This post has been republished via RSS; it originally appeared at: Intune Customer Success articles.
By: Pallavi Joshi | Program Manager | Microsoft Endpoint Manager - Intune
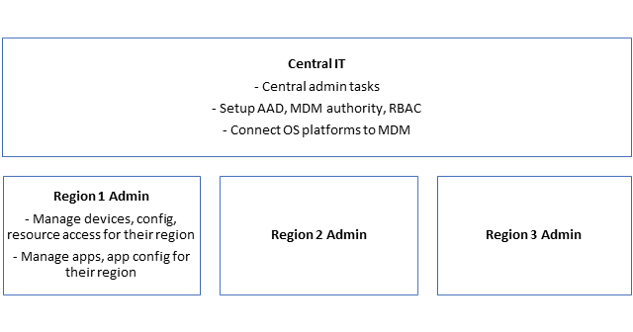
An increasing number of global organizations rely on a delegated model to manage their mobile devices, tablets and laptops. These global orgs have multiple regions and a single global tenant to manage. The central IT and regional admins are organized as shown in the figure below. These regional admins have a detailed understanding of their region’s end users and their requirements.
In this model, the Central IT team needs to perform certain configurations to setup the tenant for regional admins. These central configurations are global and impact the entire tenant (and all the regions). Once these configurations are set, the regional admins can start managing users, devices and apps for their regions. The central IT team, which has complete admin access, needs to clearly identify these configurations and provide the right level of access to regional admins to enable them to perform management activities for their region.
In Intune, there are a set of configurations that impact the entire tenant and hence need to be done by the Central IT team. Besides that, there are other configurations which can be delegated to region admins using scope tags. Role-based access control and scope tags allow the regional admins to define configurations, apps and policies and assign them to users of their region and not touch entities of other regions.
This blog is focused on identifying these configurations in Intune – those that are centralized and have tenant-wide impact, those that need to be managed by Central IT team and those that can be delegated using scope tags. This would enable Central IT teams to setup the configurations in Intune and enable regional admins to manage their regions independently.
Tenant-wide configurations in Intune
Here’s the list of global settings that have a tenant-wide impact in Intune:
- MDM Authority
- Apple MDM Push Certificate
- Managed Google Play account
- Windows Hello for Business
- Windows Automatic Enrollment – MDM and MAM user scope
- Microsoft Store for Business
- Android Enterprise – Corporate owned fully managed enrollment • App Categories • Device Cleanup Rules
Once these configurations are set, Central IT can define roles and permissions for regional admins. They can use either one of the built-in roles, or create a custom role as follows:
- Role Name – Region Admin
- Permissions – As per requirements, using the long set of toggles
- Assignments – One assignment per region can be created:
- Assignment Name – Region 1 assignment
- Members – Region 1 admin group
- Scope (Groups) – Region 1 user group
- Scope Tags – Region 1 scope tag
The role definition and permissions allow the region admins to perform management of devices, apps and define relevant configurations for their regions.
Configurations to be set by Central IT
This section contains list of configurations that do not have a tenant-wide impact, since they can have multiple instances and can be assigned to various groups e.g. multiple Apple Configurator profiles can be created in Intune and each profile can be assigned to groups of a specific region, if required. These configurations need to be set by the Central IT team. These configurations can also be set by regional admins, as they will have visibility of all the instances of these configurations and their access can be limited to user or device groups of their regions.
- Apple User enrollment
- Apple Configurator profiles
- Enrollment Status Page
- Intune Company Portal - Branding and Customization
- Conditional Access – Requires Azure Active Directory permissions
- Custom notifications
- Enrollment restrictions
Configurations to be set by regional admins
The following configurations can be completely delegated to regional admins using role-based access control and scope tags in Intune. Using scope tags, regional admins can create their own configurations, assign them to user or device groups of their regions and not be able to view or assign these configurations to other regions.
- Apple’s Automated Device Enrollment
- Android Enterprise - Corporate Owned Dedicated Devices
- Autopilot Profile
- Device Categories
- Device Management
- App Management
- Device Compliance Policies
- Device Configuration Profiles
- App Configuration Policies
- App Protection Policies
- iOS App Provisioning Profiles
- Apple VPP tokens
- Policy Sets
- Role based access control and scope tags
- Security Baselines
- Terms and Conditions
- Update policies for iOS/iPadOS
- Windows 10 update rings
We hope this identification of what to centralize and what to delegate helps you in defining relevant configurations in Intune and enabling the global and regional admins towards a successful deployment path.
If you have any questions on this post, just let us know by commenting back You can also ask quick questions at @IntuneSuppTeam out on Twitter.