This post has been republished via RSS; it originally appeared at: Running SAP Applications on the Microsoft Platform articles.
A year ago I was working with Maximilian and Marius from the SAP Developer Experience team for a new Tutorial / Mission for SAP TechEd 2018. The goal was to show how customers can build awesome cross-cloud experiences consuming data and services provided by Microsoft (O365/M365) and SAP cloud applications. In our demo, we specifically showed how data from Microsoft Graph could be integrated in SAP Fiori applications.
As a result Marius had published a beautiful mission that guides the user step by step through the process: Create a simple UI5 application, connect it to an SAP datasource, register the application in Azure Active Directory and configure access to the Microsoft Graph API. You can find the tutorial here and are more than welcome to test it out [we will also be at SAP TechEd 2019 in Las Vegas, Barcelona and Bangalore -- so feel free to stop by and ask us questions!]
When we first launched the mission during the SAP Developer Garage we already got some pretty good responses. But throughout the year Maxi, Marius and I showcased this scenario several time and got even more positive feedback. In the meantime several partners have built scenarios based on the integration that we had showcased.
One topic, that we did not discuss during the mission was how to actually setup Single Sign-On for this scenario. When you follow the steps as outlined you still need to log on with your SAP user and then do an additional authentication with your Microsoft user. In this blog, I want to outline the steps to actually configure and get a seamless SSO experience. You only log on once when you open the application and then you can retrieve both data from your SAP system and from Microsoft Graph.
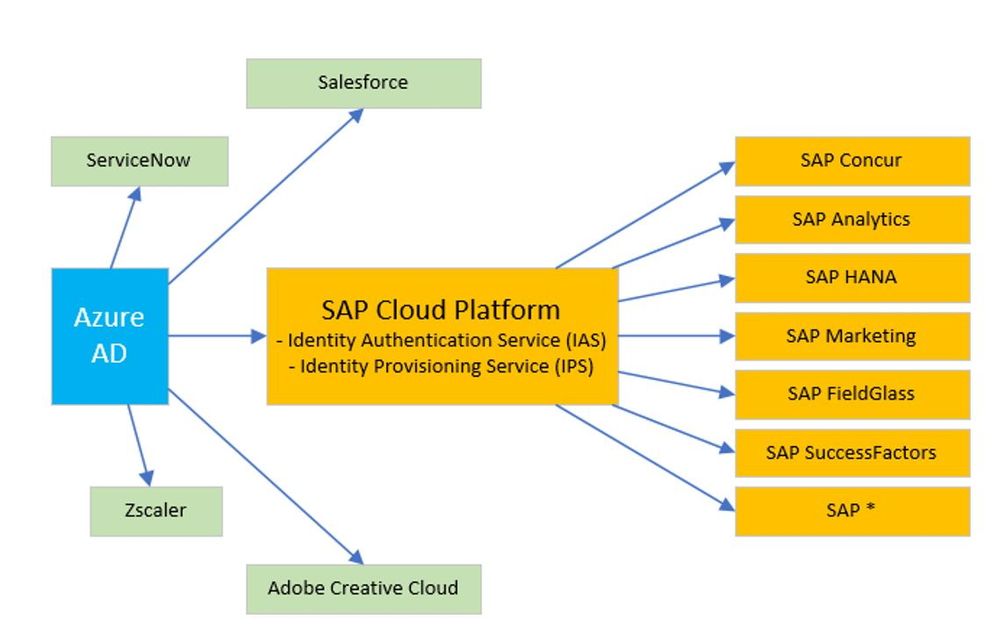
I want to highlight that there are several options on how this can be done. I want to focus on leveraging the SAP Cloud Platform Authentication: Identity Authentication Service, IAS . The beauty of this service is that once you have configured Azure Active Directory as a trusted service provider, you can get a SSO to all applications that are connected to IAS. This is of course also true for SAP applications: be it SAP Cloud Platform, Success Factors, SAP Ariba, …
In order to follow the steps below, please make sure that you have already created the Application as outlined in the Tutorial: https://developers.sap.com/mission.teched-2018-microsoft.html. Once that is done, you can configure seamless SSO experience in just 3 easy steps:
Step 1: Connect SAP Cloud Platform app to SAP IAS
a) In the first step, we need to change the Application Identity Provider in the SAP Cloud Platform from the default SAP ID Service (accounts.sap.com) to our own IAS.
In my example the the SAP Cloud Platform Trial environment belongs to a different entity than the IAS. So I need to setup the trust manually. If both belong to you -- which is most likely the case for most scenarios -- you can just follow the steps outlined
https://help.sap.com/viewer/65de2977205c403bbc107264b8eccf4b/Cloud/en-US/d3df5b457d0c43fca117da0dc14e2f0d.html (press "Add Identity Authentication” and choose the appropriate IAS tenant and you are done!)
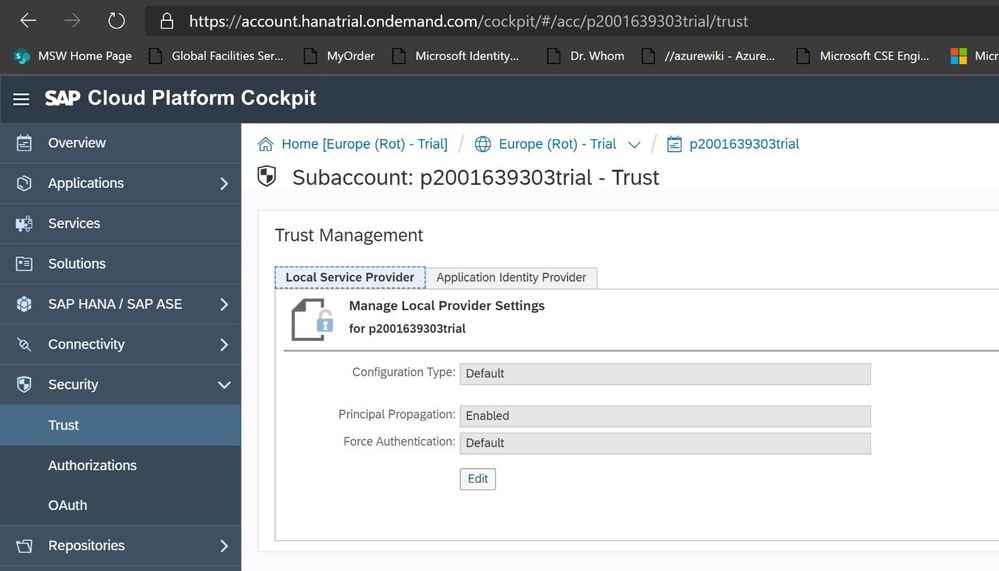
In order to set it up manually, open up the SAP Cloud Platform Cockpit https://account.hanatrial.ondemand.com/cockpit and go to Security -> Trust
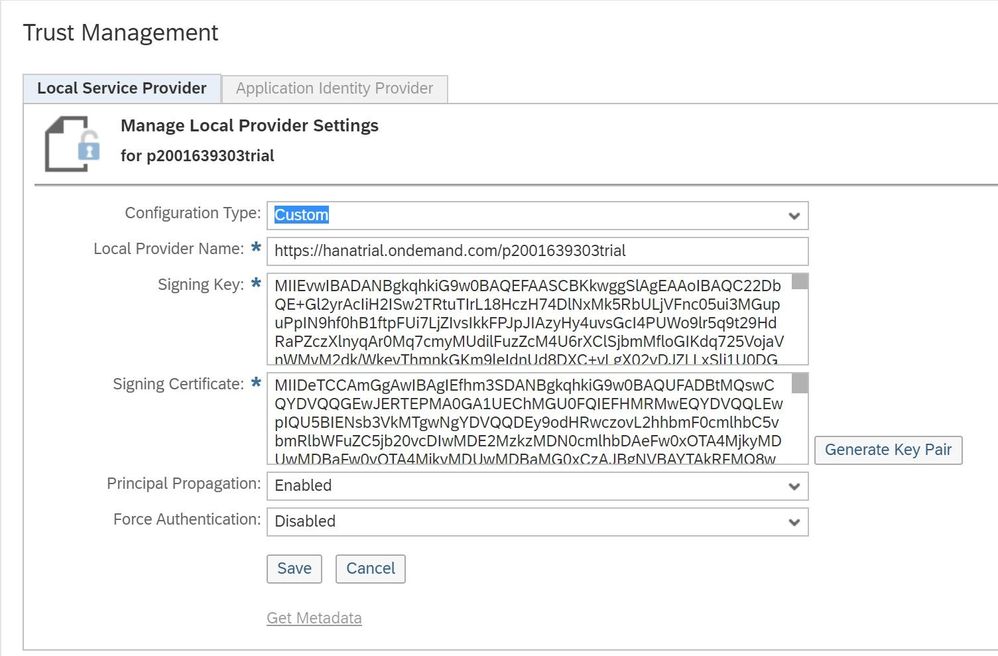
Click on Edit, select the Configuration Type Custom and click on Save.
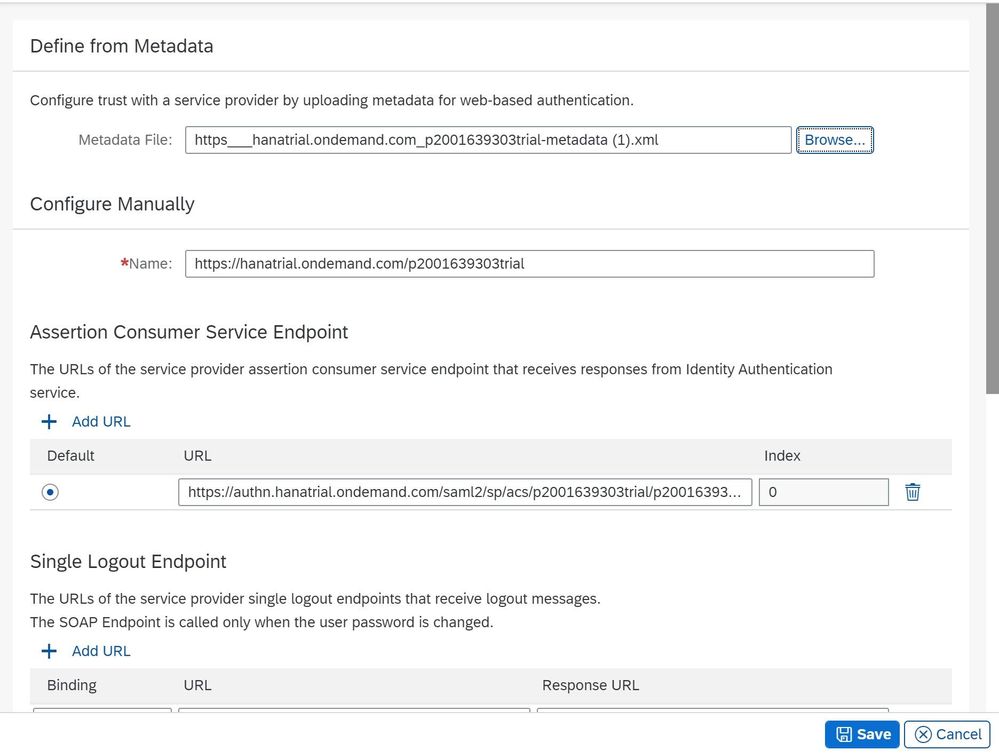
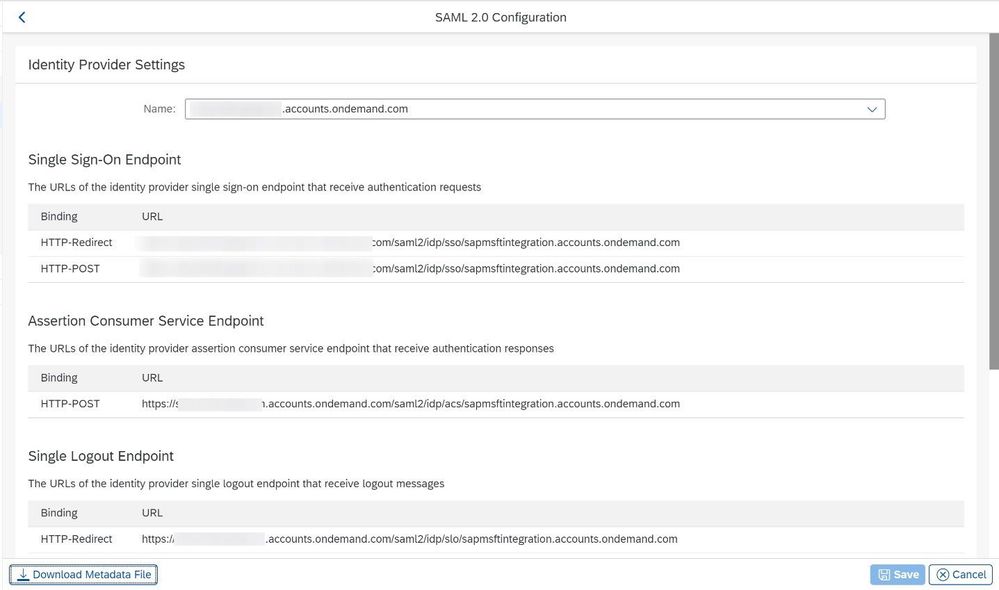
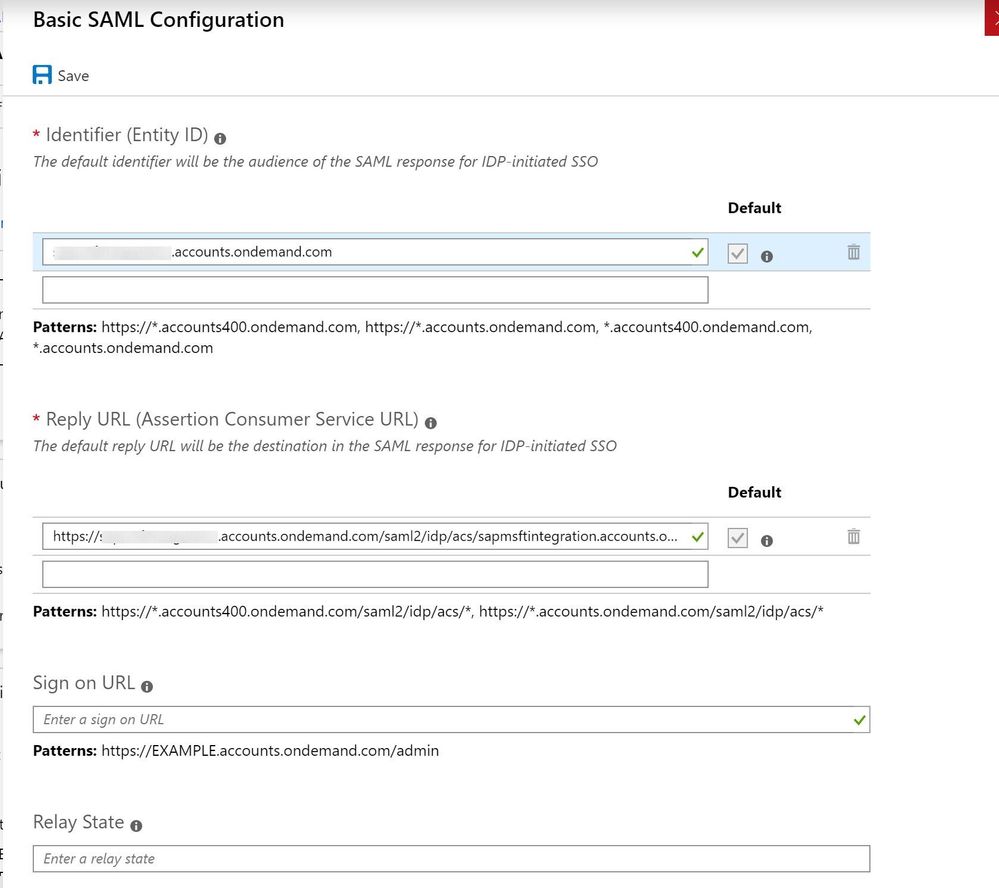
This allows you to download the Metadata files from your SAP Cloud Platform tenant (Click on Get Metadata -> https___hanatrial.ondemand.com_p2001639303trial-metadata ) and in subsequent steps upload it to IAS so that we can establish a trust between the two platforms.
Now let’s switch to the SAP Cloud Platform Identity Authentication Service, e.g. https://[your-account-name].accounts.ondemand.com/admin/#
From here select Applications & Resources -> Applications
and Click on " + Add"
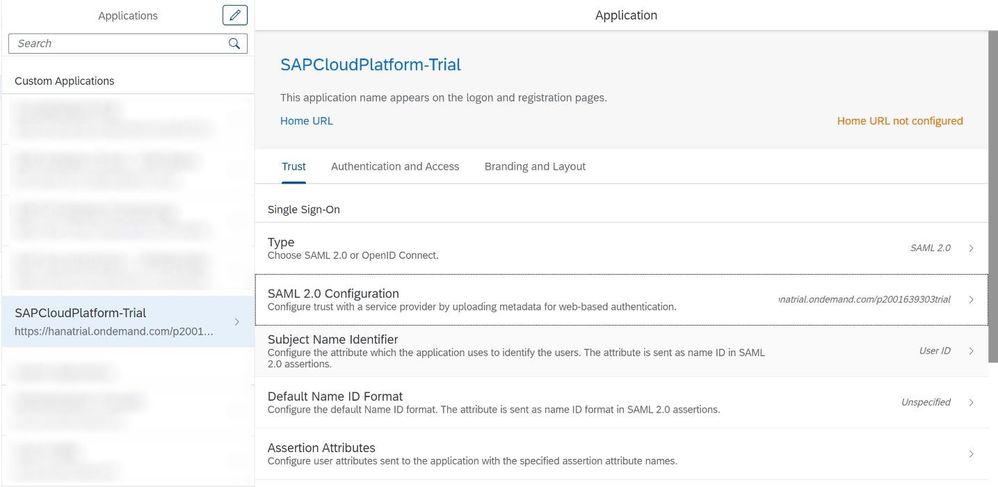
Next click on "SAML 2.0 Configuration"
Just upload the Metadata file file from your SAP Cloud Platform Trial that we downloaded previously to import all the relevant configuration parameters.
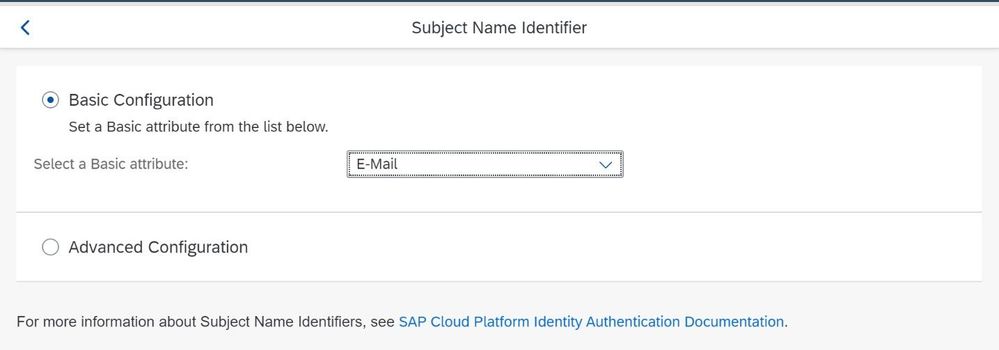
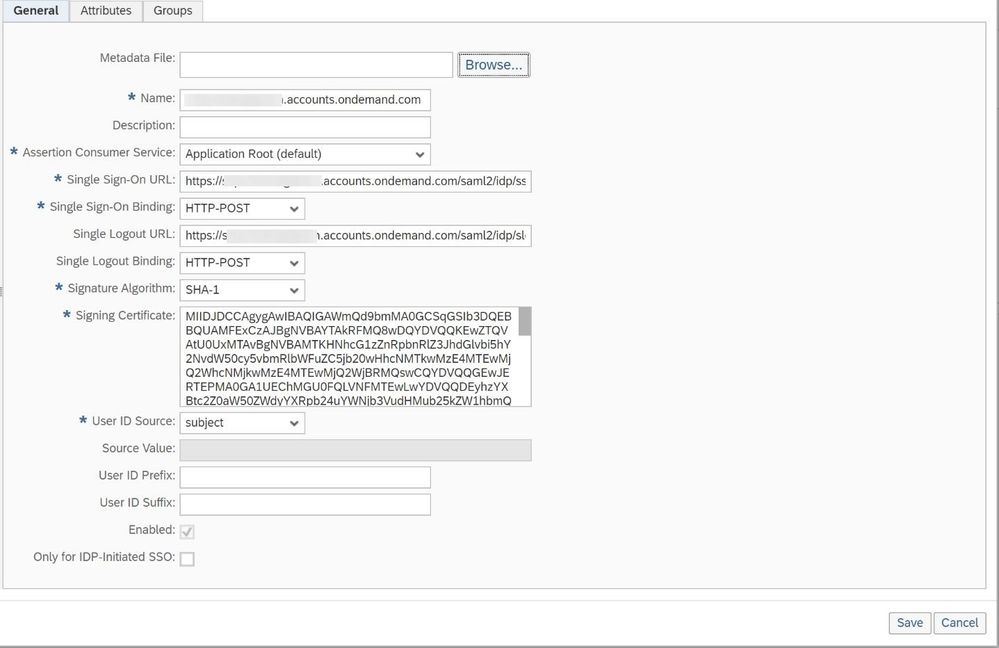
Although the configuration is already done and would work, we want to change the unique identifier from User ID to the Email-Address so that we can enable a SSO from SAP Cloud Platform to Azure Active Directory later on more easily.
For this select the Subject Name Identifier
and switch the configuration to E-Mail
Make sure to Save the configuration after that.
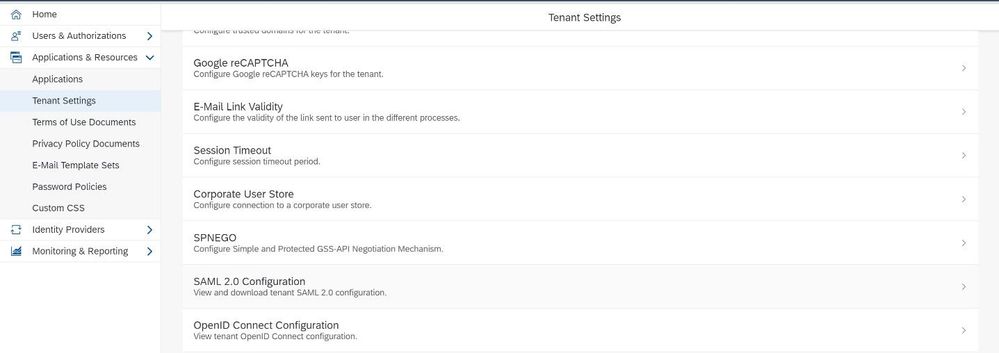
The last step now is to export the Metadata information from the IAS and import it to the SAP Cloud Platform Trial environment.
For this go to Application & Resources -> Tenant Settings -> SAML 2.0 Configuration
From here you can just download the Metadata File metadata.xml
Now we can finish the configuration in the SAP Cloud Platform. Go back to the SCP Cockpit -> Security -> Trust and select the Application Identity Providers Tab. Click on Add Trusted Identity Provider
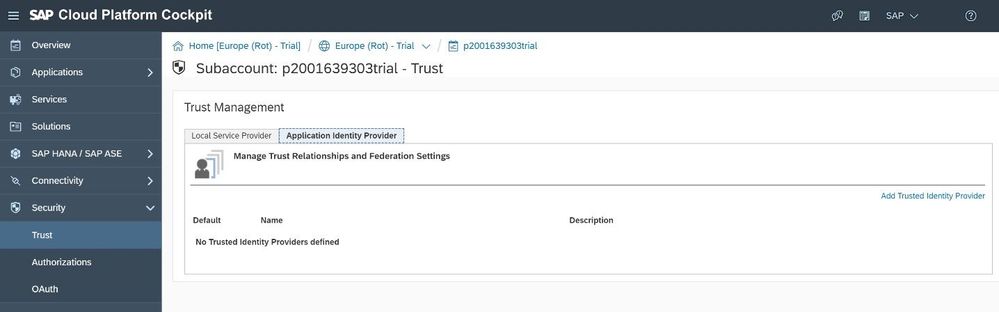
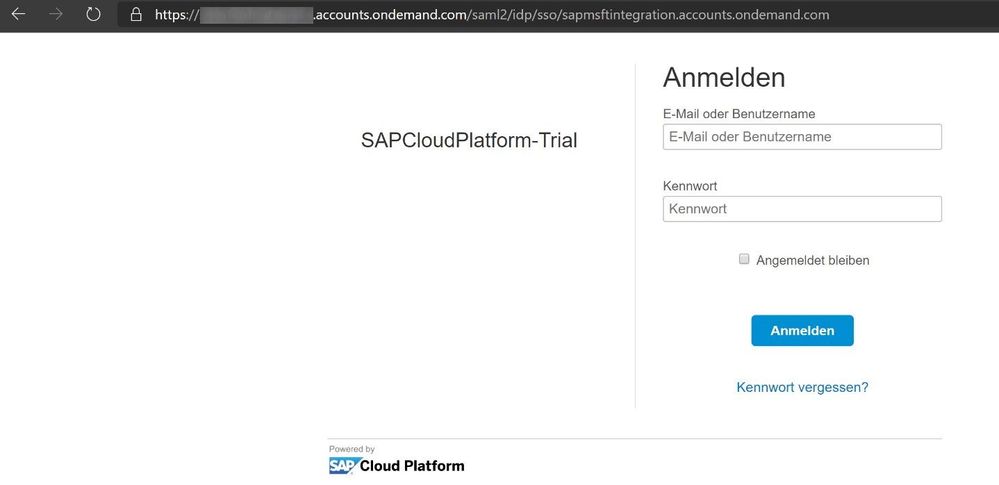
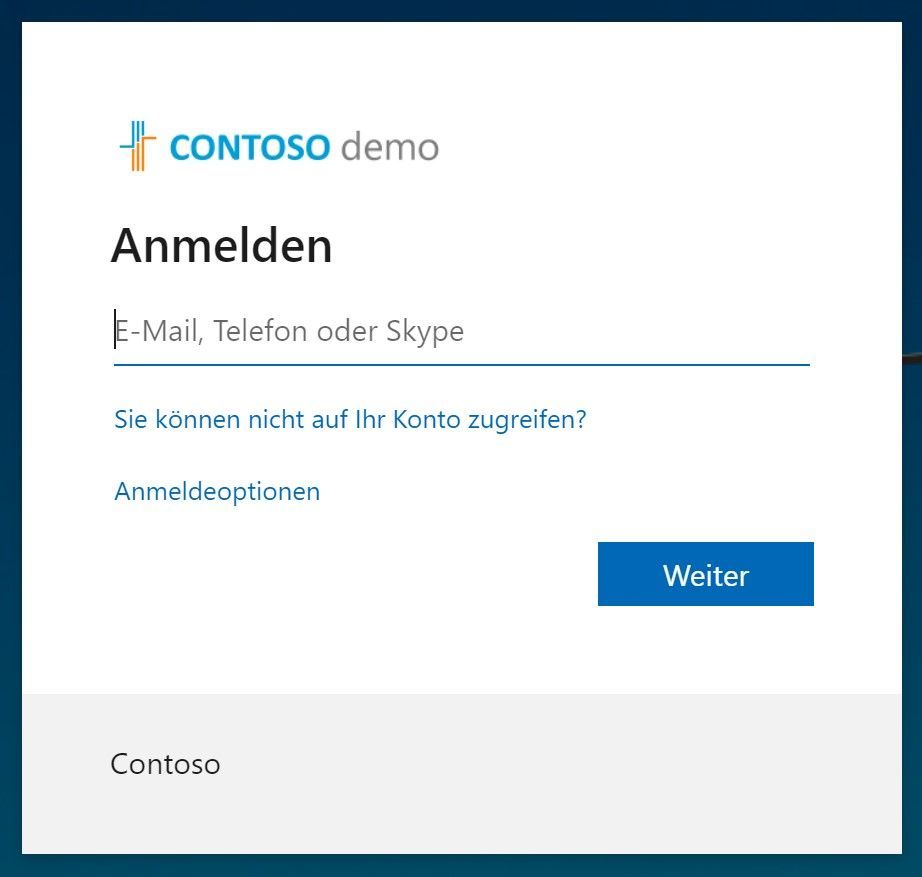
With this configuration now all applications that are running on your SAP Cloud Platform tenant and require an authentication would redirect to IAS, e.g. when I try to open the Web IDE (https://webidecp-<P-Id>trial.dispatcher.hanatrial.ondemand.com/) I can see not the default authentication screen from SCP, but the one that I have just configured
Step 2: Connect SAP IAS to Microsoft Azure AD
Now we want to change this configuration to Azure Active Directory. The SAP Cloud Platform IAS has a very easy configuration for this. Similar like before we need to configure some steps on IAS, others on the identity provider, in this case Azure Active Directory.
This time we start with Azure Active Directory.
Go to the Azure Portal, https://portal.azure.com and navigate to Azure Active Directory
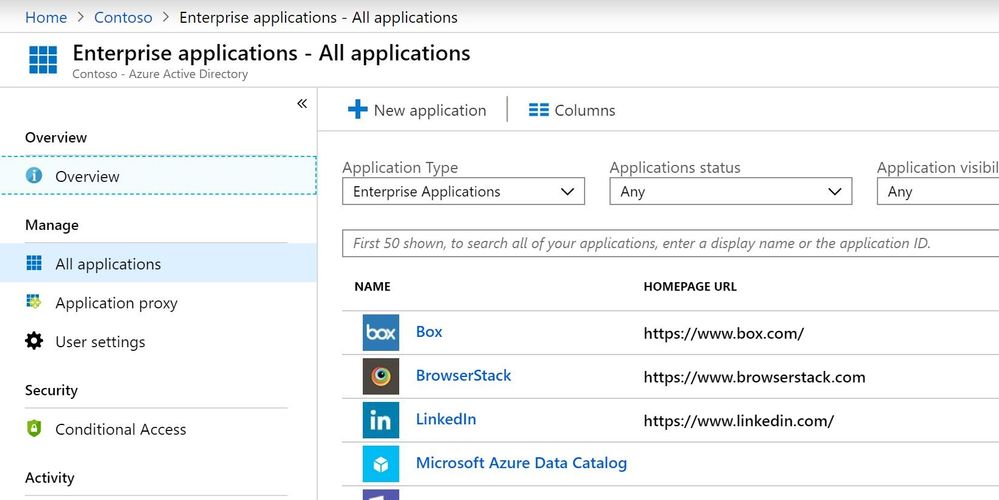
From the Azure Active Directory page select Enterprise Applications and click on "+ New application"
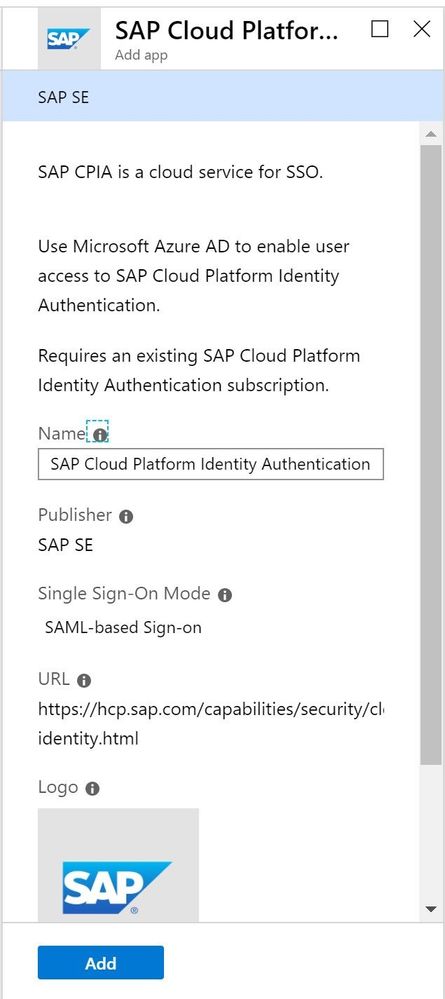
Azure AD has templates for lots of applications, one of them the SAP Cloud Platform Identity Authentication Service. Search for this and select it.
Give it a name and click on Add
After a short period of time the new Application is available in Azure AD and should open.
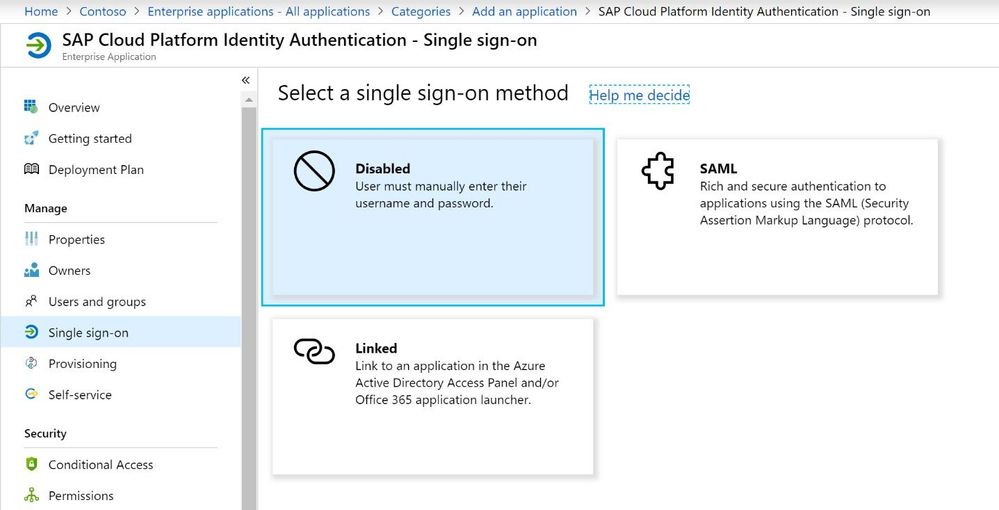
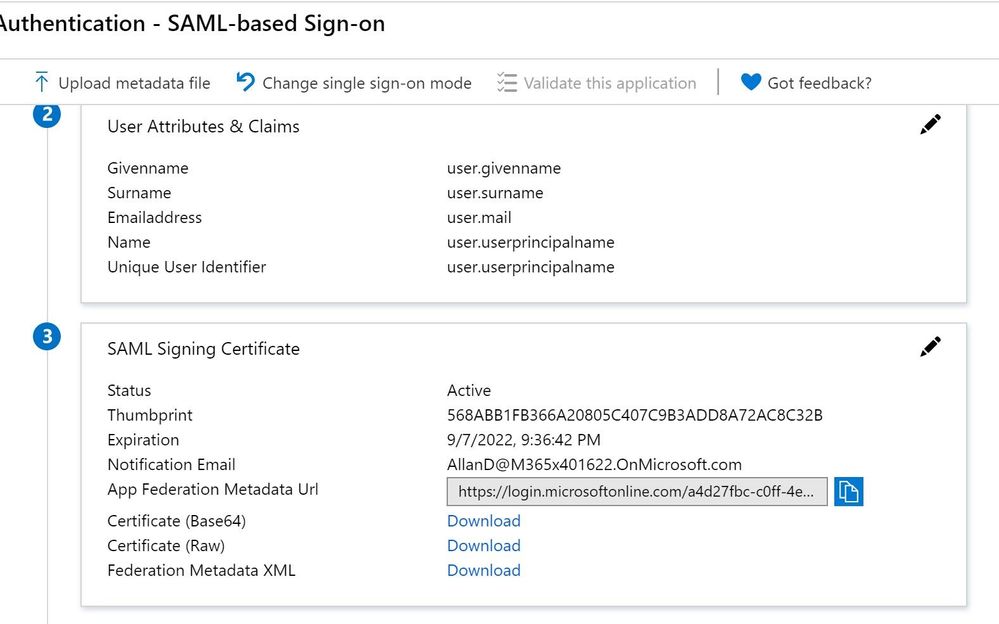
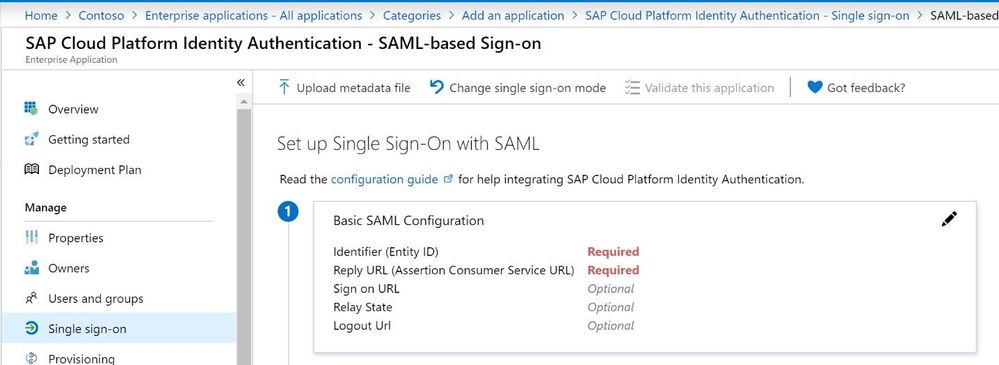
In order to configure the trust, click on Single sign-on and select SAML
Scroll down and download the Federation Metadata XML from before (SAP Cloud Platform Identity Authentication.xml)
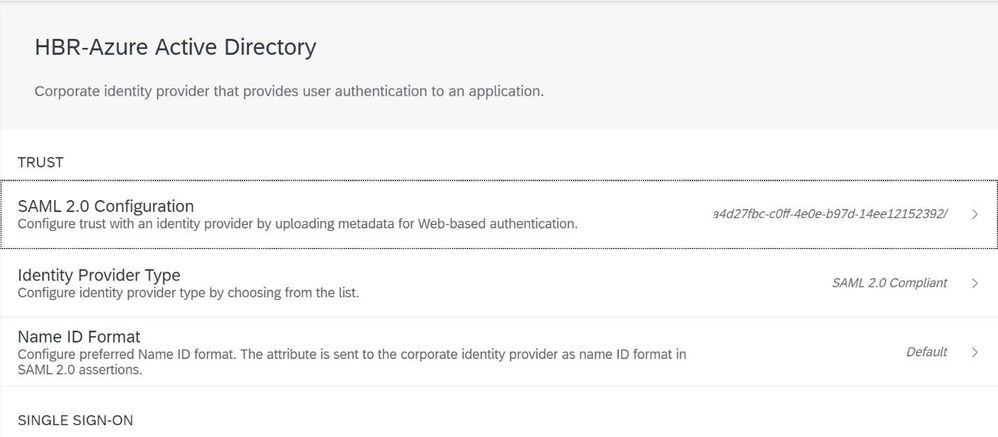
With this file lets continue with IAS. In the IAS cockpit go to Identity Providers -> Corporate Identity Providers
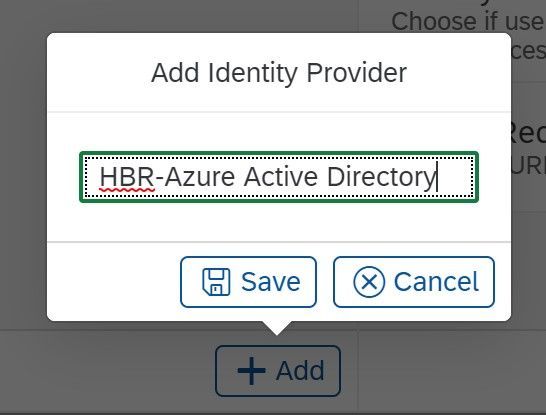
and select click on + Add and add a Name for the new Azure Active Directory Identity provider
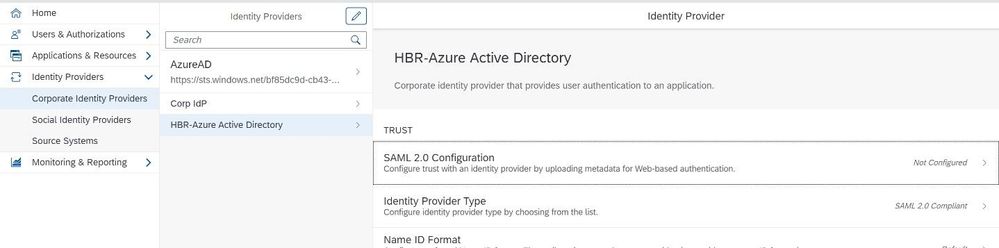
Once it is created, go to to SAML 2.0 Configuration
and upload the Metadata file from AAD:
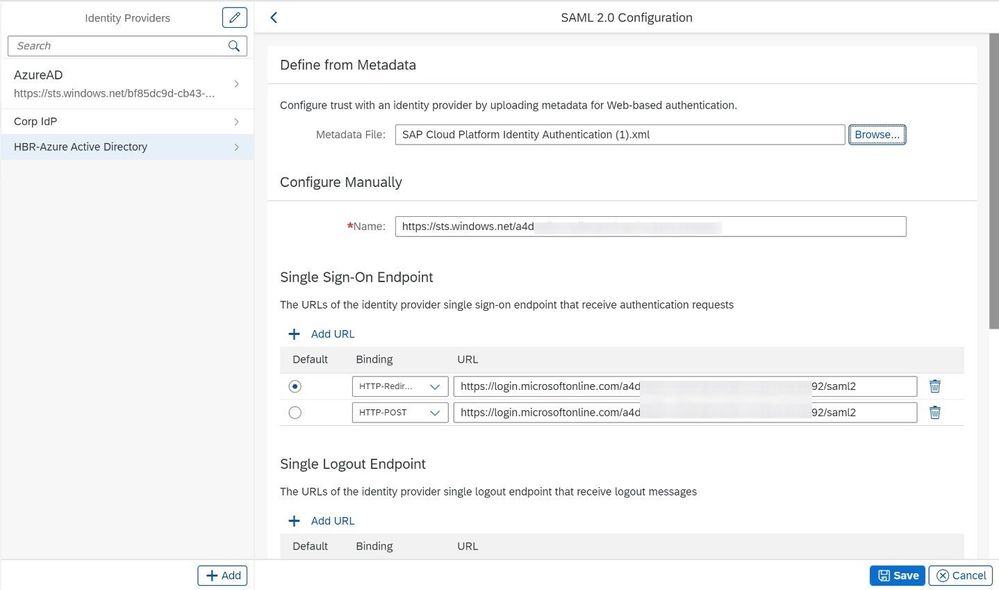
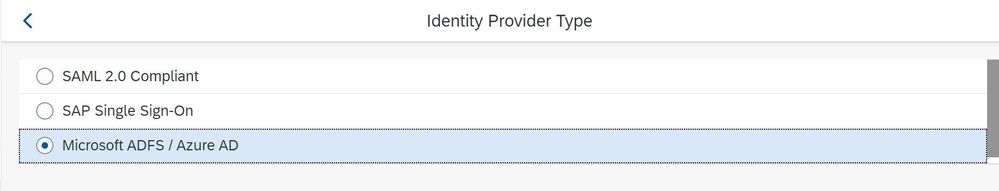
and change it to Microsoft ADFS / Azure AD
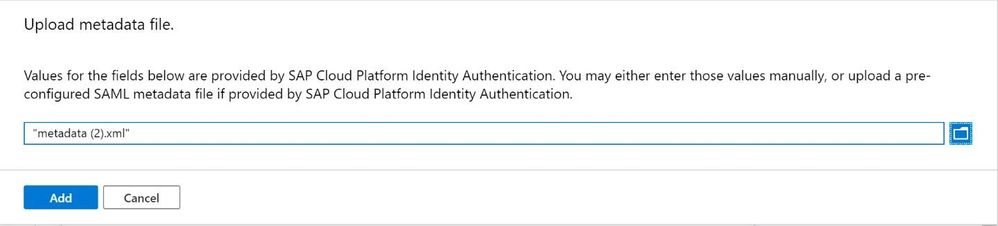
Similarly we need to upload the Metadata file from SCP IAS to Azure AD. Go back to Azure AD and upload the Metadata file from SCP IAS. Click on Upload metadata file
and select the metadata file
and click on Save
That's (almost) all the configuration required on Azure AD.
Step 3: Configure SAP Cloud Platform app in IAS to use Azure AD for authentication and grant Azure AD user access to the app
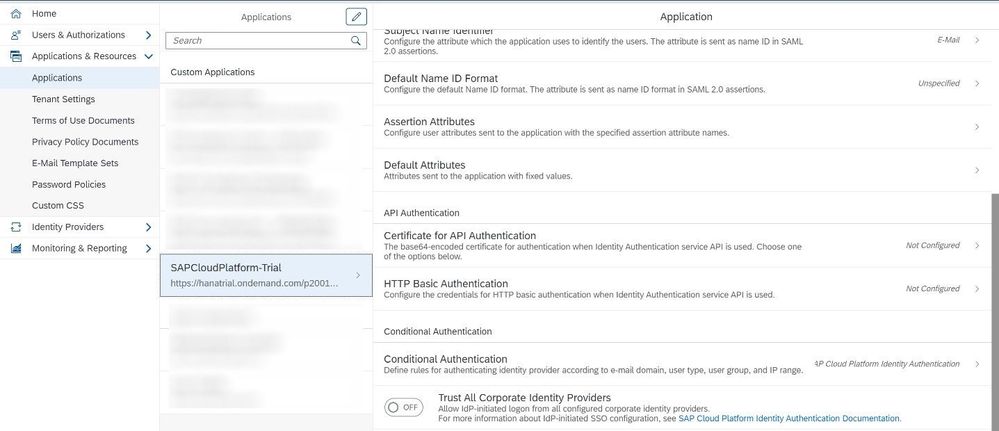
Back in the SAP Cloud Platform IAS go to the "SAP Cloud Platform - Trial" Application that we had created under Application & Resources -> Applications
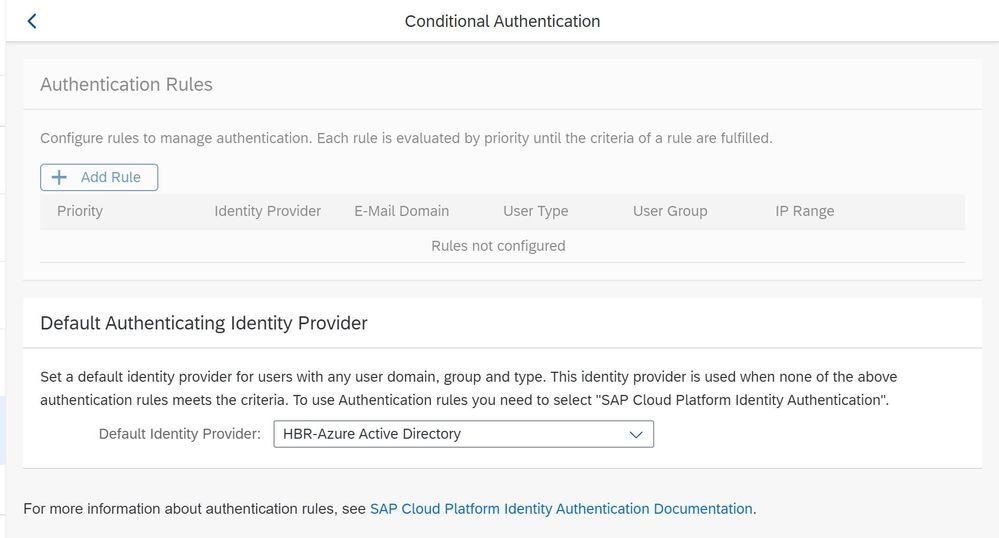
In the list of configurations select Conditional Authentication and change the authentication from SAP Cloud Platform Identity Authentication to the Azure Active Directory Identity Provider that we previously created.
Now, users that have access to the Application in Azure Active Directory and to the application on the SAP Cloud Platform can seamlessly access the application with their AAD credentials.
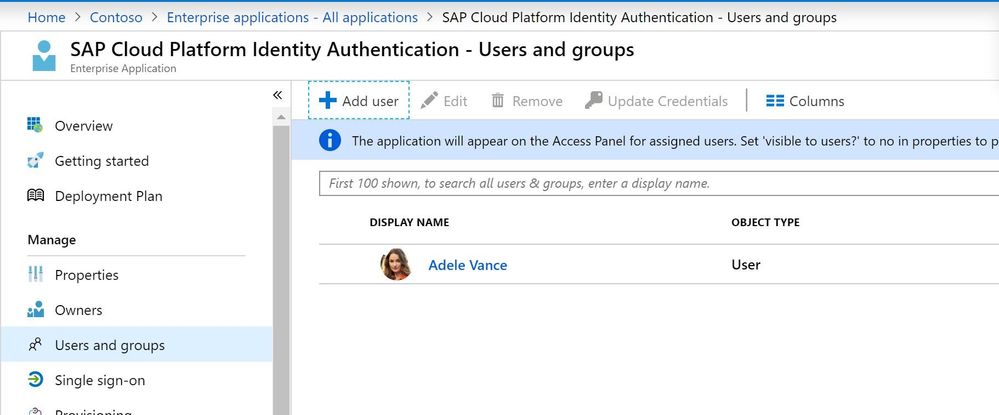
I will add one demo-user to my application in AAD. For this go back to the Azure Portal, select the Enterprise Application previously created for the SAP Cloud Platform and add the user
When I now open the Web DIE URL from before https://webidecp-<P-User>trial.dispatcher.hanatrial.ondemand.com/ I am redirected to an AAD authentication page, where I can log on with my assigned user.
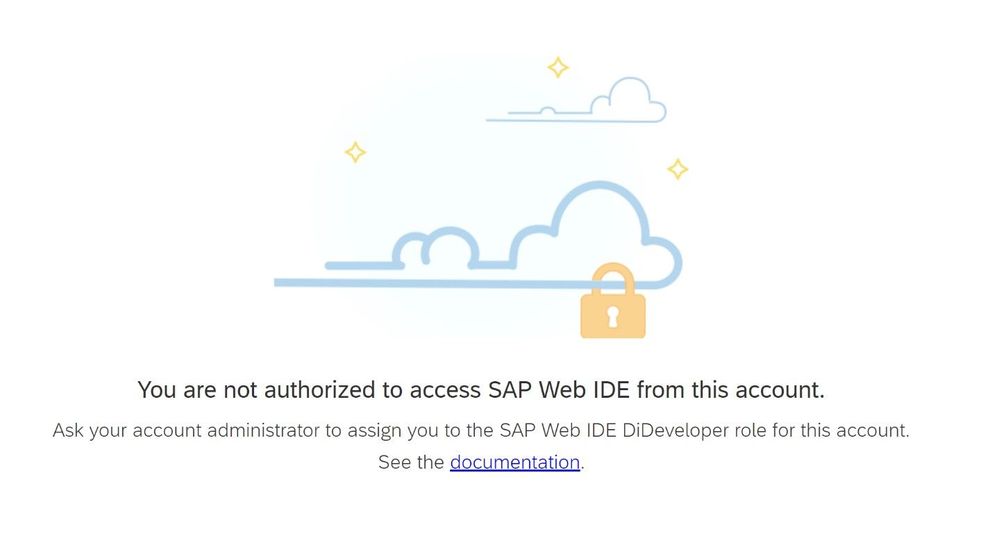
Still, when I enter the correct credentials I am still getting an authentication error.
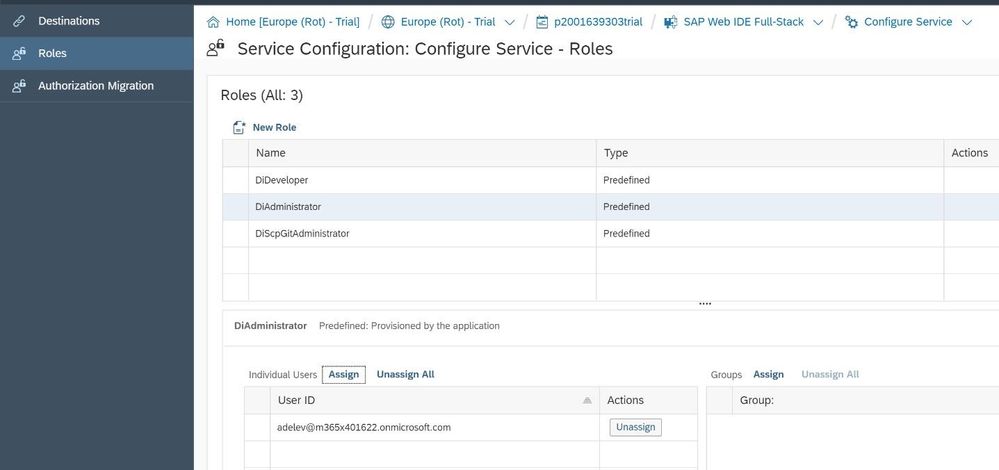
This is because I have not yet assigned this AAD user to a role that is allowed to user Web DIE. When I do this from the configuration screen of Web IDE,
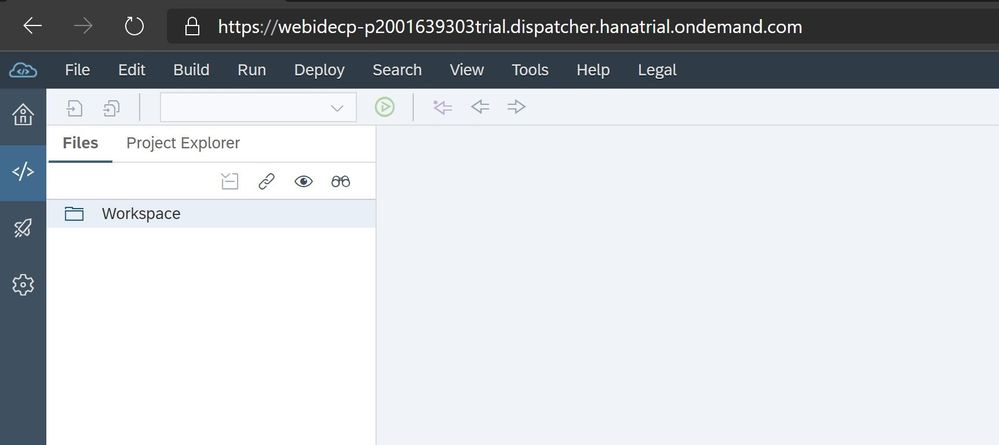
And I repeat the authentication steps, everything is working fine and I can access Web IDE
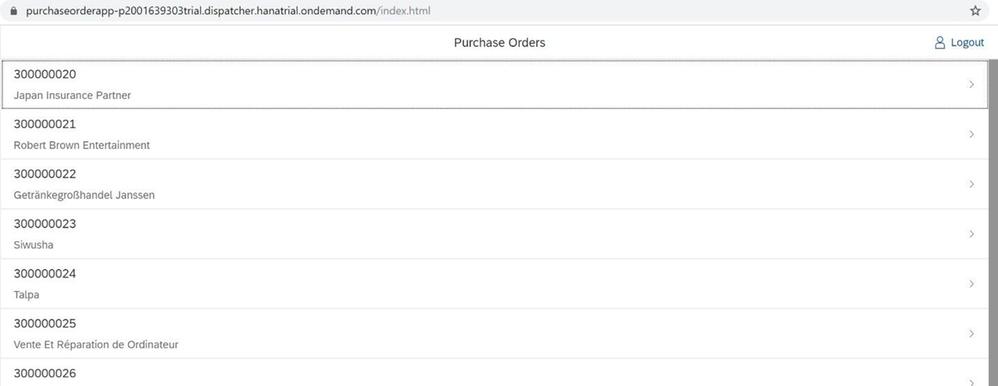
Now we are ready to call the Purchase Order application again (https://purchaseorderapp-<P-User>trial.dispatcher.hanatrial.ondemand.com).
As you remember originally you had to authenticate once using your SAP user, then again using the Microsoft user. See what's happening now. When you open the URL of the application you are redirected to authentication using your AAD credentials. Once that is done we retrieve the relevant tokens to access the Microsoft Graph in the background. So this time without any additional manual input you can access both data from SAP and from your Microsoft Emails.
I hope this blog helps you get started in enabling SSO between SAP Cloud Platform and Azure Active Directory. Once that is done integration scenarios are endless! Let me know how it works for you!
--