments, then click Select Groups and select the group you want to assign your policy to. In this example we’re assigning the policy to the All Users & All Devices group.
2. Click Save to save the assignment.
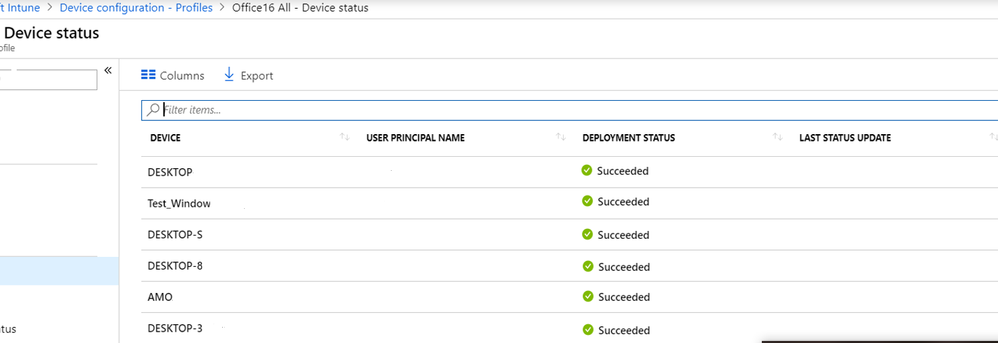
When complete, your profile is shown in the Device configuration - Profiles list.
Reviewing the settings after deployment
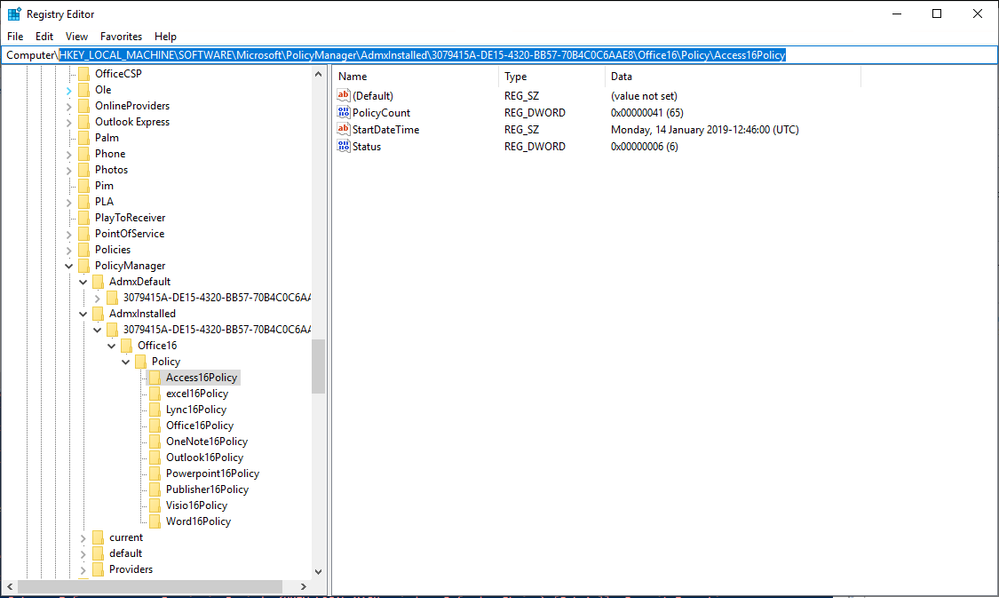
1. On a targeted computer, run RegEdit and navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\AdmxInstalled\. Drill down and you should see policy settings, similar to those shown in the screen shot below.
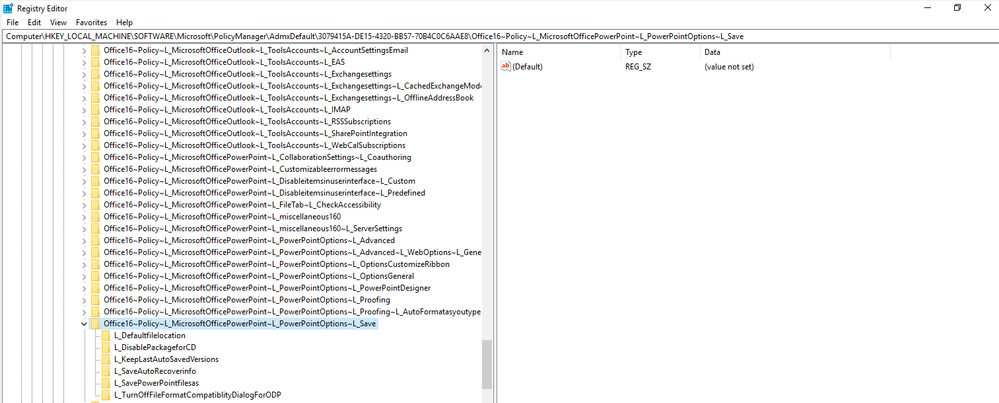
2. Now navigate to: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\AdmxDefault.You should see entries similar to the ones below depending on the policies you configured in step 2 above.
An example using PowerPoint
Now that we’ve gone over through how this works, let’s walk through an example. We’ll configure the default save location for PowerPoint files and customize the AutoRecover frequency and AutoRecover save location for PowerPoint as well.
1. In the Azure portal, select All services, filter on Intune, then select Microsoft Intune.
2. Select Device configuration -> Profiles -> Create profile.
3. Enter the following settings:
- Name: Enter a name for the profile, such as Customer PowerPoint Save Location.
- Description: Enter a description for your profile.
- Platform: Choose Windows 10 and later.
- Profile type: Choose Custom.
4. Under Custom OMA-URI Settings, select Add and enter the following settings:
- Name: Enter a unique name for the OMA-URI setting to help you identify it in the list of settings.
- Description: Enter a description that gives an overview of the setting, and any other important details.
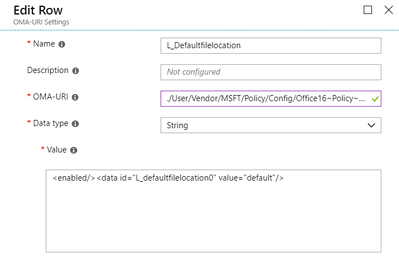
- OMA-URI (case sensitive): Enter the OMA-URI you want to use as a setting. In this example it will be ./User/Vendor/MSFT/Policy/Config/Office16~Policy~L_MicrosoftOfficePowerPoint~L_PowerPointOptions~L_Save
- Data Type: String
- Value: <enabled/><data id="L_defaultfilelocation0" value="default"/>
So how did we know all that? We can see this in the Registry:
Looking in the ppt16.admx file (you can open it in Notepad) we can also see other important information that this setting uses:
<policy name="L_Defaultfilelocation" class="User" displayName="$(string.L_Defaultfilelocation)" explainText="$(string.L_Specifiesthedefaultlocationforpresentationfiles)" presentation="$(presentation.L_Defaultfilelocation)" key="software\policies\microsoft\office\16.0\powerpoint\options">
<parentCategory ref="L_Save" />
<elements>
<text id="L_defaultfilelocation0" key="software\policies\microsoft\office\16.0\powerpoint\recentfolderlist" valueName="default" required="true" expandable="true" />
</elements>
</policy>
So when we’re done it should look something like this:
5. Select OK to save your changes. In this example I’m going to add a few other settings like L_AutoRecoversavefrequencyminutes as it will be enabled by just inputting the required settings (i.e. we do not need to add <enabled/>
<policy name="L_SaveAutoRecoverinfo" class="User" displayName="$(string.L_SaveAutoRecoverinfo)" explainText="$(string.L_CheckedCheckstheoptionSaveAutoRecoverinfoUncheckedUnchecksth)" presentation="$(presentation.L_SaveAutoRecoverinfo)" key="software\policies\microsoft\office\16.0\powerpoint\options">
<parentCategory ref="L_Save" />
<elements>
<boolean id="L_EnablesaveAutoRecoverinfo" valueName="saveautorecoveryinfo">
<trueValue>
<decimal value="1" />
</trueValue>
<falseValue>
<decimal value="0" />
</falseValue>
</boolean>
<decimal id="L_AutoRecoversavefrequencyminutes" valueName="frequencytosaveautorecoveryinfo" minValue="1" maxValue="9999" />
<text id="L_AutoRecoversavelocation" valueName="pathtoautorecoveryinfo" expandable="true" />
</elements>
</policy>
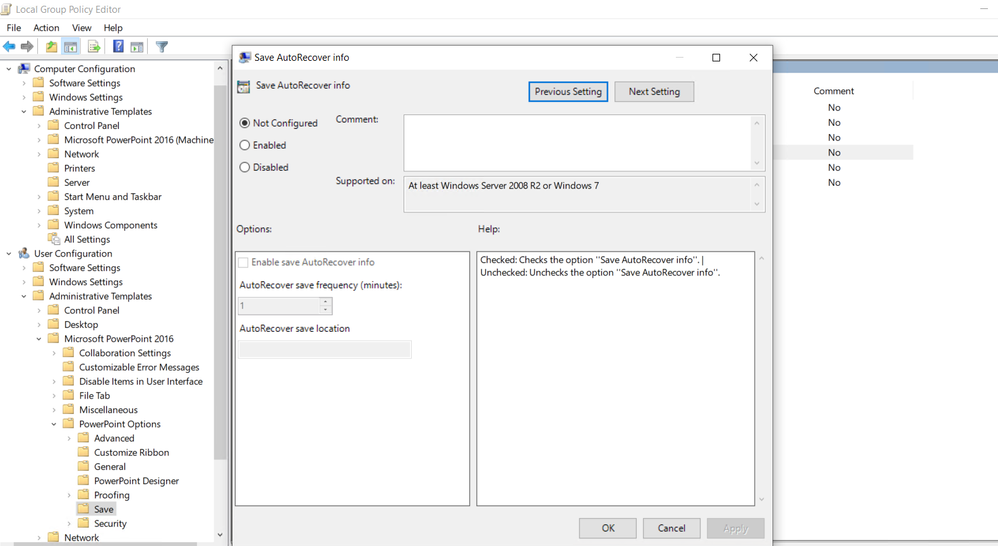
This policy includes multiple values inside of it like, the highlighted ones above (boolean, decimal and text). For these kinds of policies, I suggest adding the ADMX inside windows policy definitions and the ADML files inside Policy Definition/en-us in order to review the policy settings and the parameters inside it. Using gpedit.msc and looking under Microsoft PowerPoint 2016 we can see the data inside these parameters to enable it.
Putting all this together, the settings from the Intune side to enable this policy are as follows:
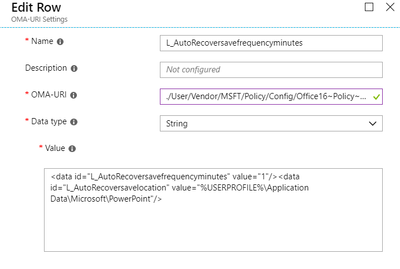
- OMA-URI: ./User/Vendor/MSFT/Policy/Config/ Office16~Policy~L_MicrosoftOfficePowerPoint~L_PowerPointOptions~L_Save/L_SaveAutoRecoverinfo
- Data-Type: String
- Value:
<data id="L_AutoRecoversavefrequencyminutes" value="1"/>
<data id="L_AutoRecoversavelocation" value="%USERPROFILE%\Application Data\Microsoft\PowerPoint"/>
It will look something like this:
When finished, choose OK and then Create to create your Intune profile. When complete, your profile will be shown under Device configuration -> Profiles.
Summary
This guide shows us the full cycle of ingesting ADMX files for Office and how to work with the policies inside, noting that each policy has its own configuration settings and that you need to be aware of how to deal with them to deliver them successfully to your targeted computers.
I also mentioned how some policies inside each ADMX file are different from other, and how you need to review the required policy from the administrative template since as it will show you a clear view of the settings included in each policy.
One last note: we have a new preview feature that has been recently added to Intune called Administrative Templates which include some of these same ingested settings, however at this point it does not yet include all of them.
Mohammed Abudayyeh
Intune Support Engineer