This post has been republished via RSS; it originally appeared at: Azure Active Directory Identity Blog articles.
Howdy folks,
Today, I’m super excited to announce the public preview of Conditional Access for the Office 365 suite. For organizations setting policy on Office 365—such as requiring users to perform Multi-Factor Authentication (MFA) or have managed devices—of Conditional Access for the Office 365 suite makes the configuration a whole lot easier.
Hundreds of millions of people use the Office 365 apps like SharePoint Online, Exchange Online, and Microsoft Teams. Part of what makes these services work so well is they interact with each other and a have a collection of supporting services. There are tons of benefits of integration—one example is shared contact information in Exchange for SharePoint and Teams. In many ways, even though Office 365 is composed of many cooperating services, it functions as a single app to help your users be productive.
Conditional Access can be used to protect all Azure AD connected apps, including thousands of pre-integrated SaaS apps, apps your organization has developed, as well as hybrid apps accessed through the Azure Application Proxy. However, because of the close relationship between Office services it makes sense to help you target Office 365 as a single app with Azure AD Conditional Access policies. Many of you have asked for this capability, and we worked with several customers to make sure we got the feature right.
Conditional Access for the Office 365 suite gives admins the option to assign policy across Office 365 with one click. It provides consistent coverage and improves the user experience by setting a consistent policy across Office 365 apps. Assigning different policies to different services can result in unexpected interrupts as users access data that requires service to service interaction. To learn more about this topic, see our Conditional Access service dependencies documentation.
You can also enforce policy to apps that aren’t available in the Conditional Access app list, like the Office.com portal. See the complete list of individual apps included in the Conditional Access for the Office 365 suite. We’ll add new Office apps as they’re released, and your policies will be automatically applied.
How Conditional Access for the Office 365 suite works
Let’s take a closer look at how to use Conditional Access for the Office 365 suite.
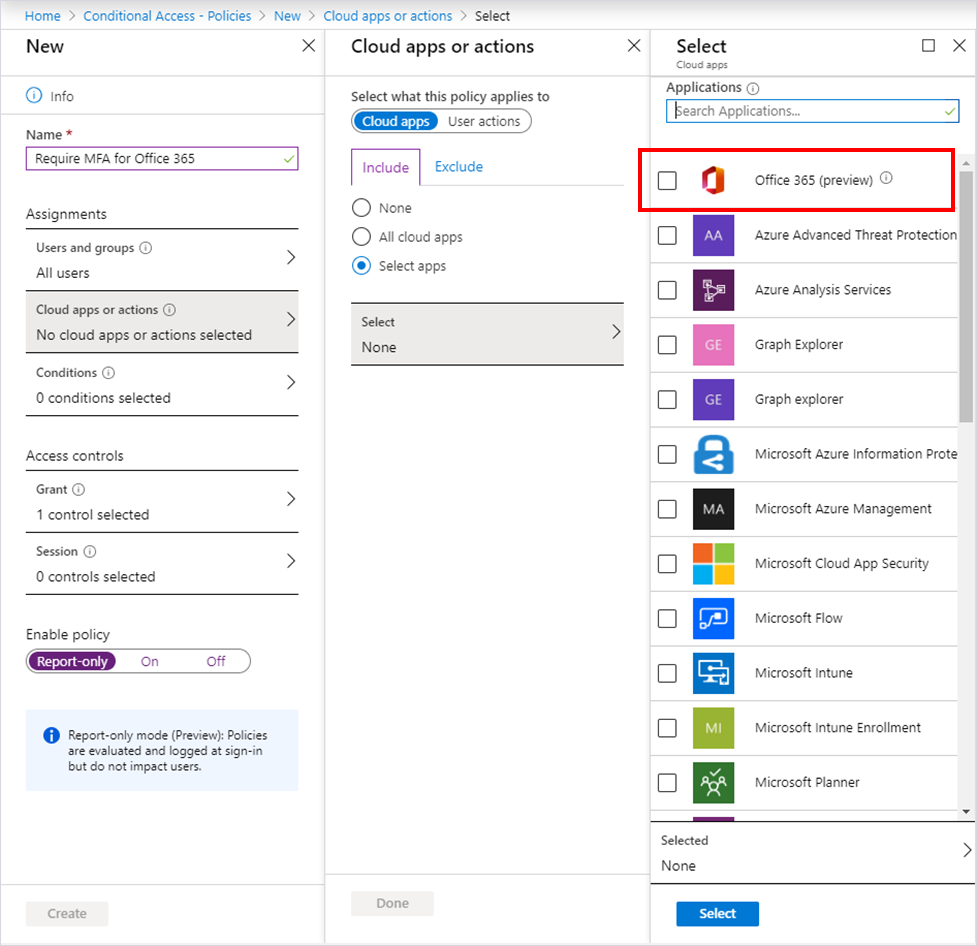
You can configure Conditional Access policy in Azure AD like you normally would. When making the app assignment, select Office 365 (preview) shown below. (We put it right at the top of the list to make it easy to find.)
When you finish setting up your policy, try running it in report-only mode. Using Conditional Access report-only mode will let you try out your policy right away and review the impact the policy will have before enabling it for your users.
One additional thing I’d like to note. Those of you who prefer to set different Conditional Access Policies for each Office workload can still do that.
Learn more about the Conditional Access for the Office 365 suite. Please try out the preview and let us know what you think in the comments below—your feedback is super valuable and greatly appreciated.
Best regards,
Alex Simons ( @Alex_A_Simons )
Corporate VP of Program Management
Microsoft Identity Division