Table level RBAC allows you to define more granular control to data in a Log Analytics workspace in addition to the other permissions is now available for Log analytics and for Azure sentinel.
Earlier this year, my colleague
His post shares in great detail the architecture and confederation for centralizing log analytics workspace vs multi workspaces in Sentinel and Azure security center.
On this blog post, we will review how the Table level RBAC lets you ingest your collected data into a centralize workspace and still keep your data segregate for a specific user or group.
Example use case
Contoso installed several Linux servers and wants to send their performance logs into Azure Sentinel workspace and enjoy Azure Sentinel advance Features.
The Contoso OPS team that manage the performance monitor workload in the organization need access only to the performance log table and not to Other sensitive data like the security events logs that store on the same workspace.
Configure RBAC table Level Access
To configure the RBAC table level access we need to:
- Define a RBAC custom role by creating custom JSON file that looks like this:
“Name”: “Contoso Performance Monitor Team”,
“Id”: null,
“IsCustom”: true,
“Description”: “Enable users to monitor Linux servers performance logs”,
“Actions”: [
“Microsoft.OperationalInsights/workspaces/read”,
“Microsoft.OperationalInsights/workspaces/query/read”,
“Microsoft.OperationalInsights/workspaces/query/Perf/read”
],
“NotActions”: [
],
“AssignableScopes”: [
“/subscriptions/8f153238-e602-xxxx-xxxx-3043fbe50918”
]
}
2. Add the custom role to our subscription, run the above PS command New-AzRoleDefinition and Point to the custom role JSON file from the preview step.
To run AZ PowerShell commands first install the AZ PS module
Name : Perf Monitor Team
Id : ab403341-d1f6-4cea-ae97-aea203b895a1
IsCustom : True
Description : Enable users to monitor Linux server performance logs
Actions : {Microsoft.OperationalInsights/workspaces/read, Microsoft.OperationalInsights/workspaces/query/read, Microsoft.OperationalInsights/workspaces/query/Perf/read}
NotActions : {}
DataActions : {}
NotDataActions : {}
AssignableScopes : {/subscriptions/8f153238-e602-427e-a7c0-xxxxxxx50918}
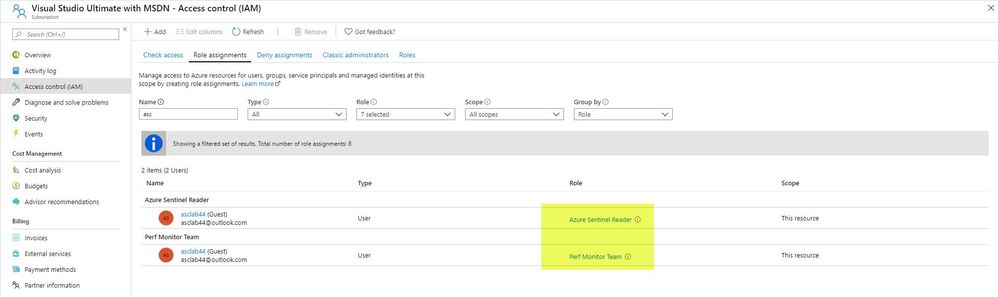
3. Add user that part of the OPs team to the new custom role and give him also Azure Sentinel Reader Built-in role at the subscription level:
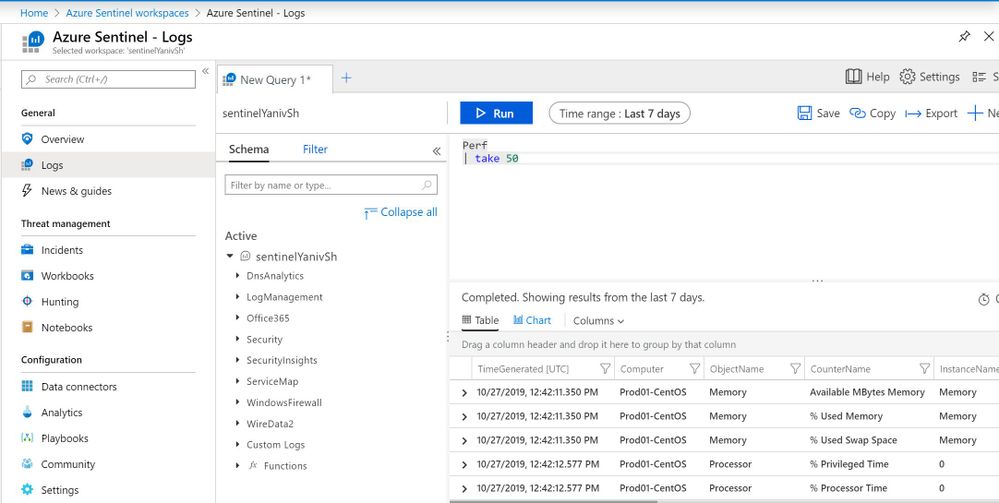
4. When Ops user opens Azure Sentinel logs tab and queires pref table he can retrieve the results:
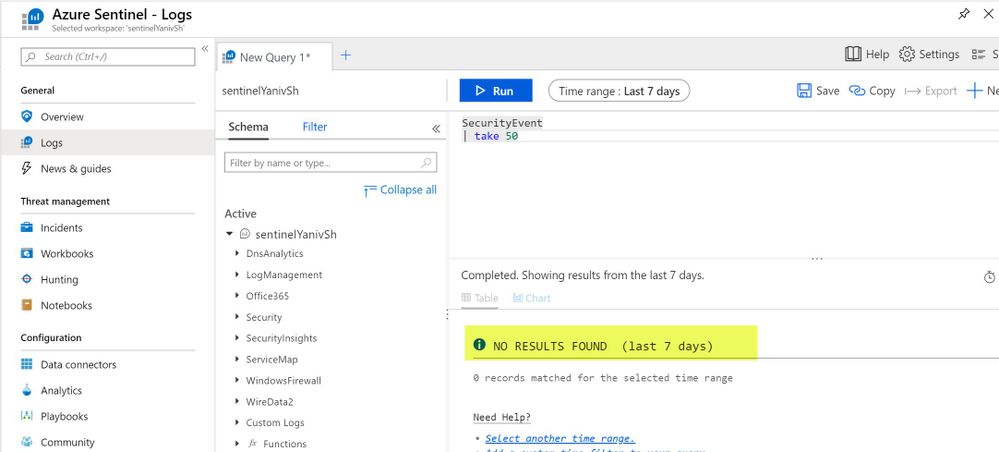
When the same user tries to query the SecurityEvent table or any other tables in Azure Sentinel workspace, no results found.
In this blog post, we reviewed the benefit of RBAC table permission and how to configure it in a real-Life scenario.
This feature can leverage Azure users to send their collected data to a centralize workspace and enjoy The advance analytic, hunting and ML and keep their data segregation.