This post has been republished via RSS; it originally appeared at: Small and Medium Business Blog articles.
Given the reality of recent times, where employees need to work from home, secure productivity is becoming an imperative for Small & Medium Businesses. Since Employees are using a plethora of devices like laptops, desktops, home computers & mobile devices to access company data and get work done, the challenge is keeping all these devices secure and ensuring secure access to sensitive company information.
The primary challenge with myriad unmanaged devices accessing your environment is that it increases the likelihood that a security breach will occur as users are likely to get breached outside of your network, exposing corporate data and potentially bringing an infected device in to your organization. It is therefore imperative to have a centralized security policy in place to protect all the devices accessing your company data not just your managed laptops. Intune in Microsoft 365 Business helps you define a unified, centralized device policy that spans across all devices accessing your network.
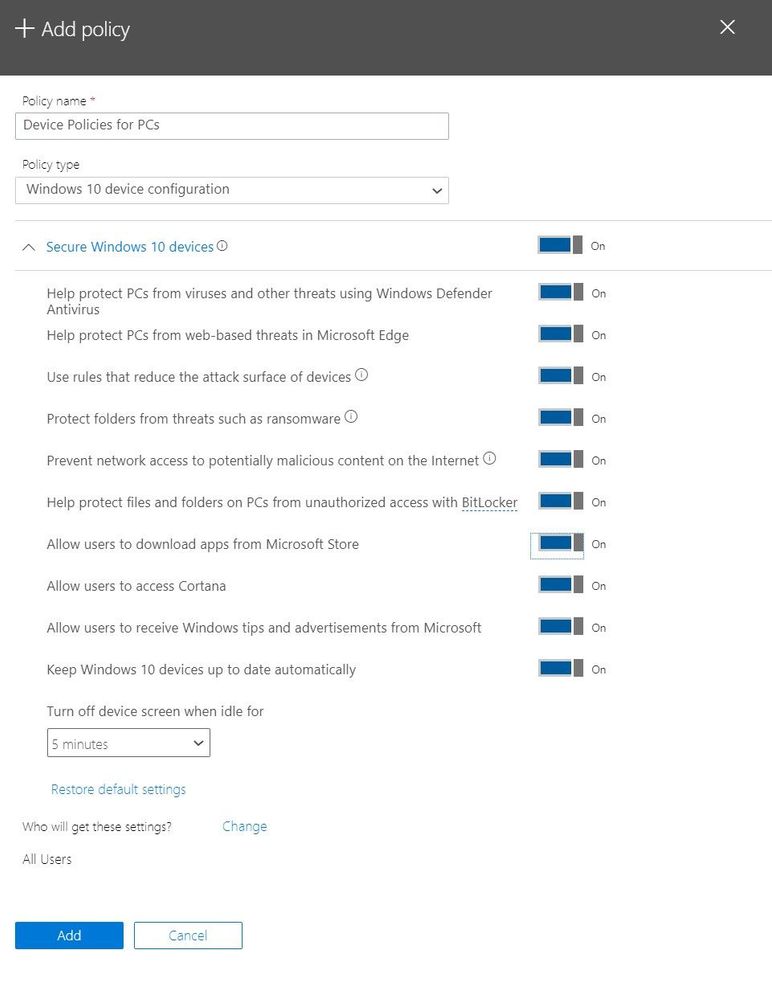
PC Management with Intune
Intune helps you manage your PCs with features such as the ability to enable security policies or wipe devices remotely. In Microsoft 365 Business, you have pre-configured Device policies for windows that help you set some basic security policies for a PC accessing your environment like – enabling Windows Defender and enabling protection for your folders from ransomware.
It is highly recommended that you enable the Windows Defender Antivirus protection in Microsoft 365 Business as Windows Defender Antivirus is the most deployed in enterprise
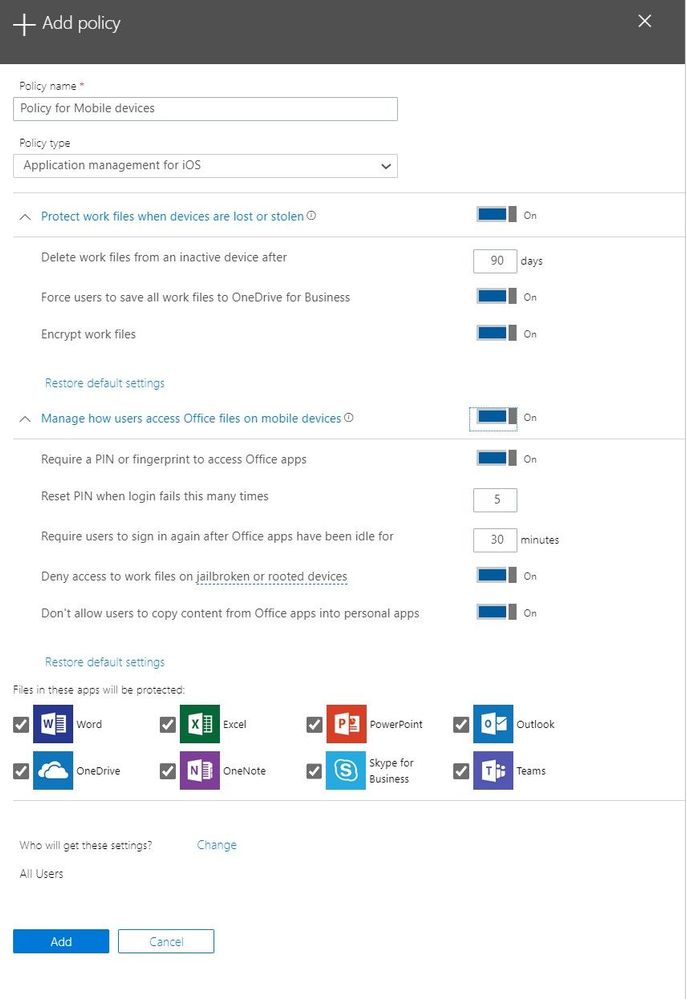
Mobile Device Management with Intune
Intune also helps you manage your mobile devices – iOS & Android devices - in two ways primarily:
- Intune Mobile Application Management: Through this, you are able to restrict users from Copy, Pasting or saving corporate data & documents from their Microsoft 365 Apps to their personal apps without requiring any kind of device enrollment. For Example, when this feature is enabled, a user is unable to copy/paste information from an email into their iOS Notes app. This can be easily enabled through the Mobile application Policy in Microsoft 365 Business Administration Console and does not require a device enrollment process. This helps you easily enforce restrictions on corporate data on personal mobile devices.
- Intune Mobile Device Management: If you want to enforce stronger mobile device policies that go beyond mobile application management, you can also do that by enabling full Mobile device management capabilities in Intune. This helps you enforce deep, device centric security policies like enabling PIN policy for the entire device, blocking screen capture or enabling customized profiles. More details on the full range of device management capabilities available with device enrollment is listed here
For more details on how to enroll devices, visit aka.ms/m365b
Device based Conditional Access
Since Conditional Access capability is available in Microsoft 365 Business, you can restrict access to applications only from devices that are registered with Azure AD, and which meet specific conditions.
Device-based conditional access protects an organization's resources from users who attempt to access the resources from:
- Unknown or unmanaged devices.
- Devices that don’t meet the security policies your organization set up.
Users who access applications that are protected by a device-based, certification authority policy must access the application from a device that meets this policy's requirements. Access is denied if attempted on a device that doesn’t meet policy requirements.
For information about how to configure a device-based, certification authority policy in Azure AD, see Set device-based conditional access policy for Azure Active Directory-connected applications.
We hope that through this blogpost, you have confidence that Microsoft 365 Business has robust features to help protect all your devices. For more details on Microsoft 365 Business, please visit aka.ms/m365b