This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
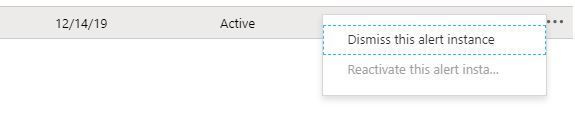
In Azure Security Center you have the capability to dismiss an alert, which basically hides the alert from the security alert dashboard. Notice that when you do this, you are only dismissing that particular instance of the alert, as shown in the floating menu that opens up:
Future alerts that are based on the same category, will continue to be surfaced in Security Alerts dashboard. So, don’t confuse dismiss, with “set as false positive”, which is a capability that is not available at this moment.
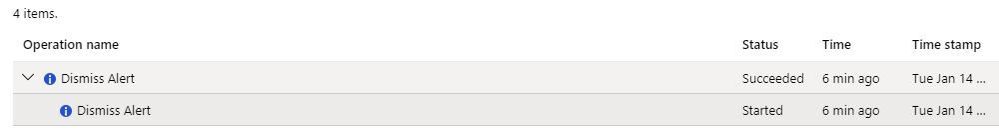
Recently the question that I received it was: how do I know which used dismissed an alert? The answer is: using Azure Activity Log. This information is logged in the activity log, as shown in the example below:
When you open this activity log, and click in the JSON, you will see all the details about the operation, and who (user) started. The only caveat is that the activity log doesn’t show the alert name, it shows the Alert ID, as shown the bold text below:
resourceId": "/subscriptions/XXXXXXXXXXX/providers/Microsoft.Security/locations/centralus/alerts/2518258566592429999_dcc4c3d0-b41c-428f-9c12-d49c0604fcab"
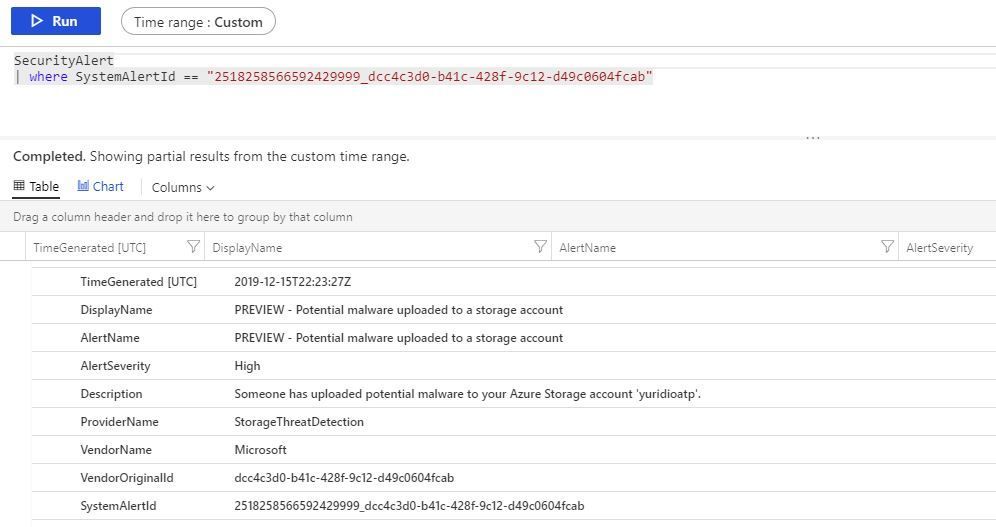
To correlate the AlertID with the alert name that appears in the dashboard, you can open Log Analytics workspace, and perform the following query:
SecurityAlert
| where SystemAlertId == <AlertID>
Below you have a sample result:
Now you have both information: the alert name and who dismissed that alert.