This post has been republished via RSS; it originally appeared at: Intune Customer Success articles.
By Luke Ramsdale – Service Engineer | Microsoft Endpoint Manager – Intune
Administrators often work with a variety of devices—newer devices equipped with the trusted platform module (TPM) or older devices and virtual machines (VMs) without TPM. When you’re deploying BitLocker settings through Microsoft Endpoint Manager - Microsoft Intune, different BitLocker encryption configuration scenarios require specific settings. In this final post in our series on troubleshooting BitLocker using Intune, we’ll outline recommended settings for the following scenarios:
- Enabling silent encryption. There is no user interaction when enabling BitLocker on a device in this scenario.
- Enabling BitLocker and allowing user interaction on a device with or without TPM.
As we described in our first post, Enabling BitLocker with Microsoft Endpoint Manager - Microsoft Intune, a best practice for deploying BitLocker settings is to configure a disk encryption policy for endpoint security in Intune.
Enabling silent encryption
Consider the following best practices when configuring silent encryption on a Windows 10 device.
- First, ensure that the Hide prompt about third-party encryption setting is set to Yes. This is important because there should be no user interaction to complete the encryption silently.
Hide prompt about third-party encryption settings
- It’s important not to target devices that are using third-party encryption. Enabling BitLocker on those devices can render them unusable and result in data loss.
- If your users are not local administrators on the devices, you will need to configure the Allow standard users to enable encryption during autopilot setting so that encryption can be initiated for users without administrative rights.
- The policy cannot have settings configured that will require user interaction.
BitLocker settings that prevent silent encryption
In the following example, the Compatible TPM startup PIN, Compatible TPM startup key and Compatible TPM startup key and PIN options are set to Blocked. BitLocker cannot silently encrypt the device if these settings are configured to required because these settings require user interaction.

Be aware that configuring these options to Required will prevent silent encryption. The Required setting involves end user interaction, which is not compatible with silent encryption.

Note
When assigning a silent encryption policy, the targeted devices must have a TPM. Silent encryption does not work on devices where the TPM is missing or not enabled.
Enabling BitLocker and allowing user interaction on a device
For scenarios where you don’t want to enable silent encryption and would rather let the user drive the encryption process, there are several configuration settings that you can use.
Note
For non-silent enablement of BitLocker, the user must be a local administrator to complete the BitLocker setup wizard.
If a device does not have a TPM and you want to configure start-up authentication, set Hide prompt about third-party encryption to Not configured in Base Settings. This will ensure the user is prompted with a notification when the BitLocker policy arrives on the device.

If you want to encrypt devices without a TPM, set Disable BitLocker on devices where TPM is incompatible to Not configured. This setting is part of the startup authentication settings and Start-up authentication required must be set to Yes.
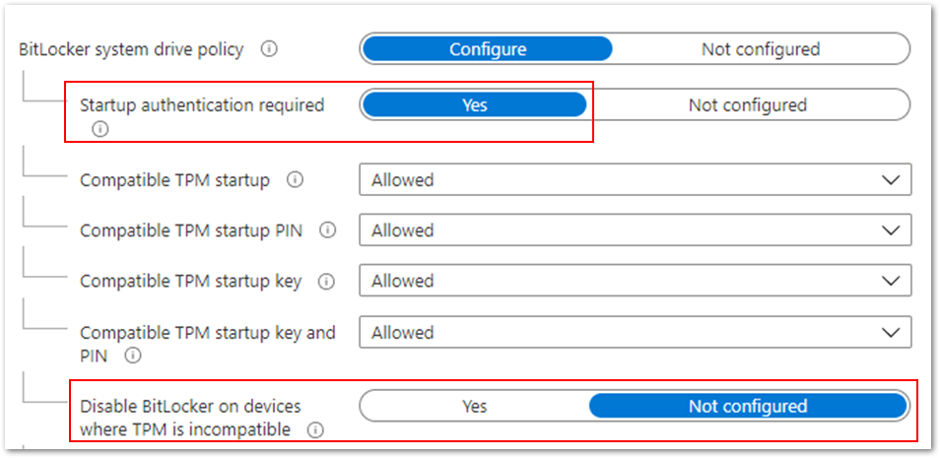
If you also want to allow users to configure startup authentication, then set the Startup authentication required setting to Yes and individual settings Allowed, as shown in the example above. These settings will offer all the startup authentication options to the end user.
Managing authentication settings conflicts
If you configure conflicting startup authentication setting options, the device will not be encrypted, and the end user will receive the following message:
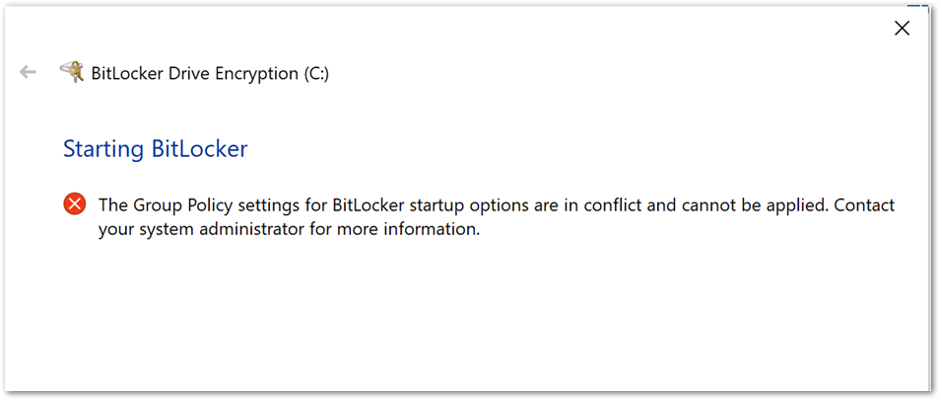
Or this message:
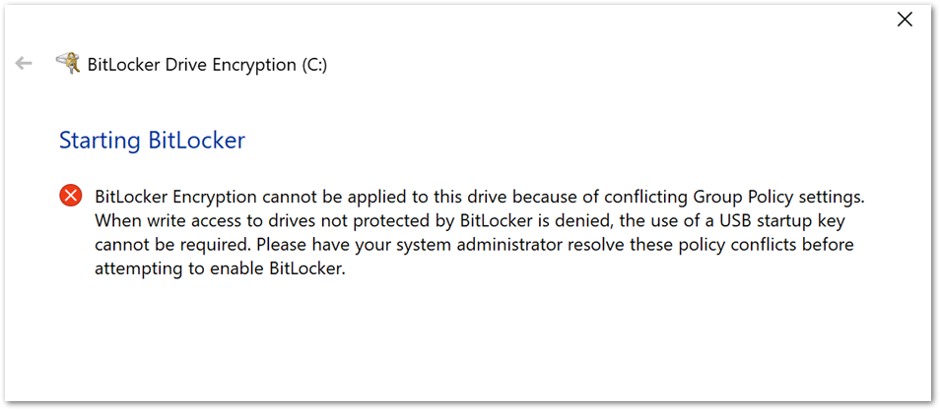
You can use one of the following options to correct the error:
- Configure all the compatible TPM settings to Allowed.
Compatible TPM settings set to Allowed.
- Configure Compatible TPM startup to Required and the remaining three settings
to Blocked.Compatible TPM startup to Required and the remaining three settings to Blocked.
- Configure Compatible TPM startup key to Required and the remaining three settings
to Blocked.Compatible TPM startup key to Required and the remaining three settings to Blocked.
- Finally, you can configure Compatible TPM startup PIN to Required and the remaining settings to Blocked.
Compatible TPM startup PIN to Required and the remaining settings to Blocked.
Note: Devices that pass Hardware Security Testability Specification (HSTI) validation or Modern Standby devices will not be able to configure a startup PIN. Users must manually configure the PIN.
If you configure the Compatible startup key and PIN option to Required and all others to Blocked, you will see the following error when initiating the encryption from the device.

If you want to require the use of a startup PIN and a USB flash drive, you must configure BitLocker settings using the manage-bde command-line tool instead of the BitLocker Drive Encryption setup wizard.
The user role in encryption
After the device picks up the BitLocker policy, a notification will prompt the user to confirm that there is no third-party encryption software installed.

When the user selects Yes, the BitLocker Drive Encryption wizard is launched, and the user is presented with the following start-up options:

Note
If you decide not to allow users to configure start-up authentication and configure the settings to Blocked, then this screen will not be displayed.
If there is no TPM on the device, the user will see the following screen instead of start-up options. The user enters a password when the device restarts.

The user will be presented with recovery key settings. (The options listed will depend on how the recovery key settings have been configured. For more information about recovery key settings, check out the blog on this topic.)
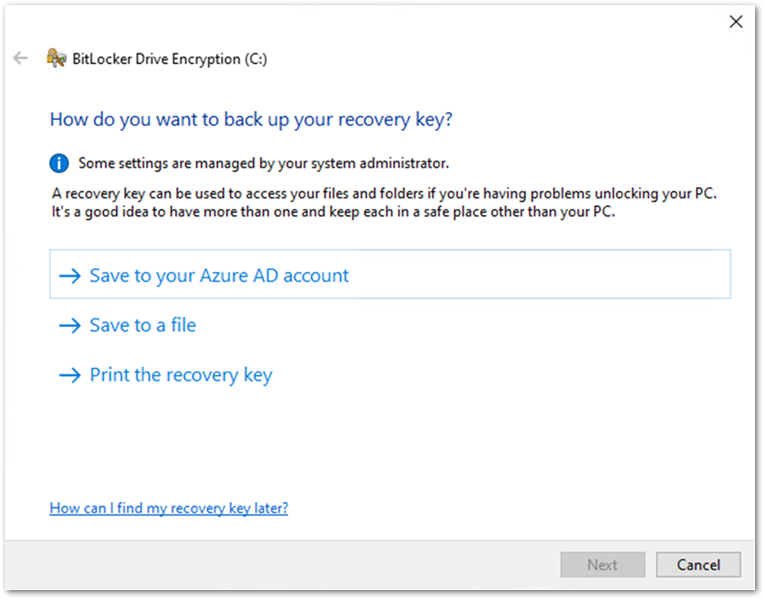
Once the recovery key has been saved, the user is prompted to encrypt the device and the process completes.
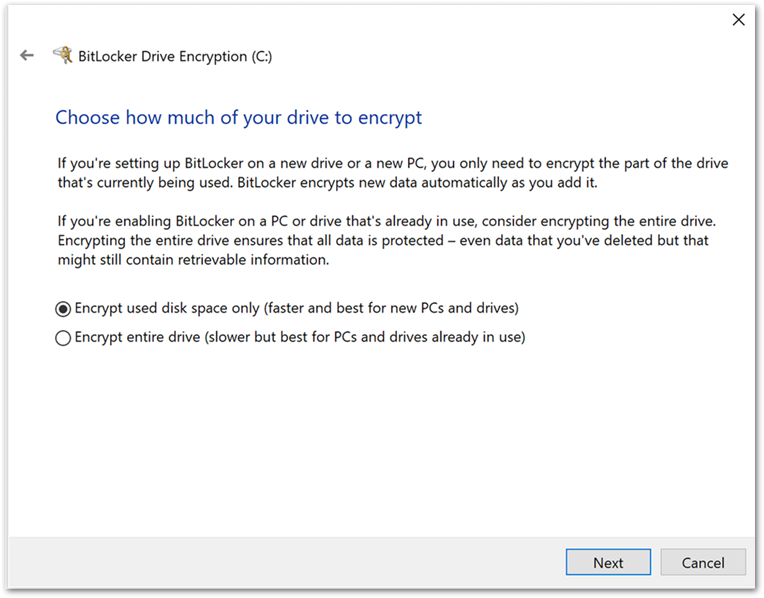
Tip
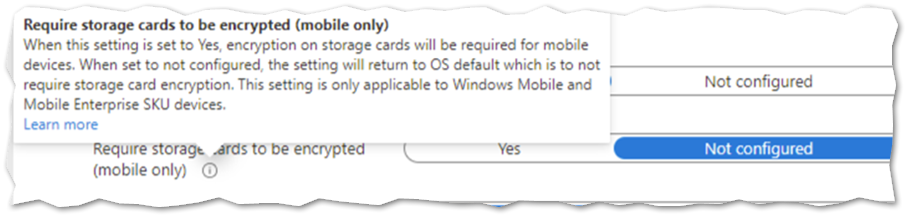
If you’re unsure about a configuration setting, you can hover the tool tip to see a description and link to additional information:
Summary
- It is possible to encrypt a device silently or enable a user to configure settings manually using an Intune BitLocker encryption policy.
The user driven encryption requires the end users to have local administrative rights. - Silent encryption requires a TPM on the device.
- Be careful when configuring the start-up authentication settings, conflicting settings will prevent BitLocker from encrypting and produce the Group Policy conflict errors.
- For devices without a TPM, set the Disable BitLocker on devices where TPM is incompatible option to Not configured.
More info and feedback
For further resources on this subject, please see the links below.
Enforcing BitLocker policies by using Intune known issues
Overview of BitLocker Device Encryption in Windows 10
BitLocker Group Policy settings (Windows 10)
BitLocker Use BitLocker Drive Encryption Tools to manage BitLocker (Windows 10)
This is the last post in this series. Catch up on the other blogs:
- Enabling BitLocker with Microsoft Endpoint Manager - Microsoft Intune
- Troubleshooting BitLocker from the Microsoft Endpoint Manager admin center
- Troubleshooting BitLocker policies from the client side
- Using BitLocker recovery keys with Microsoft Endpoint Manager - Microsoft Intune
Let us know if you have any additional questions by replying to this post or reaching out to @IntuneSuppTeam on Twitter.
