This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
Microsoft Ignite is always an exciting event for us at Microsoft --for one whole week we make many important product announcements from different teams across the company. Here on the Microsoft Defender ATP team, we've been working on new, exciting capabilities for Threat and Vulnerability Management (TVM) that are designed to improve time to detection and remediation, integration across platforms, and automated user-impact analysis.
We're excited to announce the following new capabilities that will go into public preview this month:
- Vulnerability Assessment (VA) support for Windows Servers 2008 R2 and above
- Integration with ServiceNow for improved IT/Security communication
- Advanced hunting across vulnerabilities and security alerts
- Role-based access controls (RBAC) for teams focusing on vulnerability management
- Automated user-impact analysis
Vulnerability Assessment (VA) support for Windows Server 2008 R2 and later
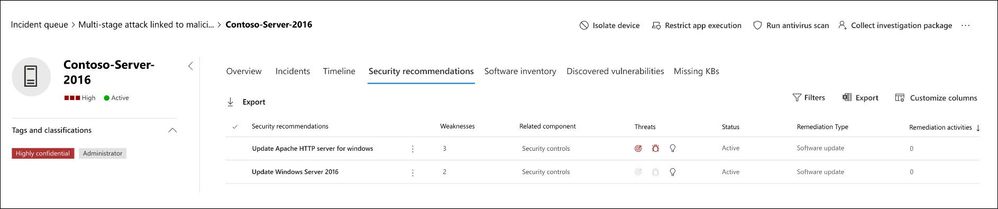
Effectively identifying, assessing, and remediating endpoint weaknesses is pivotal in running a healthy security program and reducing organizational risk. Threat and Vulnerability Management already does this for Windows 10 endpoints today, but when it comes to vulnerability detection and remediation, servers are just as important.
We're extending our vulnerability assessment capabilities to cover Windows Servers 2008 R2, 2012 R2, 2016, and 2019. With this expansion, customers can now discover, prioritize and remediate Windows server vulnerabilities across the entire stack, including OS components, Microsoft apps, and third-party software.
Integration with ServiceNow for improved communication and a transparent remediation process across teams
Effective communication between security and IT teams is key to reducing the time to mitigate vulnerabilities and to improve the overall security posture. With TVM, we introduced the unique ability to open security tasks for the IT team in Microsoft Intune via a one-click remediation request. We're extending this capability to natively support the ticketing system, ServiceNow.
With this new integration, the security team can open change management tickets in ServiceNow directly from the Microsoft Defender Security Center to ask the IT team to remediate vulnerabilities and misconfigurations.
Advanced hunting with vulnerability data
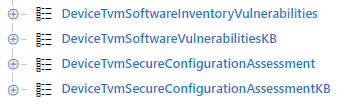
Rich vulnerability data can now be queried through advanced hunting capabilities, providing customers extensive flexibility in slicing and dicing vulnerability and misconfiguration data. Four new data schemata have been added to give customers the entities necessary for advanced hunting queries around vulnerabilities and misconfiguration: Vulnerability, Software, Recommendation, and Score. This also allows customers to correlate vulnerability data with endpoint detection and response (EDR) signals to create unique security insights.
Want to know which machines have a critical vulnerability with a public exploit, or with the firewall or AV disabled? Want to view all machines that have a critical vulnerability with an associated active alert? Interested in seeing the top five most vulnerable applications installed across the organization? These and more can now be easily done, and can even be plugged into customized PowerBI dashboards.
Role-based access controls (RBAC) for teams focusing on vulnerability management
The duty of mitigating vulnerabilities and reducing the risk of the organization is often split between multiple teams, and each of these teams needs access to different tools, data and insights. With Microsoft Defender ATP we provide all security teams across the organization with a single console for better correlation and insights. This comes with the need to allow individual teams to only see certain data or perform certain tasks. Now you can do that, and more!
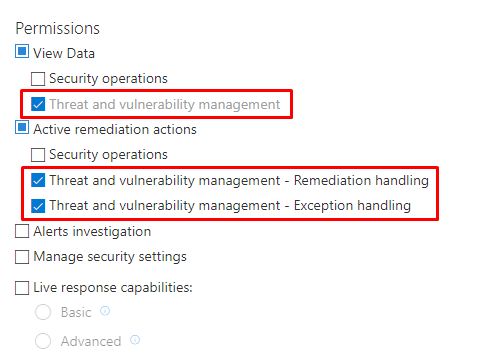
We have enriched the Microsoft Defender ATP role-based access model with new TVM permissions that allow customers to specify which data can be viewed and what actions can be performed for different roles.
This new addition provides you maximum flexibility to create SecOps-oriented roles, TVM-oriented roles, or hybrid roles so only authorized users are accessing specific data to perform their task. In addition, customers can achieve even further granularity by specifying whether a TVM role can only view vulnerability-related data, or also create and manage remediation and exceptions.
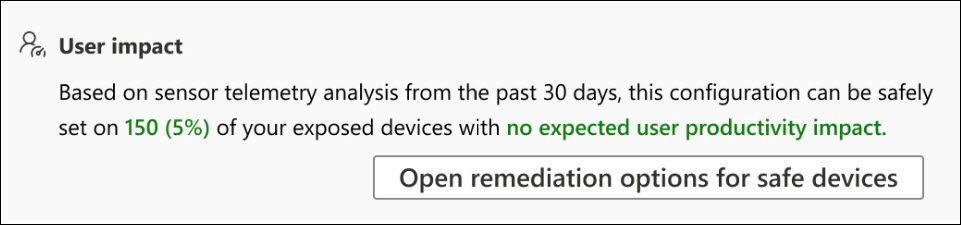
Automated user-impact analysis
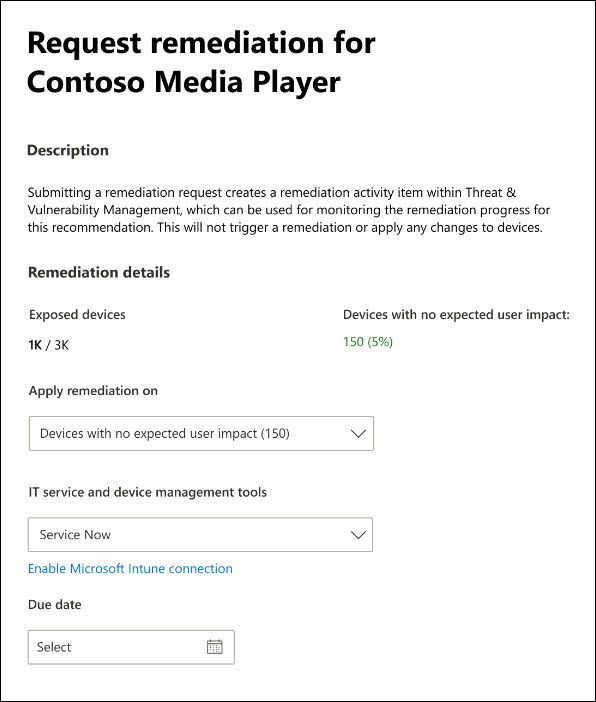
Understanding the potential impact of applying software patches or changing configurations on endpoints to user productivity (for example, enabling an attack surface reduction (ASR) rule) is vital information for both Security and IT administrators to avoid breaking critical user and business processes.
Through new intelligent data cloud analysis of signals from the past 30 days, Microsoft Defender ATP can now automatically determine which machines are considered safe for configuration change without impacting user productivity.
We're not only providing these insights as part of the TVM security recommendation, we also incorporated a seamless way to initiate remediation requests only for machines that are considered safe.
Insights on user impact will be initially available for TVM security recommendations related to ASR rules and will gradually be extended to additional security recommendation categories.
All these new capabilities continue to make Microsoft Defender ATP's Threat & Vulnerability Management a unique, game-changing solution. These capabilities are going to be available for you to try out in the coming weeks. You can follow our Twitter account to stay up to date. As always, please share your feedback with us in the comment section below or use the feedback mechanism in Microsoft Defender Security Center.