This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
Hello again and welcome to the 4th, and final, part of our “Demystifying attack surface reduction rules” blog series!
The objective of this last blog post is to shed some light on how to approach a migration from a 3rd party Host Intrusion Prevention System (HIPS) solution into ASR rules.
Migrating from a 3rd party HIPS to ASR rules
What if you're in the situation where you're either evaluating or executing a migration from a 3rd party HIPS (Host Intrusion Prevention System) over to ASR rules in Microsoft Defender ATP?
Many of the existing HIPS solutions require customers to define their own rules, or customize built-in ones. This demands deep expertise by customers to understand exactly what they need to protect against, as well as have a high-level of granularity that often works against them, by hindering overall performance and reliability.
What we have done with ASR rules is a bit different. We’re providing you with the most effective and efficient rules; the ones needed to mitigate the most common and emerging attacks, based on our continuous security research.
The promise is simple: Increase your security stance, without the hassle of creating your own custom rules, which may impact your user’s productivity and the reliability of their systems.
The lack of custom rules, often creates a false feeling of lack of protection or loss of control. It’s therefore important to understand that our view on HIPS is different: a single feature, such as ASR rules, is not meant to cover every single attack vector, nor is it meant to be a custom filter for everything happening in the system (e.g. registry, files, processes, etc.). Many of the controls and rules that customers might have used in their HIPS are in fact either built into Windows 10, the Microsoft Defender AV itself, or exist in some other component of the encompassing Microsoft Defender ATP suite.
Our goal is quite simple. We aim to provide you out-of-the-box an effective, reliable, performant, and defense-in-depth approach to HIPS.
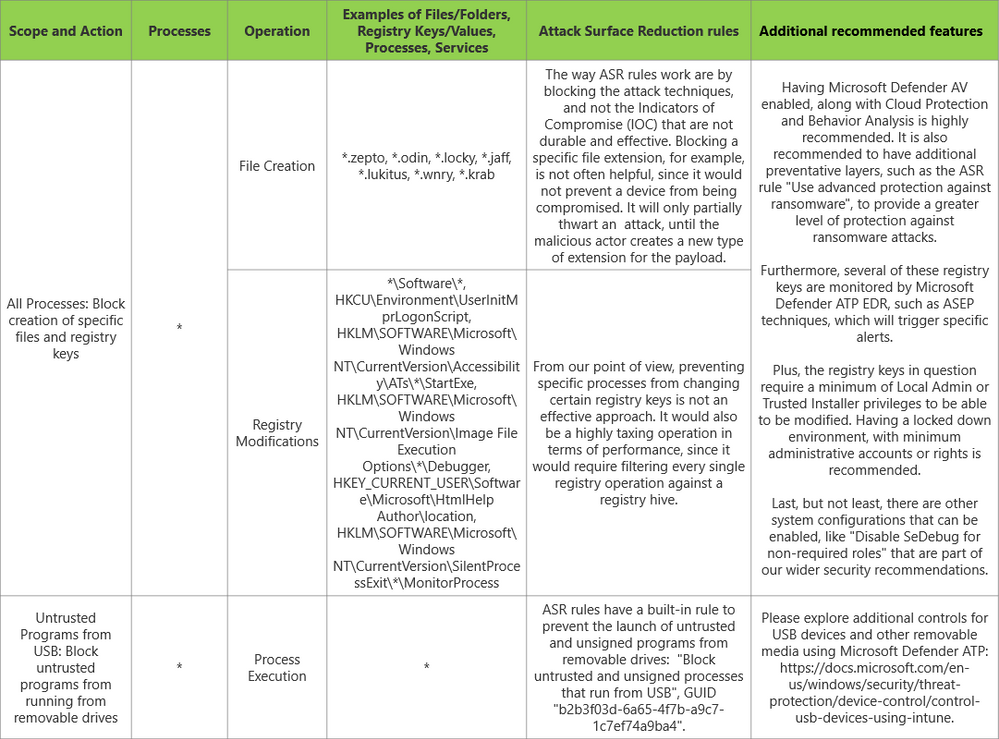
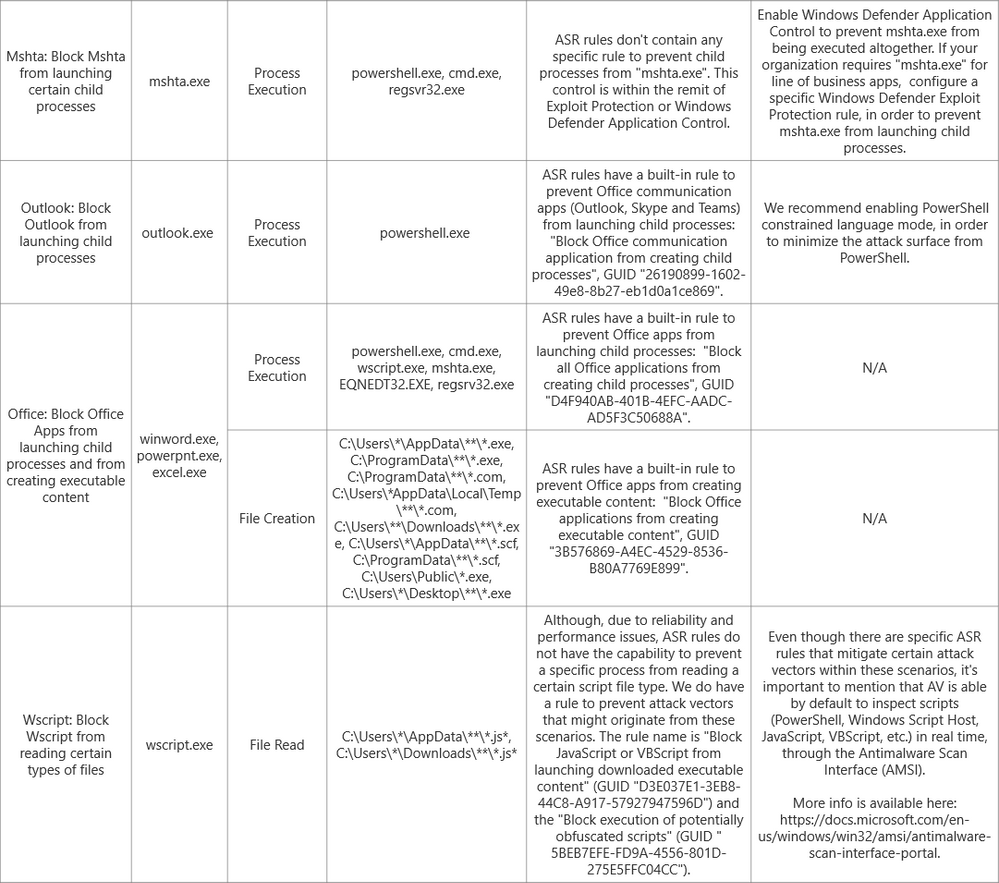
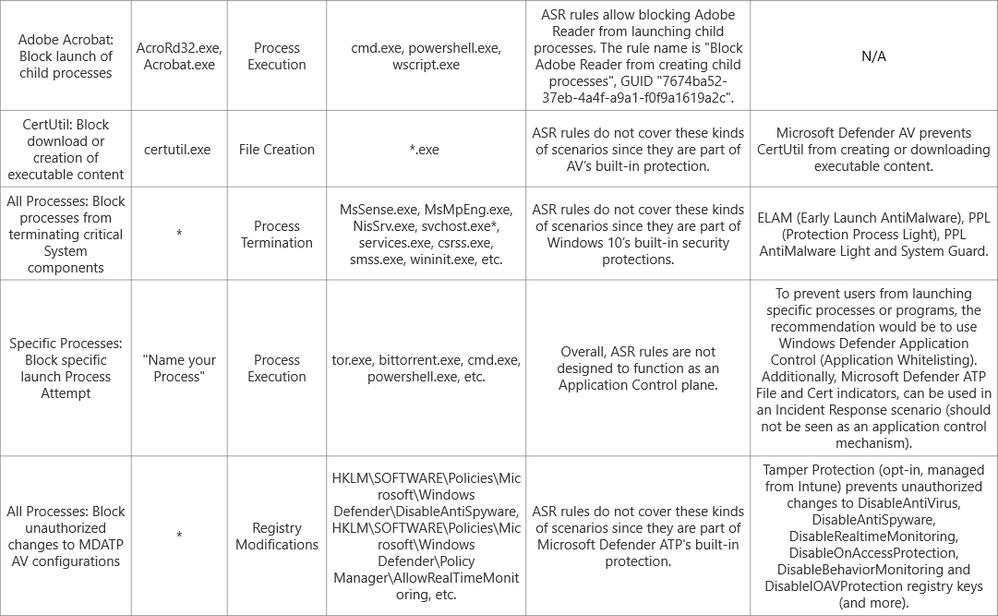
With that said, and with the aim of helping customers understanding how they can establish an effective mapping between possible rules that they are using today, and how those translate into the Microsoft Defender ATP, below is a table with the most common questions or scenarios that we get from customers, when migrating from a 3rd party HIPS product over to ASR rules. We've also attached an Excel file with this table for easier readability and use.
Conclusion
We hope that you have found the blog series on demystifying attack surface reduction rules useful and informative! As always, please reach out in the comments below if you have any questions or feedback!
See you soon!
António and Rob.
Program Managers @MDATP Product Group