This post has been republished via RSS; it originally appeared at: Intune Customer Success articles.
Hi everyone, today we have a post by Intune Support Engineer Himanshu Jangra. In this post, Himanshu takes a look at enabling Bitlocker via Intune policy, explaining how you can verify that your policy is successfully deployed to client devices as well as providing troubleshooting tips should things not work out the way that you planned. This is a must-read whether you’ve already deployed Windows Encryption policies in your environment or if you’re still just in the planning phases.
=====
When deploying BitLocker policies to Windows 10 devices using Microsoft Intune, if you encounter an issue it’s important that you first determine whether the issue is Intune-related or Windows-related so that you can focus your troubleshooting efforts in the right place. As part of that, a key question is whether the Intune policy has been successfully deployed to the target device. We’ll get to that in a moment, but first let’s take a minute and get a basic understanding of Windows BitLocker and what the purpose is.
Understanding Bitlocker
BitLocker drive encryption is a service offered for Microsoft Windows operating systems that allows users to encrypt data on their hard drives. This comes in handy if the device gets lost or stolen and in cases of inappropriately decommissioned devices. Currently BitLocker supports encryption for operating system drives, removable media drives and fixed data drives, and if the situation demands, we can use 256-bit encryption for better protection of sensitive data.
- Device Configuration policies: Certain built-in policy options are available in the Intune admin console at Device Configuration -> Endpoint Protection -> Windows Encryption Policy. You can find all the available switches and features here: https://docs.microsoft.com/en-us/intune/endpoint-protection-windows-10#windows-encryption.
BitLocker policies make use of the BitLocker CSP built into Windows to configure encryption on the client device. When Intune deploys a BitLocker policy to an assigned device, the BitLocker CSP on the client writes the appropriate values to the Windows registry in order for the settings in the policy to take effect.
If you’d like to learn more about Bitlocker, see the resources below.
- Bitlocker overview: https://docs.microsoft.com/en-us/windows/security/information-protection/bitlocker/bitlocker-overview
- Bitlocker prerequisites: https://docs.microsoft.com/en-us/windows/security/information-protection/bitlocker/bitlocker-overview-and-requirements-faq
Now that we have a general understanding of what these policies do and how they work, let’s look at how we can verify whether the BitLocker settings have been successfully applied to a Windows client.
Verifying Bitlocker Settings
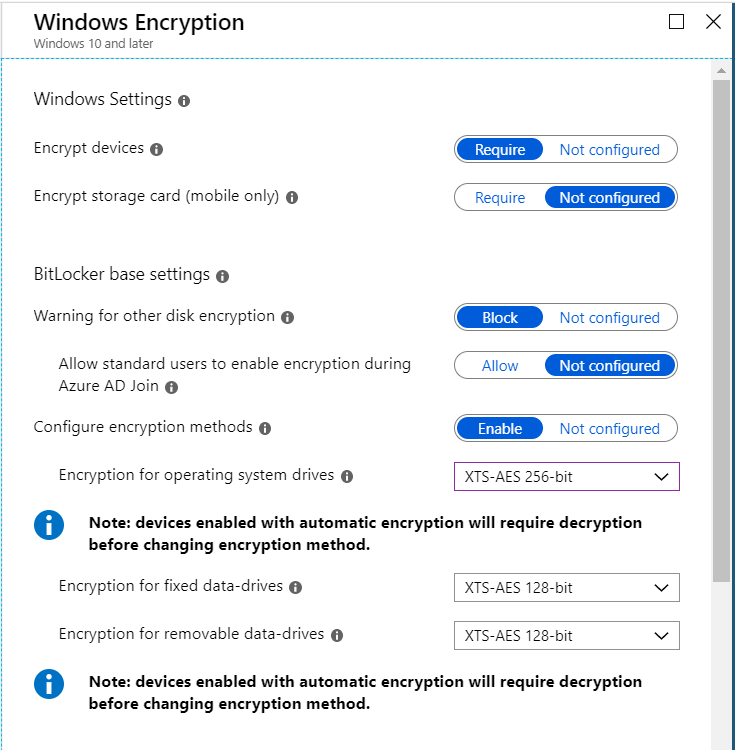
Let’s begin by assuming that we have deployed a Windows Encryption (BitLocker) device configuration policy with the settings shown below to one of our Windows 10 managed PCs.
How do we confirm that the settings have been applied to the targeted device? There are a few different ways we can do that.
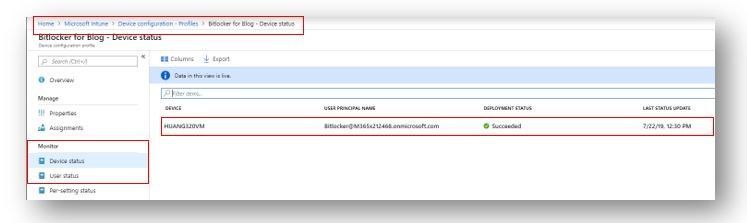
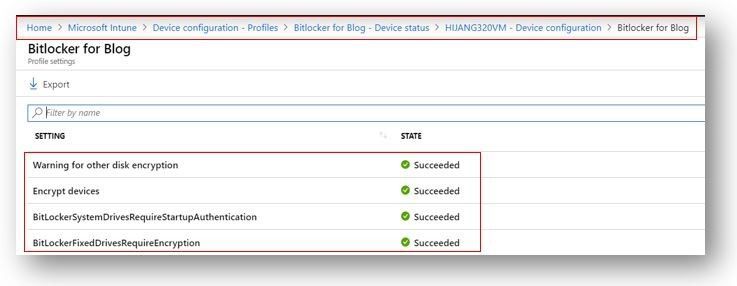
1. Check the policy deployment status in the Intune portal.
As you can see above, everything looks good and is reporting a success. You always want to check the policy status first as normally that is sufficient to determine whether the policy has been deployed successfully. However, let’s cover a few other options just in case you might find them helpful when troubleshooting related issues.
NOTE Because it takes a certain amount of time to encrypt a drive, there may be a delay between a client receiving a Bitlocker policy and the drive being fully encrypted.
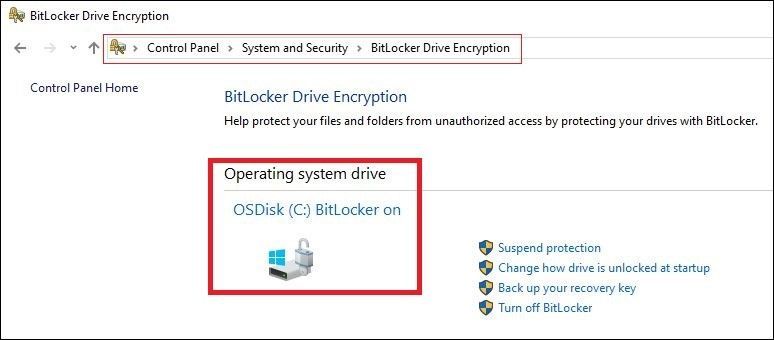
2. Check in Control Panel on the client. Once Bitlocker is on and the drive is encrypted, Bitlocker will indicate that as shown below.
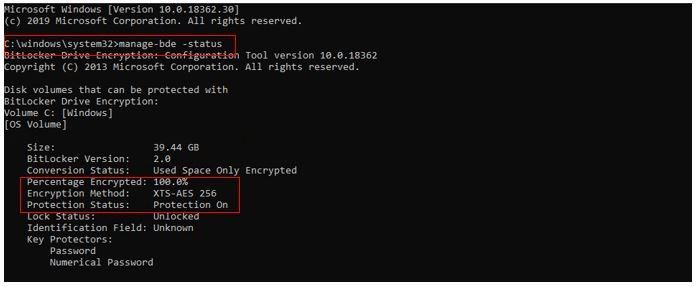
3. Verify the status from a command prompt. On the Windows 10 client, launch Command Prompt with admin credentials (right-click -> Run as Administrator) then run manage-bde -status. It should look something like this:
As we can see in the output, BitLocker protection is On, the Percentage Encrypted is 100% and our Encryption Method is XTS-AES 256.
We can also check Key Protectors by running this command:
Manage-bde -protectors -get c:
Or from PowerShell:
Confirm-SecureBootUEFI
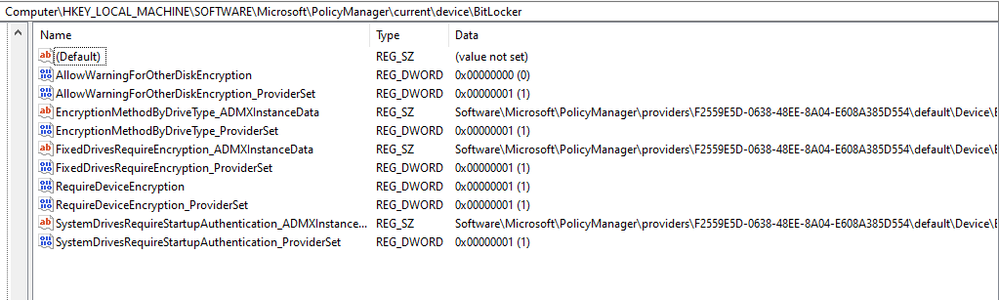
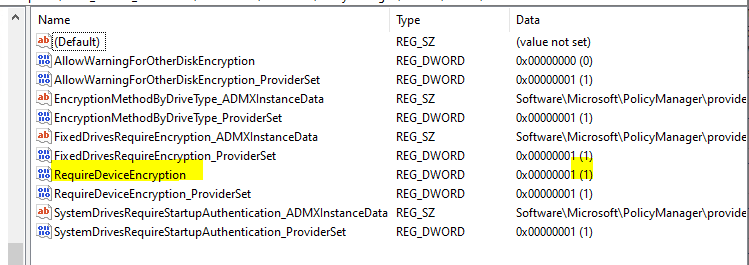
4. Verify that the Registry keys are configured. If the Bitlocker policy is successfully deployed to the target device, you will be able to see the settings in the Registry under HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\current\device\BitLocker. Here’s an example:
These values are configured by the BitLocker CSP so you can verify that the values of the keys match the settings specified in your Intune Windows Encryption policy. For more information on each of these settings see https://docs.microsoft.com/en-us/windows/client-management/mdm/bitlocker-csp.
NOTE The Windows Event Viewer will also contain various information related to Bitlocker. There are too many to list here but searching for Bitlocker API will provide you with a lot of useful information.
5. Check the MDM diagnostics report. You can also generate and view an MDM diagnostic report from the targeted device and confirm that the BitLocker policy is in it. If you can see the policy settings in the report, this is another indication that the policy was successfully deployed. The Microsoft Helpsvideo below explains how to capture an MDM diagnostic report from a Windows device.
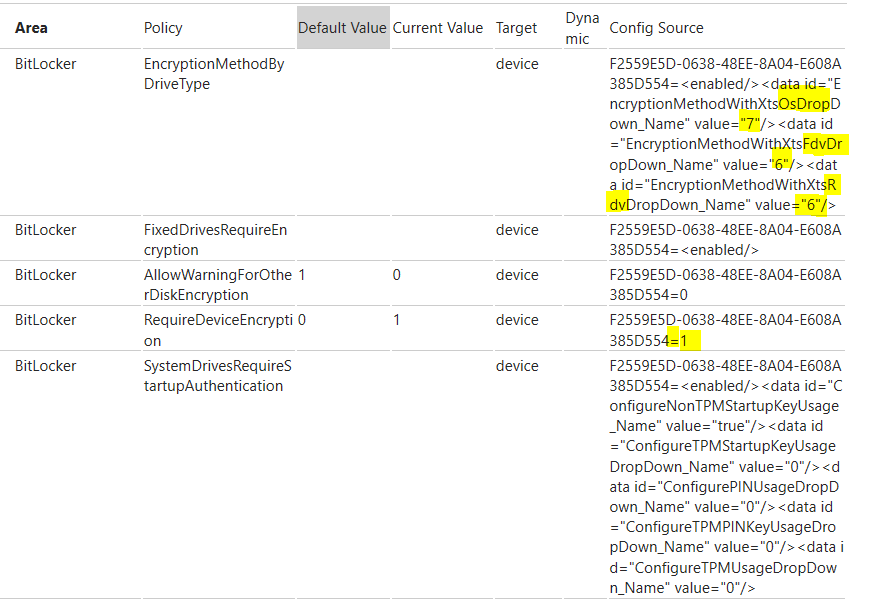
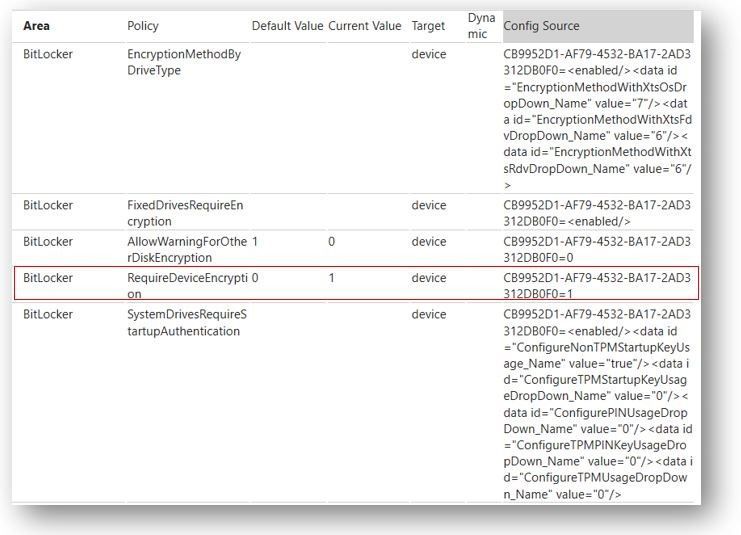
When analyzing the MDM diagnostics report, the contents can seem a little confusing at first but here’s an example showing how we can correlate what’s in the report with the settings in a policy:
The output result shows the values that correspond to the values we have configured in the BitLocker Policy:
MDM diagnostics Output results:
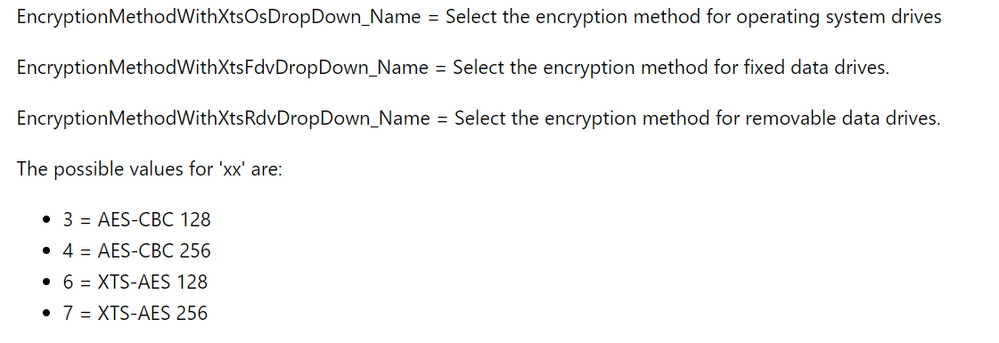
EncryptionMethodWithXtsOsDropDown: 7 (The value 7 refers to the 256 bit encryption)
EncryptionMethodWithXtsFdvDropDown: 6 (The value 6 refers to the 128 bit encryption)
EncryptionMethodWithXtsRdvDropDown: 6 (The value 6 refers to the 128 bit encryption)
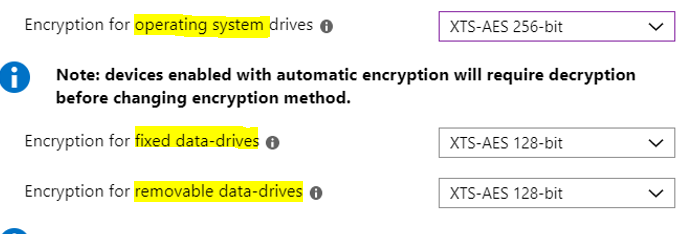
You can reference the BitLocker CSP documentation to see what each value means. For the purposes of our example here, I have shared the snippet below.
Similarly, we can see all the values and verify it from the BitLocker CSP link
TIP The primary purpose of the MDM diagnostic report is to assist Microsoft Support when troubleshooting issues. If you open a support case for Intune and the problem involves Windows clients, it’s always a good idea to gather this report and include it in your support request.
Troubleshooting BitLocker Policy
At this point you should have a pretty good idea how to confirm that the BitLocker policy is being successfully deployed, but what if it’s not? Here are a few things to check:
- Is the device properly enrolled into Microsoft Intune? If not, you’ll need to address that before troubleshooting anything specific to the policy. Help with troubleshooting Windows enrollment issues can be found here.
- Is there an active network connection on the device? If the device is in airplane mode or it’s turned off, or if the user has the device in a location with no service, the policy will not be delivered or applied until network connectivity is established.
- Have you deployed the BitLocker policy to the correct user/device group? Be sure to double check that the correct user/device really is in that group. This one is far more common than you might think and it often gets overlooked.
- Does the deployment of the entire policy fail, or is it that only certain settings are not being applied? If you find yourself faced with a scenario where only some policy settings are not being applied, here are a couple things to check:
1. Not all Bitlocker settings are supported on all Windows versions. The policy comes down in a single unit, so if some policy settings are being applied and others are not, you can be confident that the policy itself is being received from Intune successfully. Instead, this probably means that the settings that are not being applied are not supported on the version of Windows on that client. See BitLocker CSP in the Windows documentation for details on version requirements for each setting.
2. Bitlocker is not supported on all hardware. Even if you have the right version of Windows, it’s possible that the underlying hardware does not meet the requirements for Bitlocker encryption. You can find all the system requirements for Bitlocker here, but the main things to check are that the device has a compatible TPM chip (1.2 or later) and a Trusted Computing Group (TCG)-compliant BIOS or UEFI firmware.
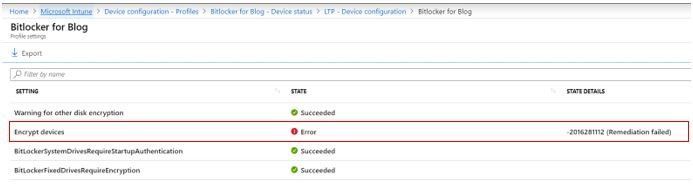
To give you an example, I recently worked with a customer who deployed a BitLocker policy to a Windows 10 device and the Encrypt devices setting was showing a status of Error in the portal:
As the name suggests, this setting allows an administrator to require encryption to be turned on by using BitLocker\Device Encryption. Using the troubleshooting tips mentioned earlier, we first checked the MDM Diagnostics report. The report confirmed that the correct policy was in fact deployed on the device:
We could also verify this in the Registry:
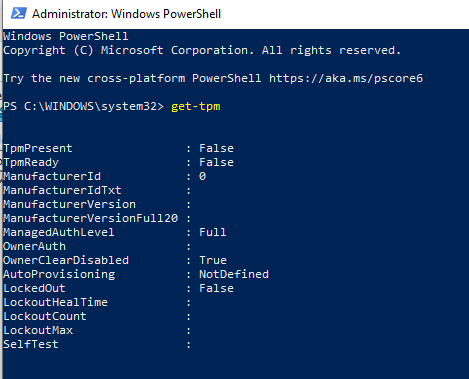
We then checked the status of TPM using PowerShell and found that TPM was not available on the device:
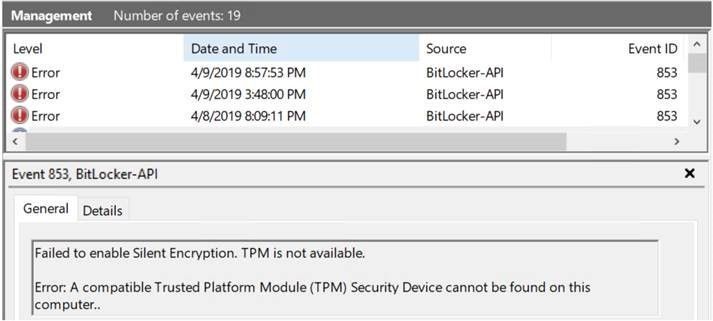
As an additional tip, you can confirm the same in the Windows Event Viewer under Applications and Services log -> Windows -> BitLocker API. In the BitLocker API event log we found an Event ID 853 which told us that TPM was not available:
Because Bitlocker relies on TPM, we could therefore conclude that Bitlocker was failing not because of a problem with Intune or the policy, but rather because the device itself either did not have a TPM chip, or TPM was disabled in the BIOS.
NOTE You can also check the TPM status by running tpm.msc on the device.
3. Pre-existing Bitlocker configuration. If the device to which you apply Bitlocker policy is already encrypted using Bitlocker but with different settings (for example – the encryption algorithm method may differ – 128 v’s 256 bit) it will not be possible for the MDM policy based settings to override the current settings and become compliant. The reason is that it is not possible for Bitlocker to modify configuration such as encryption on the fly – therefore the only way to make the device compliant with the MDM provided settings is to first decrypt the drive.
Note many Windows devices now support automatic encryption during the OOBE process which can potentially lead to the above scenario. However, by combining MDM policy with AutoPilot deployment the automatic encryption can be pre-empted allowing the MDM settings to be applied.
Conclusion
When troubleshooting Bitlocker policy issues with Intune, if you can confirm that the policy is reaching the intended client device then it’s usually safe to assume that the problem is not directly related to Intune, but more likely an issue with the Windows OS or the hardware. This means you need to start looking in other areas like the TPM configuration or UEFI and Secure boot (also required). You can also try to isolate the issue by enabling BitLocker manually – if you can turn on Bitlocker manually then Intune will not be able to turn it on via policy. Also be aware that the Windows Recovery Environment (WinRE) must be enabled on the client for Bitlocker to work. If your organization is using custom images, WinRE is another one that often gets overlooked.
Here are a few more resources you may find helpful when working with Bitlocker:
- Bitlocker product documentation
- Bitlocker system requirements
- BitLocker frequently asked questions
- BitLocker CSP documentation
- Intune Windows Encryption policy settings
- Hardware independent automatic Bitlocker encryption using AAD/MDM
- Walkthrough creating and deploying Bitlocker policy with Intune
- Setting the BitLocker encryption algorithm for Autopilot devices
Himanshu Jangra
Intune Support Engineer