This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
Azure are offering to restrict the storage account to a virtual network. This feature currently works for all Windows virtual network-supported SKUs in the Dedicated (App Service) plan and for Windows Elastic Premium plans. It is also supported with private DNS for Linux virtual network-supported SKUs. Consumption and custom DNS for Linux plans aren't supported.
One can follow below steps to apply the configuration.
Prerequisite:
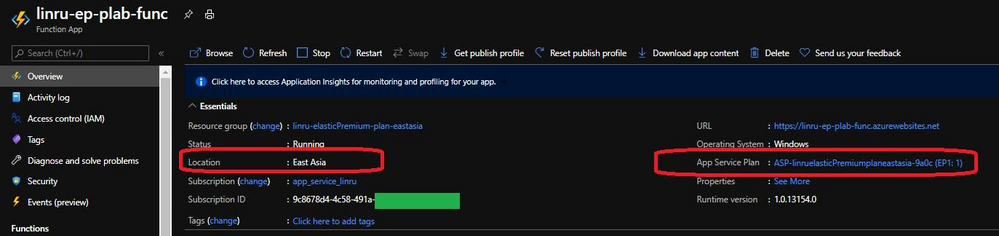
Function App: Need to be Elastic Premium plan to support Vnet integration
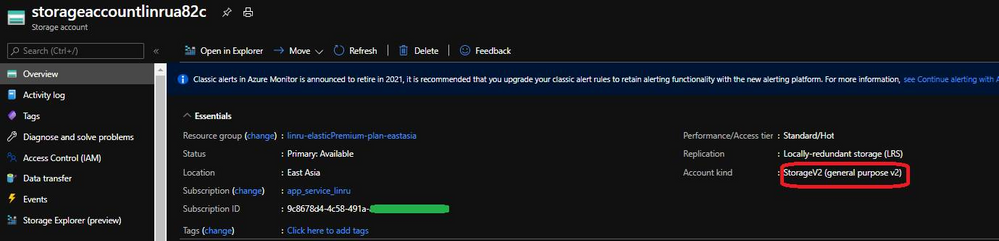
Storage Account: Need to be StorageV2 (general purpose v2) or higher to support Private Endpoint
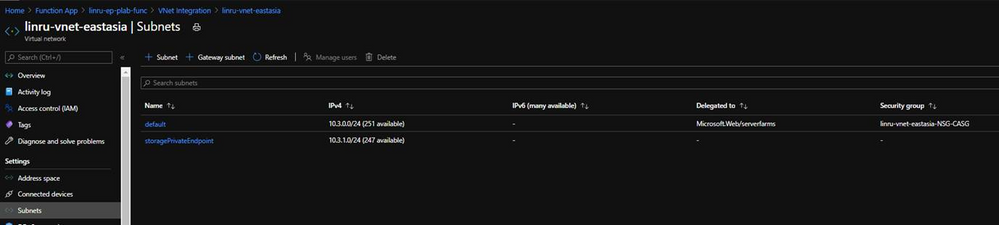
Vnet: Needs to have two subnets, one is for function app, the other is for Private Endpoint for storage account
Detailed steps:
1. Create Function App on Elastic Premium plan, the binding storage account needs to be with pricing tier general purpose v2 or higher to support private endpoint. Both function app and storage account should be hosted in the same region for better performance.
If you created a lower pricing tier for storage account, you can go to portal through blade “Configuration” to change the pricing tier.
Function app:
Storage account:
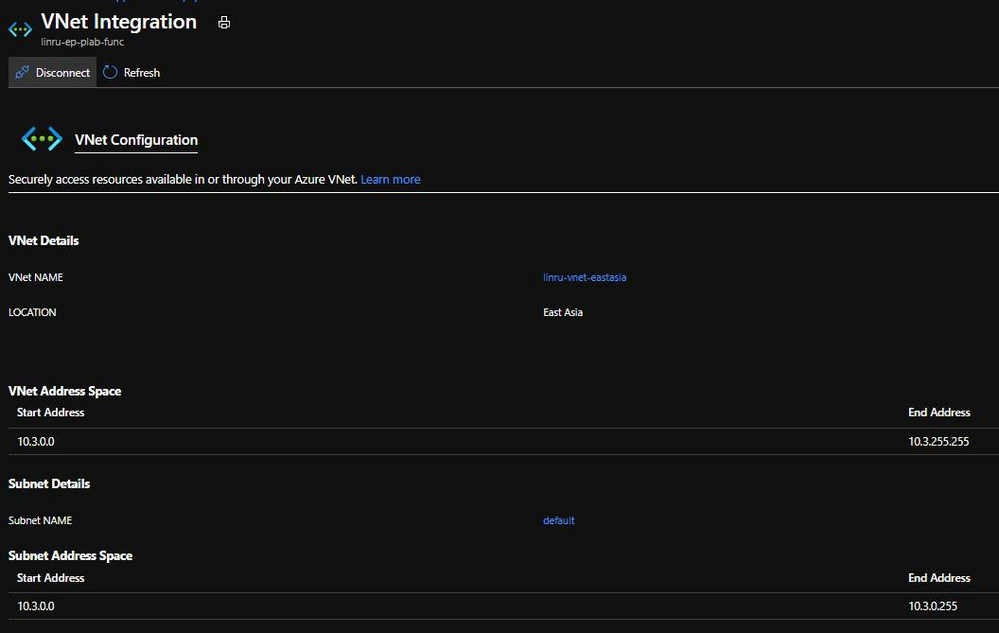
2. Create Vnet and prepare two subnets. As mentioned previously, one is for function app, the other is used to enable Private Endpoint in storage account.
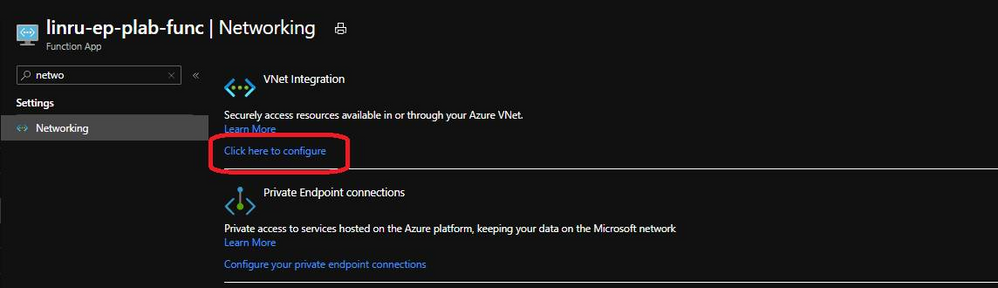
3. Integrate Vnet with your function app, select the subnet dedicated for your function.
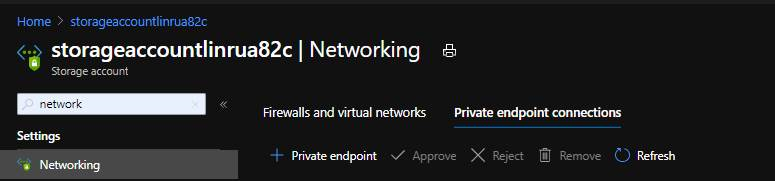
4 Go to portal storage account, in blade Networking, select Tab “Private endpoints connections”.
4.1 Click on “+ Private endpoint”;
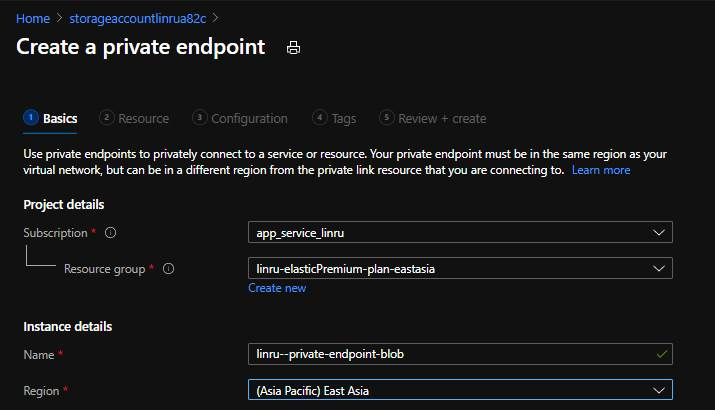
4.2 Input name for Private endpoint, then click Next: Resource
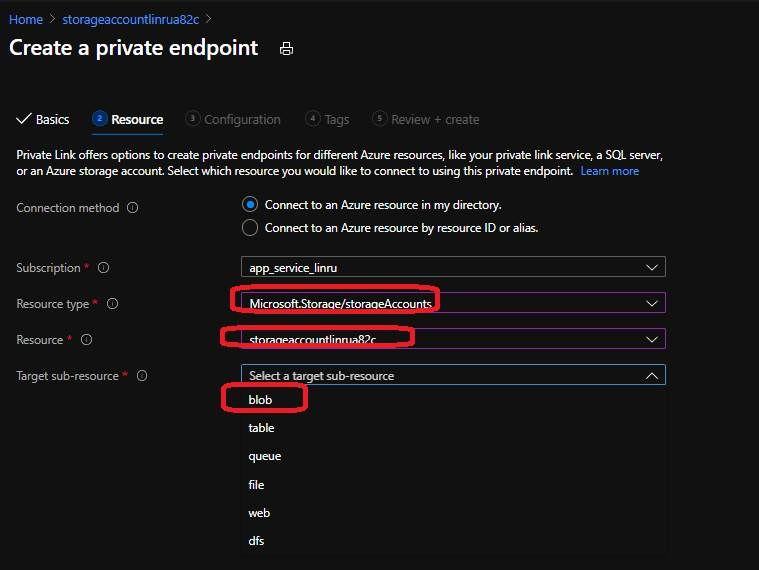
4.3 In the next page, choose storage account for “Resource type”, select the corresponding storage account, then select the target sub-source. For function apps, you need to provide private endpoint for file and blob. Click Next.
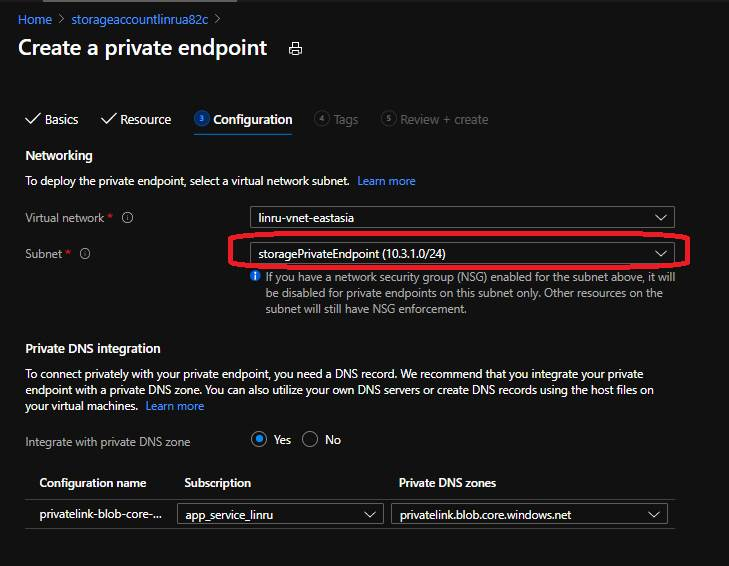
4.4 In configuration, select the vnet and subnet for private endpoints. Then review and create.
4.5 We need to create file and blob for function app, then go the whole scenario again to crate private endpoints for file. I myself created 4 private endpoints, blob, file, queue and table respectively.
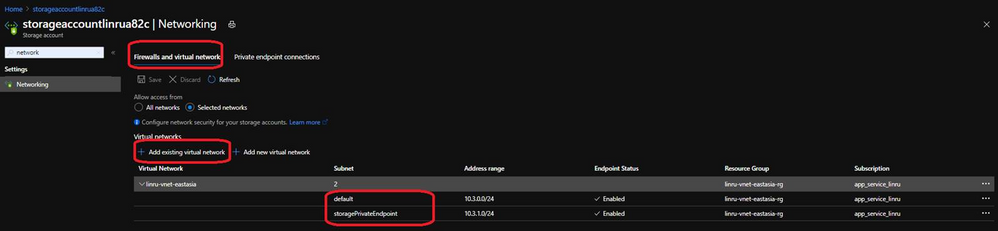
5. Set up firewall in storage account, blade “Networking” , allow access from existing two subnets of Vnet.
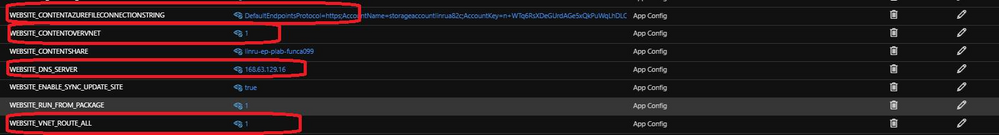
6. Something need to be caution here, we need to add corresponding app settings WEBSITE_CONTENTOVERVNET, WEBSITE_DNS_SERVER, and WEBSITE_VNET_ROUTE_ALL in order to make this feature work.
There is one thing you should be careful of when making these settings, as described in the feature documentation – the above settings should be set at the same time (in the same operation) as you set the WEBSITE_CONTENTAZUREFILECONNECTIONSTRING setting. This prevents some “confusion” on the Windows OS end when accessing the network share. Ordinarily, this would be set in a single ARM template, so all of the settings would naturally be set at the same time, but when experimenting in Portal, it’s easy to get the order wrong. Therefore, when enabling the feature on this site, you should first remove the Azure Files connection string (or point it somewhere else), wait a few minutes, then set the connection string at the same time as the other settings mentioned above.
Once done, it should be like this:
7. About runtime error reported in function portal – wake up the function runtime by accessing kudu site.
There is also sometimes a slight irregularity in how the feature interacts with Portal. It may report the “function runtime unreachable” error even when the feature itself is working as intended. Therefore, to verify whether the site is active, go to the SCM site’s Debug Console and verify that the content browser loads as usual. This “wakes up” the functions runtime and restores its connection to Portal.
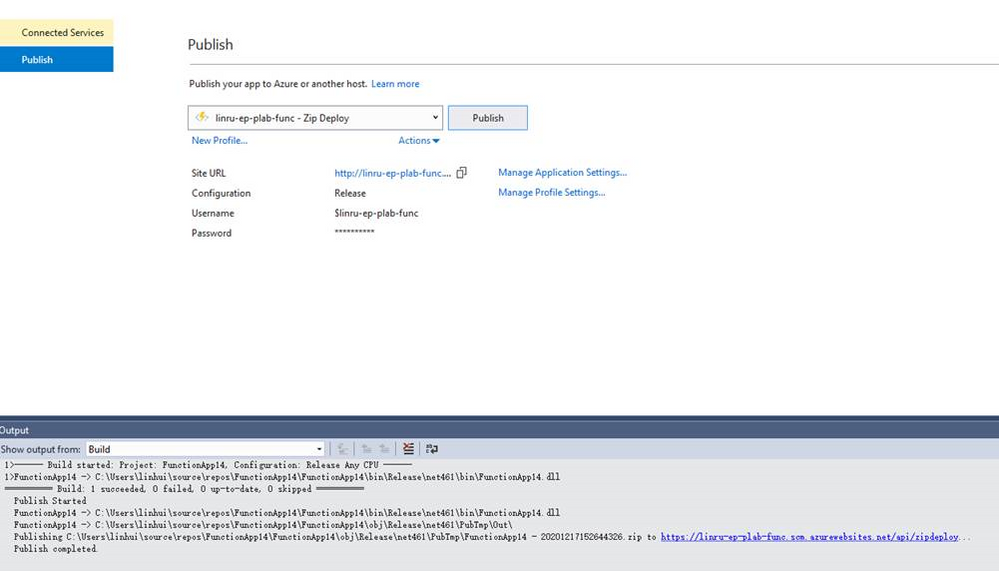
Test with different deployment methods:
Storage account is secured with firewall. Private Endpoints also grant smooth deployment experience from both VSTS and Web Deployment.
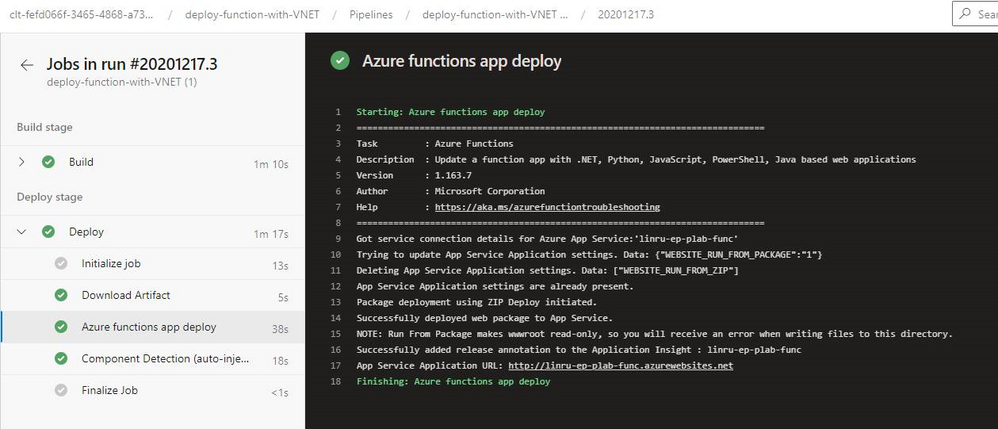
Try deploy with Azure DevOps, it ended with success.
Try deploy from local PC (it is not using the same code base as we used in Azure DevOps, after deployment it should have 3 functions)