This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
By James Grantham | Intune Sr. PM
Have you ever had a problem deploying policy to devices in Intune? Is there ever an application that you know should be on a device, that you can’t seem to get installed? As you already know – sometimes things do not go as expected for several reasons. Maybe a device was not connected to the internet to receive policy. Maybe the app failed to install because an end user uninstalled the app after it was installed. The point here is even when things are set up perfectly, sometimes there are things out of our control as administrators of the technology.
As the Troubleshooting Program Manager for Intune, I want to explain where we are today to bring awareness to troubleshooting capabilities. In addition, I’ll share improvements we are making. Through this dialog, I hope to give you a better idea of where we’re going in troubleshooting and provide a forum for you to voice your experience and feedback. For those who are attending Ignite this year – I’ll be there in person and looking for face-to-face in person feedback from this community.
Troubleshooting Blade Intent
Our customers tend to have a few simple questions we work towards answering. At a high level, my goal is that we successfully address these problems for you and empower you to self-remediate these types of issues as they are encountered:
- What is my current configuration?
- What is wrong?
- What happened?
- How do I fix it?
The Troubleshooting Blade
The Troubleshooting Blade (located under your favorites in the Device management admin portal as well as in the Azure Portal) was designed to give a helpdesk persona within your organization an “at a glance” view of one user at a time providing a snapshot of user configuration. Note that access to the blade is controlled through Role Based Access Control so that you can assign access to individual users in your organization and allow them to Troubleshoot, but perhaps not be policy creators/or configuration makers. This granularity was an intentional split as a helpdesk person who works to resolve issues for individual users and devices is not necessarily the same person that manages your entire environment.
The troubleshooting blade lets you look at the following areas today:
- User Selection
- Licensing & User information
- Groups & Messages
- Assignments
- Devices
- App Protection Status
- Enrollment Failures
Here’s what you can find and troubleshoot in each area.
User Selection
In this area:
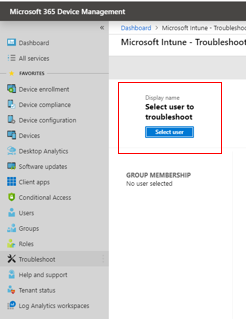
- The first thing you must do in the troubleshooting blade is select a user. Click the “Select user to troubleshoot” button to populate the rest of the page with information to help you troubleshoot issues.
Licensing & User Information
In this area:
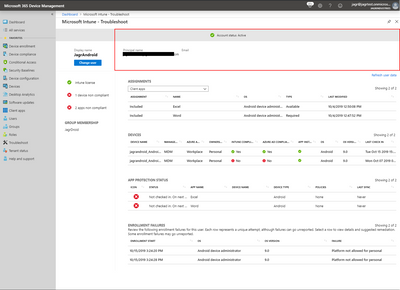
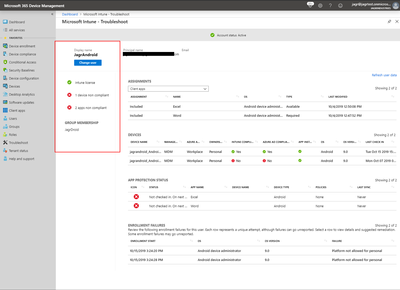
- If for any reason your account status has issue – we show you at the top, along with other important alert type information. We pair this with User principal name and email address for an at a glance view of information.
Groups & Messages
In this area:
- This shows current user selected, any alerts associated with the user after being selected, and group membership.
- This answers the question – what is wrong with this user?
- This view also answers the question – what groups is this user assigned to? This is very helpful when you’re trying to understand where policy under assignments area is coming from.
Icons Explained:
 |
Success |
 |
Warning |
 |
Error |
Assignments
In this area:
- This is meant to help answer the question – What policy is configured for this user?
- Assignments area shows client apps, Compliance policy, Configuration policy, App protection policy, Windows 10 update rings, and Enrollment Restrictions targeted at the user.
- You can change the view of assignments by clicking the drop down and picking from available assignments.
- With some areas picked (but not all) clicking on these items takes you to associated UX for more details.
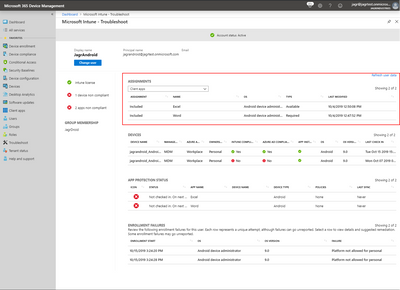
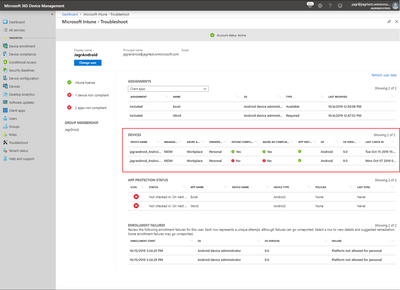
Devices
In this area:
- This is meant to help answer questions:
- Is my device Intune compliant?
- Is my device Azure AD compliant?
- Does my device have all required applications?
- Devices area also shows Devices enrolled by the user, Management types, Ownership, OS, OS version and last check-in. This is useful information for many different reasons.
- If you click a device in this view – it will take you to the Device view in Intune where you can explore the device in more detail.
Azure Active Directory and Intune Compliance Icons Explained:
 |
Compliance has been checked and device is compliant |
 |
Compliance has been checked and is not compliant |
Application Install Icons Explained:
 |
All required applications for device have been installed |
 |
Some required applications for device have not been installed |
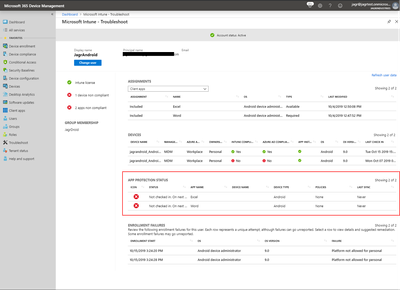
App Protection Status
In this area:
- App Name - Admin targeted this user for policy with this Application Name.
- Device Name/Device Type - The user has Application protection policies (also known as MAM) where the application (shown as App Name column) is installed from the device (shown as Device Name column). Device Name column would be blank if admin has targeted a policy for this user and app, but user has not yet enrolled (logged into the app the first time) to MAM from the app from any of the devices.
- Policies - Policy Names for policies that have been delivered to user's applications.
- Policies would state 'None' in case the user has not yet enrolled (signed into Application for the first time).
Icons Explained:
 |
Admin targeted this user for app (App Name) policy. The user has enrolled to MAM (app is installed) from device (Device Name) and the app has checked-in to service to receive policies. All targeted (admin intended) policies have been delivered to the app. Policy status is up-to-date. Status reads - Checked-in |
 |
Admin targeted this user for app (App Name) policy. The user has enrolled to MAM (app App Name is installed) from device (Device Name) and the app has checked-in to service to receive policies. Admin targeted user with more app policies after the app last checked in. On next check in, app will receive more policies. Status reads - Checked-in, On next sync, this app will receive <policy name> |
 |
Admin targeted this user for app (App Name) policy The user has not yet enrolled to MAM (app App Name might not be installed) from any device (Device Name is blank) Status reads - Not checked-in, On next sync, this app will receive one of more policies <policy name1>, <policy name 2>… based on the management level |
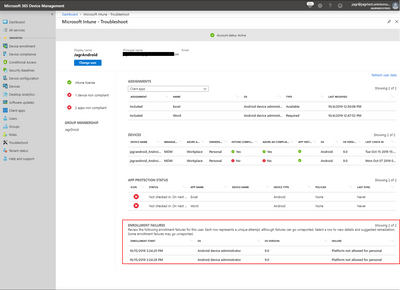
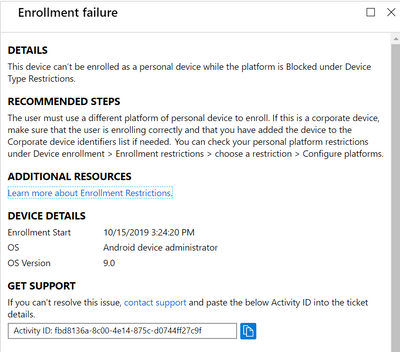
Enrollment Failures
In this area:
- This is meant to show what is wrong, what happened, and recommend how to fix it.
- Enrollment start shows time enrollment was attempted, OS shows enrollment method, OS version the OS version associated with update and failure.
- It is possible to see a failure, but since then successfully enrolled a device. If this is the case you can see a device listed under the “Devices” area that is in a healthy state.
You can click on individual failures to then see details about the failure and recommended steps to remediate:
Again, we do plan to follow-up with more in this series so if you’ve made it this far, let us know what questions or suggestions you have for our next one! And visit us at Ignite at the Intune booth.