If you’re an investigator who wants to be proactive about looking for security threats, Azure Sentinel powerful hunting search and query tools to hunt for security threats across your organization’s data sources. But your systems and security appliances generate mountains of data that can be difficult to parse and filter into meaningful events.
In the third installment of this blog series we focus on the new enhancements to this integration that will provide additional flexibility and advance your threat hunting efforts. In Part 1, we covered the steps to convert Sigma rules to Azure Sentinel using SOC Prime’s Uncoder.io tool. In the second installment of this blog we focused on the ability to advance your security analytics with SOC Prime’s extensive threat detection marketplace.
In this blog we’re thrilled to announce new enhancements to the integration between Azure Sentinel and SOC Prime which aim to help organizations save their security awareness and reduce implementation time.
Azure Sentinel | SOC Prime Multi-Tenancy
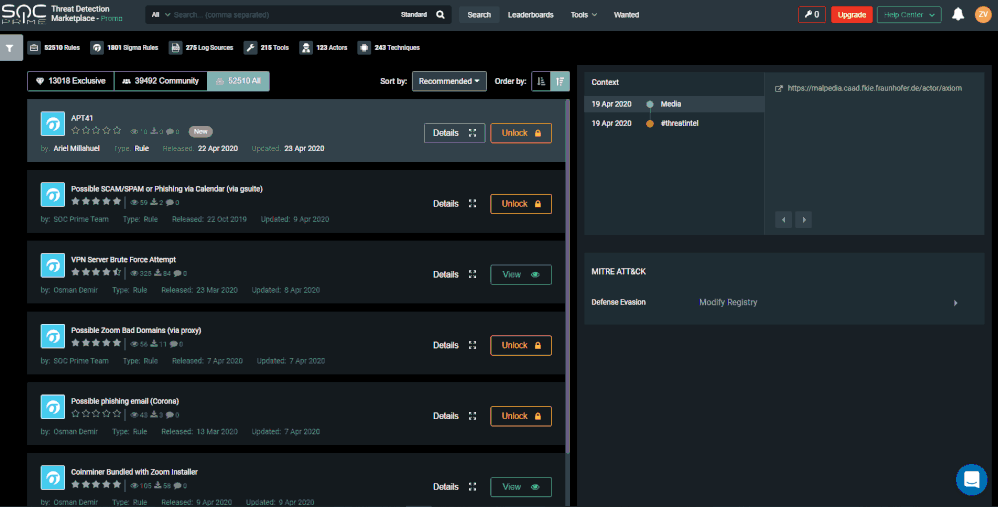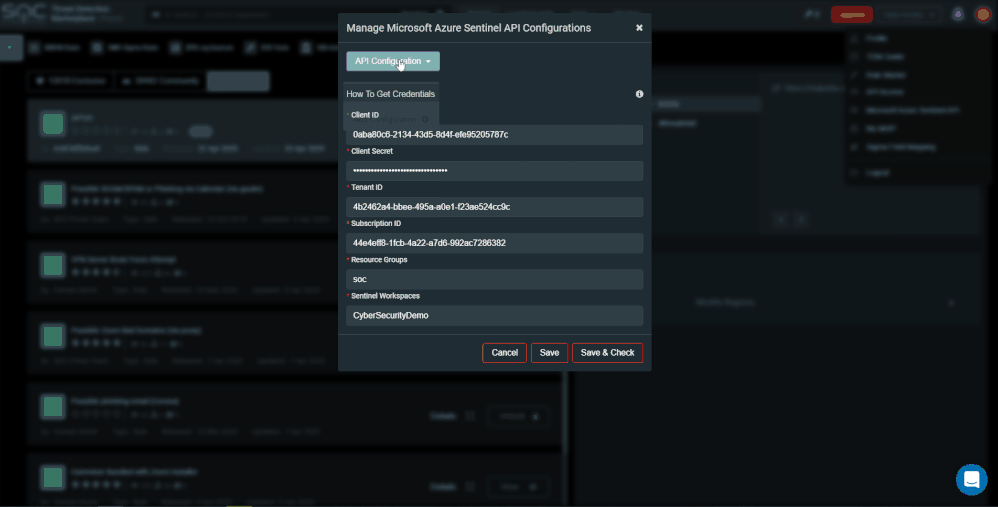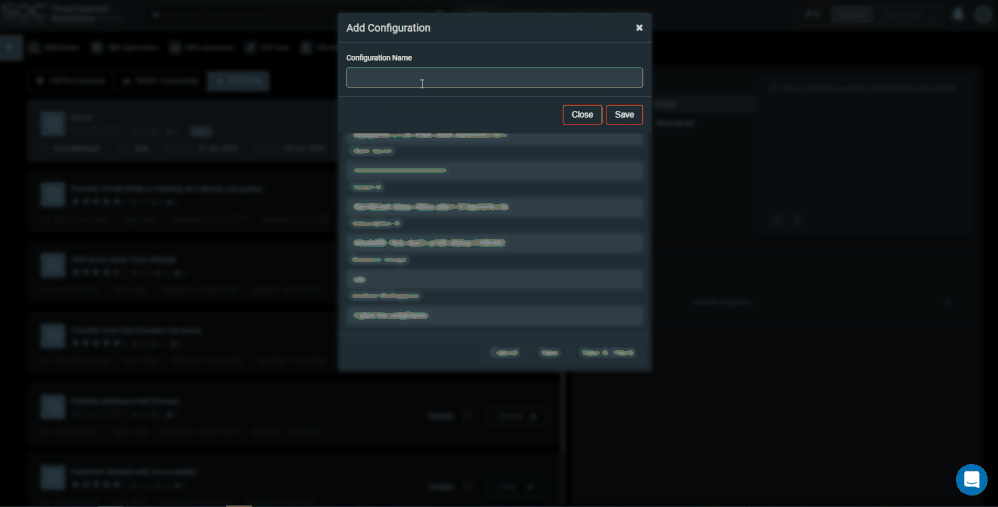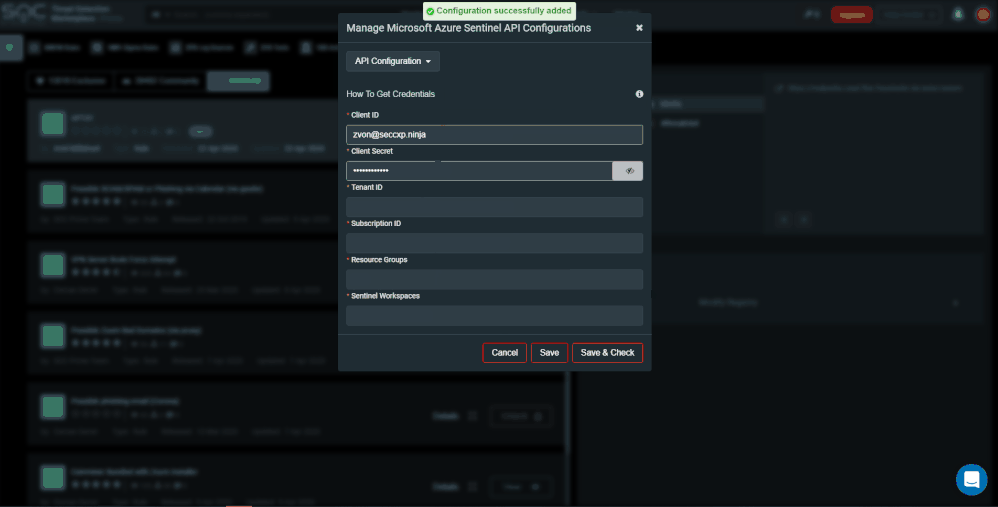
SOC Prime’s intuitive platform enables you to filter and consume rules for your desired platform, in our case – Azure Sentinel rules or queries. In the second installment, we provided details on the ability to consume rules to your Azure Sentinel instance and the steps to configure the Azure Sentinel API. We are happy to announce the Multi-tenancy hook between Azure Sentinel and SOC Prime, your security team can now consume rules and queries for more than one tenant. ![]()
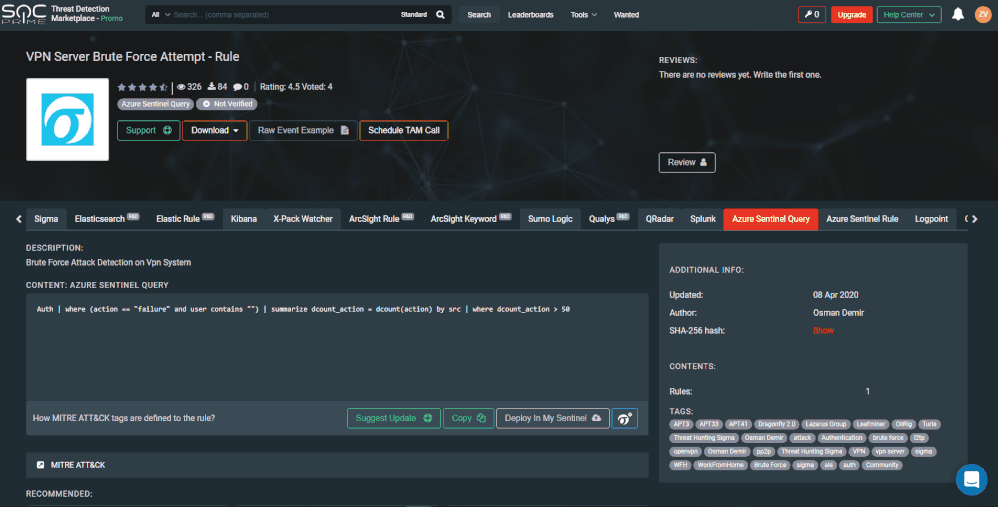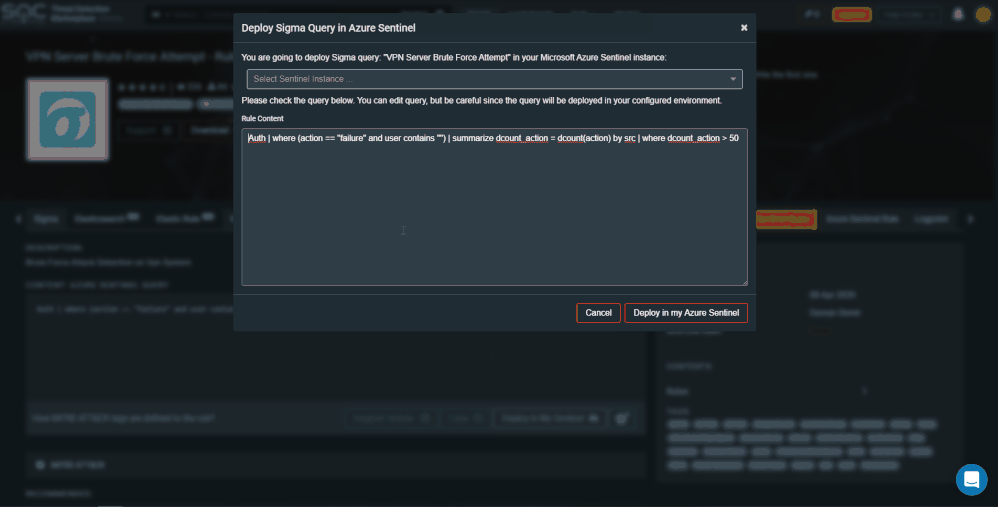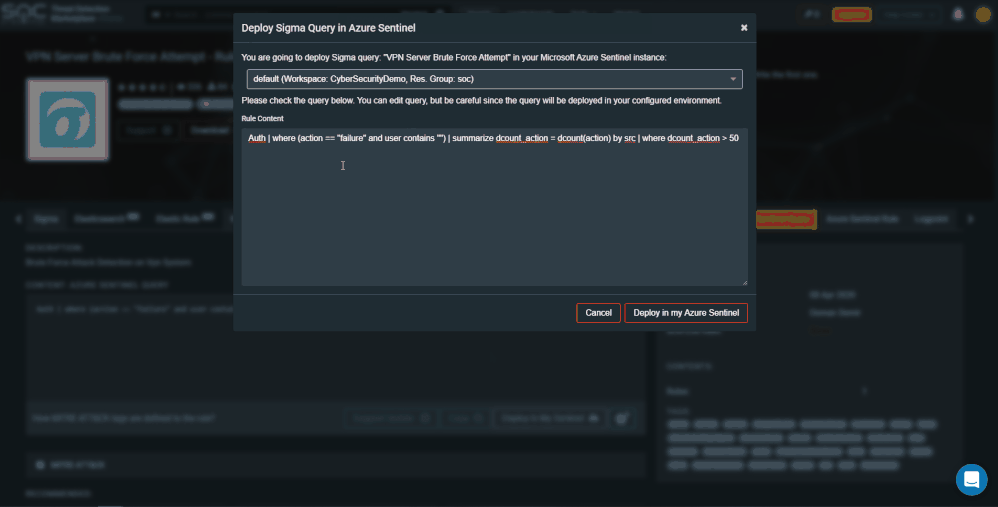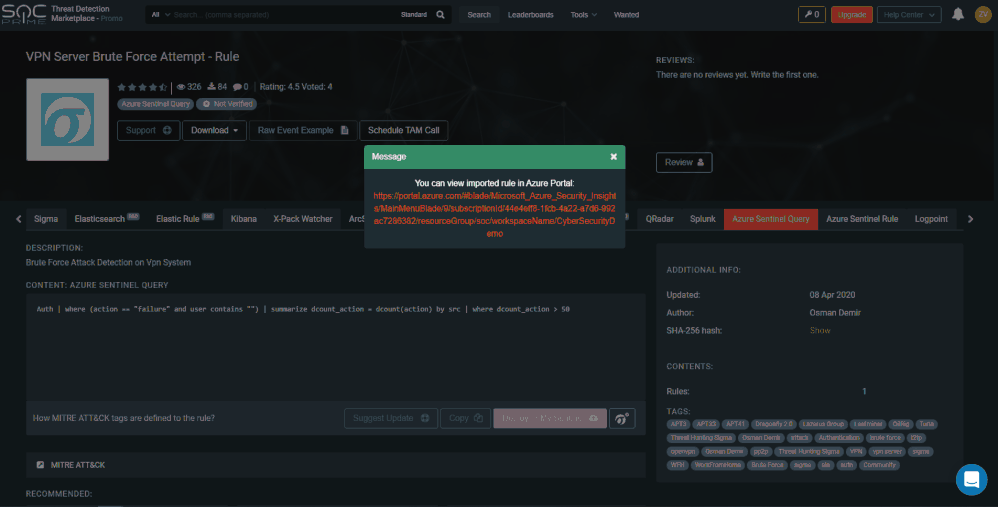
To add another Azure Sentinel tenant press the ‘Microsoft Azure Sentinel API Configuration’ button. You can a add new configuration, edit, or delete existing configuration. For example, a test, and production environment.
Deploy Hunting Queries from TDM to Azure Sentinel
It’s a no brainer that there is a call a proactive threat hunting approach. The integration has now been enhanced to enable your security team to consume hunting queries right into Azure Sentinel. Now you can simply use the “Deploy In My Sentinel” button in your TDM account to deploy queries into your saved Hunting queries.
Putting it all together – View & Edit in Azure Sentinel
After you receive the success message from SOC Prime, the query is deployed in your Azure Sentinel instance. The rule will be available under the ‘Hunting’ tab in the list of saved queries. In Azure Sentinel, you have the ability to view/edit the rule and thoroughly understand the use case and MITRE ATT&CK tactics or technique it correlates to. Additionally, your security team will be able to proactively look for new anomalies that weren’t detected by your security apps and ask the right questions to find issues in the data you already have on your network.
Summary
Supercharge your cloud SIEM today!