This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
The goal of this post is to show Azure SQL Database, and how the vulnerability scans available can help you baseline security, and how to remediate one of the items.
Azure SQL Database is a great way to host your relational data in Azure. One of the benefits you get is vulnerability assessments, with clear explanations and links for remediation.
This link will cover some of the items we wish to review: https://docs.microsoft.com/en-us/azure/sql-database/sql-vulnerability-assessment
Vulnerability Assessment is part of the Advanced Data Security offering, which is a unified package for advanced SQL security capabilities. Vulnerability Assessment can be accessed and managed via the central SQL Advanced Data Security portal.
The rules are based on Microsoft's best practices and focus on the security issues that present the biggest risks to your database and its valuable data. They cover database-level issues and server-level security issues, like server firewall settings and server-level permissions. These rules also represent many of the requirements from various regulatory bodies to meet their compliance standards.
I will walk you through my own Azure SQL Database instance, and some of the common security issues.
I first authenticate and go to portal.azure.com and click on “All Services” and then “SQL Servers”
I click on ‘georgesqldb’ (you would click on your Azure SQL Database instance).
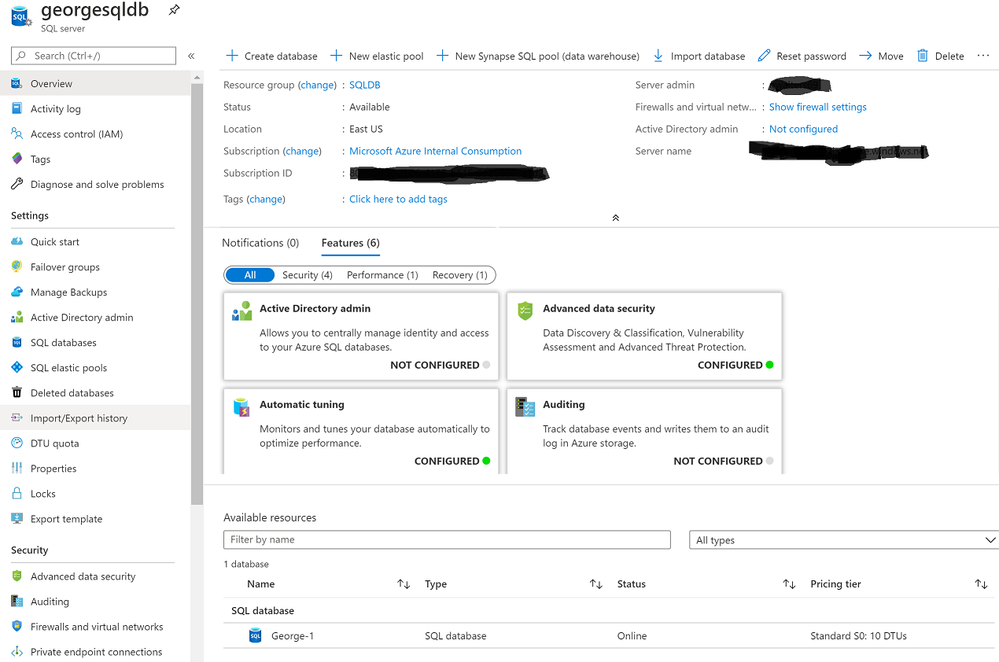
Notice how there are a few choices for features we can take advantage of! Today, we’ll focus on Security. Make sure you understand recovery (for disaster recovery) as well as performance (for performance tuning) your database.
For Security, these are the options we need to be concerned with.
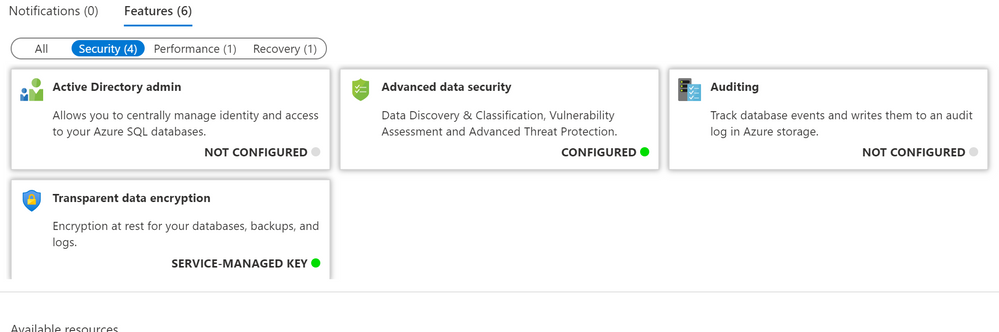
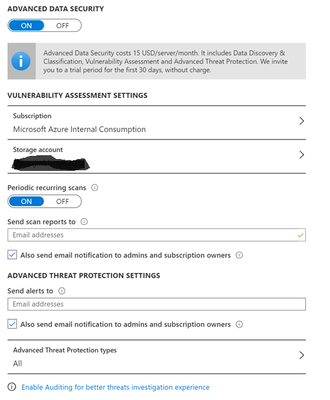
When we click on Advanced data security, we get the following:
Yes, it costs 15 USD per month, but that seems like inexpensive insurance to have regular scans done, and emailed reports.
I would encourage you to turn this on, and ensure you have at least two recipients for the scan reports and advanced threat protection.
Machine learning, coupled with a lot of data from our own systems, helps inform this threat protection model, to help protect you. Here is a reference link on this. https://docs.microsoft.com/en-us/azure/sql-database/sql-database-vulnerability-assessment-rules
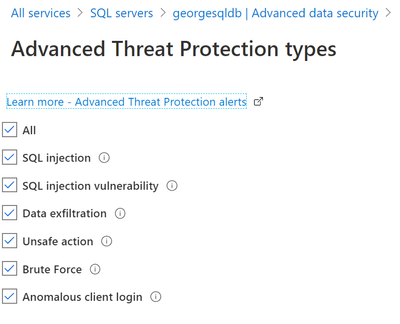
If you click on "Advanced Threat Protection Types", you will see what is protected.
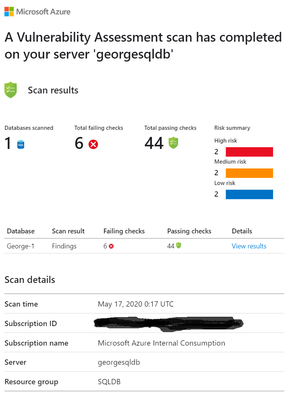
When Vulnerability assessment is enabled, and your emails are set up, you may get a report like the following, with risks assigned to high, medium, and low categories:
High Risk! What am I doing wrong!
I click on “View results” and here is the breakdown:
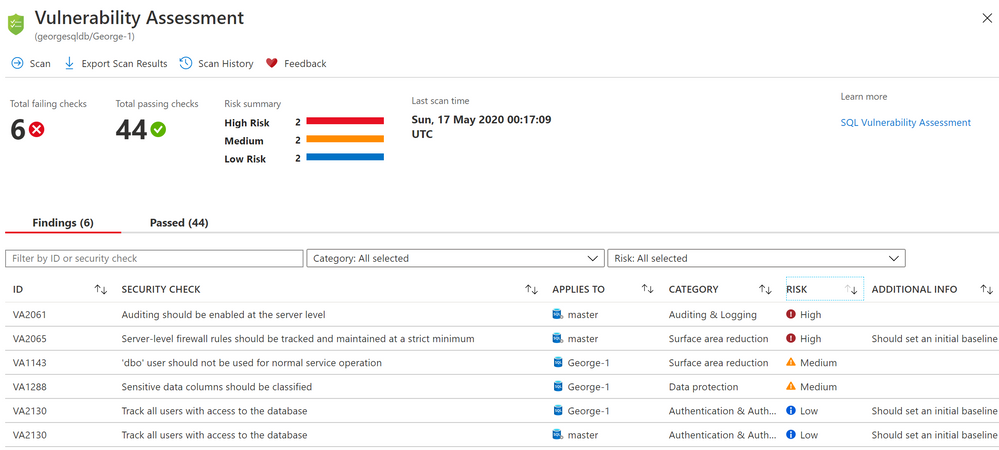
The high risk rules are around auditing (A feature of SQL Server since 2008!), and Server-level firewall rules (do you have those enabled?).
The medium risk rules triggered are about reducing attack surface area. Using dbo for normal service has been recommended against, and since SQL 2005, has been easier to do.
One handy service in Azure SQL Database is the ability to automatically classify data! That is flagged as something I should do. This could help me discover things like sensitive data, such as credit cards, social security numbers, personally identifiable information, and so forth. Knowing this is a programmatic scan that can help me might make it easier to achieve compliance.
Finally, the lower risk rules are around tracking users to both my user database and to the master database. This sort of tracking will help us protect our data, and ability to access our data.
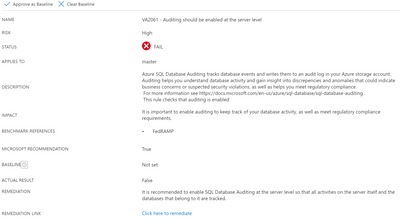
I decide to click on the top issue around auditing, and I get this:
Each flagged item gives a clear description, as well as a handy link for remediation. In this case, an example of a benchmark compliance reference, FedRAMP, is offered.
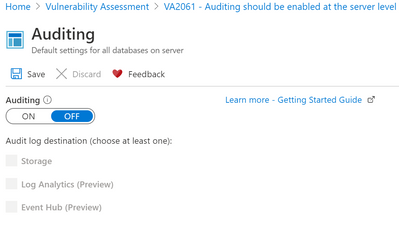
When I click on the remediation link, I get this:
In this case, auditing can be turned on, and I can choose where to send the log data. The default is Storage, which would require a storage account.
Log analytics is a way to store and analyze logs at some scale.
Event hubs is for forwarding events on to other consumption engines.
The goal of this post is to show Azure SQL Database, and the vulnerability scans available, help you baseline security, and how to remediate one of the items.
Please comment below, and happy securing!
To learn more about working with Databases in Azure, click here: https://go.microsoft.com/fwlink/?linkid=2105093