How to enable and use the new UEBA capability
In your Azure Sentinel portal, navigate to the Threat Management menu, and select Entity Behavior (Preview).
Sync users from Azure Active Directory
Syncing your Azure Active Directory is required for creating profiles for the users and entities in your organization.
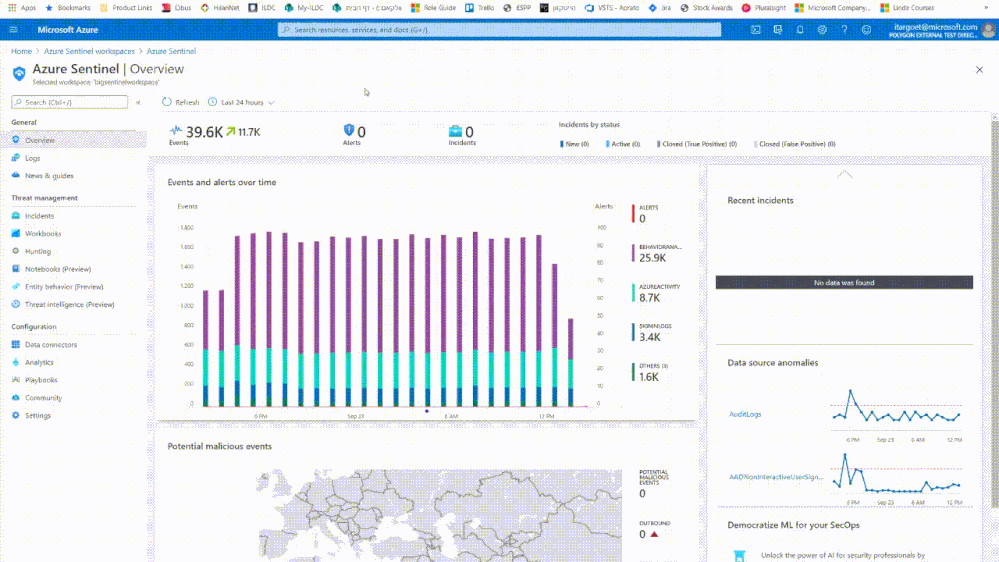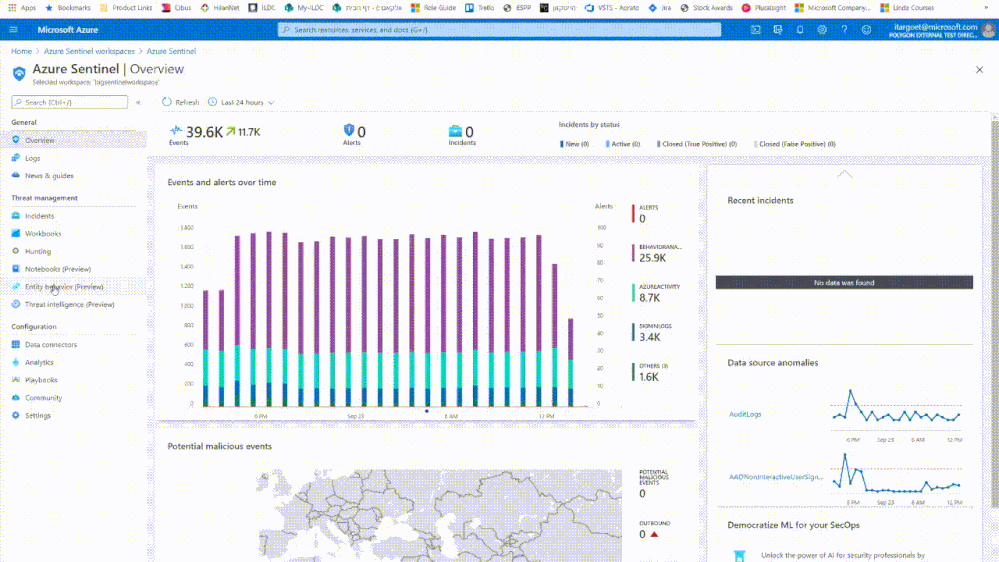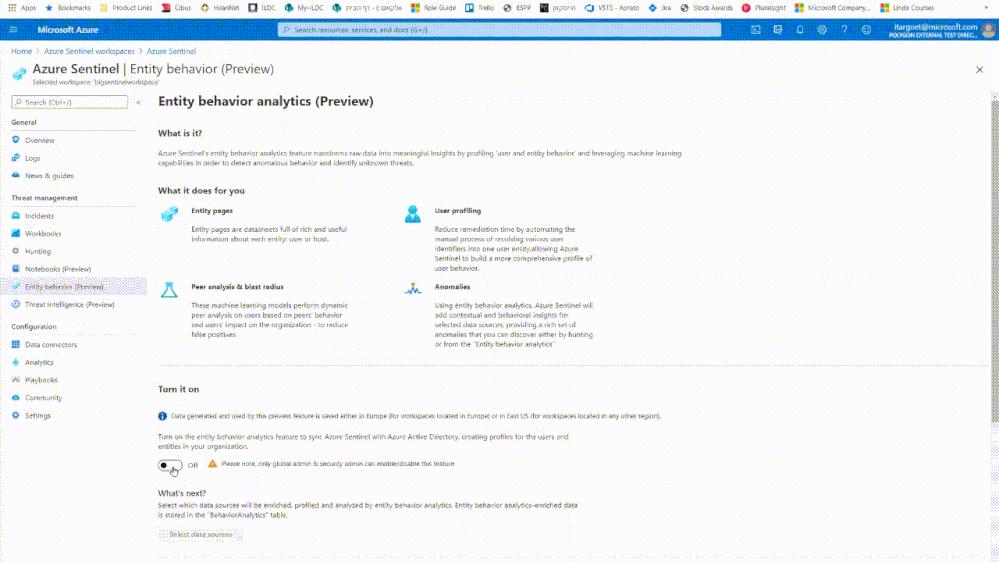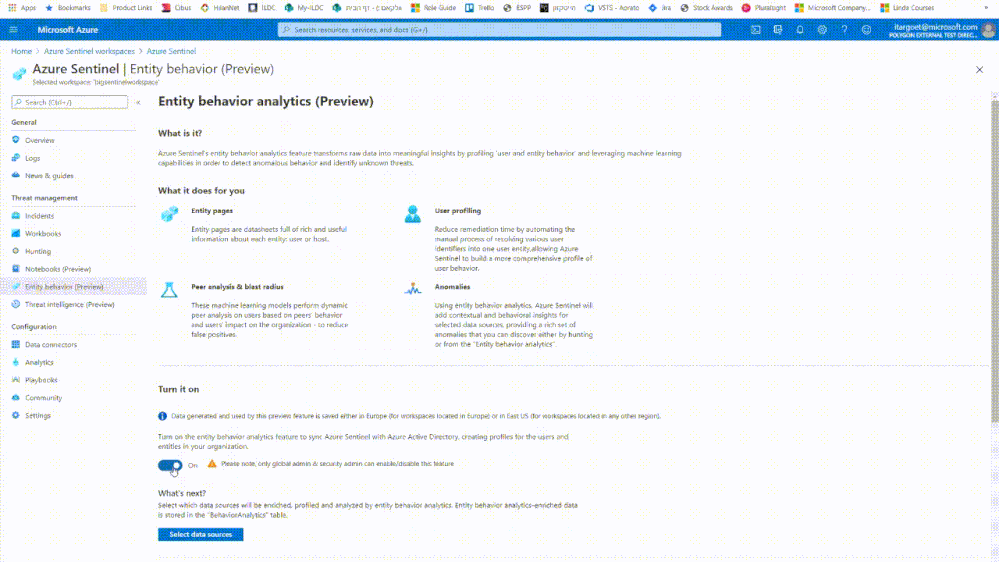
Enabling users syncing from AAD
Selecting data sources for insights & anomalies
Once users information is synced from your Azure AD, and in order to start profiling user activities
you need to select which data sources will be profiled by our UEBA engine.
We currently support
- Security events (Logon events)
- Azure Active Directory Audit logs
- Azure Active Directory Signing logs
- Azure Activity logs
Data source selected will be processed, enriched and profiled by the UEBA engine.

Select data source to be enriched, profiled by the UEBA engine to find anomalies
Investigating user and entities
Entity Pages
When you encounter any entity (currently limited to users and hosts) in a search, an alert, or an investigation, you can select the entity and be taken to an entity page, a datasheet full of useful information about that entity. The types of information you will find on this page include basic facts about the entity, a timeline of notable events related to this entity and insights about the entity’s behavior.
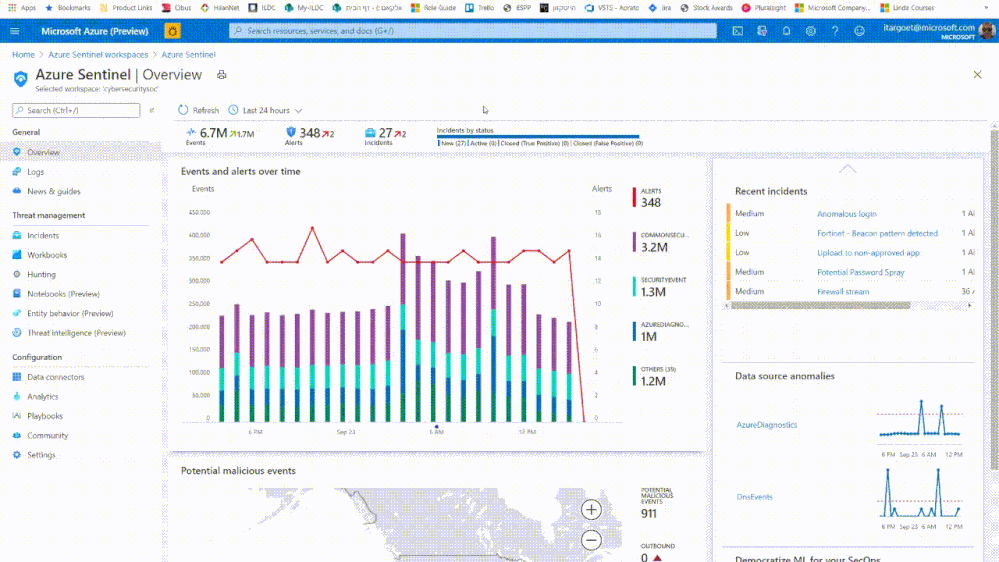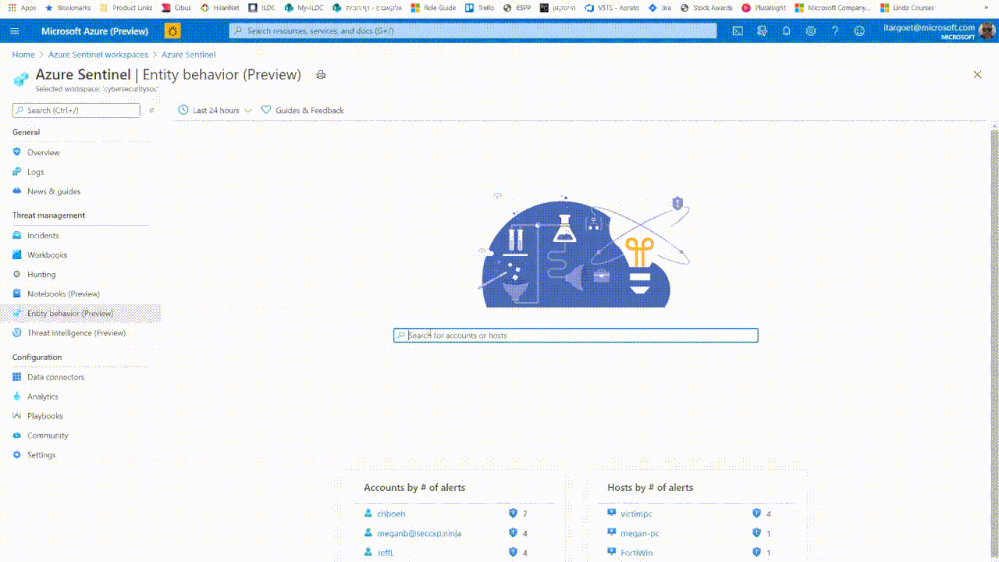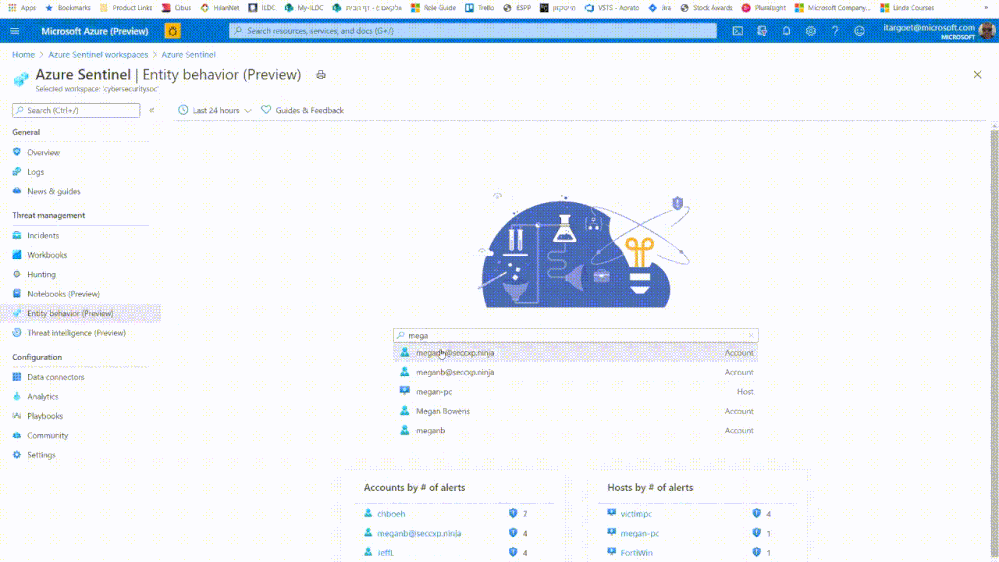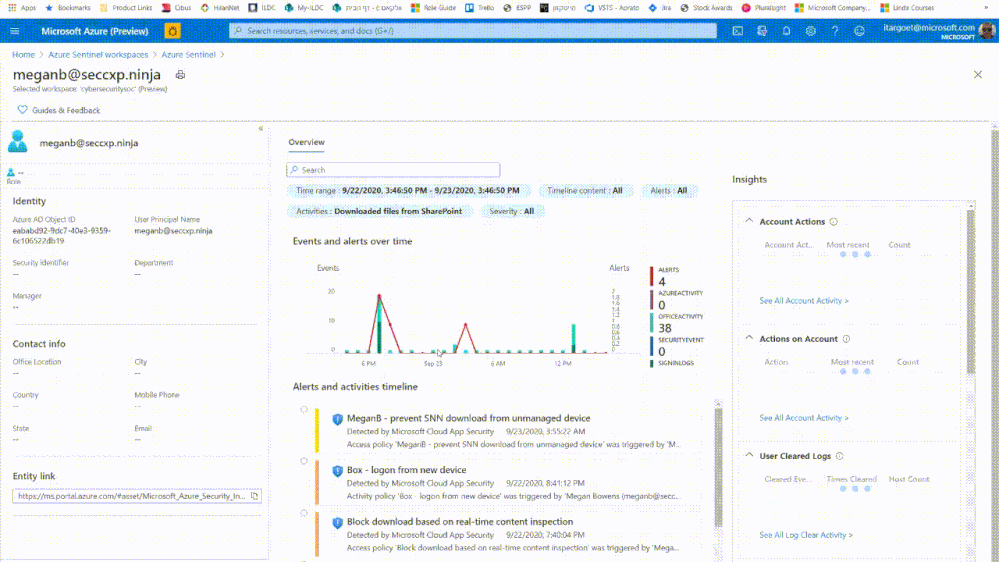
searching for user and accessing the user page
UEBA Workbook
We’ve released a UEBA workbook, focused on user investigation – based on related incidents, alerts and anomalies.
The workbook provide easy viability to the SecOps analyst about the top user to investigate, whether they’re suspected as compromised, or whether it’s an insider threat scenarios where user actions deviates from his profile.
All of our anomalies are based on real life attack scenarios, mapped to MITRE ATT&CK framework.
Each anomaly is scored with “Investigation Priority Score” – which determine the probability of a specific user performing a specific activity, based on behavioral learning of the user and their peers. Activities identified as the most abnormal receive the highest scores (on a scale of 0-10).
UEBA Workbook
Advanced Hunting
Hunting over raw data is something tier 3 analysts or hunters love to do, but sometimes, even simple hypothesis such as:
“Helpdesk user, with high impact on the org, performed some anomalous resource access”
are really hard, or even impossible to do on raw data.
By enriched the data, and storing it back into the customer own log analytics,
Hunters can run complex queries with ease – and have contextual and behavioral information embedded in them– where all the “heavy lifting” of the analytics is done in the engine in the back.
In addition, all our anomalies are available at the ‘Hunting’ blade.
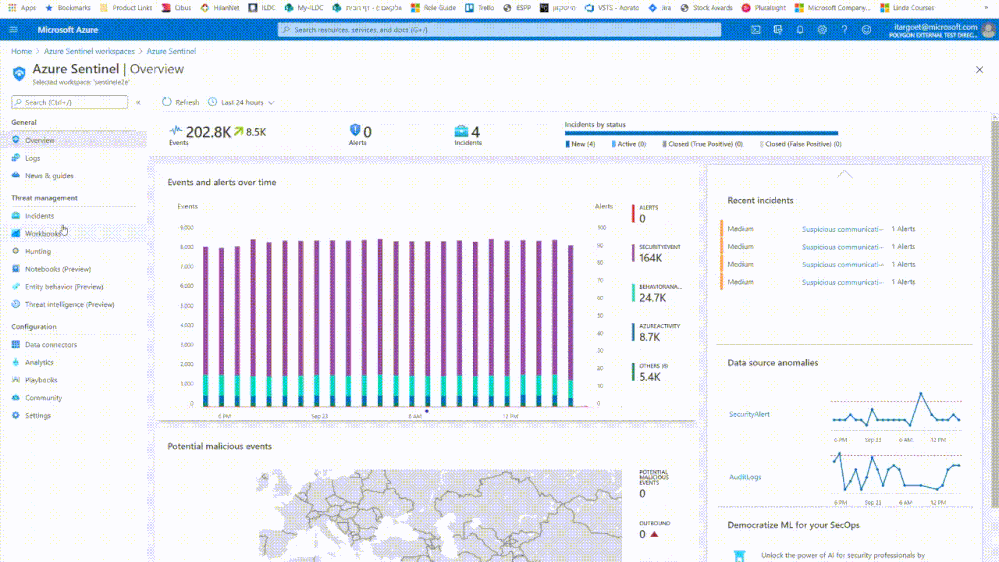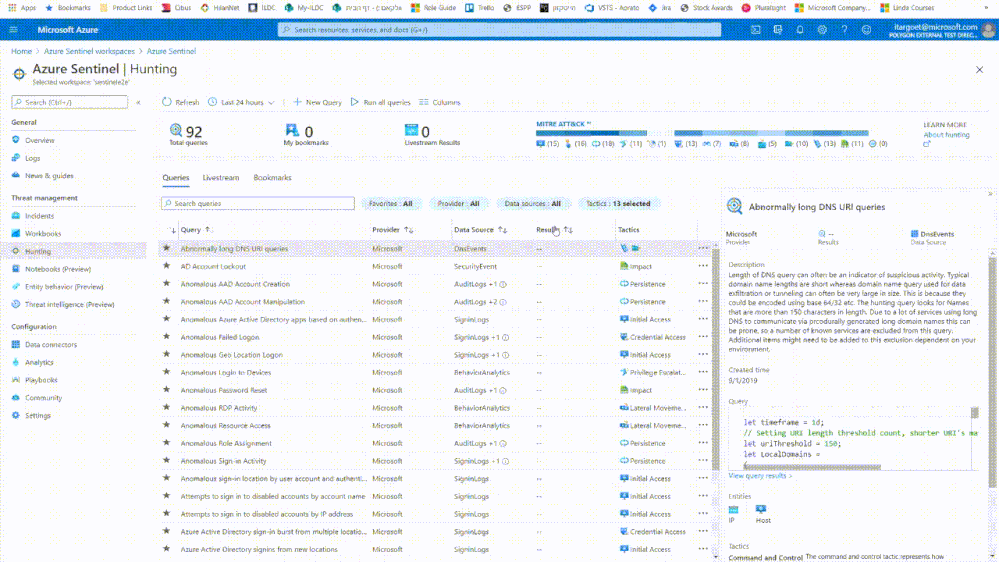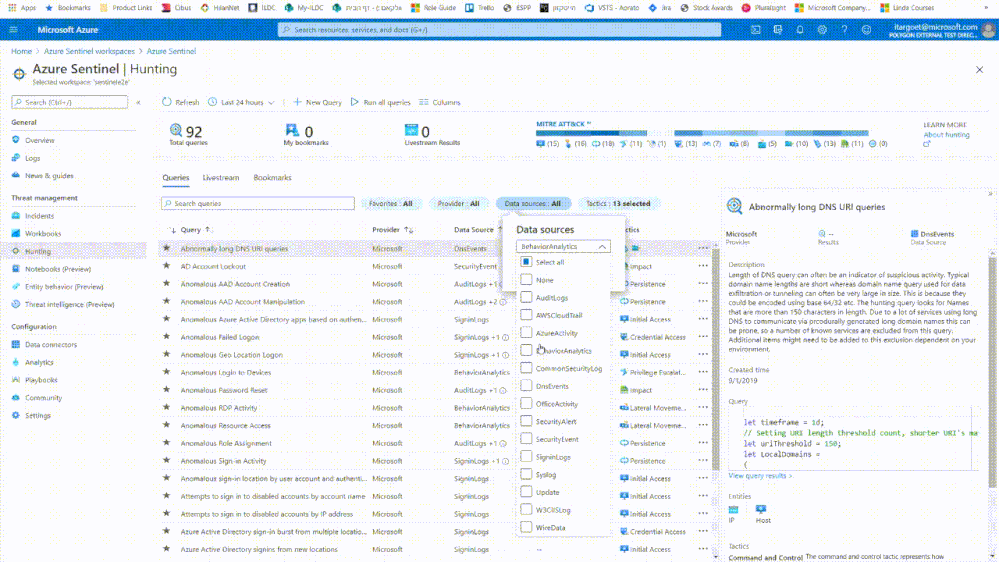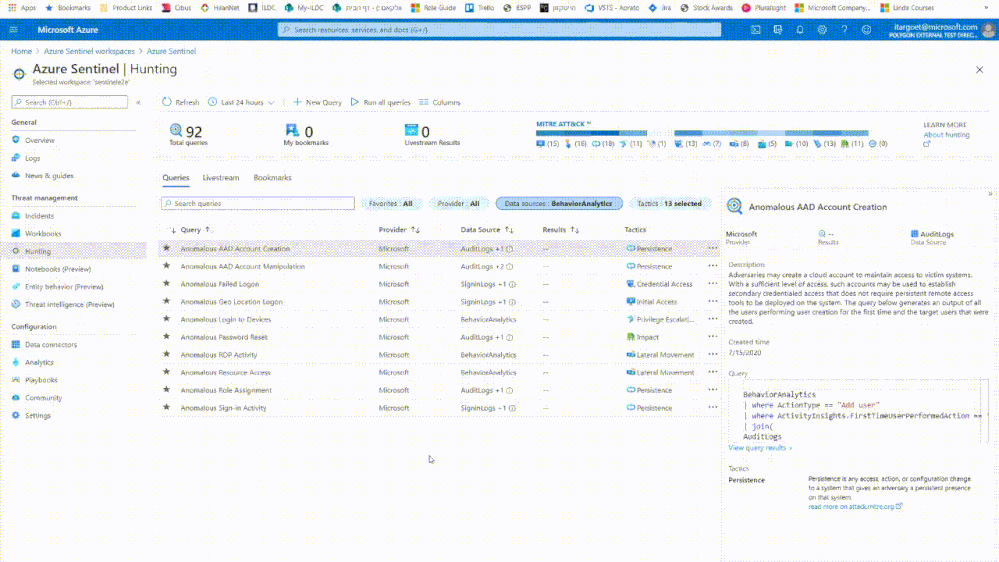
Hunting queries over data enriched with contextual & behavioral information
Guides and feedback
The “Guides & Feedback” panel provides guidance on how to maximize the use of the UEBA feature It also gives you the opportunity to share your ideas and experience with our core engineering team and vote/add your ideas on the Azure Sentinel user voice platform.
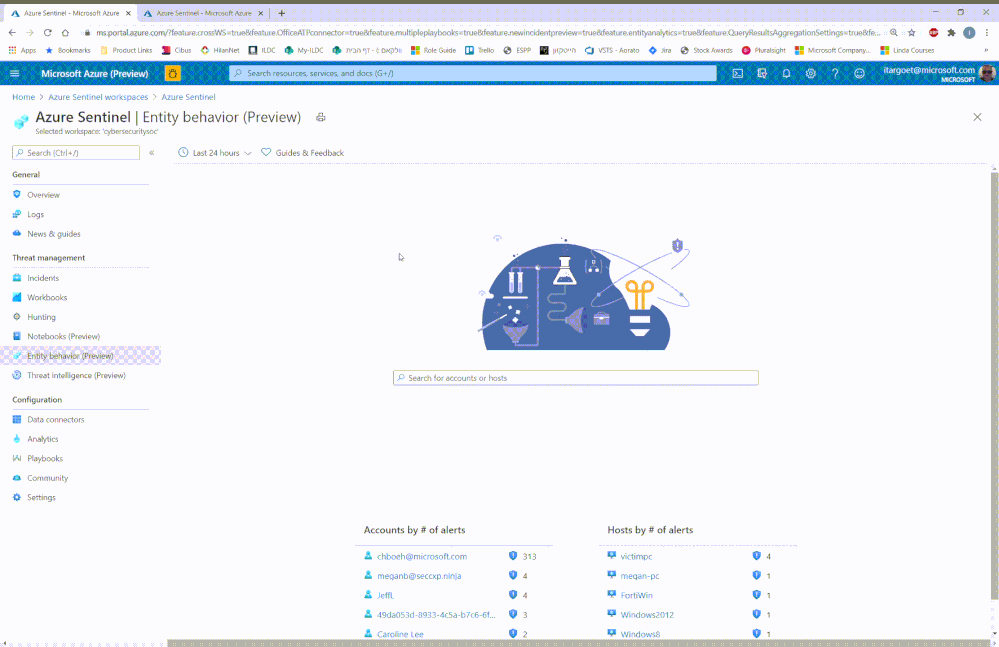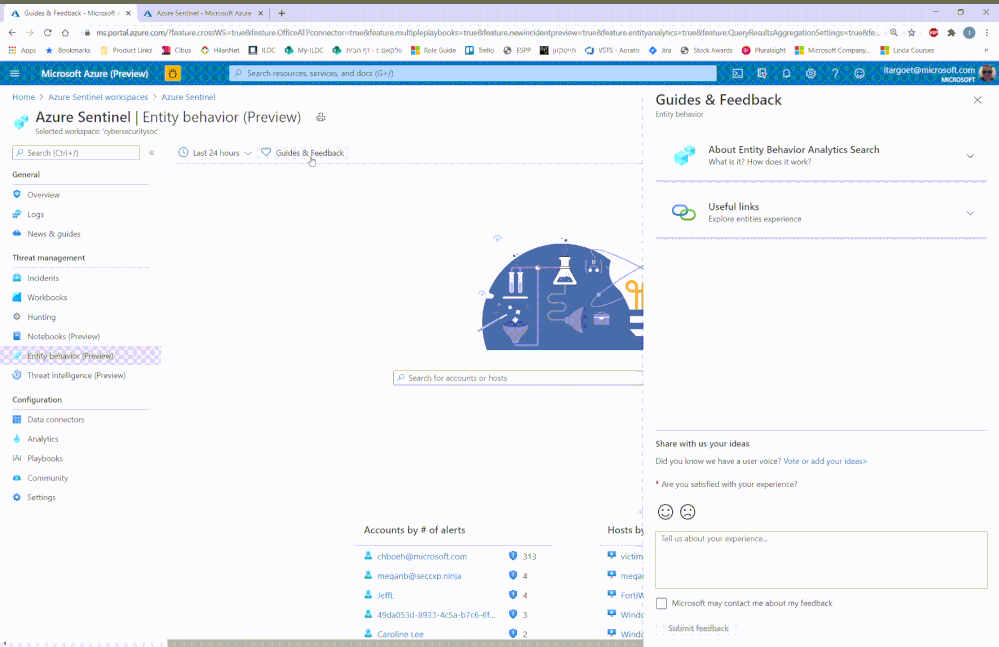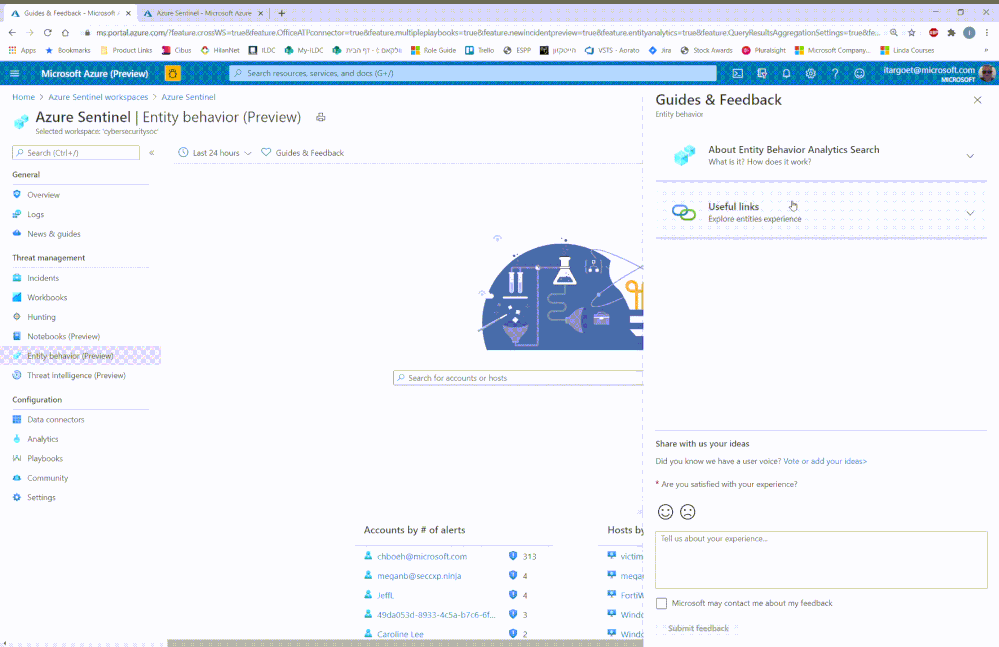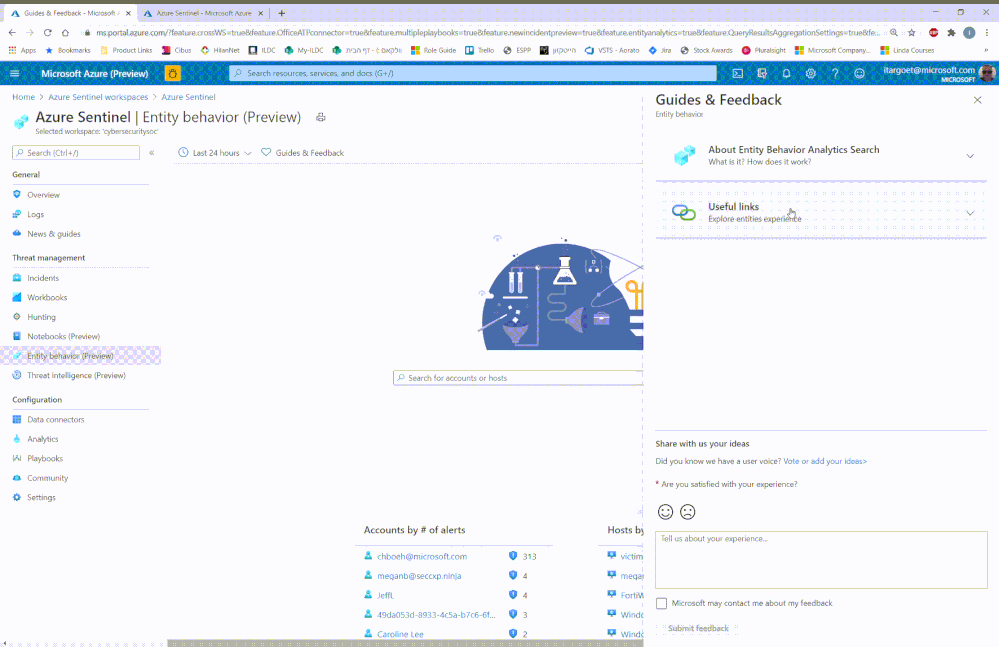
Guides & feedback
These are just a few highlights of Azure Sentinel UEBA. For a full list of the functionalities and the step-by-step instruction on how to use a certain feature on there, please refer to the documentation.
Get started today!
As you can see, enabling Sentinel UEBA is super easy! We encourage you to try it now and start hunting for insider threats and compromised user in your environment.
Try it out, and let us know what you think!
You can also contribute new connectors, workbooks, analytics and more in Azure Sentinel. Get started now by joining the Azure Sentinel Threat Hunters GitHub community.