This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
Howdy folks,
Next up from our Ignite news, I’m thrilled to announce the general availability of the refreshed Azure AD Identity Protection with new detections and capabilities! This is a huge step forward across all of our UEBA capabilities with more and enhanced signals, massively improved APIs for integration with your SOC environments, a new user interface that makes you more efficient!
Rajat Luthra led the effort for this work, so here are the details from him! Please let us know what you think in the comments below. We look forward to hearing from you!
Best regards,
Alex Simons (@Alex_A_Simons)
Corporate VP of Program Management
Microsoft Identity Division
.........................................................................................................
Hi everyone!
I’m super excited to share with you how the refreshed Azure AD Identity Protection helps you better protect your identities. The general availability of the refreshed Azure AD Identity Protection represents a huge collaborative effort across numerous teams and many customers gave us valuable feedback throughout the process!
Azure AD Identity Protection helps organizations detect and prevent identity risk through advanced risk insights and automated risk-based policies.
Last January, we announced the public preview of the refreshed Azure AD Identity Protection. Today, the following capabilities are now generally available:
- An intuitive and integrated UX—Under a new dedicated Security menu, the refreshed Identity Protection provides a risk dashboard with insights, history, and advanced reports.
- Integration across Microsoft ecosystem—Products such as Azure AD, Microsoft Cloud App Security, and Azure Advanced Threat Protection (ATP) are better connected with shared risk intelligence for a comprehensive risk assessment.
- New detections—Several new detections in Identity Protection are available with this release.
- Powerful APIs—Information accessible to you via the UI is also programmatically accessible via powerful Microsoft Graph APIs supporting advanced scenarios and simplifying your ticketing or SIEM system integration.
- Improved risk assessment—Major enhancements in our risk engines, improved existing detections, and added capabilities to ingest your risk feedback.
- Service wide alignment—Alignment across key entities such as risky users, risky sign-ins, and risk detections.
Let’s dig into each of the above capabilities:
Intuitive and integrated UX
The new UX gets you quick access to the needed risk information.
Dedicated menu for all Azure AD security features and Identity Protection—You can now find all Azure AD security features under the new Security menu, including Identity Protection. You can search for security features in the Azure Portal search without needing to know the exact feature name. For example, a search for “banned passwords” will point you to “Azure AD Password protection.”
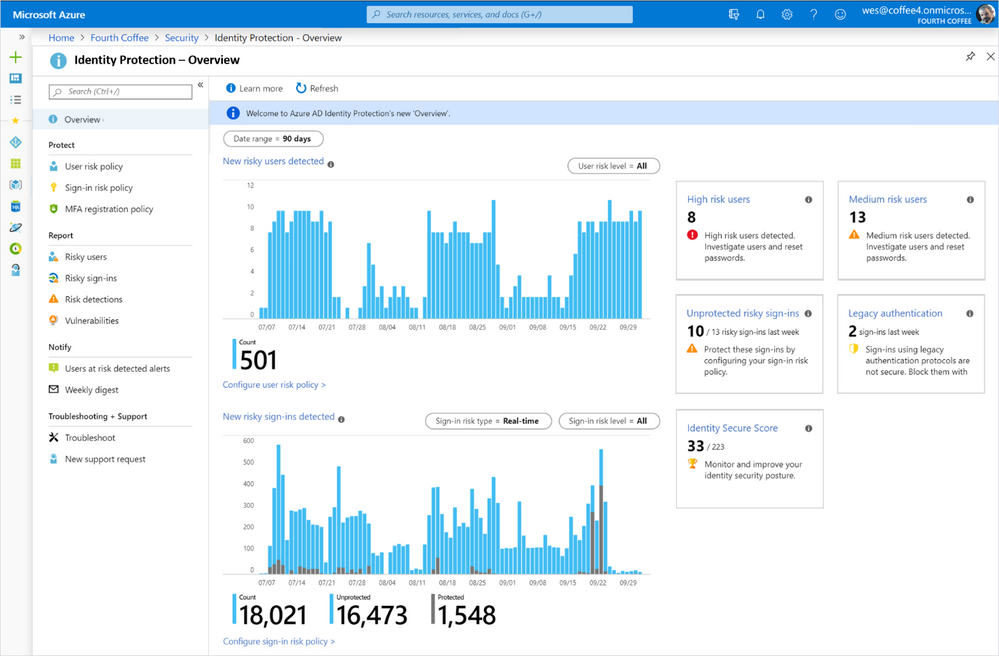
Identity Protection: Overview—Overview (report, docs) provides summary of identity risk in your organization. The risk trends help you spot attacks and understand effectiveness of your policies. The tiles call out key issues.
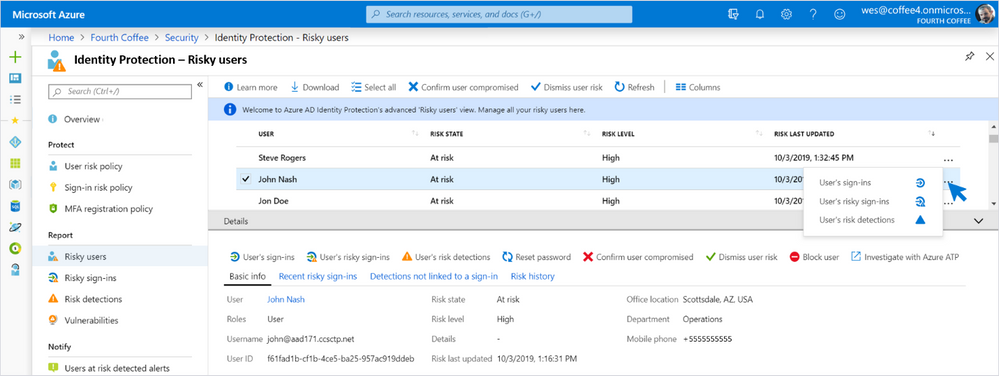
Identity Protection: Risky users—Risky users (report, docs) allows management of your Azure AD risky users by showing which users are most risky and why. In addition to blocking users, you can elevate, remediate, or dismiss their risk. A single click allows you to investigate users with Azure ATP. And thanks to your feedback, you now have access to full user risk history (via the UX and APIs).
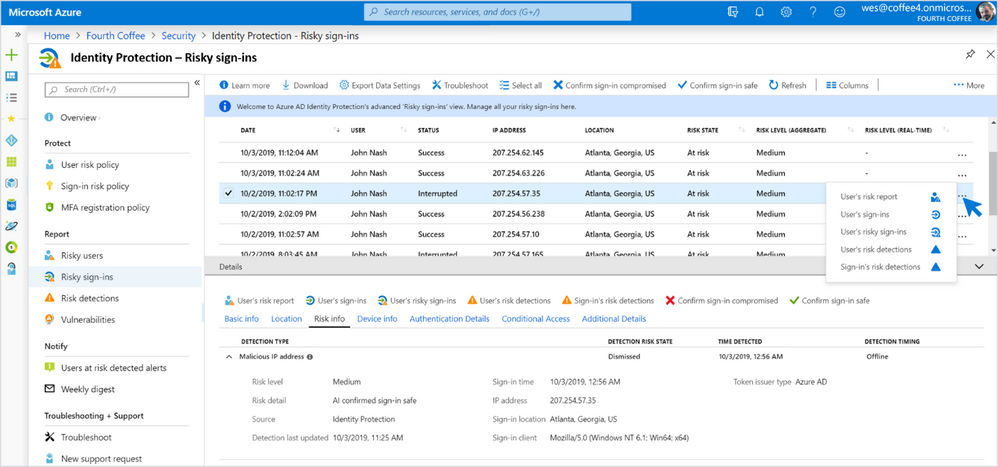
Identity Protection: Risky sign-ins—Risky sign-ins (report, docs) enables management of all your Azure AD risky sign-ins by showing which sign-ins are most risky and why. You can filter risky sign-ins by user, IP, status, location, risk levels, or detections most relevant to you.
Identity Protection: Risk detections—Risk detections (report, docs) enables management of all your Azure AD risk detections. You can filter detections by type, risk levels, timing (real-time/offline) or source.
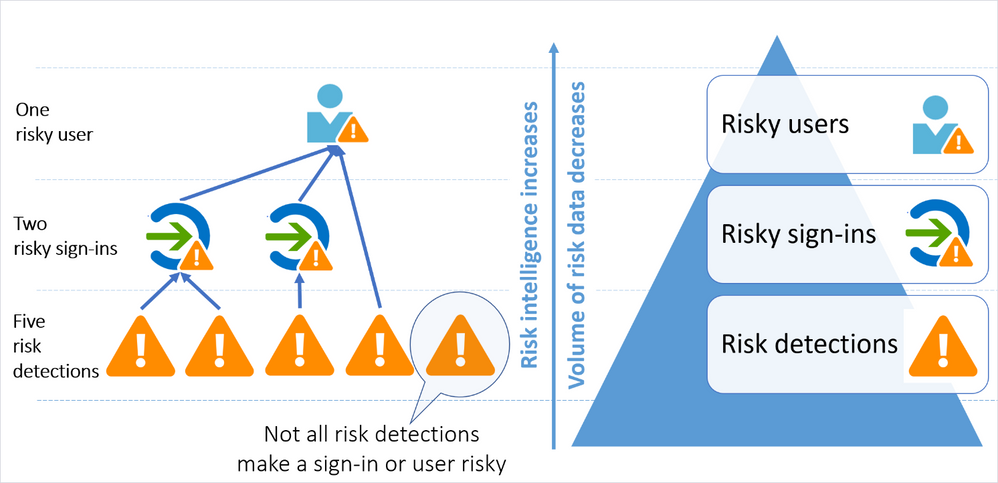
Simplified risk structure—Here’s how risk is assessed in your organization:
- A user is considered risky because the user had one or more risky sign-ins, or had risk detections not linked to any sign-ins (for example, leaked credentials).
- A sign-in is considered risky because the sign-in had one or more risk detections (for example, anonymous IP address).
Note: Identity Protection’s machine learning automatically filters out some detections during user and sign-in risk assessment. For example, even though a café may have seen many malware infected devices, your sign-in (or identity) there may not be at risk. In this case, the detection Malware infected IP address will be issued, but the machine learning may ignore it and the sign-in or the user won’t be considered risky.
Ability to provide feedback on Identity Protection’s risk assessment—You can now give Azure AD feedback on Identity Protection’s risk assessment. The system leverages this feedback and improves the current and future risk assessment across Azure AD. To learn how to provide Azure AD risk feedback, see the article How to give risk feedback in Azure AD.
Integration across Microsoft ecosystem
Azure AD Identity Protection now connects across Microsoft ecosystem to give you greater control over sessions through automated and manual responses with the following new capabilities:
- Azure AD Identity Protection allows you to investigate risky users in Azure ATP.
- Azure ATP shows Identity Protection detections for a comprehensive Security Operations experience. It shows Identity Protection’s user risk assessment and allows Security Operations to confirm users compromised in Identity Protection from the Azure ATP console.
- Azure Sentinel surfaces Identity Protection’s risk data in addition to the other Azure AD data.
New detections
We’re also releasing three new detections and significantly improving one existing detection.
|
# |
Detection type |
Summary |
State |
|
1 |
Unfamiliar sign-in properties |
Sign-in with properties we have not seen recently for the given user. |
|
|
2 |
Azure AD threat intelligence |
Indicates compromises detected by Microsoft investigations team. |
New (docs) |
|
3 |
Malicious IP address |
Sign-in from an IP address known to be malicious around the time of sign-in. |
New (docs) |
|
4 |
Admin confirmed user compromised |
Injected when identity admins confirm a user compromised in Risky users report or API. |
New (docs) |
For a complete list of Azure AD Identity Protection’s detections, see the article Azure AD Identity Protection risk detections.
Powerful APIs
The data in the three layers of the above pyramid is now accessible to you via Microsoft Graph APIs (Risky users API, Sign-ins API, Risk detections API), so you can route Identity Protection’s risk data into your SIEM, storage, tracking or alerting system.
Note: Risk detections API will replace the existing, beta Identity Risk Events API by providing you finer controls to consume Identity Protection detections. If you are using the beta Identity Risk Events API, we recommend moving to the new Risk detections API.
Improved risk assessment
The UX, new detections, integrations, and APIs above are just the tip of the iceberg. Under the hood, we significantly improved our risk assessment. Now your risk policies are more effective at stopping the bad actors.
Improved: Sign-in risk (real-time)—This is the risk assessment at the authentication time, using Azure AD’s behavioral analytics and threat intelligence-based detections. We recently improved our real-time detections (blog) to more accurately assess, in real-time, the probability a sign-in is compromised. This acts as a condition for your sign-in risk-based policies.
Improved: Sign-in risk (aggregate)—This considers all the malicious activity detected on a sign-in, thereby enabling you to focus on the highest risk sign-ins. This risk assessment computes probability a sign-in is compromised using machine learning to combine real-time detections (detections triggered during the authentication), offline detections (detections triggered minutes after the authentication), detections made across Microsoft ecosystem (for example, Microsoft Cloud App Security), and other sign-in properties.
Improved: User risk—The user risk represents the probability of a user's account being compromised. This risk level is computed using improved machine learning that considers the past risk activity of the user, detections not linked to any sign-in, and admin feedback.
Service wide alignment
After listening to our customers, we designed the entire experience across three key entities—risky users, risky sign-ins, and risk detections. Before you roll out a new risk policy, you can understand what’s going on for your users by using the options to move across these three entities.
| Entity | Automated policies? | Advanced reports? | Public API? | Enhanced risk intel? | Admin feedback enabled? | Linked to other entitles? |
| Risky users |
✓ |
✓ Risky users |
✓ |
✓ | ✓ | ✓ |
| Risky sign-ins |
✓ Sign-in risk policy |
✓ Risky sign-ins |
✓ |
✓ | ✓ | ✓ |
| Risk Detections | - |
✓ Risk detections |
✓ |
✓ | - | ✓ |
Next steps
Use the refreshed Azure AD Identity Protection, try out the powerful new APIs, or checkout the new public docs. We would love to hear your experience via the in-product feedback.
Thanks!
Rajat Luthra (@_LuthraRajat)
Senior Program Manager
Identity Security & Protection, Microsoft
