This post has been republished via RSS; it originally appeared at: Azure Active Directory Identity Blog articles.
During these challenging times, we’ve continued to collaborate closely with our customers as they react to the COVID-19 outbreak. From helping schools move quickly to enable distance learning, to supporting IT departments rapidly scale to support remote working scenarios, we’re right there in supporting our customers and the needs of their students, employees and partners.
Recently, we shared 5 steps you can take to enable remote work with Azure Active Directory. The first step we talked about is to deploy a common collaboration tool that can be used for video conferencing, chat, and document sharing.
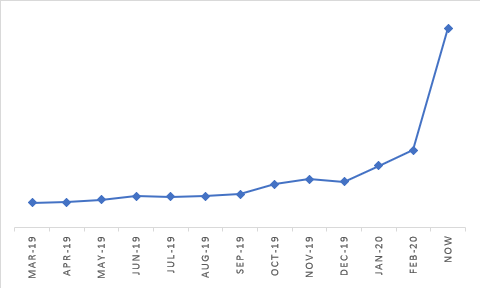
Over the last weeks, we’ve seen a huge increase in collaboration applications usage. At Microsoft, we spend most of our working days on Microsoft Teams, while our customers are leveraging Teams and other collaboration software like Cisco WebEx, Slack, Workplace from Facebook and Zoom. The chart below shows the kind of usage growth we’re seeing for just one collaboration application – increasing since the start of the year and up more than 250% in just the last three weeks.
If you’re looking to enable your workforce and partners to collaborate effectively from remote locations, here are some things to keep in mind.
Provide the best experience for your users with single sign-on
The best experience you can deliver to your users is one that doesn’t require them to learn new ways or new habits. Rather than distributing new usernames and passwords (which they can lose, or type into phishing sites), you can leverage the credentials they already use to log into to their Windows device or their email to provide access to any new app. Integrating a new app with Azure AD means they get single sign-on and won’t have to deal with annoying login prompts. Learn more.
Target the right users
If you’re already using Office 365, you’ll already have all your users in the cloud. This makes it easy for you to target the right set of users for access to your new collaboration tool. Users can be assigned to an app individually, or by group. You could even use a dynamic group, which defines its members by attributes like department name, or a self-service group, so your users could add themselves.
Targeting specific groups of users is also a best practice for rolling out an app widely, while minimizing disruption for your workforce. Start with a pilot group to quickly iron out any wrinkles, and then move more broadly. Learn more.
Accelerate account creation with user provisioning
To function properly, most applications require a user account to be created in their own user store (some apps, like Office 365, use Azure AD directly as their user store). Azure AD user provisioning programmatically creates user accounts in the target app whenever a user is assigned to the app. This reduces the complexity of setting up new apps and allows you to roll out to users sooner. Azure AD natively supports user provisioning for most widely used apps, and for any app that supports the SCIM standard. Learn more.
Improve app discoverability
Give your users one trusted place to find apps their organization has provided, which also makes it much easier to roll out new apps to your users.
If your users are already using Office 365, all apps connected to Azure AD will show up in the Office 365 Portal (office.com), and Office 365 navigation bar. This means they will be able to find a new collaboration app like Cisco WebEx or Zoom right next to Word and Excel.
As an alternative, Azure AD provides a centralized end-user app portal at http://myapplications.microsoft.com. If you already have a portal where you share apps with your users, you can embed the links from the My Apps page to provide the same functionality. Learn more.
Keep privileged accounts secured
Every IT department thinks about managing the risk of important accounts like the domain admin, but each one of your apps has super-user accounts that can be used to elevate privilege and provide access to important company information. This could be your confidential communications in a collaboration application, or it could be in other apps like your customer information in Salesforce or your executive salaries in Workday.
Our recommendation is to require Multi-Factor Authentication (MFA) for all privileged accounts – not just Azure AD, Azure and Office 365 administrators, but also the key accounts in your non-Microsoft applications. Learn more.
Protect your users and data, while enabling remote access
No matter what app is being accessed, or from where, it’s essential to verify that the user logging in is who they say they are. This helps secure your users and your company data.
This might be the first time you’re allowing your users to access company resources from off your corporate network, or you might be a pro. Either way, you should make sure you use Conditional Access to provide the right level of security and controls, without getting in the way.
In the past, allowing low impedance within the corporate network and blocking access from non-corpnet locations was a common strategy. With lots of users now working off the corporate network, policies that limit access by location will create friction.
We recommend to start with requiring MFA for all locations. With adaptive access policies, Azure AD will only re-prompt for MFA if conditions have measurably changed, to reduce the impact on your users. You can also add a requirement that apps can only be accessed from a compliant device, even if you need to allow BYOD. (If you’re rolling this out for the first time, make sure you’re not accidentally blocking users from registering for MFA or enrolling a new device.)
If you’re using Microsoft Cloud App Security (MCAS), you can enable more advanced session controls to prevent certain types of riskier behavior. If you have Azure AD P2, you should definitely enable Risk-based Conditional Access, which will do real-time deflection of dynamic attacks.
Integrating your favorite collaboration app with Azure AD allows you to deploy them out to your users, wherever they are, quickly and securely. We hope these recommendations will help you enable uninterrupted operations for your organization in these challenging times. Stay safe and be well.
|
Need more support?
Microsoft FastTrack is a program to help you deploy, drive usage, and adopt best practices for cloud technologies. This service is available for customers with 150 or more licenses of an eligible plan – go here to request assistance. If you need technical support, reach out through the administration portal |