This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
Scenario:
You want to mount the Azure Blob storage container on Linux VM and access the data using either Managed Identities or Service Principal.
Prerequisites:
Azure storage account
Linux VM
Action:
To mount the Azure Blob storage container as a filesystem on Linux VM, you can make use of Blobfuse which allows you to access the existing data in your storage account through the Linux filesystem.
Mounting of storage account using the Storage account key has been explained in our article:
https://docs.microsoft.com/en-us/azure/storage/blobs/storage-how-to-mount-container-linux
Below are the steps to mount the storage account either using Managed Service Identity or using Service Principal.
Step 1:
Configure the Linux software repository for Microsoft products using the below command:
For Ubuntu:
wget https://packages.microsoft.com/config/ubuntu/18.04/packages-microsoft-prod.deb
sudo dpkg -i packages-microsoft-prod.deb
sudo apt-get update
For RHEL:
sudo rpm -Uvh https://packages.microsoft.com/config/rhel/7/packages-microsoft-prod.rpm
Note: Change the URL accordingly based on the Ubuntu version and RHEL Distribution that you’re using.
Step 2:
Install the blobfuse in your Linux VM.
For Ubuntu:
sudo apt-get install blobfuse
For RHEL:
sudo yum install blobfuse
Step 3:
Blobfuse requires a temporary path in the file system to buffer and cache any open files.
You can make use of SSD disks available on your VMs for blobfuse. You can also make use of ramdisk and create a directory for blobfuse.
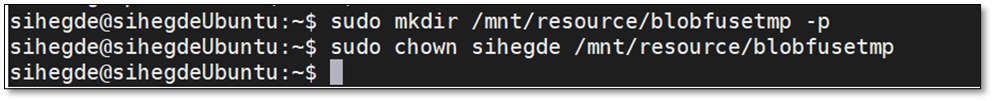
To use SSD as a temporary path, below is the command:
sudo mkdir /mnt/resource/blobfusetmp -p
sudo chown <youruser> /mnt/resource/blobfusetmp
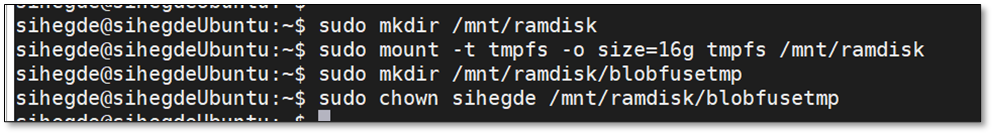
Or to use ramdisk for the temporary path, below is the command:
sudo mkdir /mnt/ramdisk
sudo mount -t tmpfs -o size=16g tmpfs /mnt/ramdisk
sudo mkdir /mnt/ramdisk/blobfusetmp
sudo chown <youruser> /mnt/ramdisk/blobfusetmp
Step 4:
Blobfuse requires the authentication methods and credentials to be configured either in a configuration file or as an environment variable.
To create a configuration file and to restrict the access to the file so that no other users can read it, use the below commands:
touch ~/fuse_connection.cfg
chmod 600 fuse_connection.cfg
To mount the storage to the VM, you can make use of either System Assigned Managed Identity or User-assigned managed Identity or Service Principal.
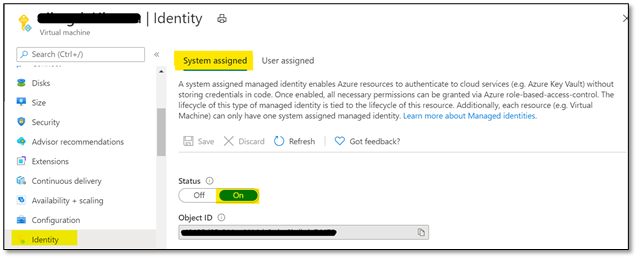
- Using System Assigned Managed Identity
- To use this configuration, please enable ‘System-assigned’ managed identity on the Linux VM that you’re using as shown below:
- Ensure that the Object ID or the system managed identity is given sufficient RBAC role at the storage account level.
- To use this configuration, please enable ‘System-assigned’ managed identity on the Linux VM that you’re using as shown below:
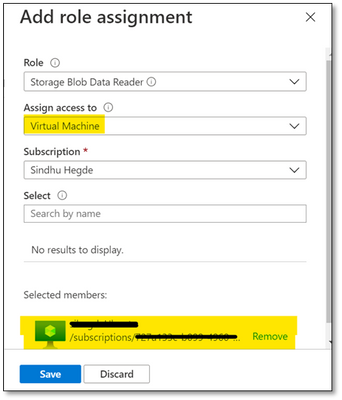
Note: Please make sure that you give minimum of ‘Reader’ and ‘Storage Blob Data Reader’ role to the managed identity at the storage account level.
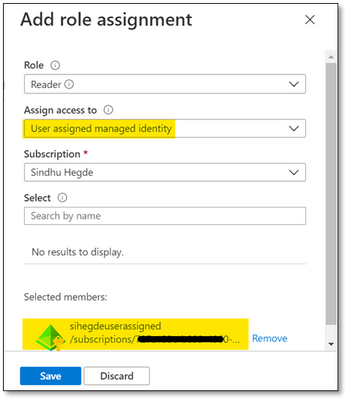
You can assign these roles here: Storage account -> Access Control (IAM) -> Add role assignment and selecting Virtual Machine in ‘Assign access to’ option as shown below:
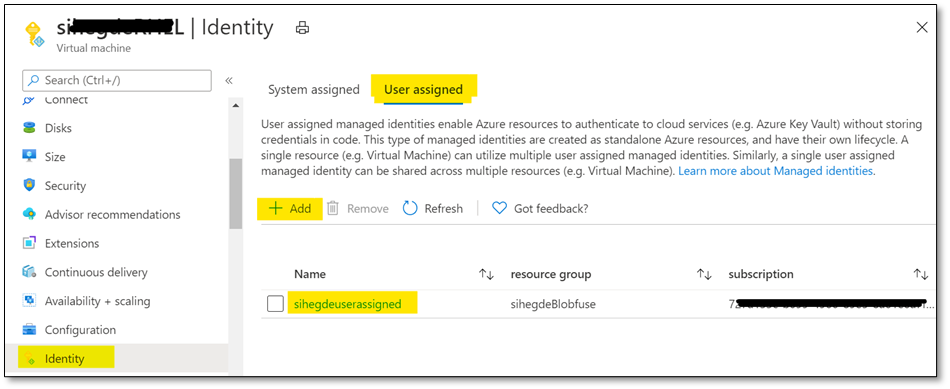
2. Using User-Assigned Managed Identity
i. If you’re using User assigned managed identity, please add the identity in ‘User assigned’ configuration of your Linux VM as shown below:
ii. Ensure that the managed identity is given necessary RBAC roles at the storage account level as shown below:
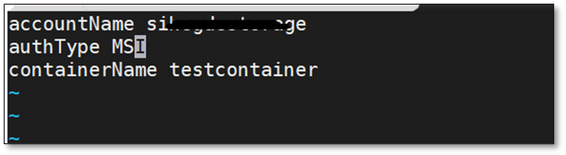
For both scenarios, update the configuration file that was created earlier with the storage account credentials and mention authType as ‘MSI’ as shown below:
accountName <storage account name>
authType MSI
containerName <container name>
3. Using Service Principal
i. Ensure that SPN is given sufficient RBAC roles at the storage account level.
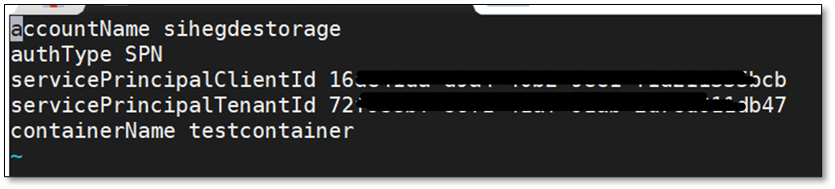
ii. Update the configuration file with Storage account details and Service Principal details. Also, the authType for Service Principal authentication would be SPN as shown below:
accountName <storage account name>
authType SPN
servicePrincipalClientId <Client ID or Application ID of the Service Principal>
servicePrincipalTenantId <Tenant ID of the Service Principal>
containerName <container name>
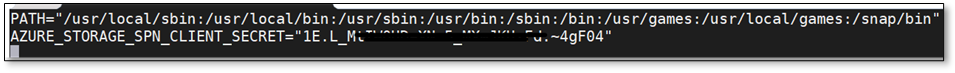
iii. The client secret for your application or the Service Principal must be saved as an Environment Variable and should not be mentioned in the configuration file. It will be saved as AZURE_STORAGE_SPN_CLIENT_SECRET. Please save it in /etc/environment in the below format:
AZURE_STORAGE_SPN_CLIENT_SECRET="your client secret"
Step 5:
Create an empty directory for mounting using the below command:
mkdir ~/mycontainer
Step 6:
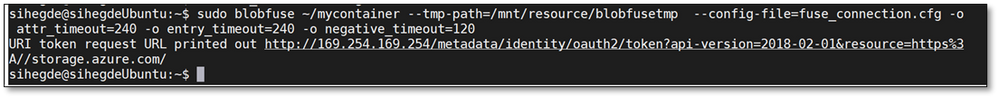
To mount the blob storage using blobfuse, run the below command which will mount the specified container in the configuration file onto the empty directory that we created:
sudo blobfuse ~/mycontainer --tmp-path=/mnt/resource/blobfusetmp --config-file=/path/to/fuse_connection.cfg -o attr_timeout=240 -o entry_timeout=240 -o negative_timeout=120
Note: To allow access to all users, please use the switch -o allow_other while mounting.
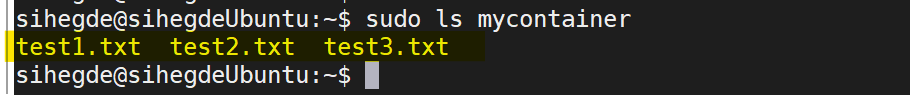
Once the container is mounted, you can access the blobs using the regular file system APIs in your Linux VM.
Hope that helps!