In this blog post I will introduce a way to automate inclusion of new Azure Security Center subscriptions into Azure Sentinel, more specifically, any new subscriptions in the organization will stream Azure Security Center alerts to Sentinel.
The Azure Security Center to Azure Sentinel integration challenge
Azure Security Center is enabled, collects data and generates alerts per subscription. Connecting the organization ASC subscriptions to Azure Sentinel is also done per subscription, from the connector page in the portal or by API call.
When you on boarded Azure Sentinel for the first time, you have probably connected all subscriptions that were available at that time.
But what happens if the organization expects new subscriptions to be added on a regular basis? In this case you would probably like to have a mechanism that will make sure that all new subscriptions Azure Security Center alerts are streamed to Sentinel as well.
The solution will be based on an Azure Active Directory application identity and Azure Logic Apps playbook.
Quick Link to Azure Sentinel GitHub to deploy the ASC AutoConnect playbook
This blogpost includes:
- Solution summary
- Prerequisites
- Playbook Deployment Instructions
- Azure Logic Apps workflow (playbook) explained
- Registered application as the identity explained
- Q&A
- Documentation reference
Solution summary
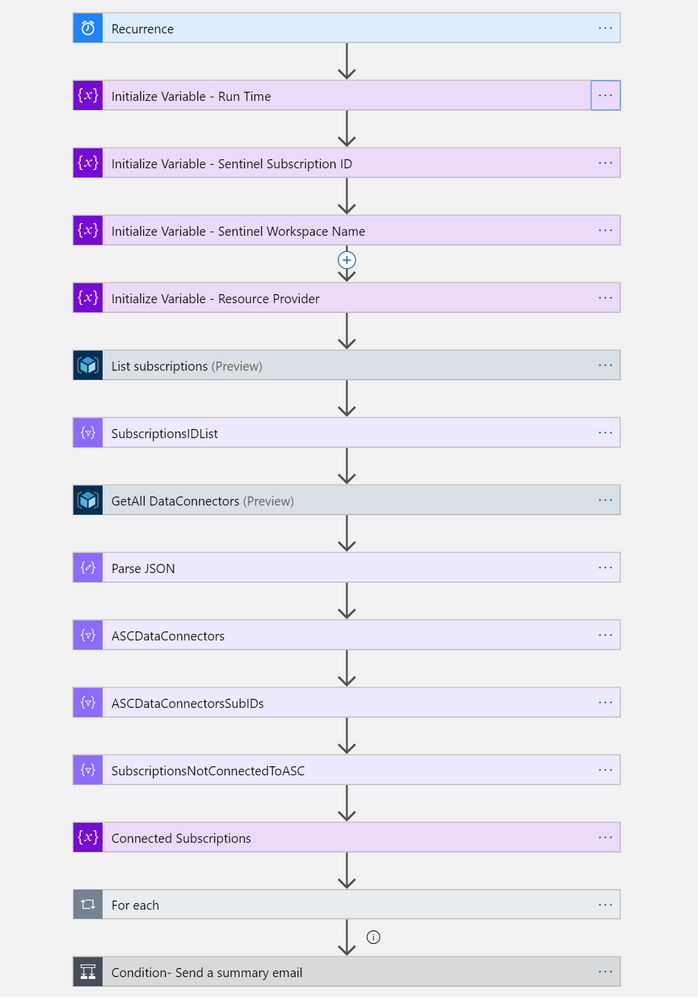
An Azure Logic Apps workflow (playbook) is triggered on a scheduled basis.
It is running on behalf of a registered Azure AD application, which monitors a certain management group.
For each subscription this app has access to, if the subscription doesn’t have an Azure Security Center connection enabled, a connection to Azure Sentinel is created.
Playbook can be found in the the Azure Sentinel GitHub repository: AutoConnect-ASCSubcription playbook.
Prerequisites
- ASC is enabled on standard tier
Integration can be enabled only with subscriptions that are running Azure Security Center standard tier.
Getting Started with Azure Security Center
- Management Group selection
Define the management group which the playbook will monitor. It might be the root management group.
- Register an application and grant RBAC roles
- Register an Azure AD application, as explained here.
- Get credentials
In the registered application blade, get the application credentials for later signing in:
Client Id: Under Overview
Client Secret: Under Certificated & secrets you can create a client secret. - Grant permissions
For each of the scopes below, go to Access control (IAM), find the app and add the role, as explained here.
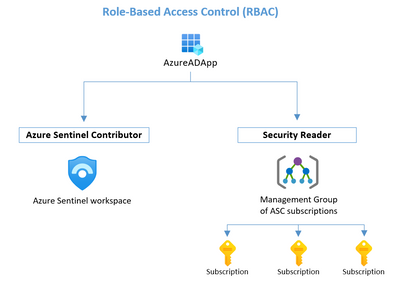
Scope | RBAC Role |
Management Group | Security Reader |
Azure Sentinel Workspace | Azure Sentinel Contributor |
Playbook deployment instructions
- Open the link to the AutoConnect-ASCSubcription playbook. Scroll down on the page and Click on “Deploy to Azure” or “Deploy to Azure Gov” button depending on your need.
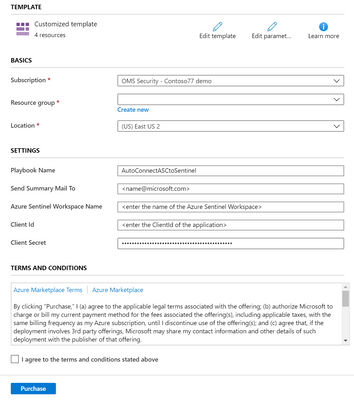
- Fill the parameters:
- Basics
Fill the subscription, resource group and location Sentinel workspace is under. - Settings
- Playbook name
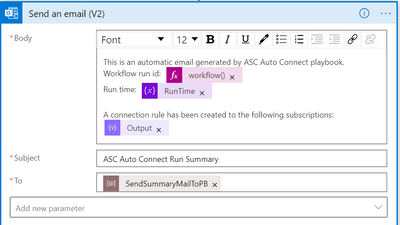
- Send Summary Mail to:
Choose recipients to get an email in case a new subscription was connected. - Azure Sentinel Workspace Name
- Client Id of the registered application
- Client secret of the registered application
- Basics
- Check the terms and conditions and click purchase.
Configure your playbook
Go to the Logic Apps designer view.
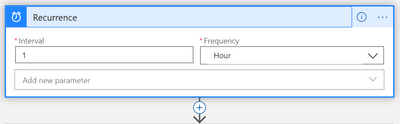
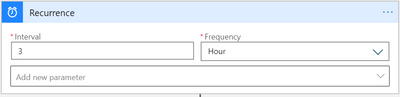
- Choose your time interval:
In Logic Apps designer, under “Recurrence” (first action), choose the preferred interval and frequency in which the playbook will run. - Confirm connections, and edit the actions, for Logging:
Log Analytics (Azure monitor Logs)
Authenticate:
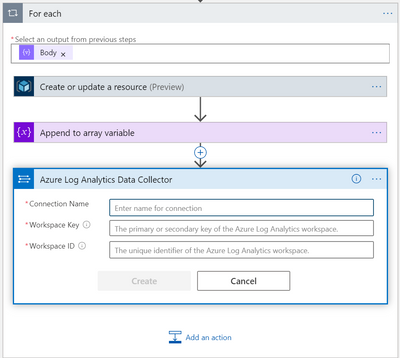
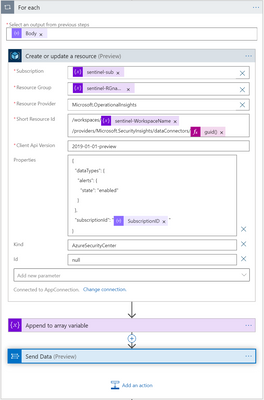
In the “For Each” loop, configure the connection for the “Send Data” action.
You can choose an available connection from a different Logic App, or create a new one:
If you are creating a new connection, Workspace Key is provided under:
Azure Sentinel -> settings -> Workspace settings -> advanced settings -> advanced settings.
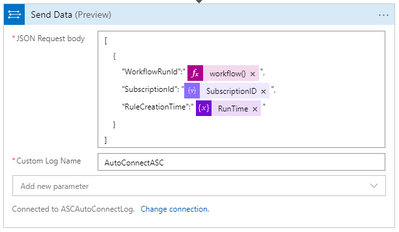
You can change the log contents and Custom Log name:
Office (outlook):
Authenticate:
Edit mail that will be sent in case of new subscriptions:
Azure Logic Apps workflow (playbook) explained
- On a scheduled basis (configurable), ASC-AutoConnect playbook is triggered.
Recurrence trigger (built in trigger)
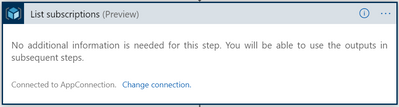
- Playbook scans all the subscriptions an Azure AD registered application has access to.
It gets a list of all the subscriptions under a management group which the application was granted a Security Reader RBAC role.
List Subscriptions action (Connector: Azure Resource Manager)
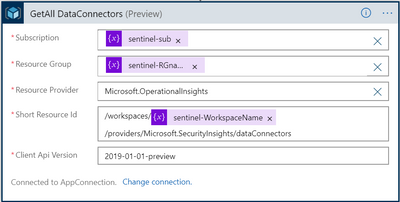
- Playbook then queries Azure Sentinel for all the existing data connections to ASC.
Read a resource action (Connector: Azure Resource Manager)
For each subscription which is not connected to Azure Sentinel, an ASC connection rule is created.
For each (Built in connector), Create or update a resource action (Connector: Azure Resource Manager)
- New ASC subscriptions that were discovered in this run are now connected, and security alerts are streamed into Azure Sentinel.
Full designer view:
Registered application as the identity explained
The playbook actions are operated on behalf of an Azure AD application identity (Service Principal), which has been granted permissions to the following scopes:
- Management Group which ASC subscriptions are under.
This is required for listing all available subscriptions, including new ones which are not connected yet. In some organizations, it is the Root Management Group. - Azure Sentinel workspace.
This is required for checking if a connection exists for a certain subscription, and for creating the connection rule from a not connected subscription to Azure Sentinel.
RBAC required for the application that is running the playbook actions
Q&A
How can I track the connection of new subscriptions?
The playbook includes:
- Custom logging of new connections to Log Analytics custom table.
- Send an informative email to selected recipients in case of new subscriptions added.
Both can be configured after playbook is deployed.
How to be notified only on failure?
Two possible sloutions:
- Use Azure Monitor Alerts
Set up monitor alerts on the Logic App, as explained here.
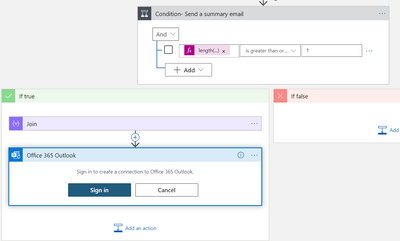
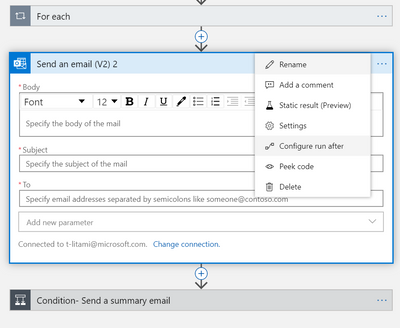
- Add an action to the playbook:
- Add an “Send an email” action between “For each” and “Condition – Send a summary email”.
- Click on the three dots in the right corner of the action, select Configure run after”.
- Check all other conditions other than “is successful”.
I want to be updated in other ways.
Azure Logic Apps offers hundreds of connectors (integrations). This playbook is using “Send and Email” action, but it can be replaced by any other connector you choose, such as Microsoft Teams, Slack, Ticketing system etc.
How can I monitor visually the list of connected subscriptions?
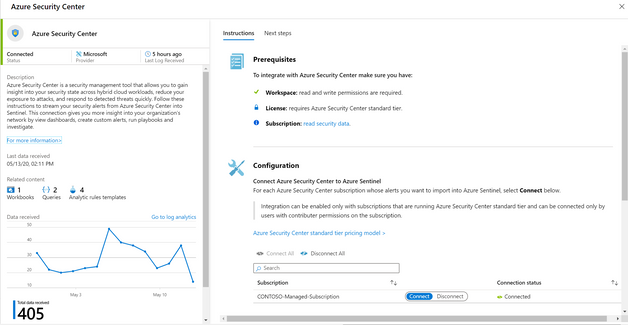
- Azure Security Center connector page can be found In Azure Sentinel portal, under Data connectors.
Note: ASC connector page shows the connection status of subscriptions which your user has at least reader access to. There might be more subscriptions in your organization.
ASC data connector page in Azure Sentinel
- Use Azure Security Center monitoring workbook, which shows:
- A list of all the subscriptions which have an ASC connection enabled.
- Last log received from each subscription.
- Make an API call:
https://management.azure.com/subscriptions/{subscriptionId}/resourcegroups{resourceGroupName}/providers/Microsoft.OperationalInsights/workspaces/{sentinelWorkspaceName}/providers/Microsoft.SecurityInsights/dataConnectorsapi-version: “2019-01-01-preview”
Documentation references
- Azure Logic Apps
- Azure Management groups as containers of subscriptions to monitor
- Azure Active Directory registered application, assigned with RBAC roles