This installment is part of a broader series to keep you up to date with the latest features in Azure Sentinel. The installments will be bite-sized to enable you to easily digest the new content.
This post was written in collaboration with
Introduction:
Threat hunting is a powerful way for the SOC to reduce organizational risk, but it’s commonly portrayed and seen as a complex and mysterious art form for deep experts only, which can be counterproductive. Sophisticated cybercriminals burrow their way into network caverns, avoiding detection for weeks or even months, as they gather information and escalate privileges. If you wait until these advanced persistent threats (APT) become visible, it can be costly and time-consuming to address. In today’s cybersecurity landscape, SOC analysts need controls and integrated toolsets to search, filter, and pivot through their telemetry to derive relevant insights faster.
Taken into account, we are delighted to announce that we have introduced 80 new hunting queries that can empower your SOC analyst to reduce the gaps in your current detection coverage and ignite new hunting leads.
Hunting queries included:
The following queries are designed to help you find suspicious activity in your environment, and whilst many are likely to return legitimate activity as well as potentially malicious activity, they can be useful in guiding your hunting. If after running these queries you are confident with the results you could consider converting them to analytics or add hunting results to existing or new incidents.
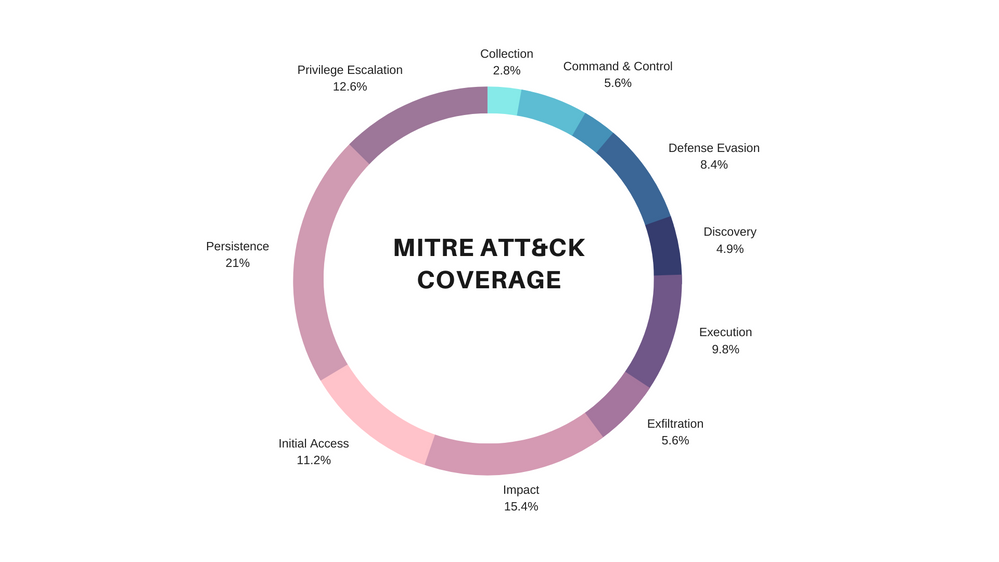
The figure below illustrates the diversification and threat hunting coverage the new hunting queries provide across the MITRE ATT&CK framework matrix:
Feel free to expand the spoiler below to view the new list of out the box hunting queries and the MITRE ATT&CK tactics that are covered:
Query MITRE Tactic
| Alerts related to IP | { Persistence Discovery LateralMovement Collection } | { } | |
| Anomalous AAD Account Creation | { Persistence } | { } | |
| Anomalous Login to Devices | { PrivilegeEscalation } | { T1078 } | |
| Anomalous Password Reset | { Impact } | { T1531 } | |
| Anomalous Role Assignment | { Persistence } | { T1098 } | |
| Attempts to sign in to disabled accounts by IP address | { InitialAccess } | { T1078 } | |
| Azure Active Directory signins from new locations | { InitialAccess } | { T1078 } | |
| Azure DevOps- Guest users access enabled | { Persistence DefenseEvasion } | { T1098 T1089 } | |
| Azure DevOps- Project visibility changed to public | { Collection } | { T1213 } | |
| Azure DevOps- Public project created | { Persistence DefenseEvasion } | { T1098 T1089 } | |
| Azure Sentinel Connectors Administrative Operations | { Impact } | { T1496 } | |
| Azure Sentinel Workbooks Administrative Operations | { Impact } | { T1496 } | |
| Azure storage key enumeration | { Discovery } | { T1087 } | |
| Azure Virtual Network Subnets Administrative Operations | { Impact } | { T1496 } | |
| Common deployed resources | { Impact } | { T1496 } | |
| Crypto currency miners EXECVE | { Persistence Execution } | { T1059 T1053 } | |
| Cscript script daily summary breakdown | { Execution } | { } | |
| Detect beacon like pattern based on repetitive time intervals in Wire Data Traffic | { CommandAndControl } | { T1043 T1065 } | |
| DNS – domain anomalous lookup increase | { CommandAndControl Exfiltration } | { T1483 T1008 T1048 } | |
| Entropy for Processes for a given Host | { Execution } | { } | |
| External user from a new organisation added | { Persistence } | { T1136 } | |
| Failed Login Attempt by Expired account | { InitialAccess } | { T1078 } | |
| Failed service logon attempt by user account with available AuditData | { CredentialAccess } | { T1110 } | |
| GitHub OAuth App Restrictions Disabled | { Exfiltration } | { T1537 } | |
| Hosts running a rare process with commandline | { Execution Persistence Discovery LateralMovement Collection } | { } | |
| Least Common Parent And Child Process Pairs | { Execution } | { } | |
| Least Common Processes by Command Line | { Execution } | { } | |
| Multiple Teams deleted by a single user | { Impact } | { T1485 T1489 } | |
| New domain added to Whitelist | { Persistence } | { T1098 } | |
| New PowerShell scripts encoded on the commandline | { Execution CommandAndControl } | { } | |
| New processes observed in last 24 hours | { Execution } | { } | |
| New time zone observed | { InitialAccess } | { T1078 } | |
| New User created on SQL Server | { Persistence } | { T1136 } | |
| Non-owner mailbox login activity | { Collection Exfiltration } | { T1114 T1020 } | |
| Permutations on logon attempts by UserPrincipalNames indicating potential brute force | { CredentialAccess } | { T1110 } | |
| Potential DGA detected | { CommandAndControl } | { T1483 T1008 } | |
| Powershell or non-browser mailbox login activity | { Execution Persistence Collection } | { T1059 T1098 T1114 } | |
| Preview – TI map File entity to OfficeActivity Event | { Impact } | { } | |
| Preview – TI map File entity to Security Event | { Impact } | { } | |
| Preview – TI map File entity to Syslog Event | { Impact } | { } | |
| Preview – TI map File entity to VMConnection Event | { Impact } | { } | |
| Privileged role attached to Instance | { PrivilegeEscalation } | { T1098 } | |
| Rare Audit activity initiated by App | { Persistence LateralMovement } | { T1136 } | |
| Rare Process Path | { Execution } | { } | |
| Rare User Agent strings | { InitialAccess } | { T1190 } | |
| RareDNSLookupWithDataTransfer | { CommandAndControl Exfiltration } | { T1043 T1048 } | |
| Same IP address with multiple csUserAgent | { InitialAccess } | { T1190 } | |
| Signin Logs with expanded Conditional Access Policies | { Impact } | { } | |
| Suspicious credential token access of valid IAM Roles | { InitialAccess DefenseEvasion } | { T1078 } | |
| Tracking Privileged Account Rare Activity | { PrivilegeEscalation Discovery } | { T1078 T1087 } | |
| Uncommon processes – bottom 5% | { Execution } | { } | |
| User added to SQL Server SecurityAdmin Group | { Persistence PrivilegeEscalation } | { T1098 T1078 } | |
| User added to Team and immediately uploads file | { InitialAccess } | { T1566 } | |
| User created by unauthorized user | { Persistence PrivilegeEscalation } | { T1098 T1078 } | |
| User Granted Access and associated audit activity | { Persistence PrivilegeEscalation Impact } | { T1098 T1078 T1496 } | |
| User Granted Access and Grants others Access | { Persistence PrivilegeEscalation } | { T1098 T1078 } | |
| User made Owner of multiple teams | { PrivilegeEscalation } | { T1078 } | |
| User removed from SQL Server Roles | { Persistence PrivilegeEscalation Impact } | { T1098 T1078 T1496 } | |
How to access the new hunting queries:
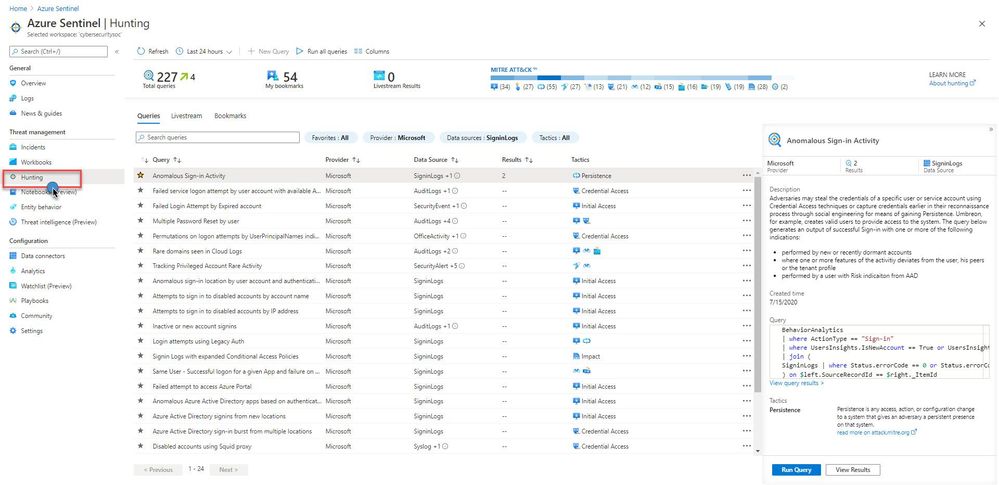
All of the queries are available via the Hunting UI page. For this example, I will demonstrate how to filter the new Microsoft Teams hunting queries. To learn more, see article on the new Microsoft Teams data connector (Preview).
Navigate to the Azure Sentinel console, and select “Hunting” under the Threat Management area
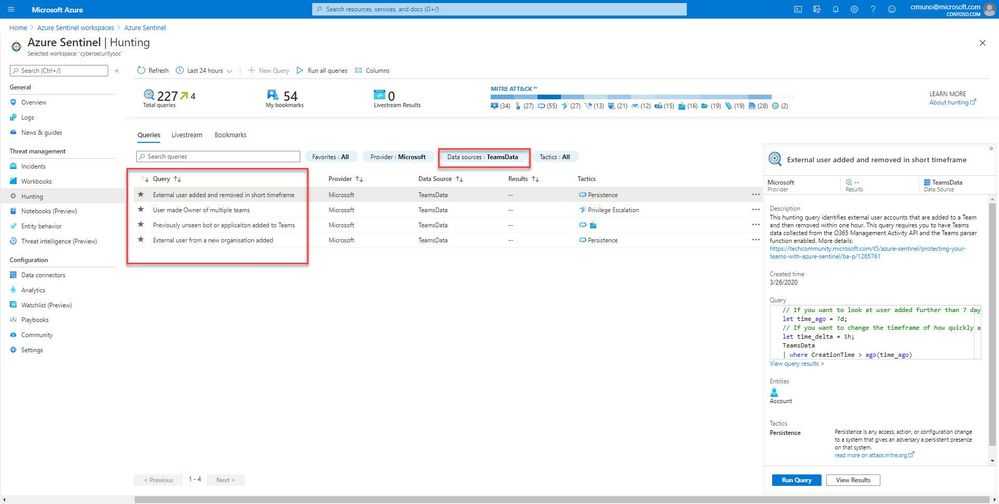
Next, use the filter pills to filter the data source (TeamsData) for the hunting query. In this example, we are highlighting hunting queries that satisfy several use cases for Microsoft Teams:
Example: Previously unseen bot or application added to Microsoft Teams
As an example, this hunting query helps identify new, and potentially unapproved applications or bots being added to Microsoft Teams. This query requires you to have Microsoft Teams data ingesting into Azure Sentinel. Ensure you have the relevant data collectors configured for the target hunting queries. Visit here (Connect data sources to Azure Sentinel | Microsoft Docs) for more information.
let data_date = 14d;
let historical_bots = (
TeamsData
| where CreationTime > ago(data_date)
| where isnotempty(AddOnName)
| project AddOnName);
TeamsData
| where CreationTime > ago(1d)
// Look for add-ins we have never seen before
| where AddOnName in (historical_bots)
// Uncomment the following line to map query entities is you plan to use this as a detection query
//| extend timestamp = CreationTime, AccountCustomEntity = UserId
Get started today!