This post has been republished via RSS; it originally appeared at: ITOps Talk Blog articles.
In my last post, I looked at the difference between Microsoft’s Azure AD Identity Protection and Azure AD Conditional Access.
While these capabilities can reduce the risk of a compromised account or a risky sign-in attempt from successfully completing an authentication and authorization attempt, what if circumstances change after a user has successfully logged in?
Once you’ve successfully logged in to a service, you’re issued with an OAuth 2.0 access token. The token has a lifespan, and your session is valid until that token expires. By default that’s 1 hour, unless a Configurable Token Lifetime policy is in place or authentication session management has been configured with Azure AD Conditional Access
But imagine if you’re an admin whom, for whatever reason, needs to block a specific user’s access immediately. Or if the service detects that a user is now accessing it from free Wi-Fi at a coffee shop instead of from their corporate office. We somehow need to revoke their valid, non-expired access token, forcing them to re-attempt authentication and authorization - which will fail if their account has been disabled or may present them with a Multi Factor Authentication challenge because of their new location.
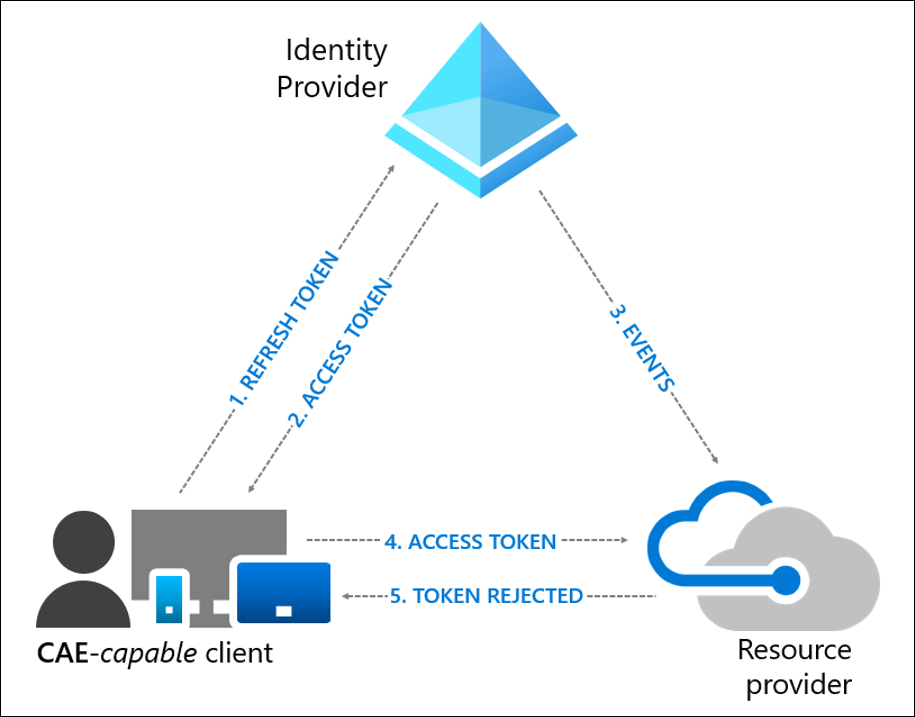
Fortunately, OpenID Connect (OIDC) used for authentication and OAuth 2.0 access tokens for authorization are both industry standards, that Microsoft contributes to. Through the OpenID Foundation’s Shared Signals and Events working group, we’re helping shape the sharing of security events, state changes and other signals used between dependent systems. From this work, comes the Continuous Access Evaluation Protocol (CAEP).
CAEP provides a standard way for an identity provider or a service (also known as the relaying party or resource provider) to be told to stop honoring a valid token and to re-issue an authentication and authorization attempt. With this mechanism in place, the lifespan of a token is no longer important, as we can re-challenge a user whenever circumstances change, without having to wait for their token to expire.
This has such great security benefits that we’ve recently announced a Continuous Access Evaluation capability in Microsoft Exchange and Microsoft Teams. Initially, the following events will be supported for Outlook and Teams clients on Windows, Mac, iOS and Android:
- User account is deleted or disabled
- Password for a user is changed or reset
- MFA is enabled for the user
- Admin explicitly revokes all refresh tokens for a user
- Elevated user risk is detected by Azure AD Identity Protection
And this is just the beginning, with plans for other events like location change or device state change.
Importantly, our implementation of this will help us feed back important findings to the Shared Signals and Events working group, to further improve CAEP as a ratified industry standard.
To learn more:
Announcement: Moving towards real time policy & security enforcement
Docs.microsoft.com: Continuous access evaluation