This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
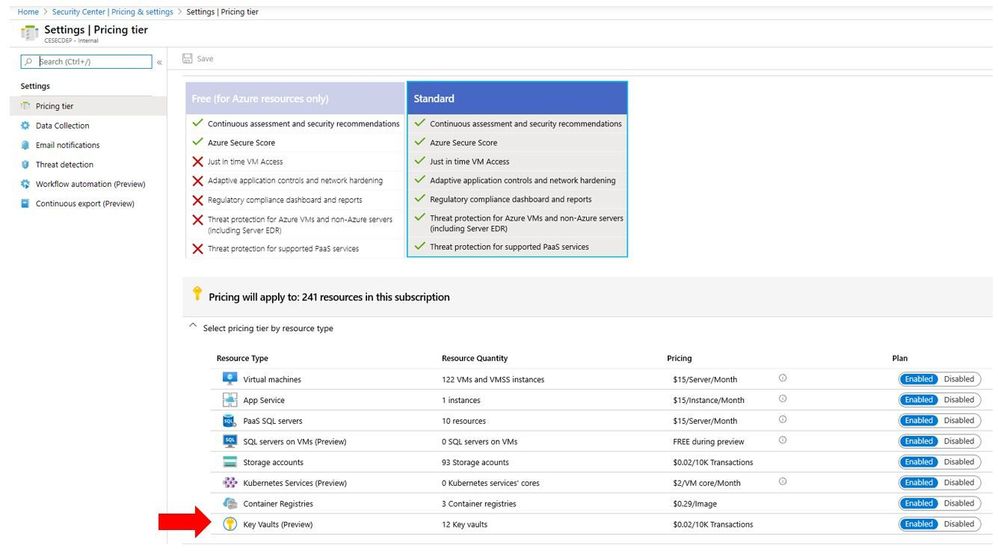
Azure Security Center includes advanced threat protection for Azure Key Vault. Security Center detects unusual and potentially harmful attempts to access or exploit Key Vault accounts based on behavior analysis using machine learning. To use this threat detection capability, you need to enable the Key Vault threat bundle in Azure Security Center pricing tier as shown below:
The validation steps that follows are going to help you to simulate an action that will trigger an alert in Azure Security Center. This action may be benign in some cases, but it could also indicate that the Key Vault has been accessed by someone using the TOR IP anonymization system to hide their true source location. Follow the steps below to perform this simulation:
1. If you don’t have a Key Vault created yet, make sure to create one following the steps from this article.
2. After finishing creating the Key Vault and the secret, go to a VM that has Internet access and download TOR Browser from here.
3. Install TOR Browser on your VM
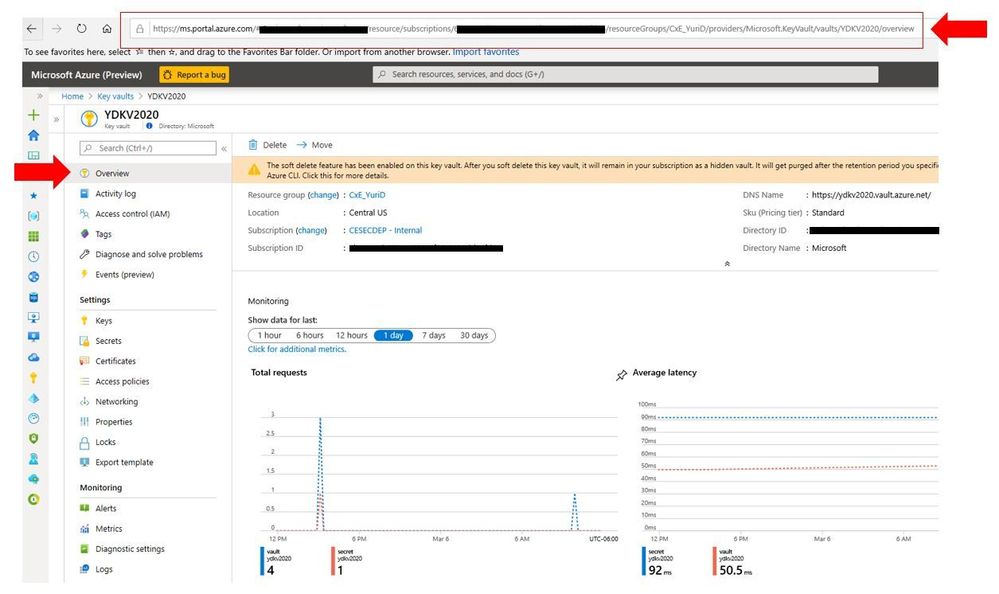
4. Once you finished the installation, open your regular browser, logon to the Azure Portal, and access the Key Vault page. Select the URL highlighted below and copy the address:
5. Open TOR and paste this URL (you will need to authenticate again to access the Azure Portal).
6. After finishing access, you can also click in Secrets option in the left pane.
7. In the TOR Browser, sign out from Azure Portal and close the browser.
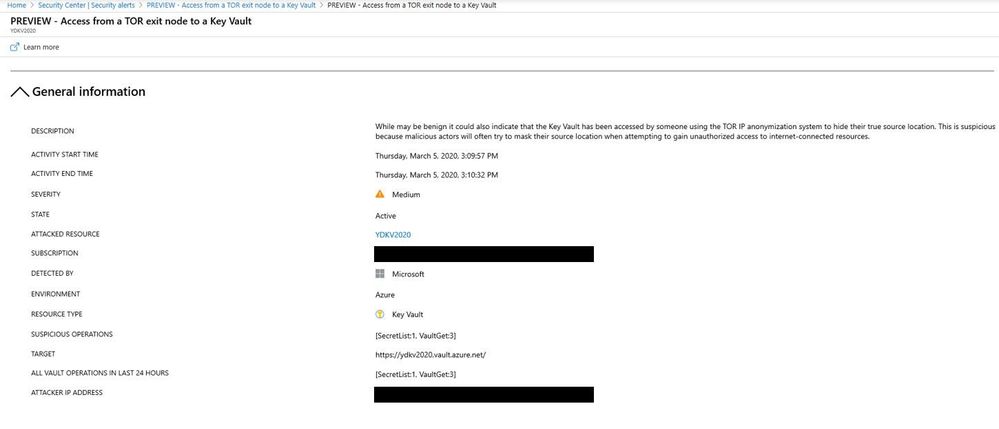
After some time, Security Center will trigger an alert with detailed information about this suspicious activity, as shown below:
For a complete list of potential alerts that could be triggered by Azure Key Vault threat detection in Azure Security Center, access this reference guide for alerts.
Special thanks to the reviewers:
Sharon Xia, Principal PM and
Walner Dort, PM