Generally there are multiple forms of Cyber Threat Intelligence (CTI) categories, “Tactical TI” mainly for observables & indicators – “Strategic TI” for actors intensions, capabilities & motivations (broader trends typically meant for a non-technical audience) – “Operational TI” for techniques , tools & procedures (technical details about specific attacks and campaigns) – “OSINT” for open standard formats and many others.
To maximize the value of the threat intelligence you produce, it’s critical that you identify your use cases and define your objectives before doing anything else via following the TI Lifecyle procedure: “Planning & Direction”, “Collection”, “Processing”, “Analysis”, “Dissemination”, & “Feedback”.
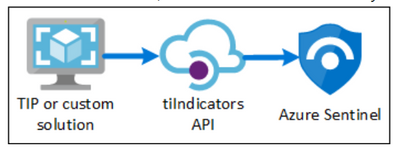
Azure Sentinel provides an out-of-the-box Tactical TI connectors for indicators & observed data that lets you import – stream the threat indicators your organization is using, which can enhance your security analysts’ ability to detect and prioritize known threats. Several features from Azure Sentinel then become available or are enhanced: Analytics , Workbooks , Hunting & Notebooks.
There is a great blog post by
Step (1) – Sign In to your ThreatConnect API User Connection
- Sign in to https://app.threatconnect.com/auth/index.xhtml#/
- Type your system administrator (Organizational role) credentials, for your details about organization role
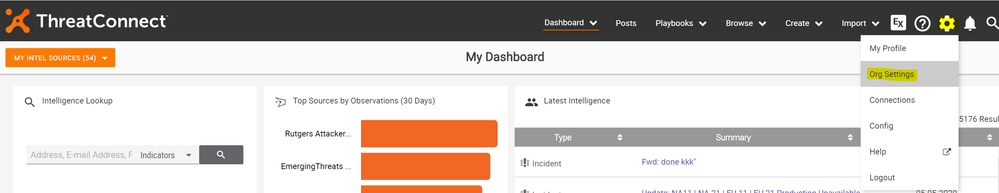
- Click on settings > Org Settings
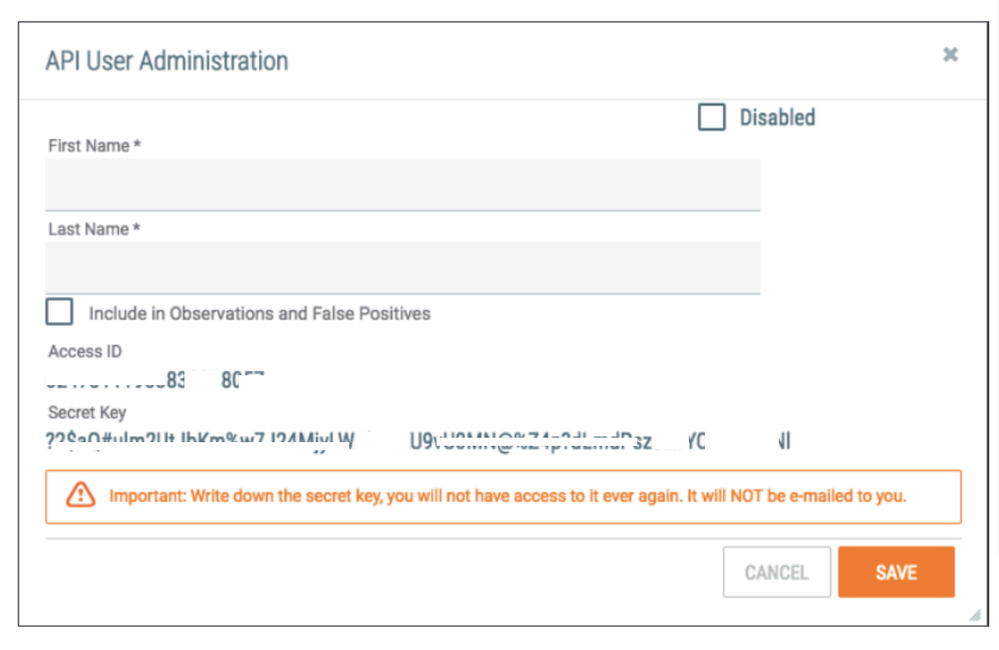
- Under Membership > Create API User, then save the user account and keep the key value
- Keep your Access ID & Secret key
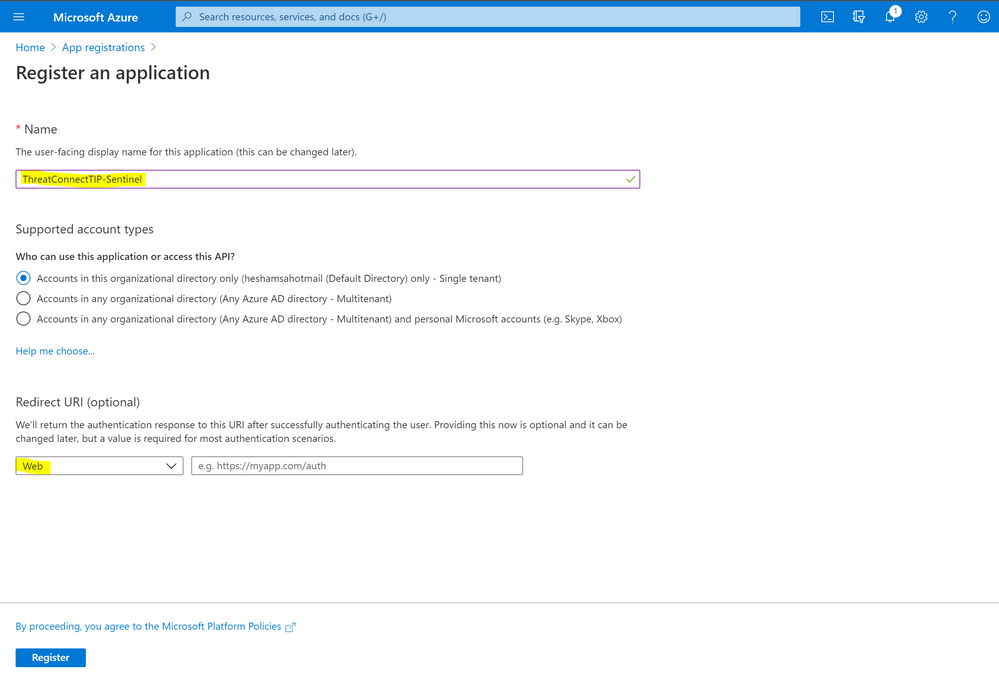
Step (2) – Azure App Registrations
- Sign in to your Azure portal http://portal.azure.com
- Search for App registrations > type a name for your app and click register
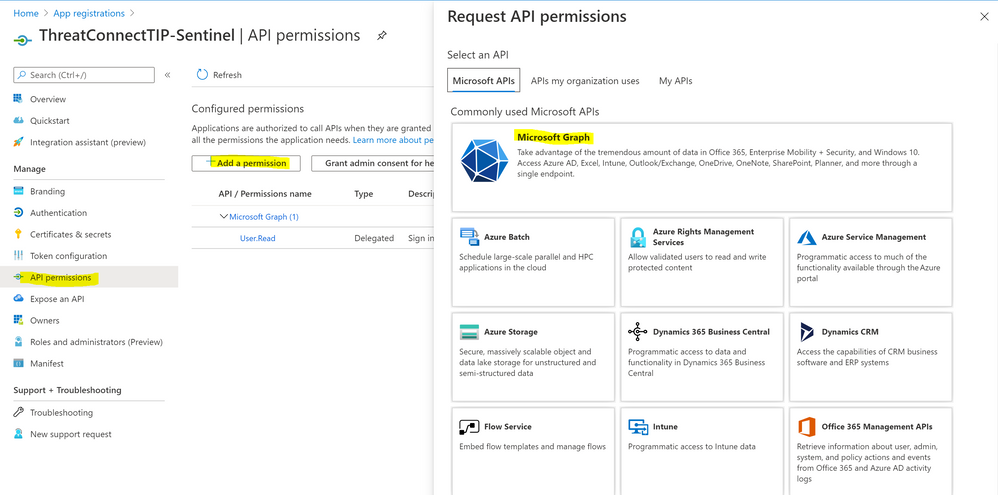
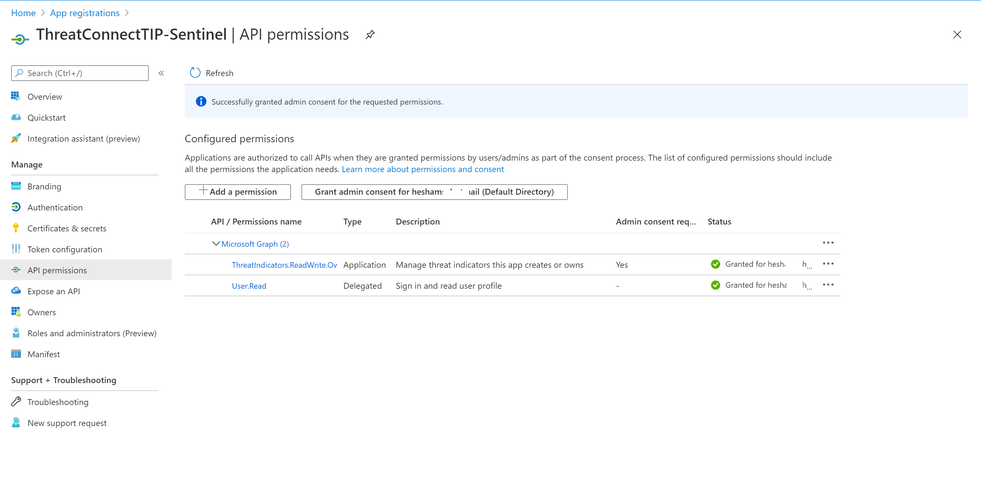
- Under API permissions > Click Add a permission > Select Microsoft Graph
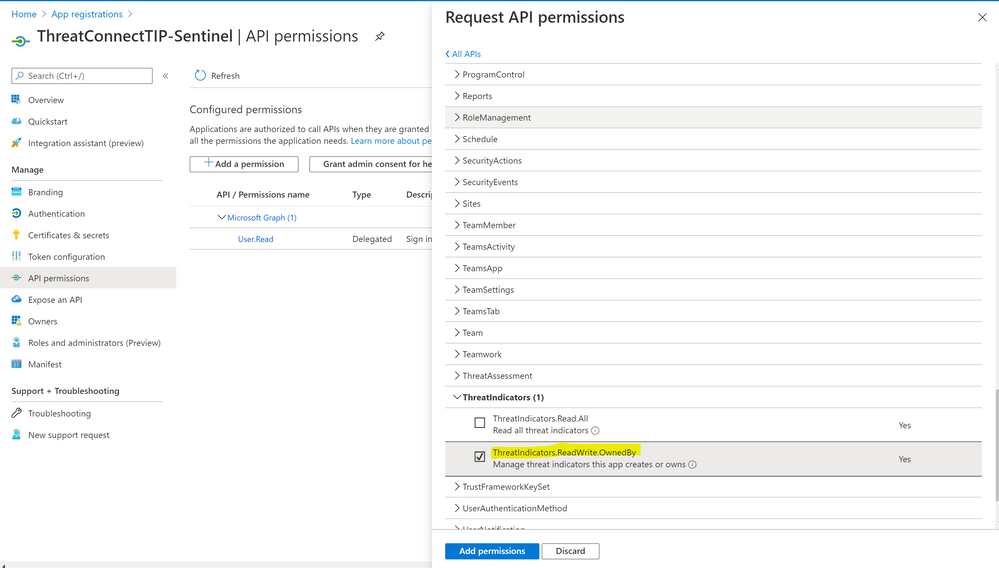
- Select Application permissions > Under ThreatIndicators > Check “ThreatIndicators.ReadWrite.OwnedBy”
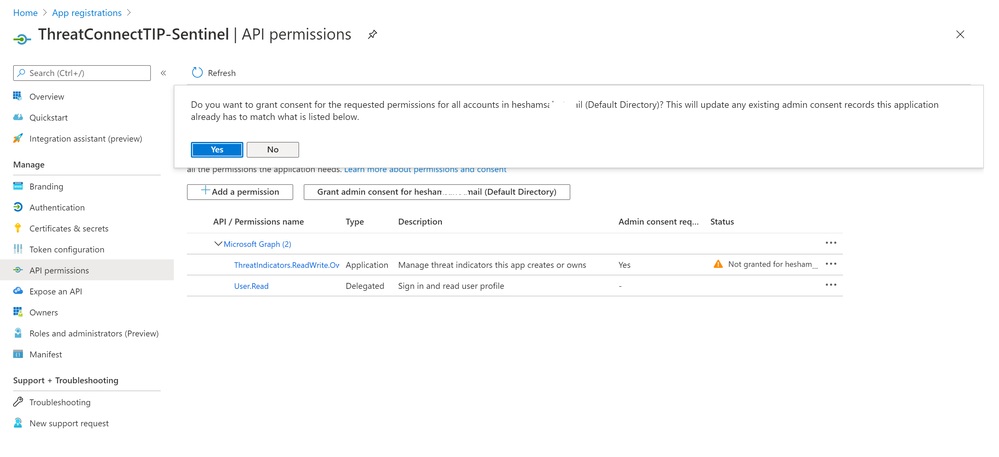
- Click “Grant admin consent” button > Yes
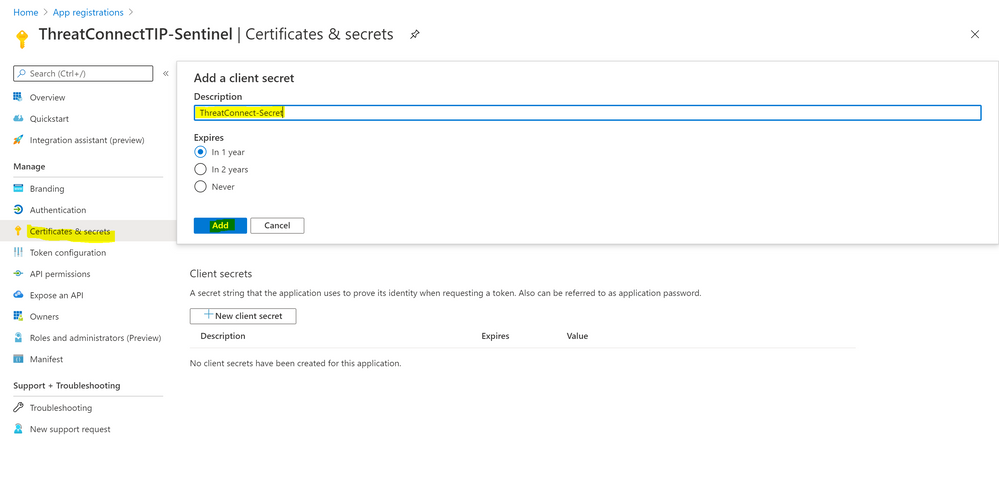
- Click “Certificates & secrets” > New client secret > type a description and select expires option, then Add
- Keep the new registered app “Client ID”, “Secret” and Tenant ID value
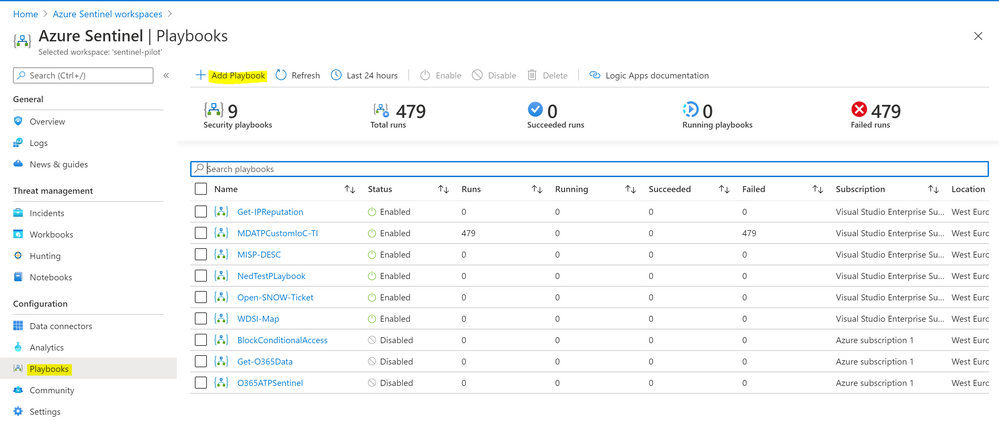
Step (3) – Build the Azure Sentinel Logic App – Playbook
- Sign in to Azure Sentinel
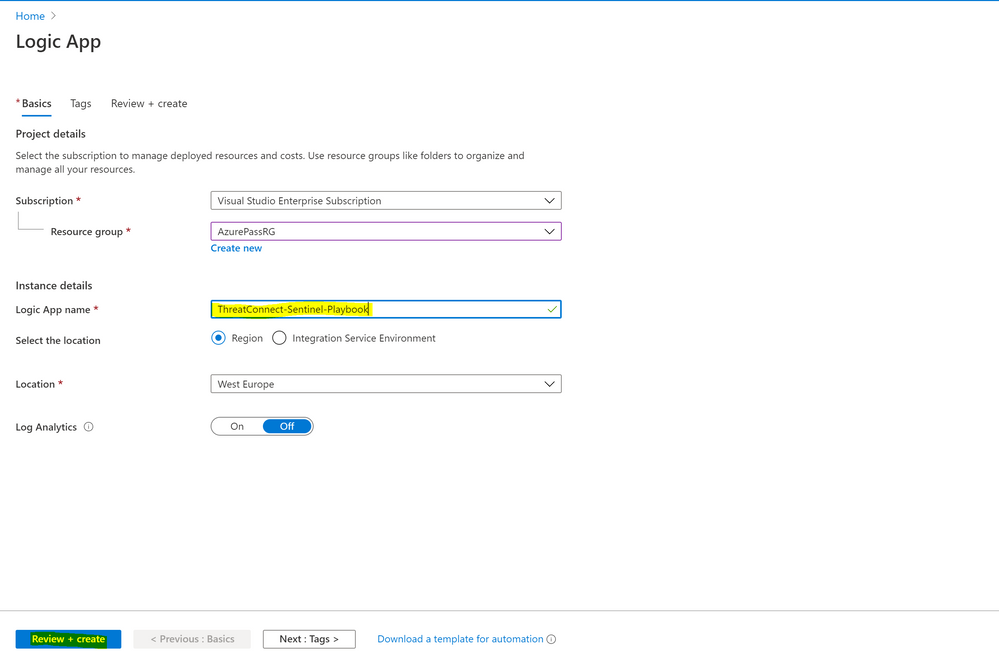
- Under configuration > Playbooks > Add Playbook
- Select subscription, resource group, type Logic App name, select location and click review & create
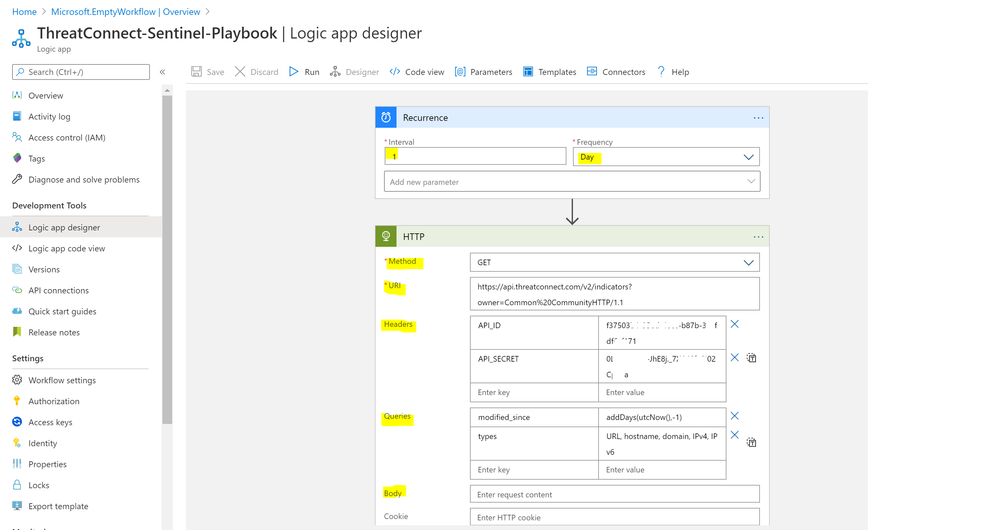
- Select Recurrence as a trigger template:
- Type interval & frequency value
- Add new step > HTTP
- Method: GET
- URI:
https://api.threatconnect.com/v2/indicators?owner=Common%20CommunityHTTP/1.1
- Headers:
- API_SECRET: type API Secret value
- API_ID: type API ID value
- Queries:
- modified_since: addDays(utcNow(),-1)
- types: URL, hostname, domain, IPv4
- Then run the API for body sample to parse and keep the body value
- Noting that here’s a list of the out of the box ThreatConnect Indicators types
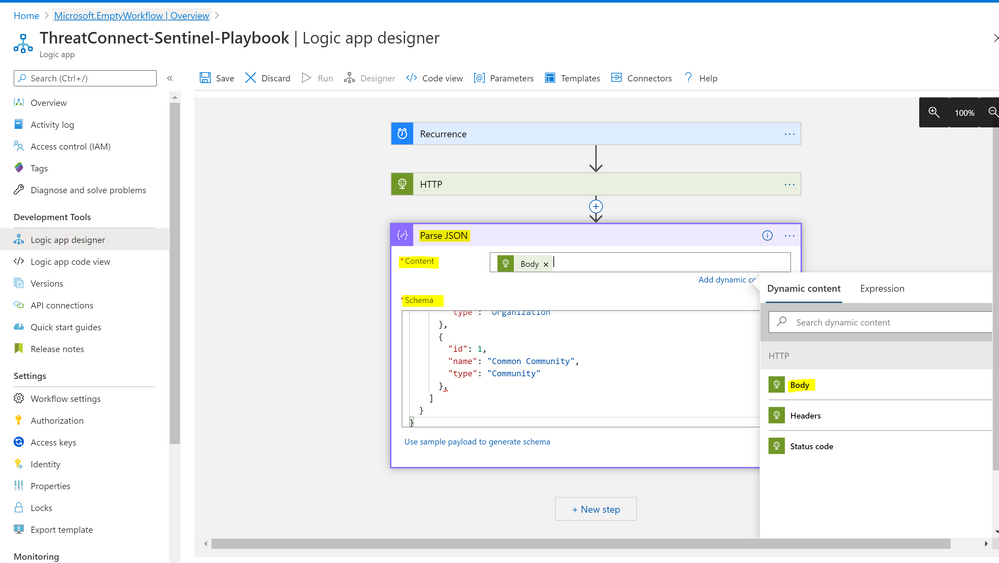
- Add new step > select Data Operations > Parse JSON under actions
- Content: Add dynamic content > Body
- Schema: Paste the copied sample body
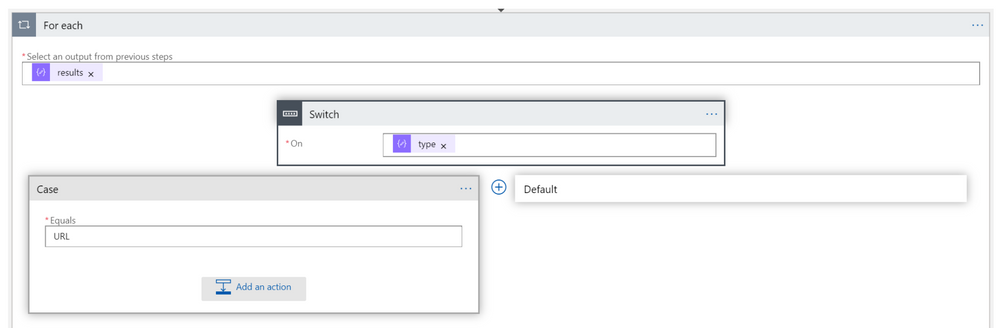
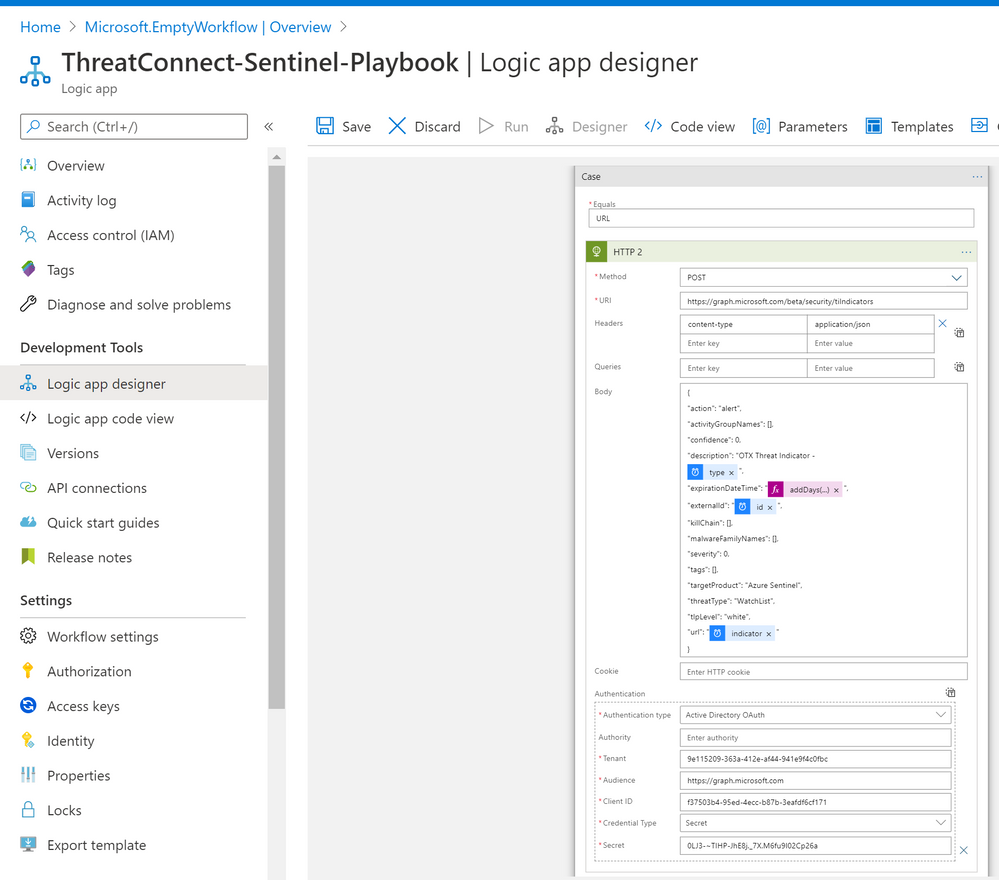
- Now lets add a step to send data to security graph, choose Control and select Switch
- On: Type
- Case: URL
- Under “Case” > Add an action
- Method: POST
- URI: https://graph.microsoft.com/beta/security/tiIndicators
- Headers:
- Key: content-type
- Value: application/json
- Body:
“action”: “alert”,
“activityGroupNames”: [],
“confidence”: 0,
“description”: “OTX Threat Indicator –
@{items(‘For_each’)?[‘type’]}”,
“expirationDateTime”: “@{addDays(utcNow(),7)}”,
“externalId”: “@{items(‘For_each’)?[‘id’]}”,
“killChain”: [],
“malwareFamilyNames”: [],
“severity”: 0,
“tags”: [],
“targetProduct”: “Azure Sentinel”,
“threatType”: “WatchList”,
“tlpLevel”: “white”,
“url”: “@{items(‘For_each’)?[‘indicator’]}”
}
- Check “Authentication”
- Authentication type: Active Directory OAuth
- Tenant: type Azure tenant ID
- Audience: https://graph.microsoft.com
- Client ID: Azure App registrations Client ID value
- Credential Type: Secret
- Secret: Azure App registrations Secret value
- Now you can repeat the steps via a case for each separate indicator type
Step (4) – Azure Sentinel TIP Data Connector & Detections
- Sign in to Azure Sentinel
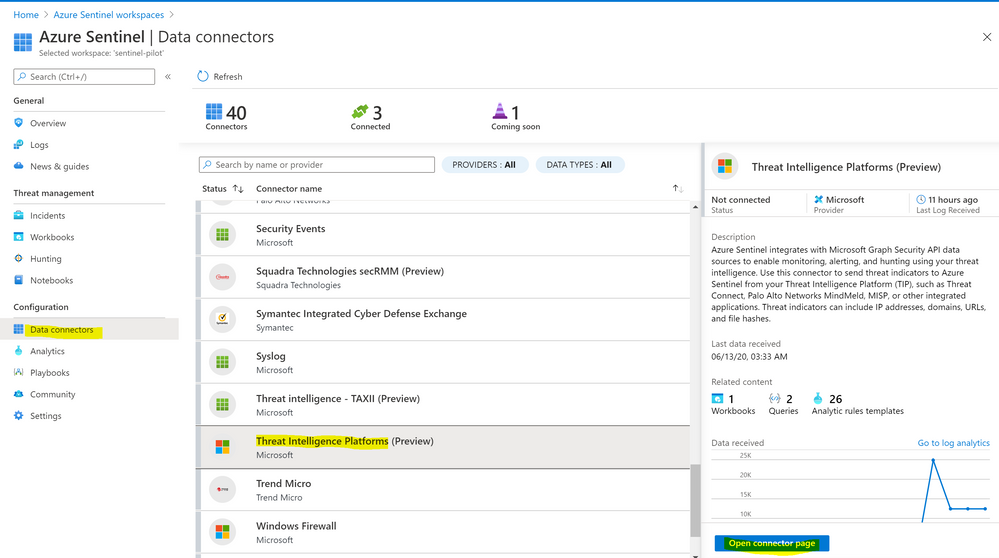
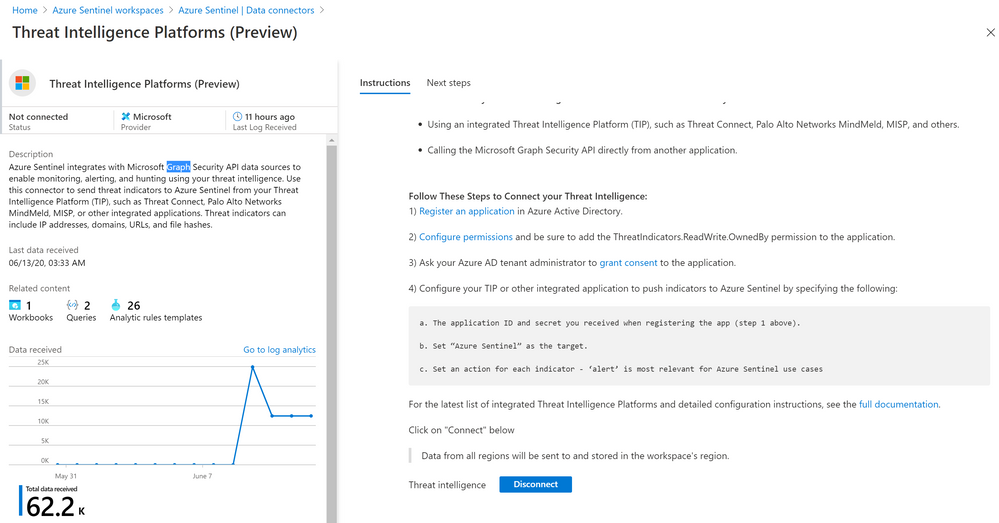
- Under configuration > Data Connectors > Threat Intelligence Platforms > Open Connector Page > Connect Button
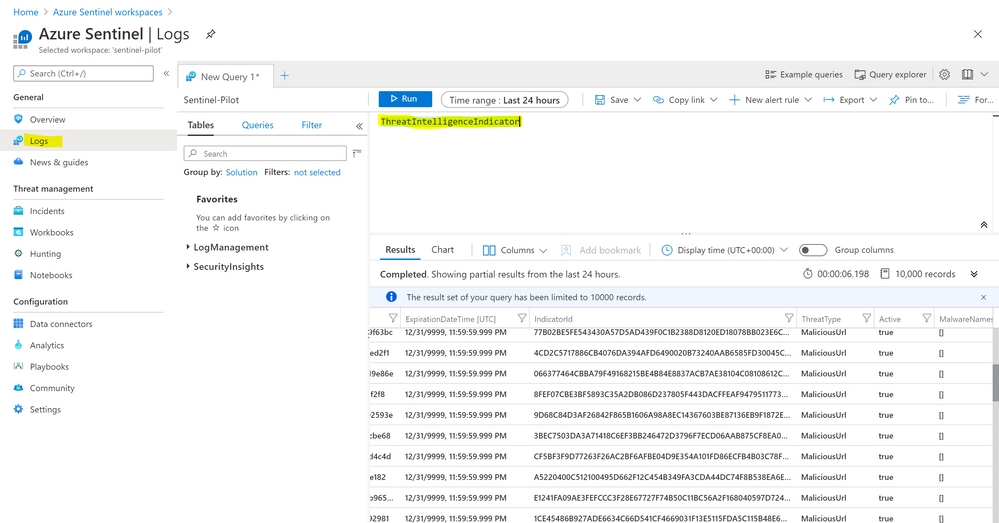
- Now you can query the ingested ThreatConnect indicators – feeds to Azure Sentinel, go to Logs and query “ThreatIntelligenceIndicator” table
- Enjoy as well the out of the box TI analytics rules, feel free to use, reuse , customize or build new rules from scratch: