This post has been republished via RSS; it originally appeared at: Premier Field Engineering articles.
Welcome to part two of “A Journey to Holistic Cloud Protection with the Microsoft 365 Security Stack. For those wanting to checkout part one which was the overview please click here.
For our first stop on the journey to holistic cloud protection with the Microsoft 365 security stack we will be discussing Identity security.
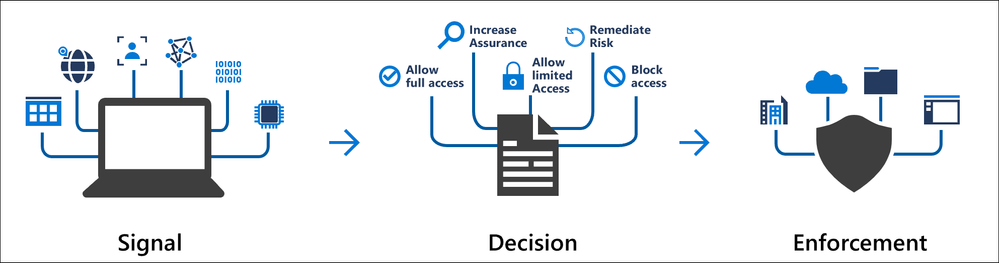
At the core of identity security, we must ensure that whoever is authenticating is really who they present themselves as. To do this we leverage conditional access to define unsafe scenarios to block access to corporate data while also providing access requirements when scenarios are acceptable. Your identity is the front door to your organization’s data. Just like the front door to our houses, some have locks with keys while other locks are integrated with an app on our phone. Keys can be lost or duplicated while the app will use something we have with you to allow access.
Conditional Access:
The modern workforce is more mobile and user preference centric than ever. Gone are the days where everyone works in a corporate building with a corporate assigned device. We work from home, a local cafe, a plane during travel and even out in the middle of the woods. Instead of a corporate standard issued computer; people work from their family computer, personal mobile device or even a hotel kiosk.
Using conditional access organizations are able to specify access scenarios that are safe to allow access, require additional requirements to be satisfied or block access all together. With conditional access you can define the below plus much more:
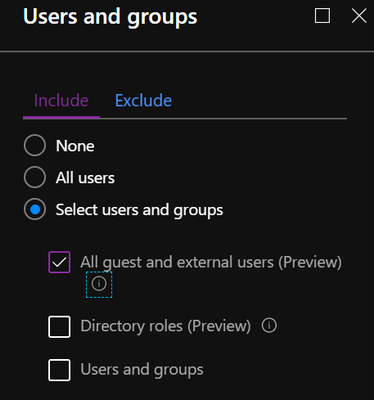
- Who does the policy affect
- Specific users, groups, directory roles or even external/guest accounts
- What does the policy affect
- All cloud apps, specific Office 365 apps or third party apps that you have integrated in with Azure AD
- Where does the policy affect
- From specific IP addresses or countries
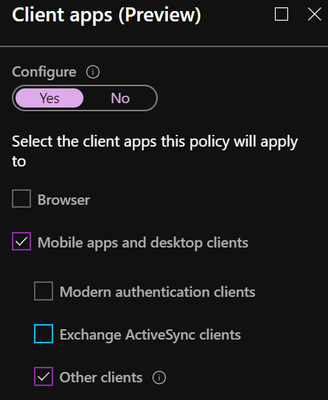
- From specific protocols from a browser, desktop app, mobile app, modern authentication, Exchange ActiveSync or legacy authentication
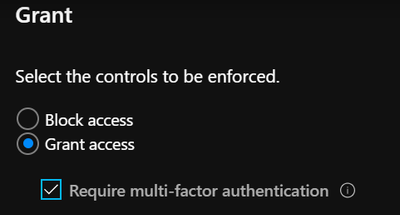
- Allow access with requirements or block access
- Require Multi-Factor Authentication
- Require the device to be compliant with Intune or hybrid Azure AD Joined
- Require acceptance of a terms of use
Below are some common scenarios that organizations must think about when layering security around identity.
Issue #1: Password are insecure… period - Passwords rely on an individual remembering a key piece of information to prove who they are. Passwords can be harvested through phishing campaigns, cracked using password sprays/brute force attacks or found written down. It’s a known fact that the first password created by someone will be the strongest one they ever create. Over time the strength will decrease as password expiration policies force them to think of new ones which are frequently variations of the original password.
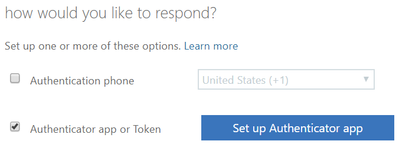
Solution: Enforce MFA using conditional access to add another layer of security that results in the person authenticating using something they have with them to prove who they are. At Microsoft we recommend using the Microsoft Authenticator App with push notification as your MFA option. While we also allow phone call and SMS verification options, these are less secure due to exploits like text/call masking techniques and SIM swapping. To reduce the need to MFA internal you can also create trusted IP address ranges using Named Locations and not enforce MFA while connecting from those ranges. With MFA enabled a user’s password becomes useless by itself to the attacker since you also have to approve the authentication attempt with your MFA method to gain access.
Issue #2: Guests have unverifiable security - As an organization you are able to decide the level of security you will enforce. Unfortunately, some organizations may have a different prioritization of security and leave themselves vulnerable to malicious attacks. If you share access to areas of your environment with an organization that gets compromised, then your data is accessible by the malicious attacker.
Solution: By applying conditional access policies to external accounts we can extend the organizations security posture to those outside the organization. This allows to create a baseline for acceptable conditions for external users accessing organization data no matter what level of security is being imposed by their organization. This reduces the threat of having data accessed by an attacker that has compromised an external user account that has been granted access to your organizations data.
Issue #3: Basic Authentication is risky - As an organization, modern authentication should be used in all case scenarios for Microsoft 365 and when connecting to third party services. Basic authentication including POP, IMAP, MAPI, SMTP and Office clients below 2016 are often used as protocols for malicious attacks due to how the authentication process occurs compared to modern authentication. Basic authentication is also incapable of leveraging modern authentication security techniques like conditional access which leaves them vulnerable to attack.
Solution: Block basic authentication using conditional access and enable modern authentication for all cloud services. If there are instances where basic authentication must occur, like sending emails using an SMTP service account, it is recommended to only allow it to authenticate from within trusted IP ranges. This can be accomplished using Named Locations in conditional access to define trusted areas for the specific service accounts.
Password Less Sign-Ins:
Over the course of a person’s life they will create many passwords for personal accounts, work accounts, and family accounts. With so many passwords, we begin to re-use passwords or create easier variations of originally complex passwords. From time to time organizations may have their security compromised resulting in the leaking of passwords used with them which ultimately compromise other accounts that share the same password. As you can see passwords have to go and we must move into a password less society where something that we have with use becomes our method of authentication.
Within the Microsoft 365 security stack we have two options for password less sign-ins which are available for authentication to Azure AD accounts and Azure AD/Hybrid AAD Joined devices.
- Microsoft Authenticator password less sign-in
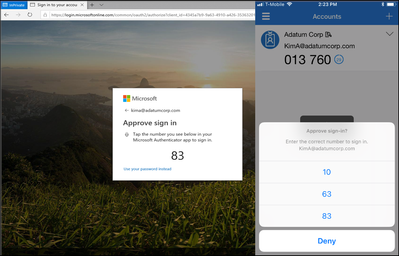
- This method leverages the Microsoft Authenticator app on our mobile device to sign in by matching a two digit number presented on the sign-in page with three sets of two digit numbers on their mobile device. This method can be seamless if your organization is already using the Microsoft Authenticator app for MFA. When setting up, it can be scoped to specific users/groups for piloting and a controlled deployment.
- FIDO2 Security Key
- This method leverages a physical security key that you either insert into your device or place in proximity of the device it allows. By having the security key you validate who you are and are allowed to authenticate. There are many supported vendors, but please ensure the one you select states it is FIDO2 compatible. When setting up, it can be scoped to specific users/groups for piloting and a controlled deployment.
As we put the brakes on this stop in our journey to holistic cloud protection with the Microsoft 365 security stack… I want to reflect on the importance of identity security. Your identity is the front door to access your organization’s data and we must always protect the front door. Security is everyone’s responsibility and as a society we are only as secure as our weakest link. By securing your organization you are making the workplace a little bit more secure for everyone else.
Thank you so much for joining me during this stop while we discussed identify security. Our next stop in this journey will be discussing Device security and how to keep all of our devices secure using the Microsoft 365 security stack.