This post has been republished via RSS; it originally appeared at: Core Infrastructure and Security Blog articles.
First published on MSDN on Nov 17, 2016This is the third part in a series dealing with basic configuration of commonly used management agents. In Part 1 we looked at configuration of an Active Directory Management Agent (ADMA), and in Part 2 we looked at the configuration of the FIM Service Management Agent (FIMMA). With this post, we’ll take a look at another common type, a MSFT SQL Management Agent (SQLMA).
Now we are going to create a management agent (MA) for Microsoft SQL Server. This type of MA may be used for any connected data source which utilizes Microsoft SQL Server as the underlying data system.
To begin, open the Synchronization Engine. In the right-hand menu, select “Create”.

For “Management agent for:”, select “SQL Server” from the drop-down list. Enter a name for this MA and click “Next” to continue.
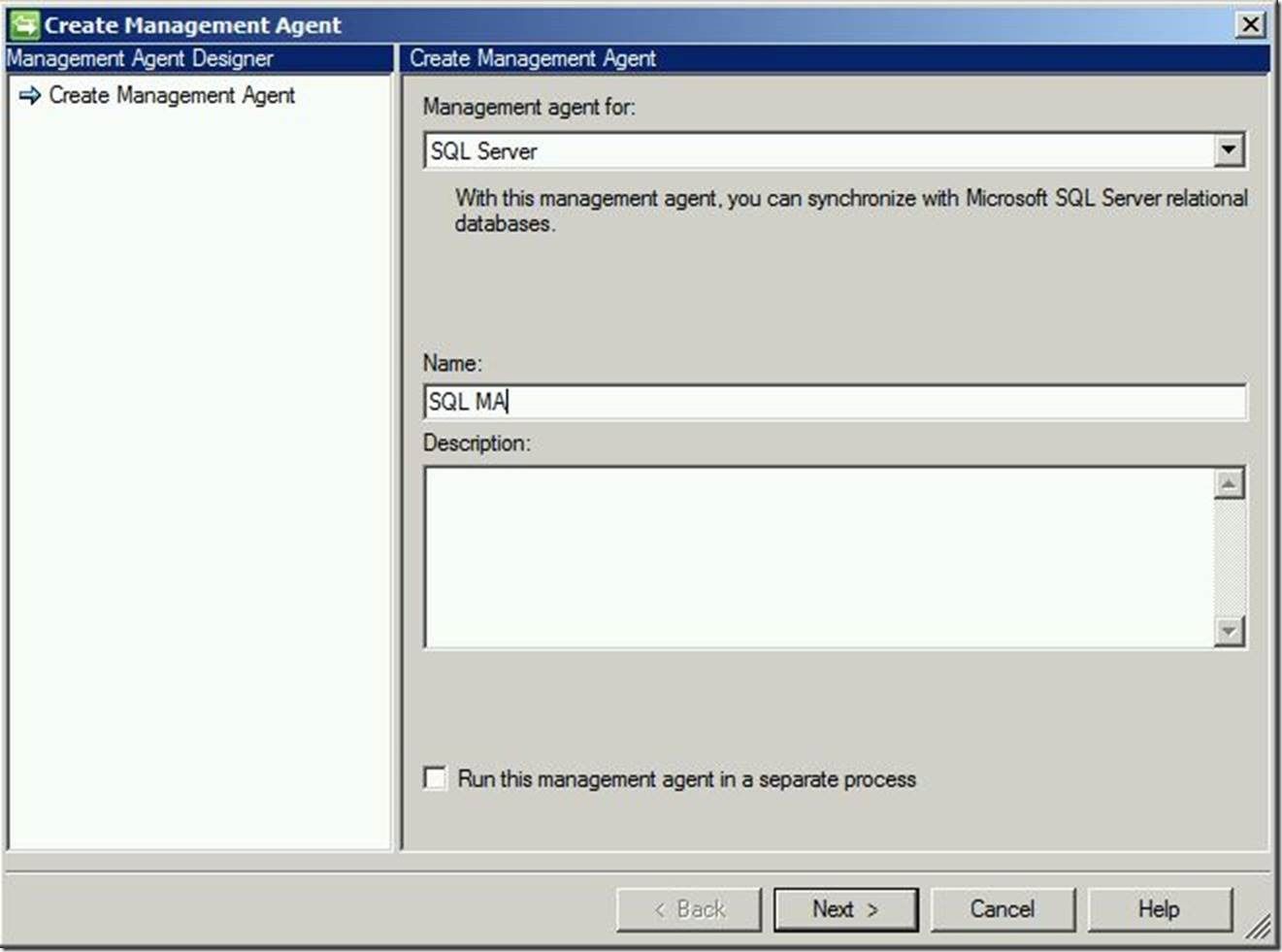
Next, enter the connection information for the server, database, connection/view and authentication, then click “Next” to continue.
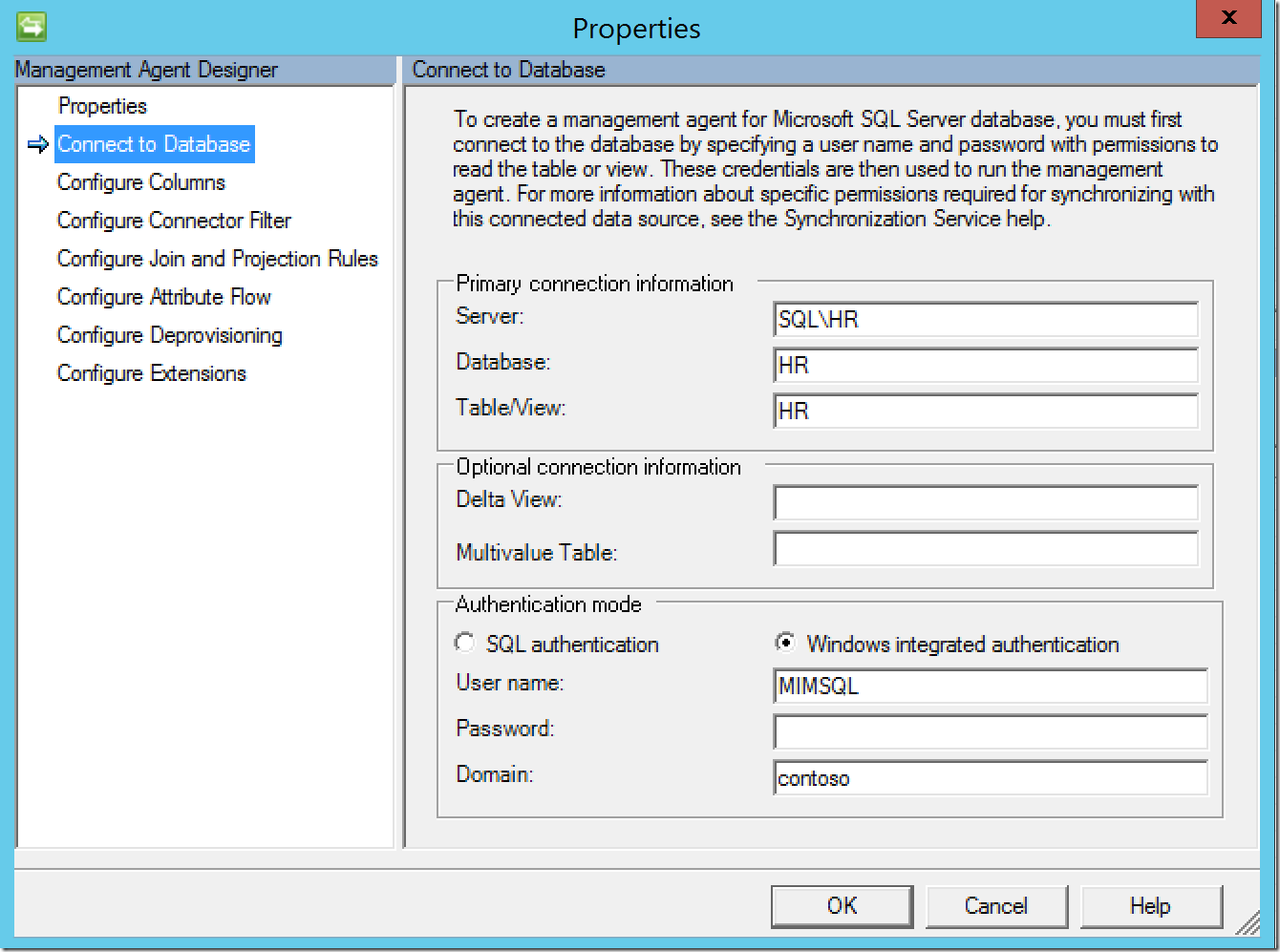
Once successfully authenticated to the database/table/view, the MA will pull in the column names automatically. Review that the data is correct, then click “Set Anchor…”. The anchor attribute value must be unique to each user object and exist in both the connected data source (in this case, Microsoft SQL Server) as well as the metaverse.
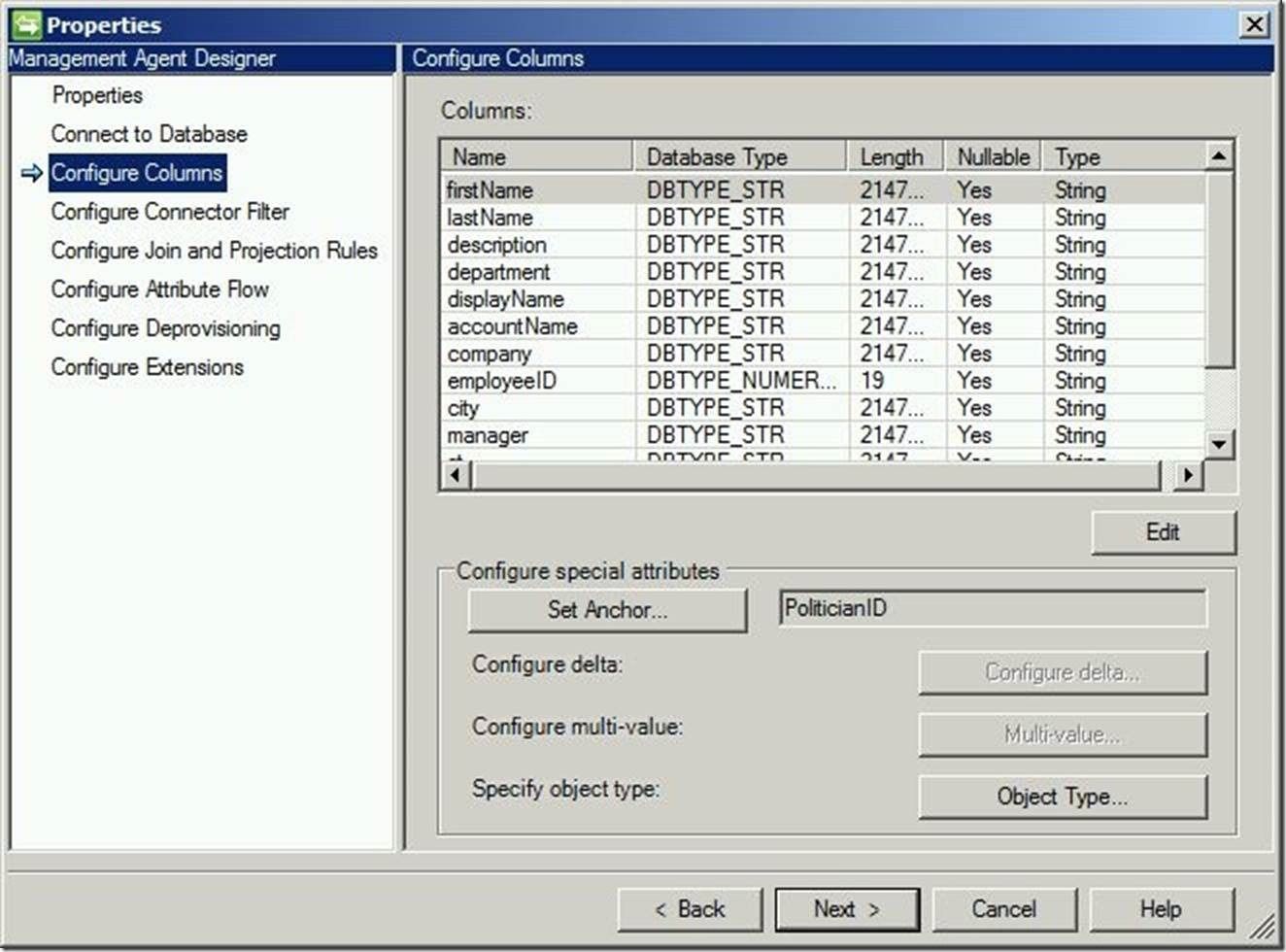
For “Configure Connector Filter”, the defaults may be used. Click “Next” to continue.
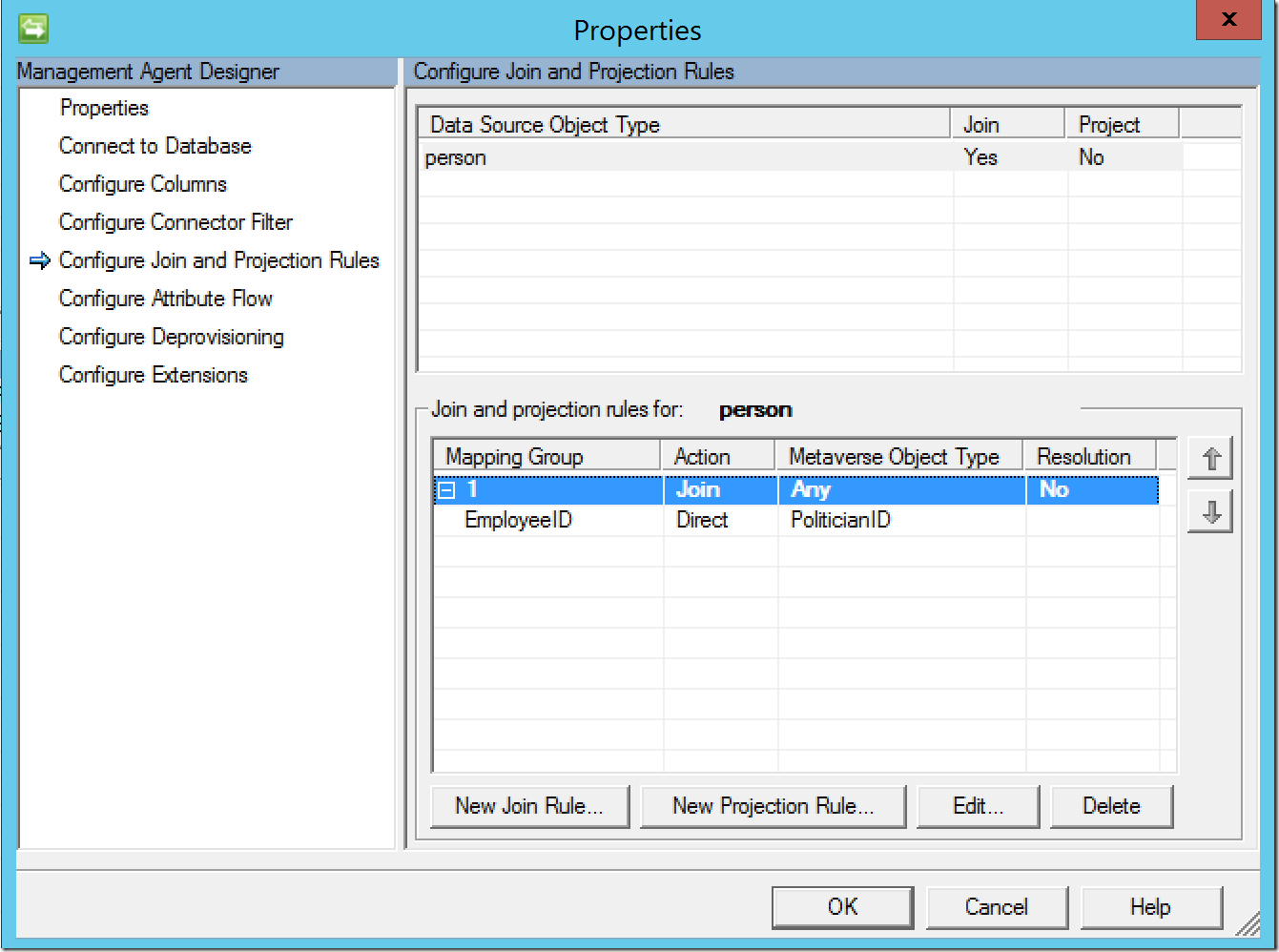
Now we must configure join rules. These rules will allow a user object in the connected data source to join its associated object in the metaverse, rather than creating another (duplicate) object. For a join to occur, the attribute in the join rule must be unique to each individual user object. Also, multiple joins rules can be created to assure a join occurs. In this scenario, joins are attempted between the “EmployeeID” and “PoliticianID” attributes. To create a join rule, click on “New Join Rule…”. Click “Next” when finished.
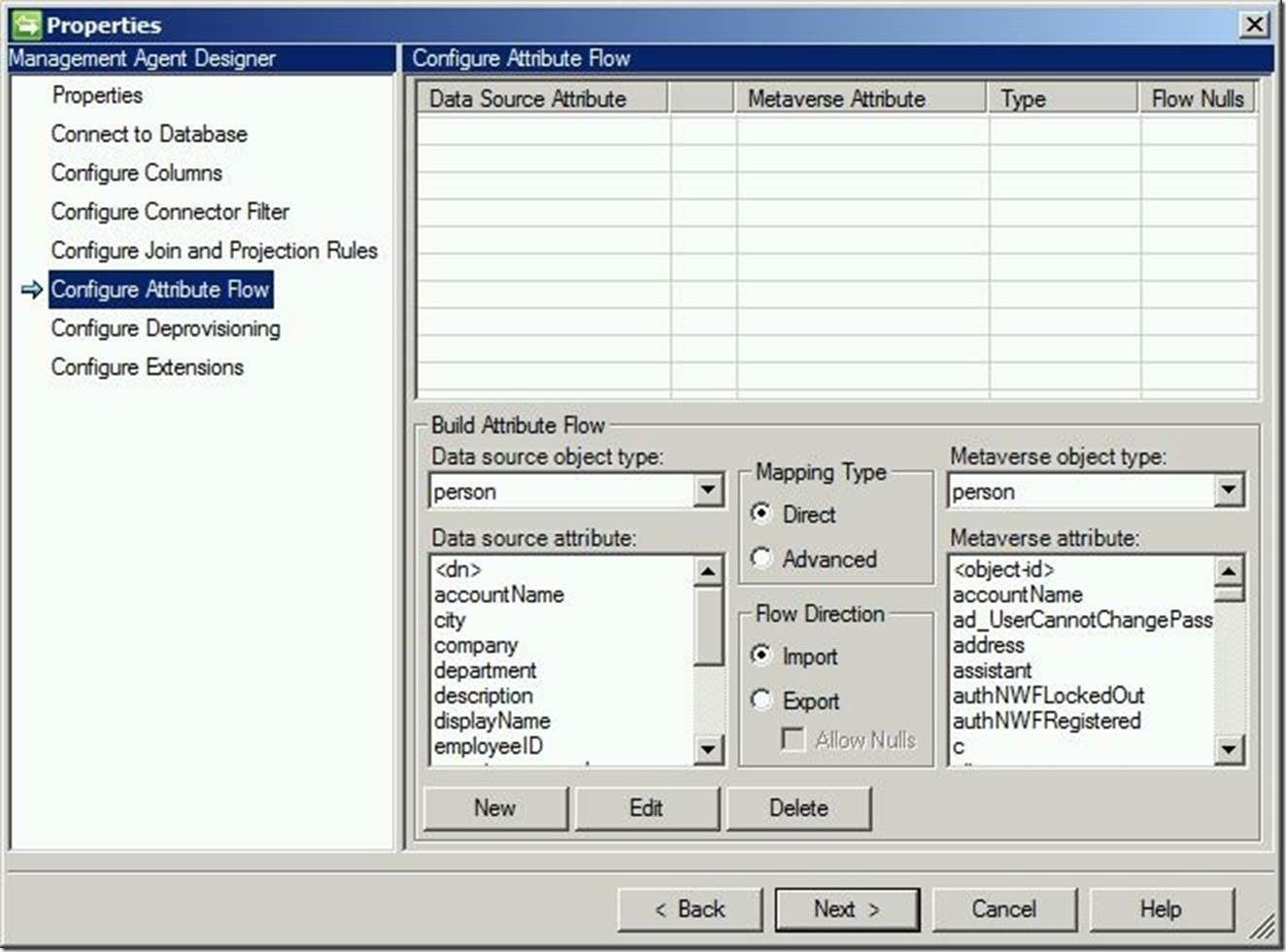
For “Configure Attribute Flow”, we may leave this default. Much like an ADMA, we want to put everything into FIM and then provision intelligently based on what we need. Click “Next” to continue.
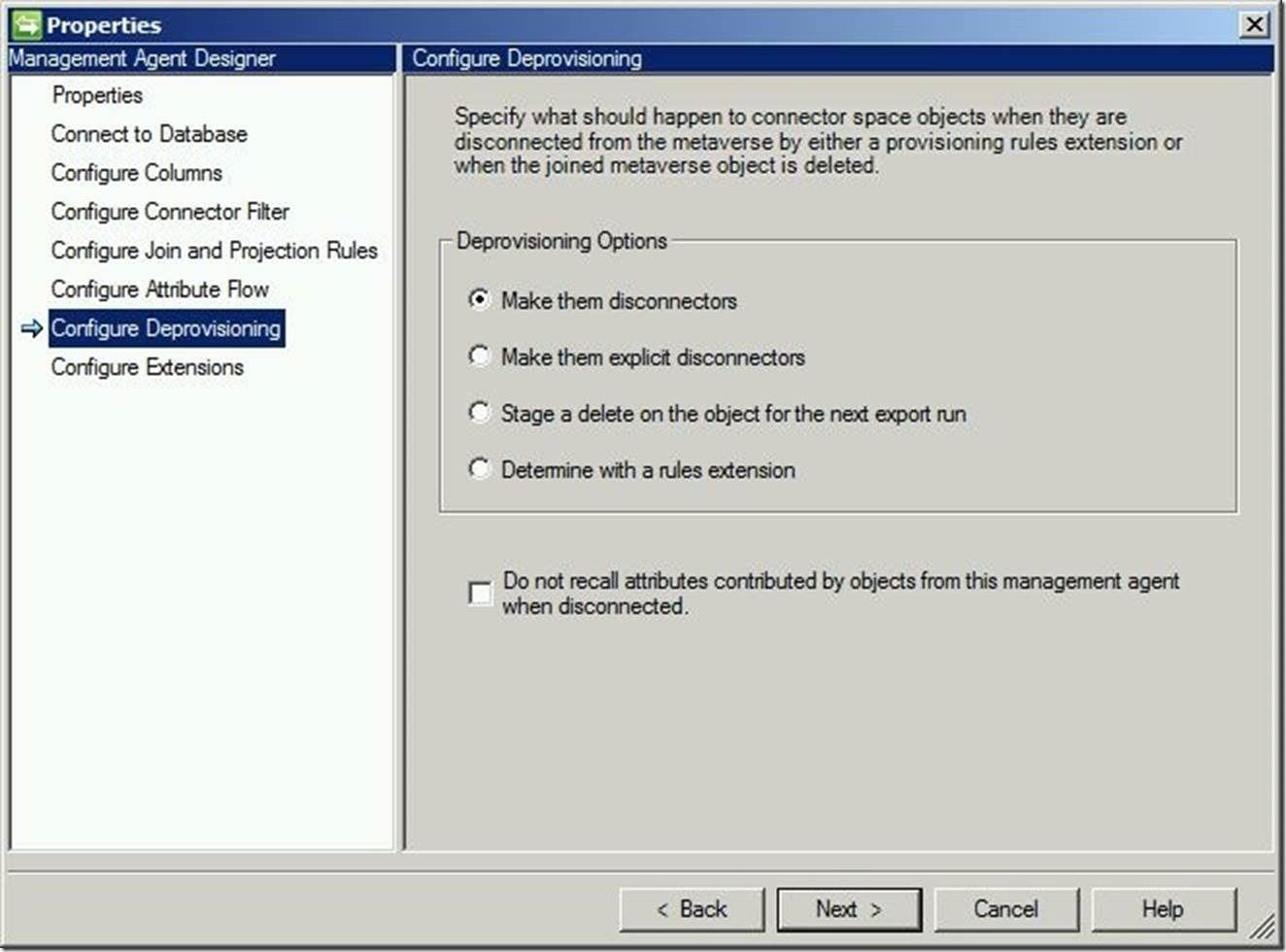
For “Configure Deprovisioning”, you may leave this default (to create disconnectors), or select accordingly based on your environment. Click “Next” to continue.
For an explanation of these options, please see this post for disconnections, this post for explicit disconnections and this post for deletions.
For “Configure Extensions”, we will leave this default.
Questions? Comments? Love FIM/MIM so much you can’t even stand it?
>WE WANT TO HEAR FROM YOU<
