This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
It’s Cybersecurity Awareness month and a perfect time to highlight Microsoft 365 compliance capabilities for GCC, GCC High and DoD environments that I feel are important in helping you address and manage risk. The reality today for many government agencies is there is no audit traceability to determine which email messages and content an attacker may have seen during a breached session into a user’s mailbox. The standard level of Office 365 auditing includes events that a user logged into their mailbox but does not include detailed information on the activity that occurs within the mailbox. As a result, organizations have no choice but to assume all content within the mailbox is compromised whether or not sensitive data or PII was actually viewed by the adversary.
Under this circumstance, organizations subject to regulations such as HIPAA may face significant reporting requirements and need to notify constituents of the potential data breach.
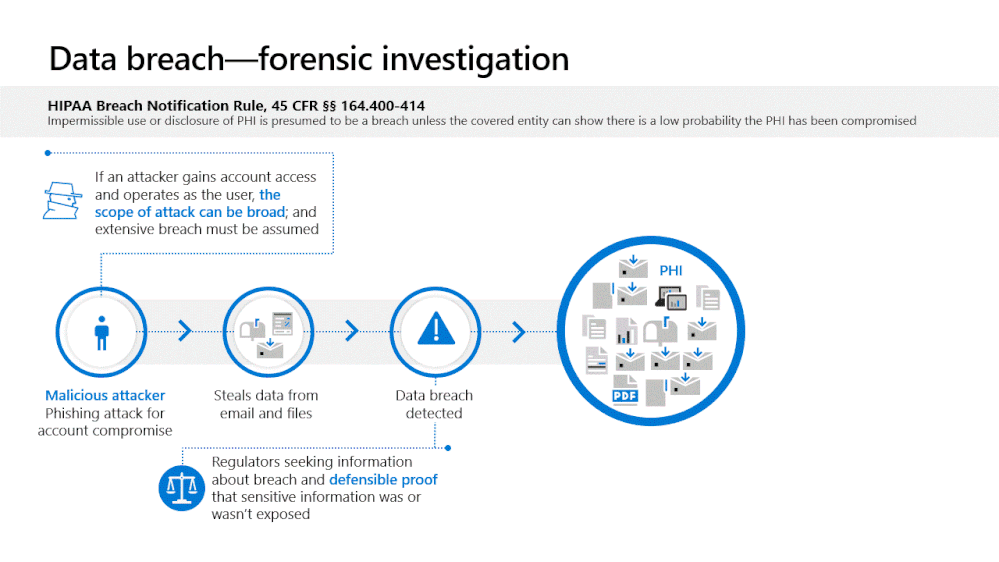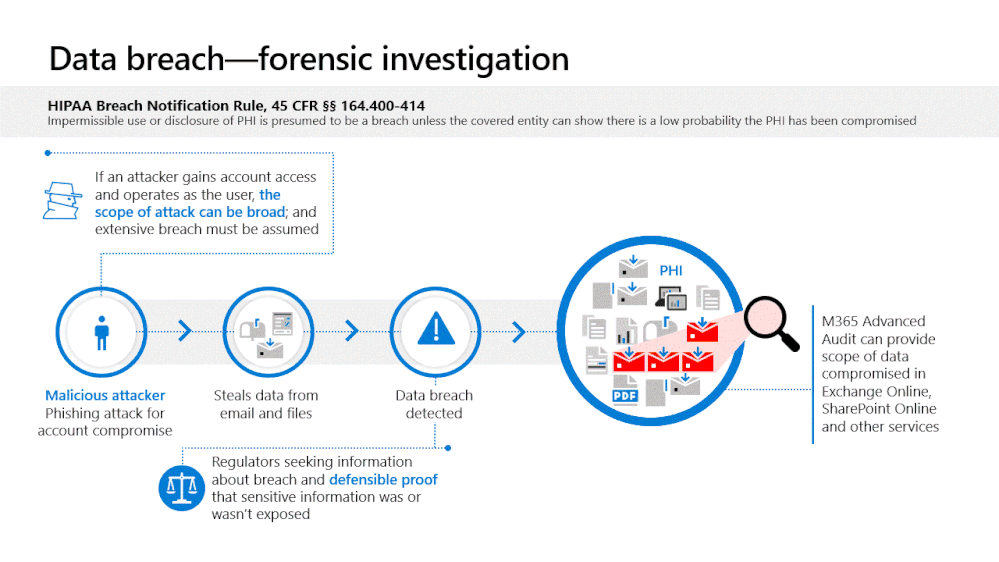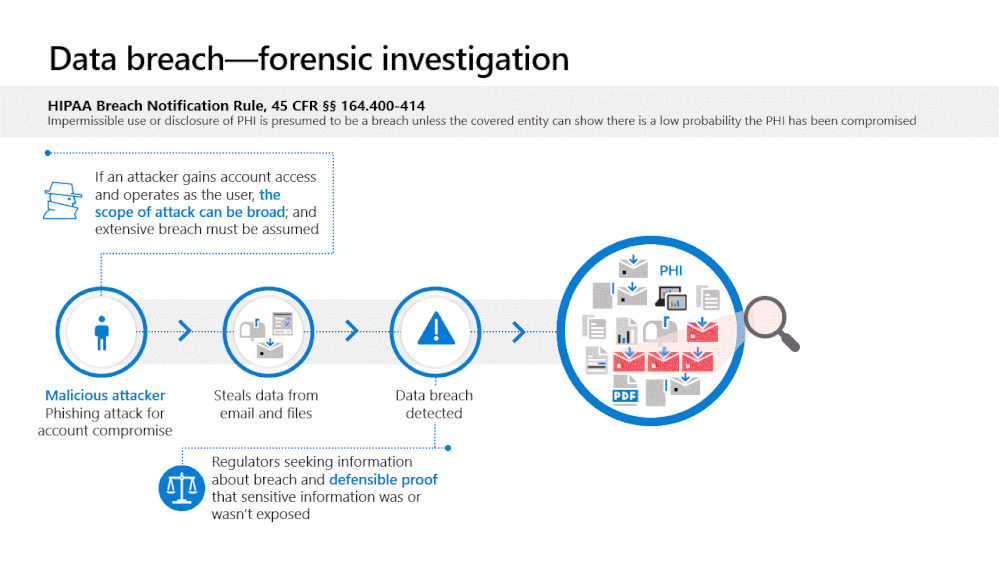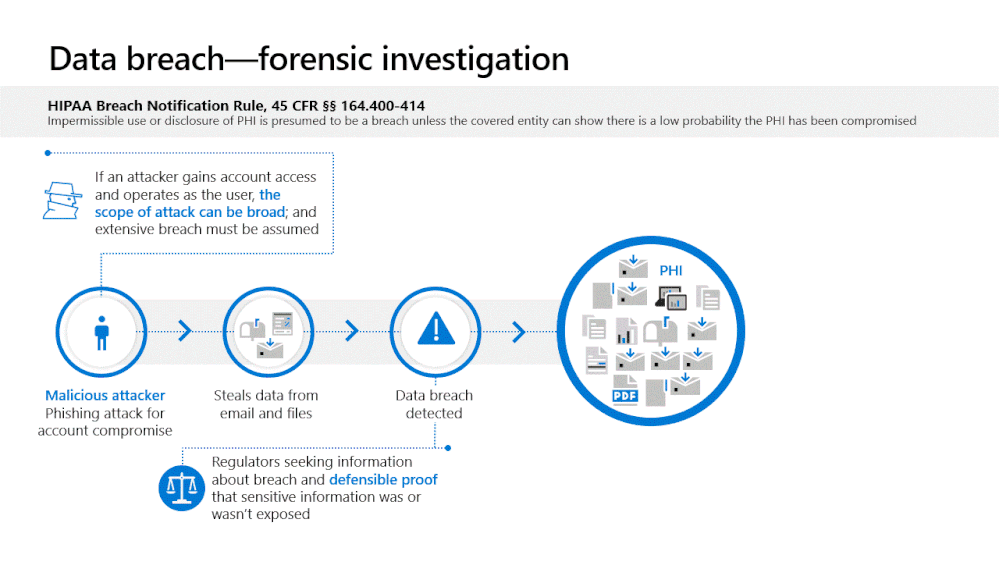
With Advanced Audit, an organization can investigate a business email compromise knowing they have detailed audit data that documents each message that was accessed by an adversary. Rather than assuming more mail data was compromised than actually was, Advanced Audit provides defensible data for you to trace the attacker's actual presence.
NOTE: Search term events in Exchange Online and SharePoint Online are expected to be available to GCC, GCC-High and DoD customers by end of Q1 CY2021.
What is Advanced Audit?
Advanced Audit is designed to help organizations conduct forensic investigations to help meet their regulatory, legal, and internal obligations. Advanced Audit not only helps identify the scope of data breach by providing additional events that help customers with forensic investigations, but also helps provide defensible proof on whether sensitive information was or wasn’t compromised.
Key capabilities include:
- Access to audit events that are crucial to forensic investigations, such as the MailItemsAccessed event, which can help with forensic investigations for business email compromise. Additional events will be brought to Government Community Cloud (GCC), GCC-High, Department of Defense (DoD) environments to include mail send events and user search events for both Exchange Online and SharePoint Online. Release schedule details will be posted on the public Microsoft 365 Roadmap as available.
- Increased audit storage from 90 days to 365 days within the Office 365 audit log. As Ponemon Research indicates in their recent study Cost of a Data Breach Report 2020 | IBM, the average time to identify a breach is over 200 days, this increased storage time enables organizations to conduct investigations within Office 365 for up to a year without having to move the audit data. The newly announced option for 10-year retention will be available for GCC, GCC-High, and DoD in early 2021. Further information will be provided on the public Microsoft 365 Roadmap.
- Increased API throughput to streamline the consumption of audit data into your existing process. Organizations that access auditing logs through the Office 365 Management Activity API were restricted by throttling limits at the publisher level. Advanced Audit shifts from a publisher-level limit to a tenant-level limit with increased bandwidth.
What are the benefits of MailItemsAccessed?
MailItemsAccessed, the first crucial event is now available to GCC and available in GCC-High and DoD tenants by end of October 2020, helps organizations investigate the potential scope of compromise following an incident. An audit event is triggered when mail data is accessed by both mail protocols and mail clients. With Advanced Audit, the new MailItemsAccessed event replaces MessageBind in audit logging in Exchange Online. This new auditing action plays a key role in providing defensible forensics to help assert whether a piece of mail data was compromised.
The MailItemsAccessed mailbox auditing action covers the following mail protocols: POP, IMAP, MAPI, EWS, Exchange ActiveSync, and REST. MailItemsAccessed provides several significant forensic improvements worth highlighting such as:
- Applies to all logon types
- Events are triggered by both bind and sync access types
- Events are aggregated into fewer audit records for when the same email message is accessed
It is important that forensic/investigation teams understand that this new information is available and modify investigation processes to enable consumption of the new information being written to the audit log. For detailed information on how to use this feature in Advanced Audit go to Use MailItemsAccessed audit records for forensic investigations.
What does this mean for investigation and reporting?
With the additional level of detail available in Advanced Audit, an organization will be able to investigate a business email compromise knowing they have detailed audit data that documents each message that was accessed by an adversary. Rather than assuming that more mail data was compromised than actually was, Advanced Audit provides defensible data for you to trace the attacker's actual activity. Detailed information on how to use this new event to investigate business email compromise is available at Use Advanced Audit to investigate compromised accounts - Microsoft 365 Compliance | Microsoft Docs.
Recommended next steps
The Advanced Audit capability is available across GCC, GCC-High, and DoD environments at the Microsoft 365 G5 and Microsoft 365 G5 Compliance levels of licensing. For forensic/investigation teams, examine your current process to confirm the new audit events are being consumed and used in your existing investigation process.
For those organizations that are already licensed, review the documentation at Advanced Audit in Microsoft 365 - Microsoft 365 Compliance | Microsoft Docs for further technical implementation details. Support is available via the standard channels in the tenant or via your Customer Success Account Manager. We also encourage your feedback via the Microsoft 365 Security and Compliance UserVoice forum.
Building a cyber risk reduction strategy for federal government IT article and podcast
In a recent podcast with FedScoop for Cyber Security Awareness month ,
Cloud and AI key to managing risk for government agencies - FedScoop
The remote workforce has opened up the floodgates on cyber risk, presenting agencies with new challenges to operate safely outside the bounds of traditional on-premises IT environments. In addition to staying on top of growing threats, government CTOs and CISOs are also required to keep their environments current on an extensive list of federal regulations.
Additional resources
Microsoft 365 Roadmap to get the latest updates on our best-in-class productivity apps and intelligent cloud services.
Microsoft 365 Discover and Respond: Advanced eDiscovery and Advanced Audit website to learn more about the tools to help your organization find relevant data quickly and cost effectively.