This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
Introduction
This article is part of our Azure Defender PoC Series which provides you with guidelines on how to perform a successful proof of concept for a specific Azure Defender plan. For a more holistic approach where you need to validate Azure Security Center and Azure Defender, please read How to Effectively Perform an Azure Security Center PoC.
Azure Defender is the Cloud Workload Protection Platform (CWPP) built into Azure Security Center, which provides advanced threat detection and alerting for all kinds of hybrid and multi-cloud workloads, including servers and virtual machines, SQL databases, Storage, Containers and Kubernetes, Key Vaults, Web Applications, DNS, and Azure Resource Manager.
Planning
As part of your Azure Defender for Container Registries PoC, you need to identify the use case scenarios you want to validate. Unlike other Azure Defender plans, Azure Defender for Container Registries will not create security alerts based on Azure Defender’s threat intelligence. It will rather inform you about vulnerable container images that are found in your registry by creating a recommendation in the Remediate Vulnerabilities Security Control. Vulnerability management is an important part of security hygiene since bad actors can and will leverage open and/or undiscovered vulnerabilities to get access to your environment, to deploy malicious images, or to exfiltrate data. As of this writing, Azure Defender for container registries can scan Linux container images in an Azure Container Registry, which is accessible from the internet with shell access.
You can enable Azure Defender for Container Registries on the subscription level, with a 30 day free trial. Keeping that in mind, you should plan to execute your PoC prior to this expiration and, based on the results, decide to keep it enabled or not.

Preparation
In order to enable Azure Defender for Container Registries, you need a user account that has at least the Security Admin role. For more information about roles and privileges, read this article.
From a readiness perspective, make sure to review the following resources to better understand Azure Defender for Container Registries:
- Azure Defender for Containers | Azure Security Center in the Field #7
- Azure Defender for Container Registries Documentation
Implementation and validation
Once you have enabled Azure Defender for Container Registries, it will automatically start to scan your subscriptions for existing Azure Container Registries. Once protected, images scans wills be triggered on each Azure Container Registry as follows:
- whenever a new image is pushed to the registry
- continuously, when an image has recently been pulled (during the last 30 days)
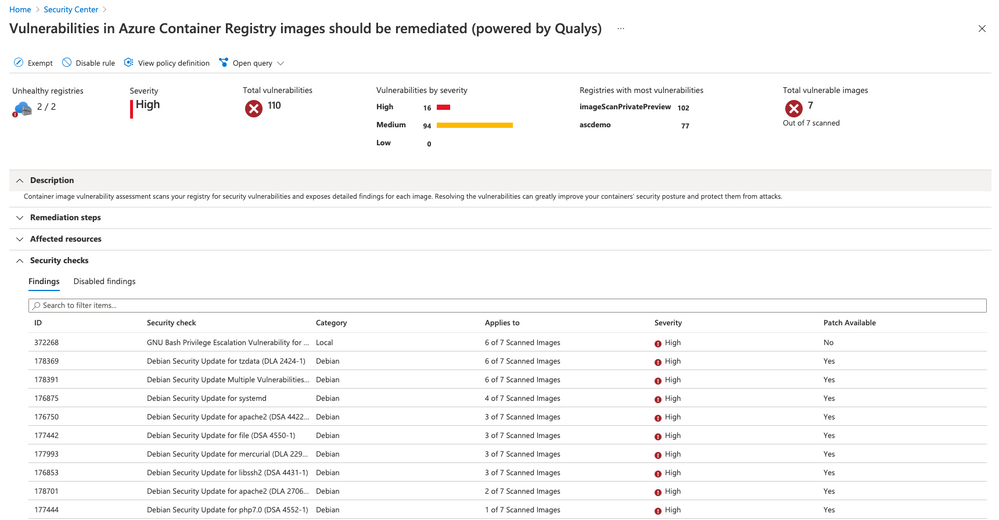
The recommendation will contain information about all affected resources, meaning all unhealthy registries with all unhealthy images in them, as well as information about all vulnerabilities that have been found. With that, you have two different views, focused on registry and image, or focused on vulnerabilities. In addition to that, vulnerabilities can be exported using Continuous Export, or accessed via our Sub Assessments REST API. Read this article for more information on how to scan your images for vulnerabilities.
Conclusion
By the end of this PoC, you should be able to determine the value of this solution and the importance to have this level of threat detection to your workloads.
Reviewers
Special thanks to Yuri Diogenes and Maya Herskovic for reviewing this article.
