This blog post is a collaboration between
For those that have wanted to get into the Azure Sentinel notebooks, but are more comfortable with PowerShell than Python, we have news for you. Using the latest version of the Azure Sentinel notebooks, you can now enable PowerShell notebooks via .Net Interactive Public Preview.
To get started, you will need to install .Net Interactive Public Preview on your notebook server and enable the PowerShell kernel. This article also includes a companion Azure Sentinel PowerShell notebook to get you started and be sure to check out the Azure Sentinel notebook official documentation for details on configuring the environment.
What are PowerShell Jupyter notebooks?
The Jupyter notebook is an interactive open source programming tool for data analytics and visualizations. A notebook is divided into cells. Each cell is a section that can combine the programming code and its output along with markdown, graphs, comments, API results, and other powerful visuals. An analyst can traverse between cells, execute them individually and adjust them on the fly and re-run them if changes are required.
Why PowerShell Jupyter notebooks for threat hunting and investigation?
The interactive nature of notebooks results in iterative and rapid development, as well as code sharing and reuse, thus making notebooks an increasingly popular choice for data scientists and analysts. Notebooks have increasingly become adopted by security analysts to automate frequent mundane tasks, incorporate APIs and visualize and provide context for security datasets. In addition, security analysts can share the code/logic and outcome of a given hunt or investigation which can be run as-is or improved over time. Review this article for a more comprehensive list of capabilities.
Since many security analysts are already comfortable with PowerShell and may already have several go-to scripts for their daily work, PowerShell Jupyter notebooks will help those users embrace Jupyter notebooks to supercharge their threat hunts and investigations!
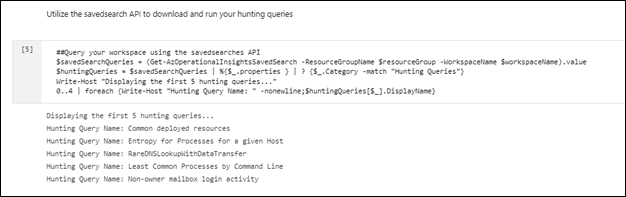
Leverage charts for your incident and/or hunting data:
Access your hunting queries:
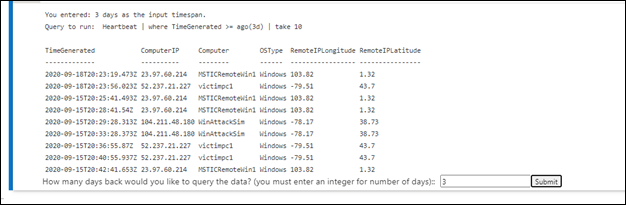
Run KQL queries with interactive input:
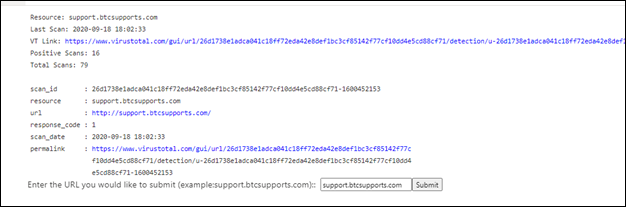
Retrieve scan results from Virus Total:
What is .Net Interactive Public Preview and how do I install it?
.Net Interactive Public Preview is a group of tools and APIs that enables users to create embedded .Net Interactive experiences across the web, markdown and notebooks. This includes the ability to author and run notebooks in C#, F# and PowerShell.
Prerequisites
The instructions below assume you have already deployed your Azure Machine Learning (AML) workspace and compute. If you have not already done so, follow the instructions here.
Installing .Net Interactive on your notebook server
Open terminal window on your notebook server:
Once you see the terminal window, you are ready to start:
Check Ubuntu version
Install the .Net SDK and the runtime based on your version
These instructions work for version 16.04. Refer to the .Net Core on Ubuntu documentation (article) for definitive guidance.
sudo dpkg -i packages-microsoft-prod.deb
sudo apt-get update; \
sudo apt-get install -y apt-transport-https && \
sudo apt-get update && \
sudo apt-get install -y dotnet-sdk-3.1
Install dotnet interactive tool source
Create a symlink between the installed location of dotnet interactive and your local bin directory:
Install Jupyter interactive
Run Jupyter kernelspec list to verify that PowerShell is listed as a kernel
The output should look like this:
Now you will need to clone the Azure Sentinel GitHub repository to your notebook server. (In the near future this step will not be required as this notebook will be added to the Azure Sentinel notebook portal)
Important:
!! Before you proceed, if you had the notebook UI open, you must refresh your browser to see the .Net kernel options in the dropdown. (yes, they are cached) !!
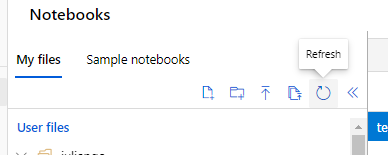
Click ‘Refresh’ in the notebook UI to see the files you cloned:
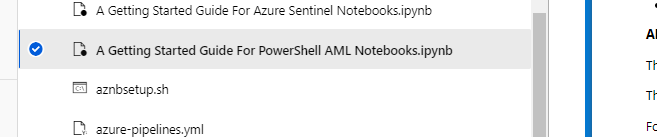
Go to the folder with your cloned files and select the sample PowerShell notebook:
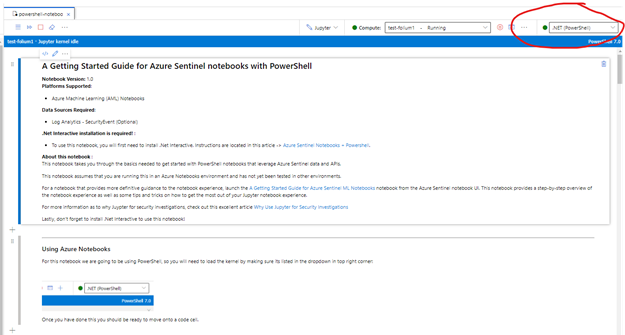
Your notebook is now ready to go, select the PowerShell kernel from the drop down to start: