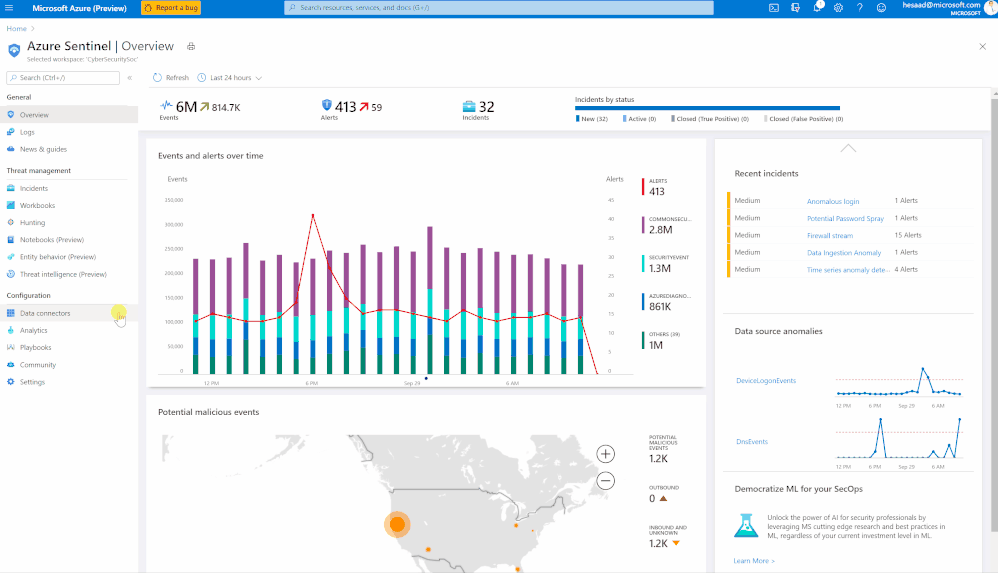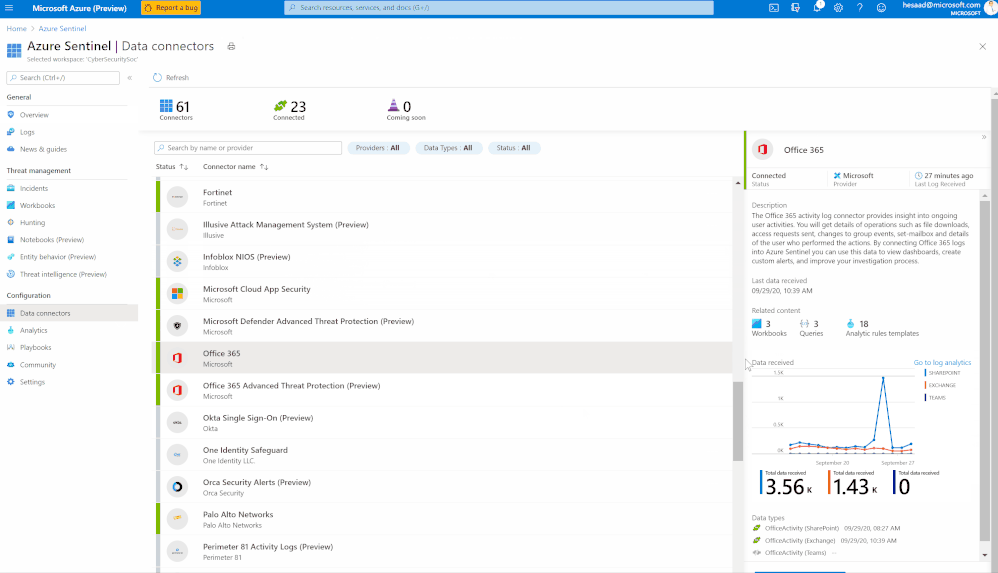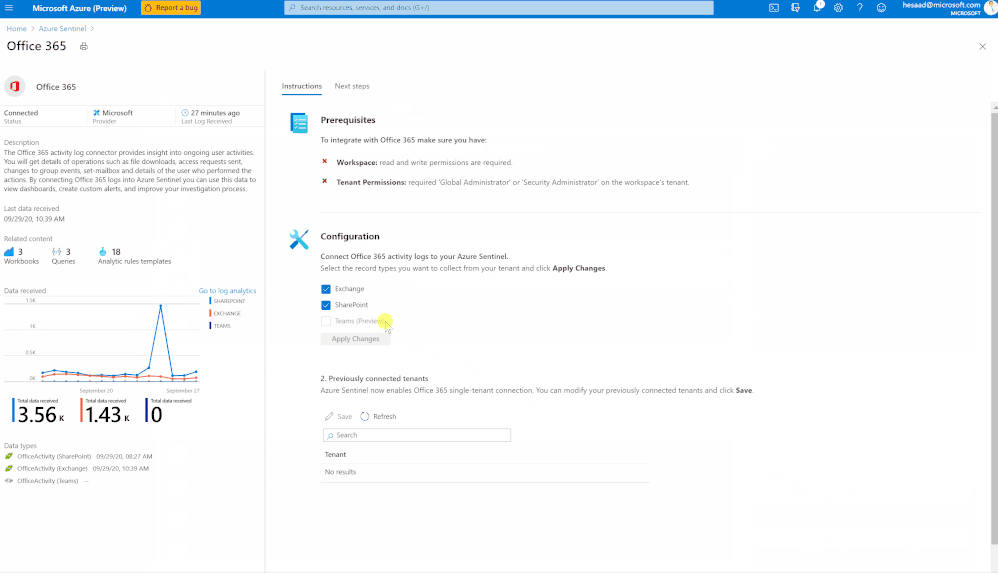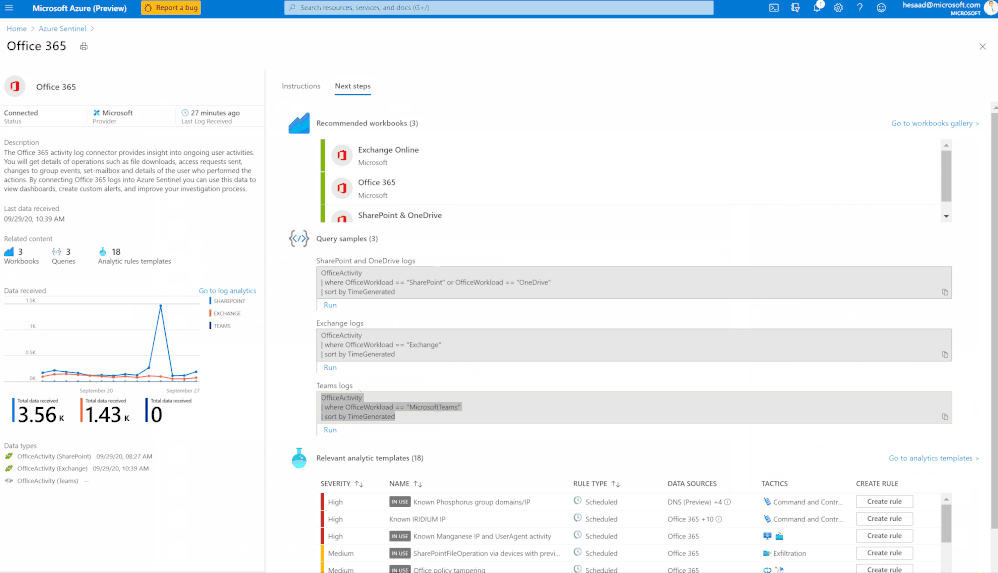
Millions of people are using Microsoft Teams as their secure, productive and mobile collaboration & communication tool, today
Microsoft Teams now has an official connector at Azure Sentinel:

- Easy deployment (in a single checkbox)
- Data into Office Activity
- It’s free activity logs
- Only keep the custom connector for other workloads
Here’s a quick demonstration:
You can check as well a couple of hunting queries been shared on the Azure Sentinel GitHub
Lets understand now Microsoft Teams Schemas:
- Office 365 Management API
- Microsoft Graph API:
What’s in Teams Logs:
- TeamsSessionStarted – Sign-in to Teams Client (except token refresh)
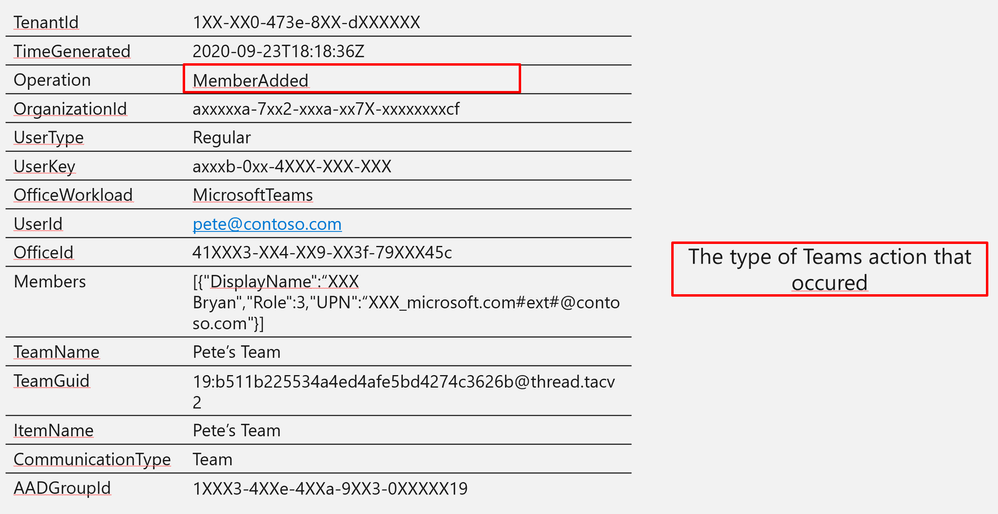
- MemberAdded/MemberRemoved – User added/removed to team or group chat
- MemberRoleChanged – User’s permissions changed 1 = Owner, 2 = Member, 3 = Guest
- ChannelAdded/ChannelRemoved – A channel is added/removed to a team
- TeamCreated/Deleted – A whole team is created or deleted
- TeamsSettingChanged – A change is made to a team setting (e.g. make it public/private)
- TeamsTenantSettingChanged – A change is made at a tenant level (e.g. enable product)
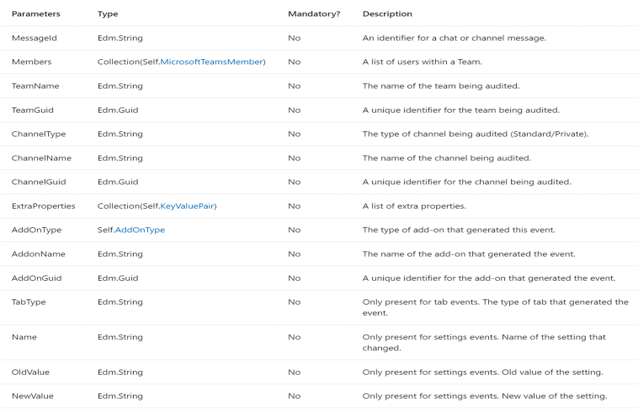
+ Bots, Apps, Tabs
https://docs.microsoft.com/en-us/microsoftteams/audit-log-events
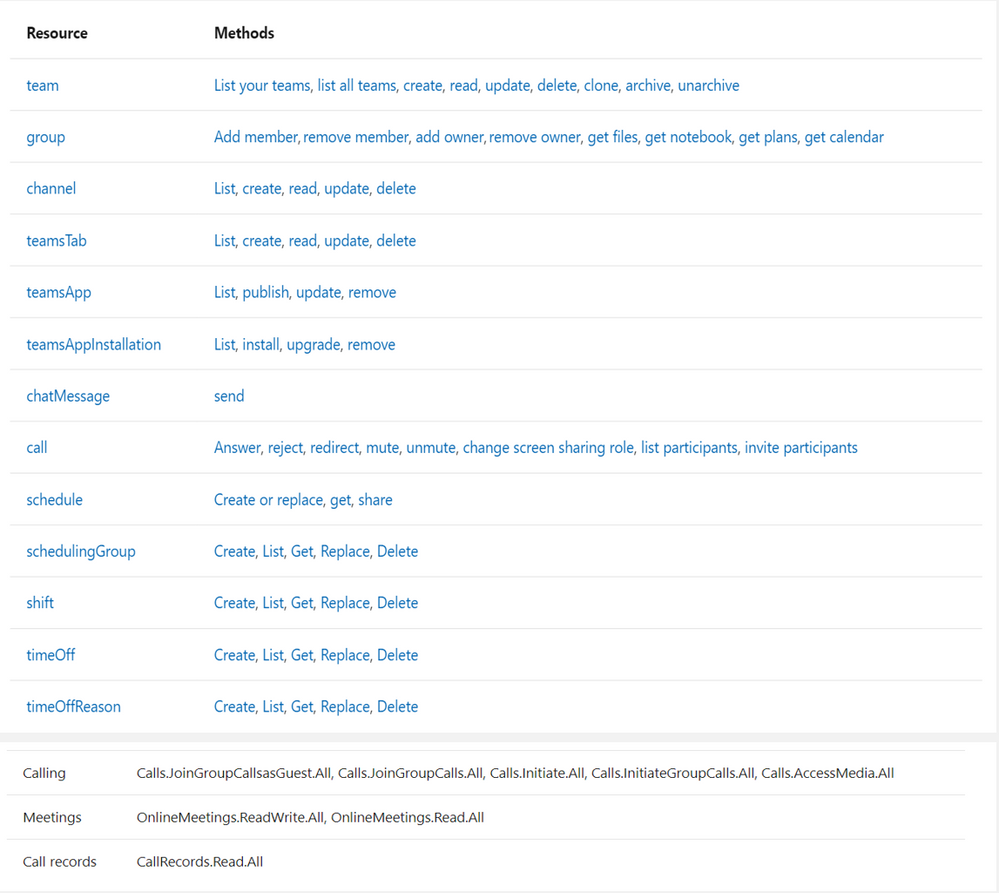
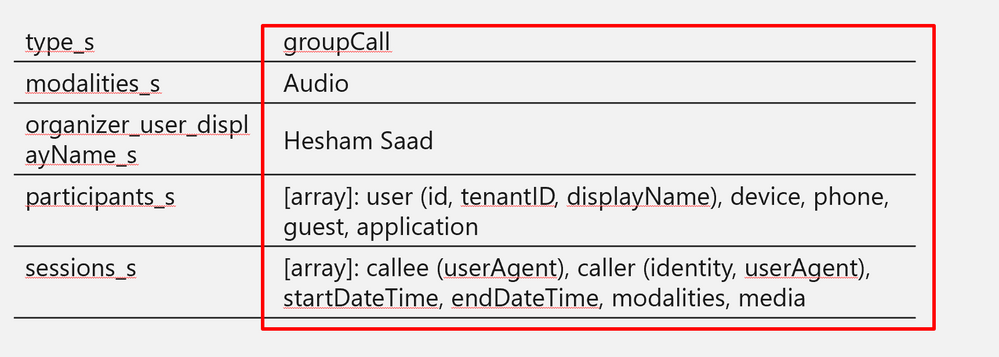
- callRecord: Represents a single peer-to-peer call or a group call between multiple participants, sometimes referred to as an online meeting.
- onlineMeeting: Contains information about the meeting, including the URL used to join a meeting, the attendees list, and the description.
- callRecord/organizer – the organizing party’s identity
- callRecord/participants – list of distinct identities involved in the call
- callRecord/type – type of the call (group call, peer to peer,…etc)
- callRecord/modalities – list of all modalities (audio, video, data, screen sharing, …etc)
- callRecord/ (id – startDateTime – endDateTime – joinWebUrl )
- onlineMeeting/ (subject, chatInfo, participants, startDateTime, endDateTime)
https://docs.microsoft.com/en-us/graph/api/resources/communications-api-overview?view=graph-rest-1.0
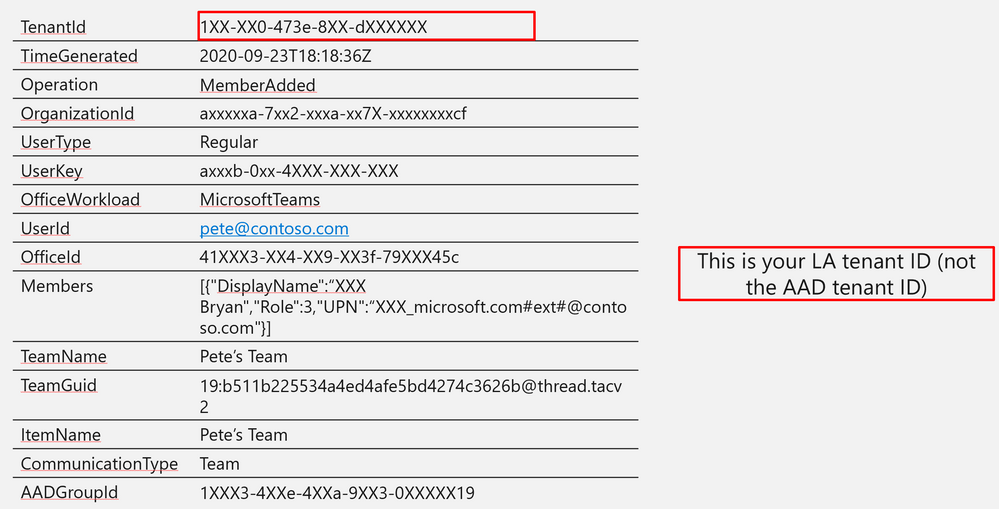
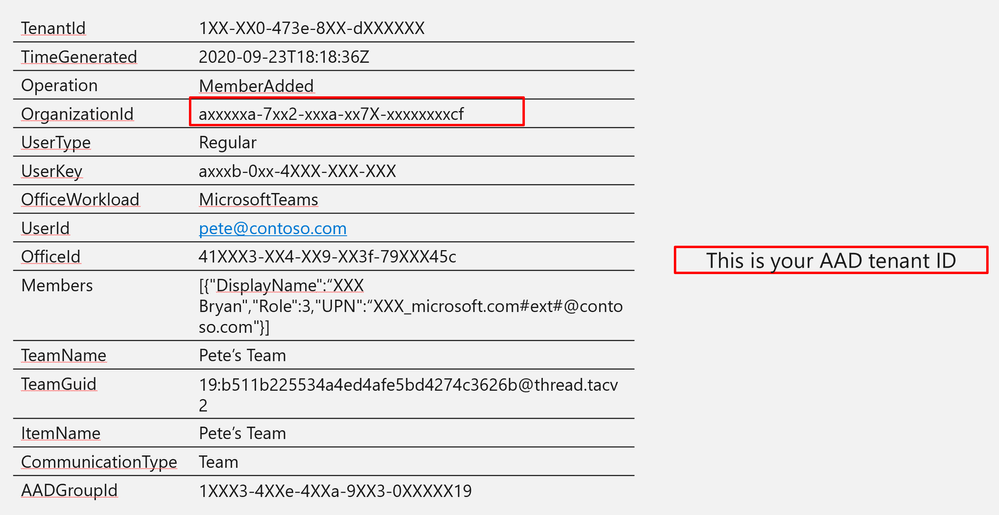
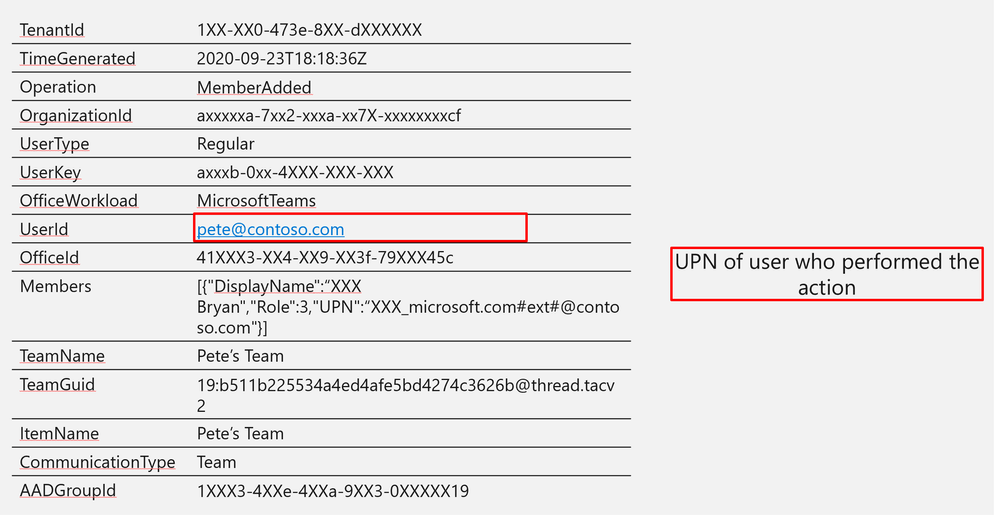
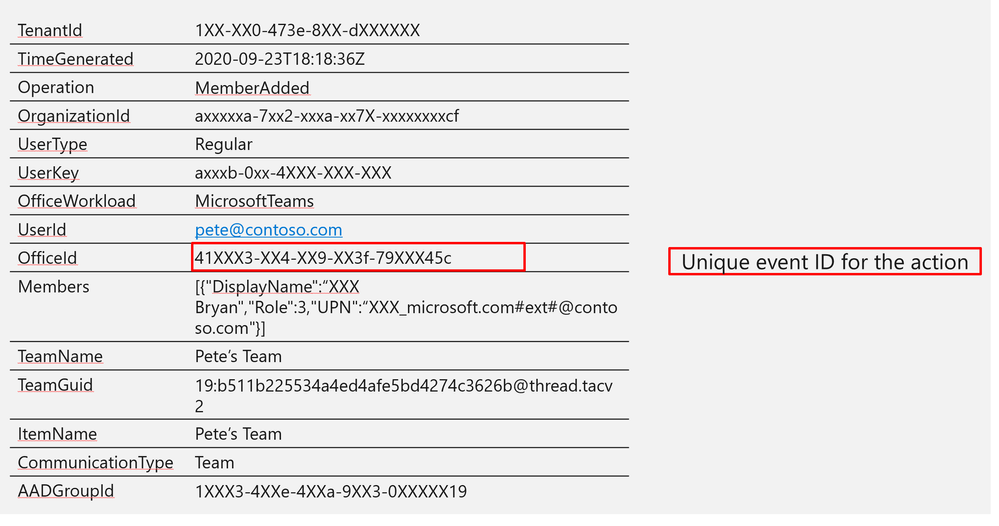
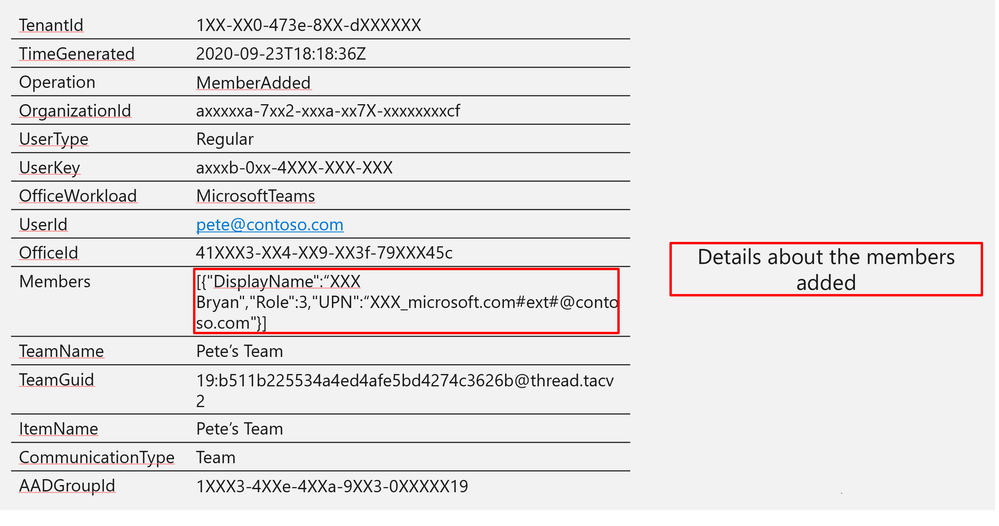
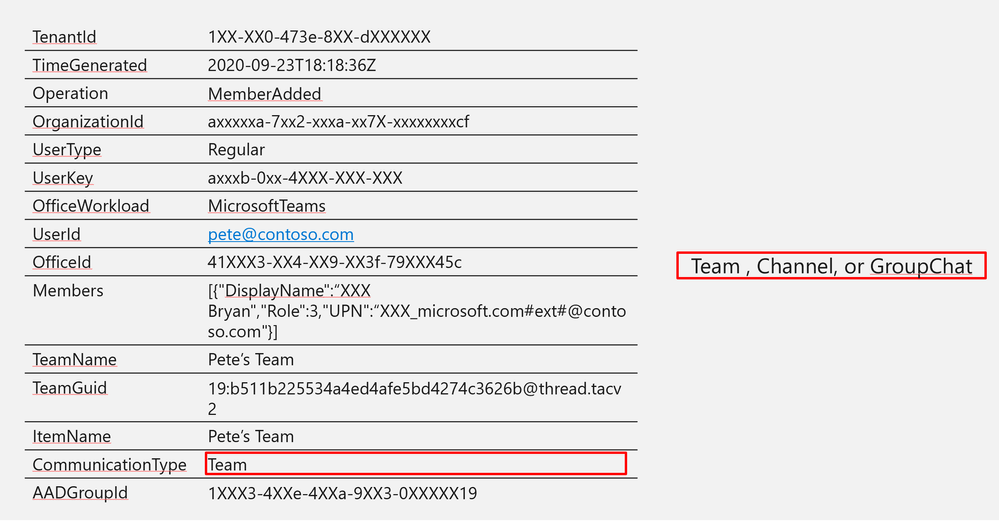
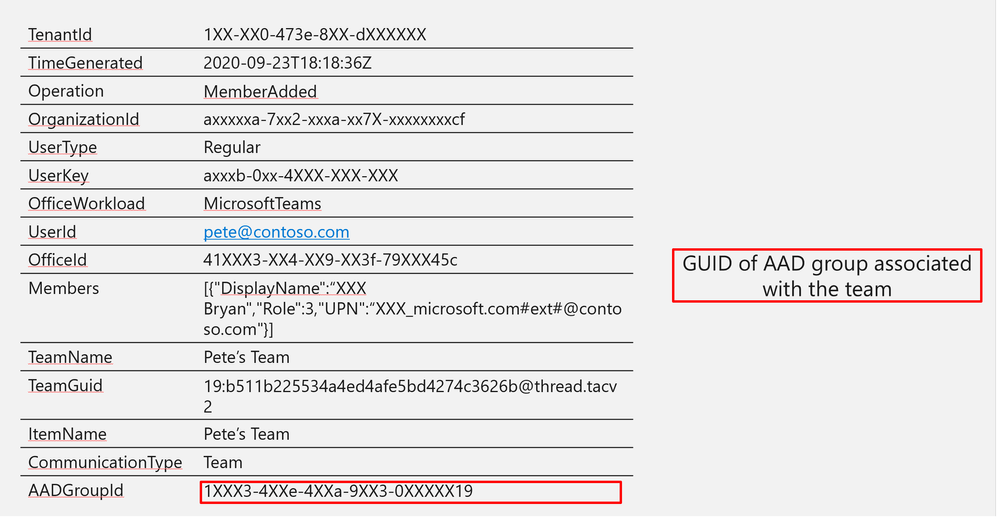
Log Structure:
TenantId | 1XX-XX0-473e-8XX-dXXXXXX |
TimeGenerated | 2020-09-23T18:18:36Z |
Operation | MemberAdded |
OrganizationId | axxxxxa-7xx2-xxxa-xx7X-xxxxxxxxcf |
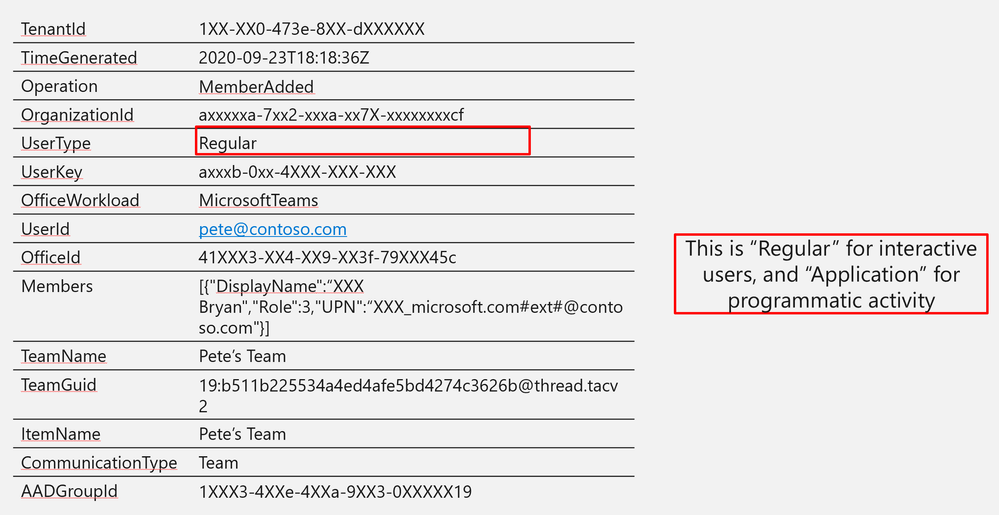
UserType | Regular |
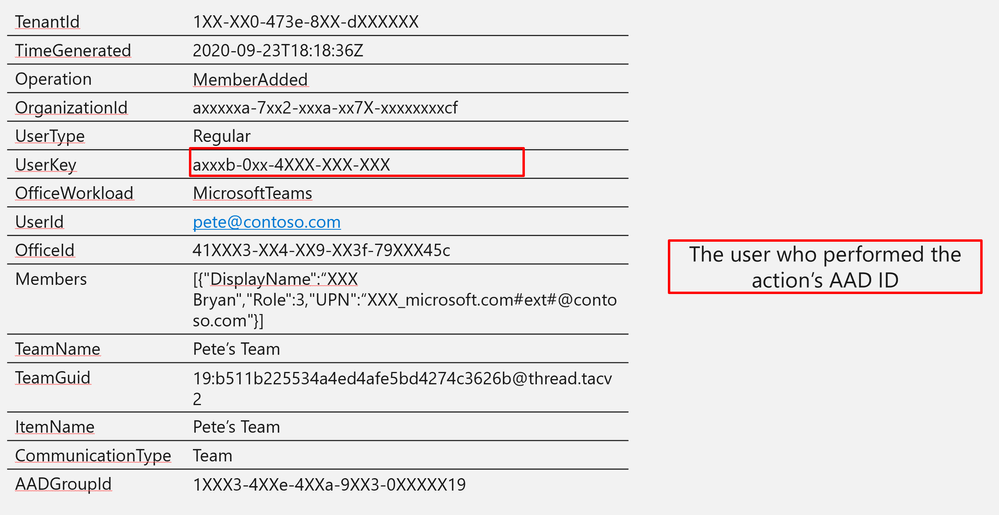
UserKey | axxxb-0xx-4XXX-XXX-XXX |
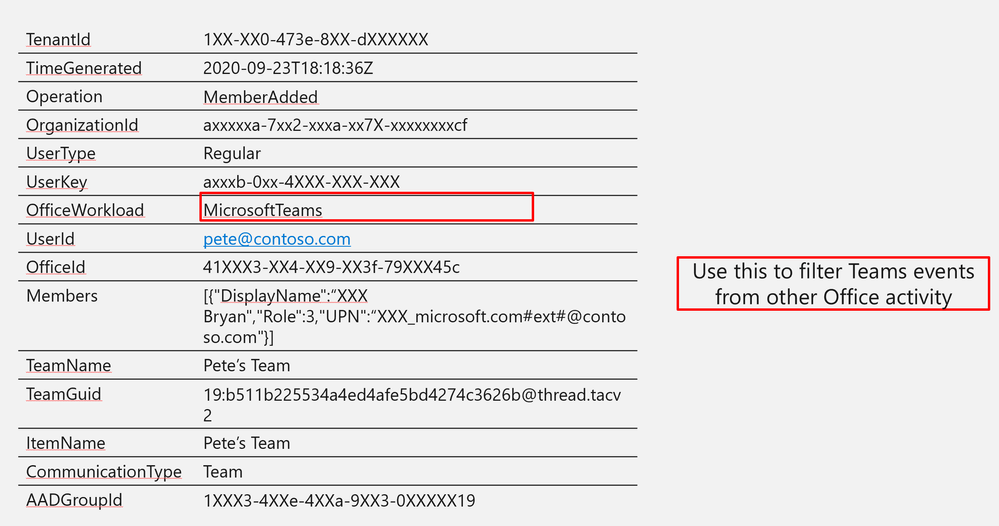
OfficeWorkload | MicrosoftTeams |
UserId | |
OfficeId | 41XXX3-XX4-XX9-XX3f-79XXX45c |
Members | [{“DisplayName”:“XXX Bryan”,”Role”:3,”UPN”:“XXX_microsoft.com#ext#@contoso.com”}] |
TeamName | Pete’s Team |
TeamGuid | 19:b511b225534a4ed4afe5bd4274c3626b@thread.tacv2 |
ItemName | Pete’s Team |
CommunicationType | Team |
AADGroupId | 1XXX3-4XXe-4XXa-9XX3-0XXXXX19 |
Log Structure (additional fields)
A step-by-step guide on how to ingest CallRecords-Sessions Teams data to Azure Sentinel via Microsoft Graph API, check out Secure your Calls- Monitoring Microsoft TEAMS CallRecords Activity Logs using Azure Sentinel blog post.
Other Logs:
AAD Signin for Teams
| where AppDisplayName contains “Microsoft Teams”
Files uploaded via Teams
| where SourceRelativeUrl contains “Microsoft Teams Chat Files”
Hunting:
- Users added and removed
- Large number of team ownership changes
- Mass deletes
- External user adds followed by file uploads
- Link with SigninLogs
- Suspicious sign-in followed by file uploads
- Visualize activity, more details : https://techcommunity.microsoft.com/t5/azure-sentinel/graph-visualization-of-external-teams-collaborations-in-azure/ba-p/1356847
Detection:
- Difficult due to usage variations between orgs
- SigninLogs analytics will protect against a lot of common attack types
- New external organization hunting query is a good candidate
SOAR:
- Plenty of actions in Azure Sentinel Playbooks – LogicApps controls for Teams
- Use this to get additional context for alerts
- You can also post messages to teams
Get started today!
We encourage you to try it now and start hunting in your environment.
You can also contribute new connectors, workbooks, analytics and more in Azure Sentinel. Get started now by joining the Azure Sentinel Threat Hunters GitHub community.