This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
This blog post is a collaboration with
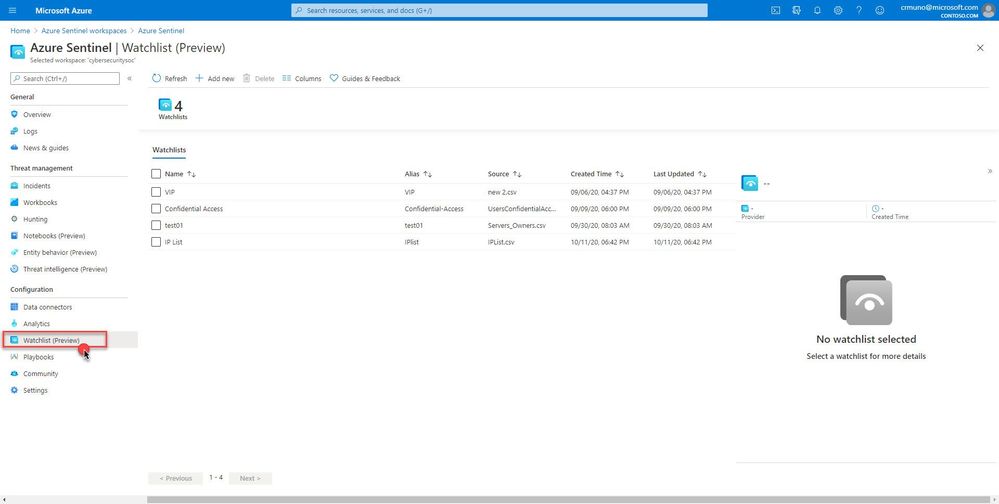
While each specialized security tool has a partial view of the world, a SIEM can utilize its broader outreach to enrich event and alert data and centrally manage allow-lists and watch lists. We are happy to announce the public preview for the Watchlist feature for Azure Sentinel!
What is it?
Azure Sentinel watchlists enables the collection of data from external data sources for correlation against the events in your Azure Sentinel environment. Once created, leverage watchlist in your search, detection rules, threat hunting and response playbooks. For a full list of the functionalities and the step-by-step instructions, refer to the official documentation.
The Watchlist feature can be utilized for the following use cases:
- Investigate threats and respond to incidents quickly with fast import of IP addresses, file hashes, etc. from csv files. Then utilize the watchlist name/value pairs for joining and filtering for use in alert rules, threat hunting, workbooks, notebooks and for general queries.
- Import business data, such as user lists with privileged system access as a watchlist. Then use the watchlist to create allow and deny lists. For example, use a watchlist that contains a list of terminated employees to detect or prevent them from logging in to the network.
- Create allow-lists to reduce alert fatigue. For example, use a watchlist to build an allow list to suppress alerts from only a limited set of IP addresses to do specific functions and thus removing benign events from becoming alerts.
- Use watchlists to enrich your event data with field-value combinations derived from external data sources.
Where do I find it?
In your Azure Sentinel portal, navigate to Configuration in the left navigation menu and select Watchlist (Preview).
How does it work?
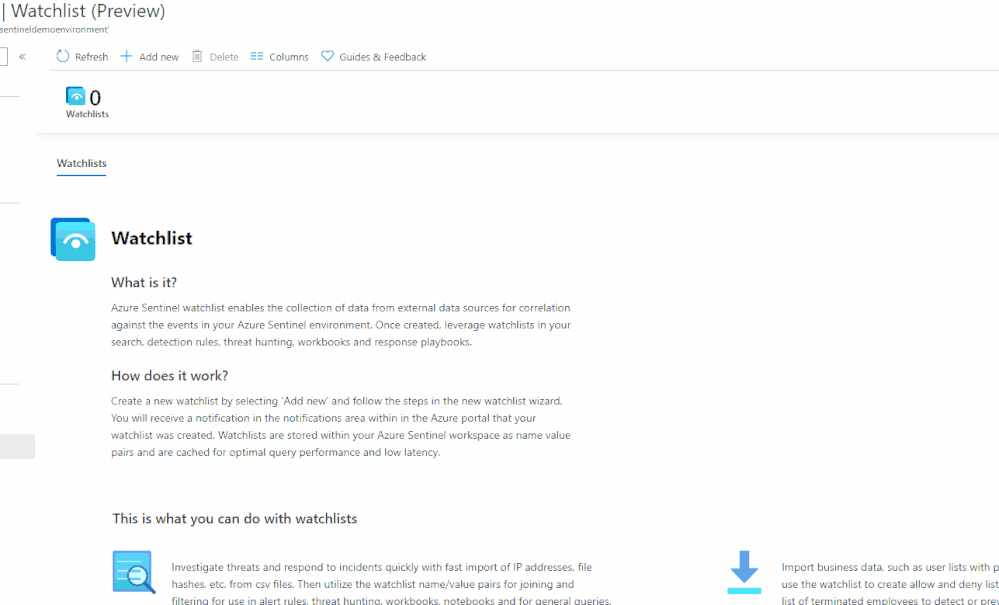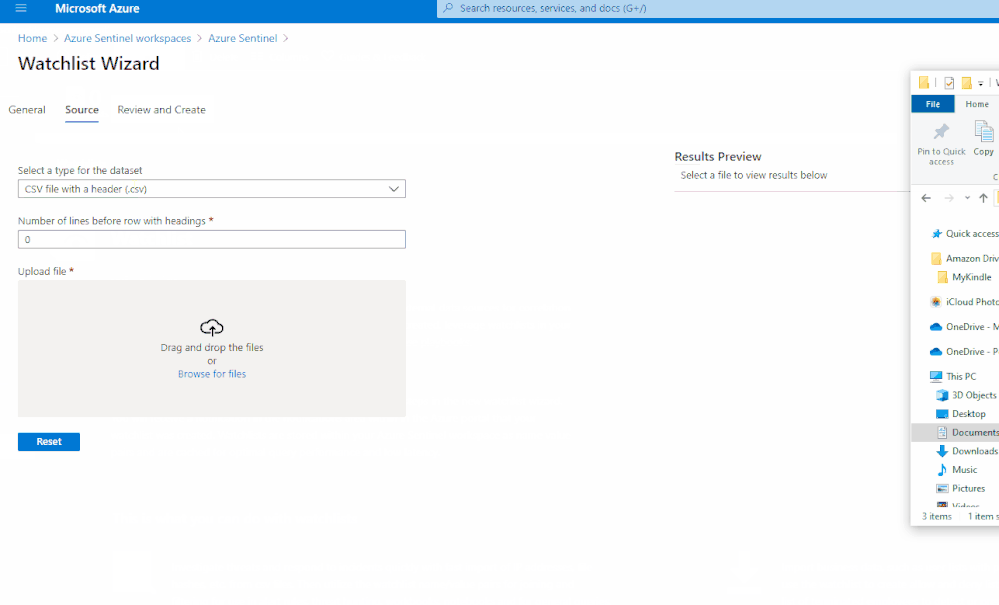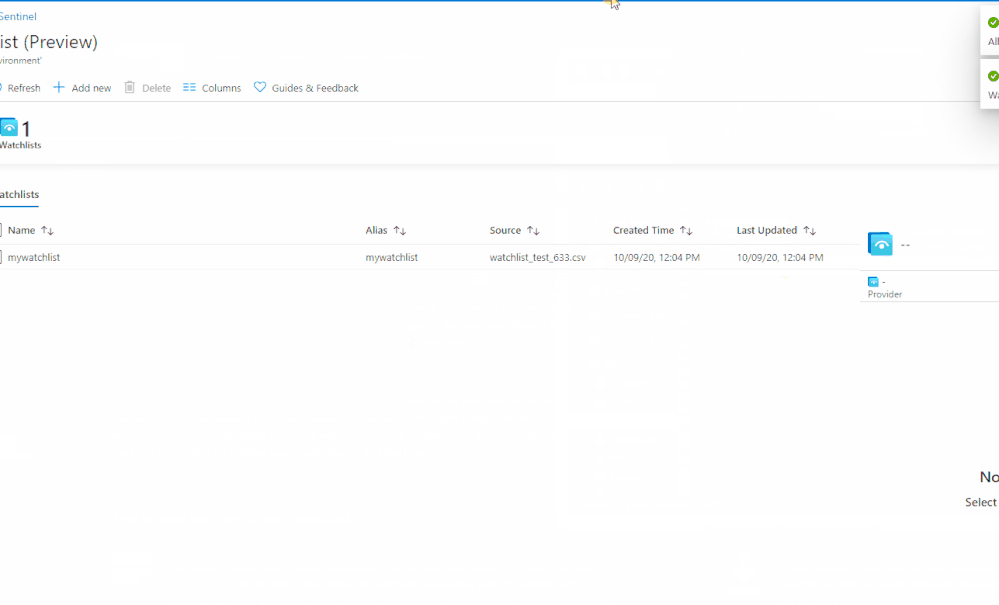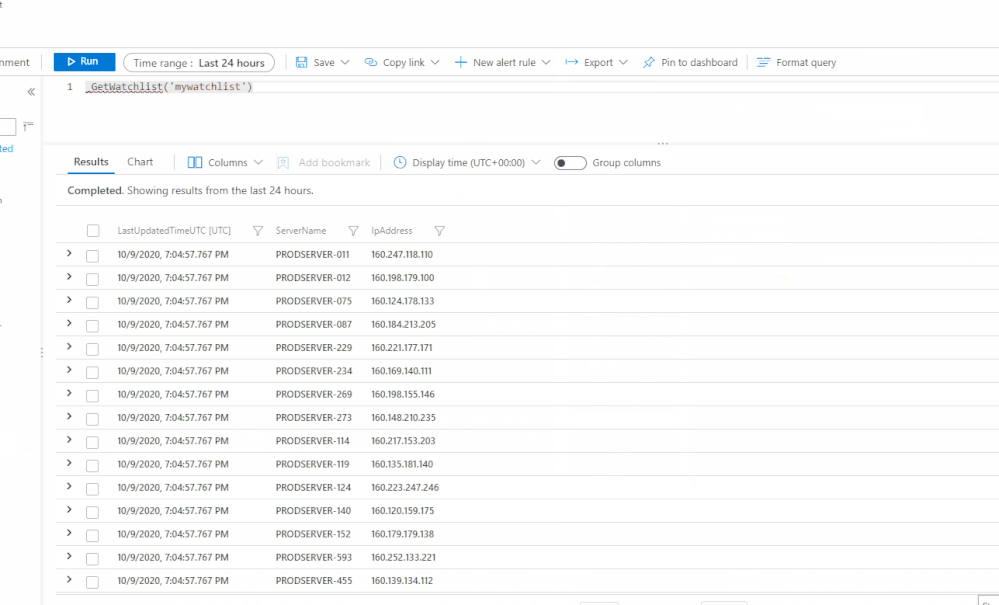
Create a new watchlist by selecting ‘+ Add new’ and follow the steps in the new watchlist wizard. You will receive a notification in the notifications area within in the Azure portal that your watchlist was created. Watchlists are stored to your Azure Sentinel workspace as name value pairs and are cached for optimal query performance and low latency.
How can I use watchlists in my security automation and orchestration?
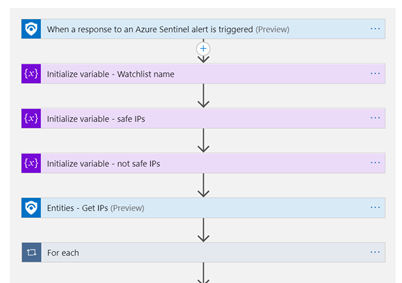
Check out a couple of example Logic App playbooks you can deploy to your Azure Sentinel workspace to show you what is possible:
https://github.com/Azure/Azure-Sentinel/tree/master/Playbooks/Watchlist-CloseIncidentKnownIPs
What's coming
This is just the beginning, in the near future we will be delivering additional features to enhance the watchlist experience:
- Ability to add and remove items from the watchlist
- Support for larger file uploads (upper limit is currently 3.8MB)
- Logic Apps watchlist connector making it easier to utilize watchlist in automation scenarios
- Built-in watchlists combined with analytics and much more!
Get started today!
We encourage you to try using watchlists now in your analytic rules, playbooks, workbooks and for threat hunting.
Try it out, and let us know what you think!