This post has been republished via RSS; it originally appeared at: Intune Customer Success articles.
This month we’ve released Windows Defender tamper protection management in Microsoft Intune!
Tamper protection is a new setting available in the Windows Security app which adds additional protections against change to key Windows Defender security features.
Enabling this feature prevents others (including malicious apps) from changing/disabling important protection features such as:
- Real-time protection, which is the core antimalware scanning feature of Microsoft Defender ATP next gen protection and should rarely, if ever, be disabled
- Cloud-delivered protection, which uses our cloud-based detection and prevention services to block never-before seen malware within seconds
- IOAV, which handles the detection of suspicious files from the Internet
- Behavior monitoring, which works with real-time protection to analyze and determine if active processes are behaving in a suspicious or malicious way and blocks them
The feature also prevents the deletion of security intelligence updates and the disabling of the entire antimalware solution.
Enterprise management of this feature via Intune requires an E5 license (such as those with a Microsoft Defender ATP license) and the device be MDM enrolled into Intune. The feature is available on Windows 10 1903 Enterprise devices, and we’re looking at backporting the feature to down level Windows clients later this year.
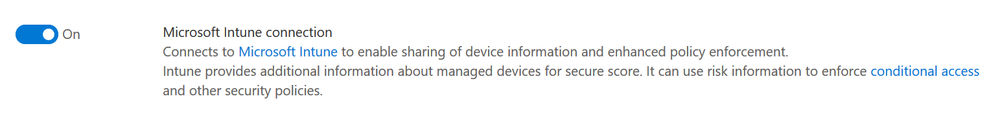
Before you can enable the setting, you need to connect Microsoft Defender ATP to Intune. To do this, browse to https://securitycenter.windows.com and visit Settings > Advanced features. Turn the Microsoft Intune connection on and press save.
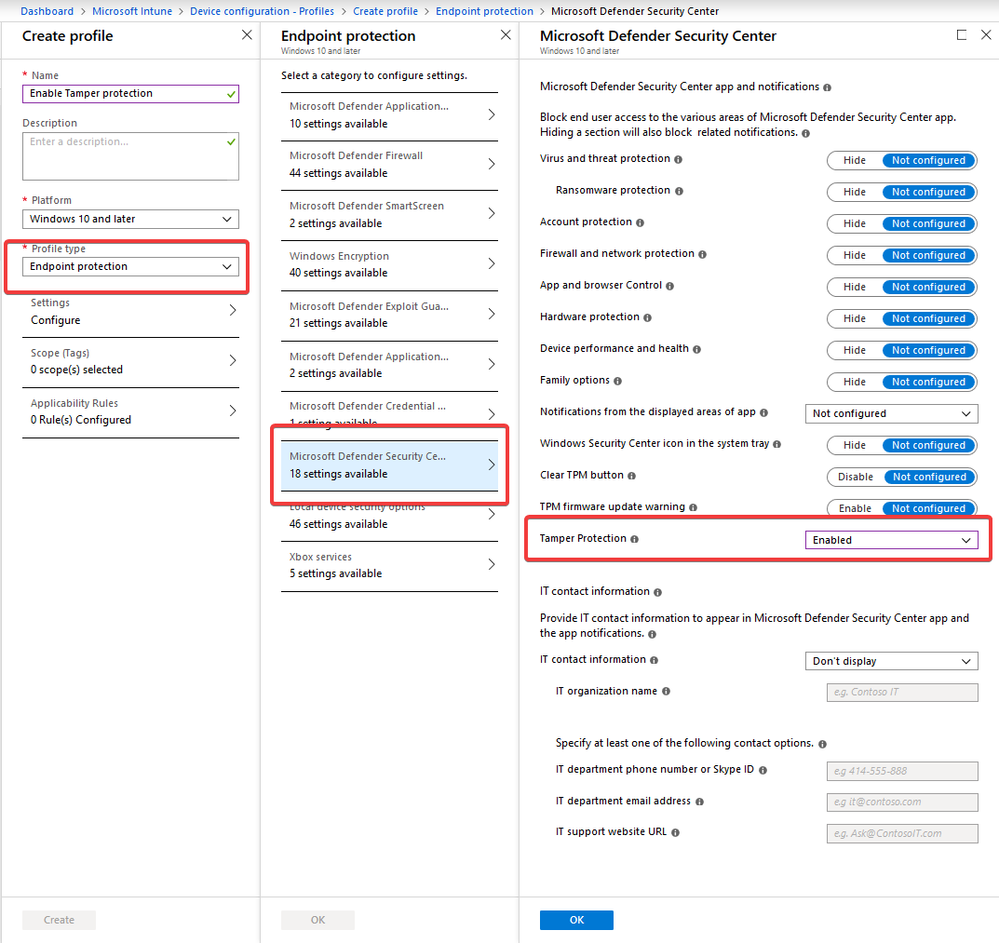
Next, browse to the Microsoft Intune console. To enable Windows Defender tamper protection, create an Endpoint Protection policy in Intune and enable the Tamper protection feature.
Assign this policy to a user or device group, and tamper protection will be enabled.
To disable the feature, change the setting to Disabled and deploy the policy to the target devices.
Note: Not configured will not change the state of a previously deployed configuration. To disable tamper protection, you must deploy a Disabled policy state.
For more information on the Windows Defender tamper protection feature, visit https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-antivirus/prevent-changes-to-security-settings-with-tamper-protection
Matt Shadbolt
Senior Program Manager
Microsoft Intune