This post has been republished via RSS; it originally appeared at: Intune Customer Success articles.
By Lothar Zeitler – Senior Program Manager | Microsoft Endpoint Manager – Intune
Frontline workers are essential in global workforces, performing critical jobs as first responders, supply chain workers, and many other roles across industries. For a long time, frontline workers used walkie-talkies (two-way radios) as the primary tool to communicate with colleagues and supervisors during their shifts. With the digital transformation of the last decade, workers need devices that offer more functionality and line-of-business applications, such as inventory management systems or Microsoft Teams for collaboration and communication.
However, for specific scenarios that require fast and direct communication, you can use the Walkie Talkie app in Microsoft Teams. The app provides instant push-to-talk (PTT) communication from a mobile device, without having to start Microsoft Teams or dial a phone number. Samsung offers the ability to configure a hardware button for the Walkie Talkie app on the Galaxy XCover Pro. Once configured and connected to a channel, you can use PTT functionality with the click of a button. For more info on this feature and applicable scenarios, see How to use Microsoft Teams Walkie Talkie on your Galaxy XCover Pro | (samsung.com).
In this post, we will walk through the steps to configure the Microsoft Teams PTT functionality for Intune-managed Samsung XCover Pro devices in Microsoft Endpoint Manager.
Set up device management in Intune
First, we need to and set up a device group for Samsung devices that are corporate-owned dedicated devices with Azure Active Directory (Azure AD) shared device mode. This is required to enable devices to support multiple users. For detailed instructions, see Setup Intune enrollment for Android Enterprise dedicated devices and Shared device mode for Android devices.
For this example, in the Microsoft Endpoint Manager admin center we created a new enrollment profile named “A_SM_XCover_MU” with the token type Corporate-owned dedicated device with Azure AD shared mode.
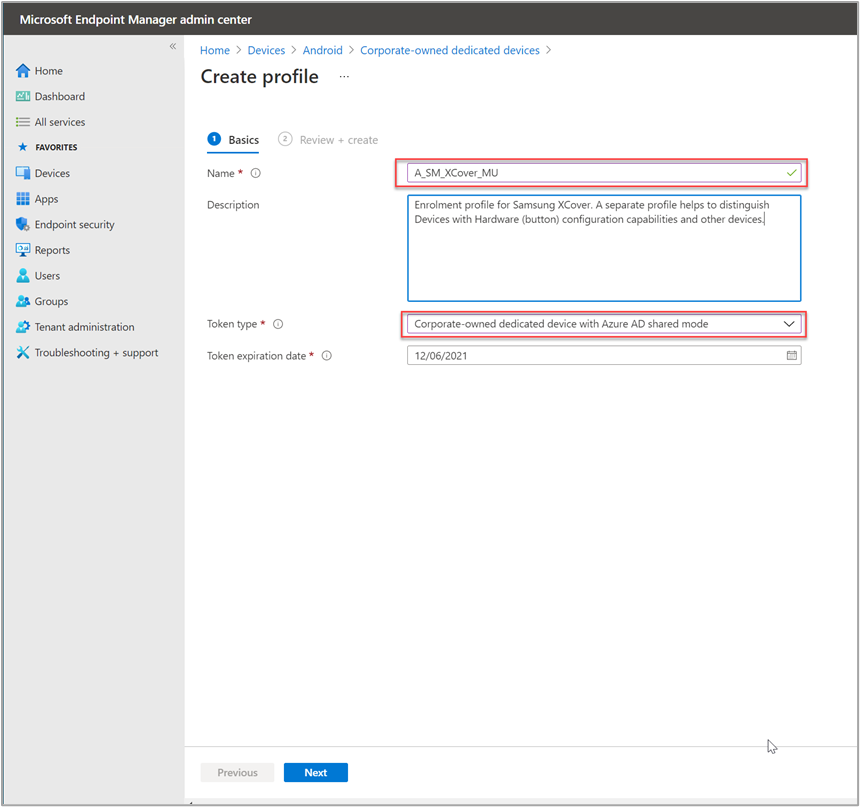
The example enrollment profile looks like this:
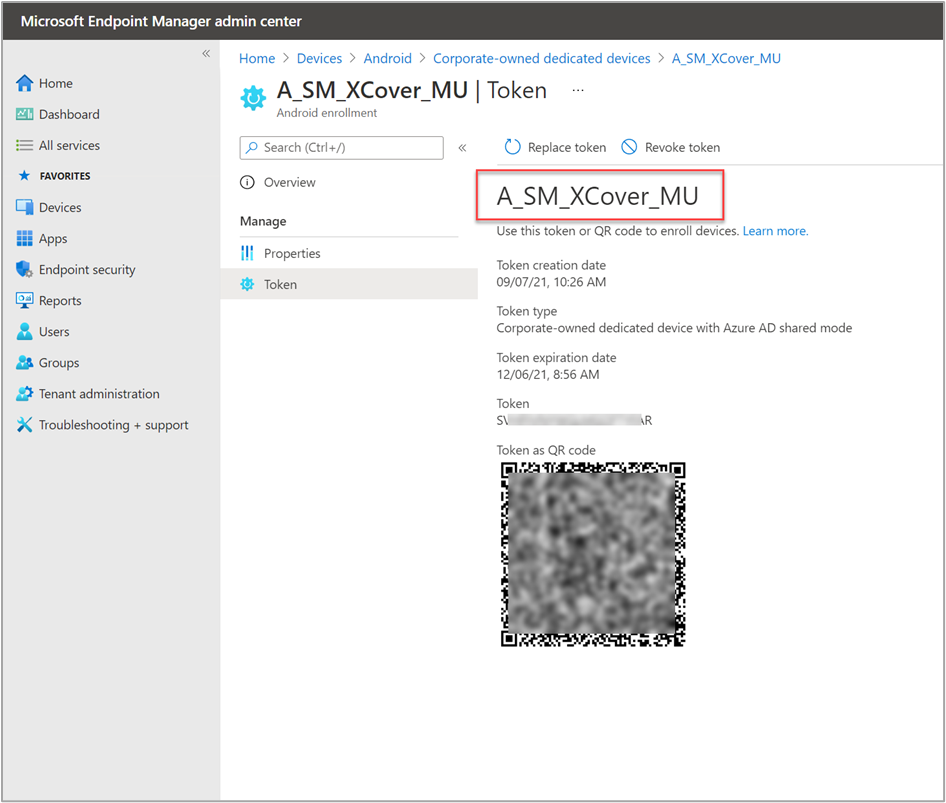
Next, we create a new device group to dynamically add all Samsung models with the same enrollment profile. We will use this dynamic group to assign policies, apps, and configurations, including the PTT configuration, to each new device that belongs to that group. We use the same enrollment profile name that we used for our device group: "A_SM_XCover_MU". When you create this new group, make sure to select Dynamic Device in the Membership type field.

As a membership criterion for the group, we use the name of the enrollment profile. We define the rule criteria under Dynamic device members > Add a dynamic query. Under Property, we select enrollmentProfileName, then under Operator, select Equals, and under value, we enter the profile name " A_SM_XCover_MU."
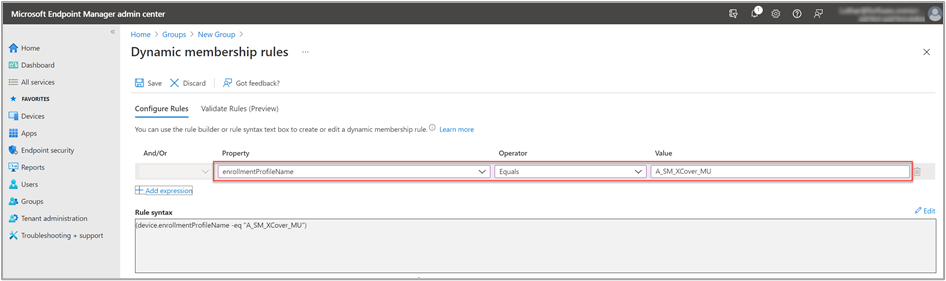
Now, all devices that are enrolled with this profile in Intune automatically become members of our group.
Create a compliance policy for shared devices
The default settings of Intune require a custom compliance policy. This setting might have been changed in your environment, but we create and assign a custom compliance setting for our shared devices for our testing.
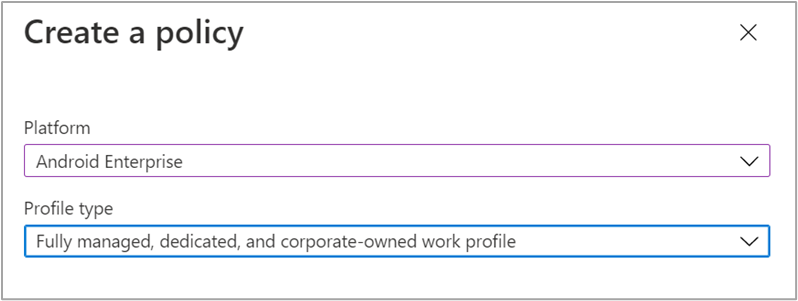
First, we create a new compliance policy and select Android Enterprise as the platform and Fully managed, dedicated and corporate-owned work profile as the profile type.
The next step is to define a name and optionally a description in the Basics section. We name our example "A_SM_XCover_MU_Compliance".

We choose the minimum OS version as the compliance setting and set the value to "10".
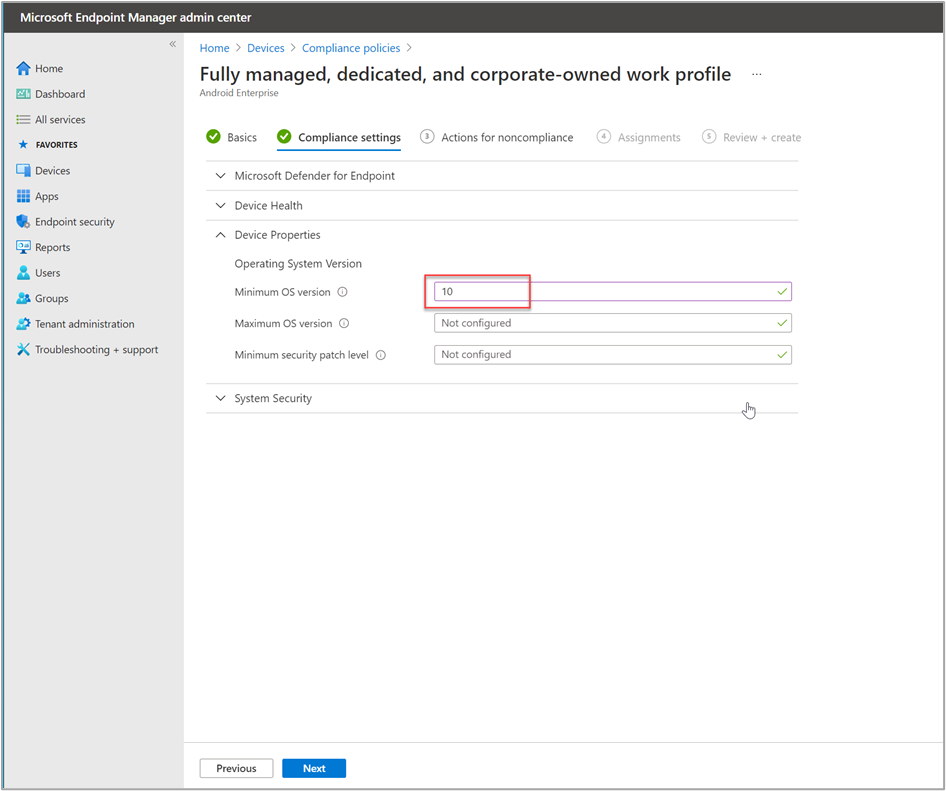
We leave the default settings on the Actions for noncompliance tab and continue to Assignments. Here, we add the dynamic group we created "A_SM_XCover_MU" and click Select.

We review the new compliance policy settings and select Create.

Add apps for installation
We'll focus on the key applications we need to enable PTT communication on shared devices. Our example uses the Microsoft Teams Walkie Talkie app and the configurable hardware, walkie-talkie button on Samsung Galaxy XCover Pro devices. It also requires the Microsoft Managed Home Screen app.
First, let's assign Teams to the Galaxy XCover Pro devices. In the Microsoft Endpoint Manager admin center, we go to Apps > All apps > Add, and in the Select app type pane, select Managed Google Play app.

In the Managed Google Play app store, we select Microsoft Teams.

Next, we select Approve to accept the app permissions and the requirements in Managed Google Play.
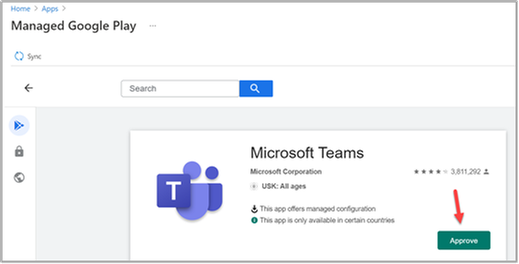

Additionally, we need to decide how we'll handle permission changes. In our example, we choose to keep the app approved when it requests new permissions, and then select Done to confirm.

Next, we repeat these same steps to add the Managed Home Screen app.
Create app assignments
Once we’ve added both apps (marked in red in the following image), we need to create assignments in Intune to install them on your devices. In contrast, the Microsoft Authenticator and Microsoft Intune apps (marked in green) will be installed automatically during enrollment.
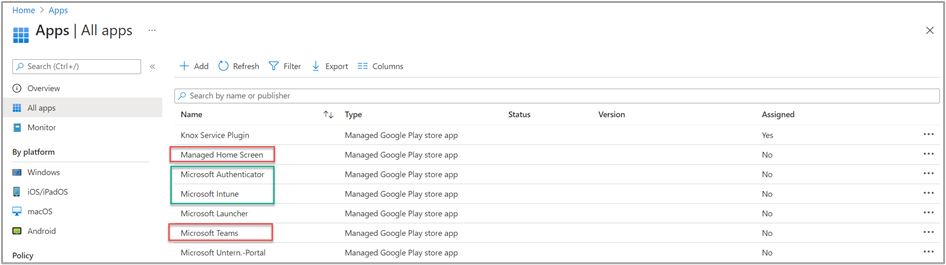
We’ll walk through the steps to assign the Teams app to our device group. In the Microsoft Endpoint Manager admin center, we go to Apps > All apps and select the Microsoft Teams app. We select Properties and then next to Assignments, select Edit to get to the assignment settings.
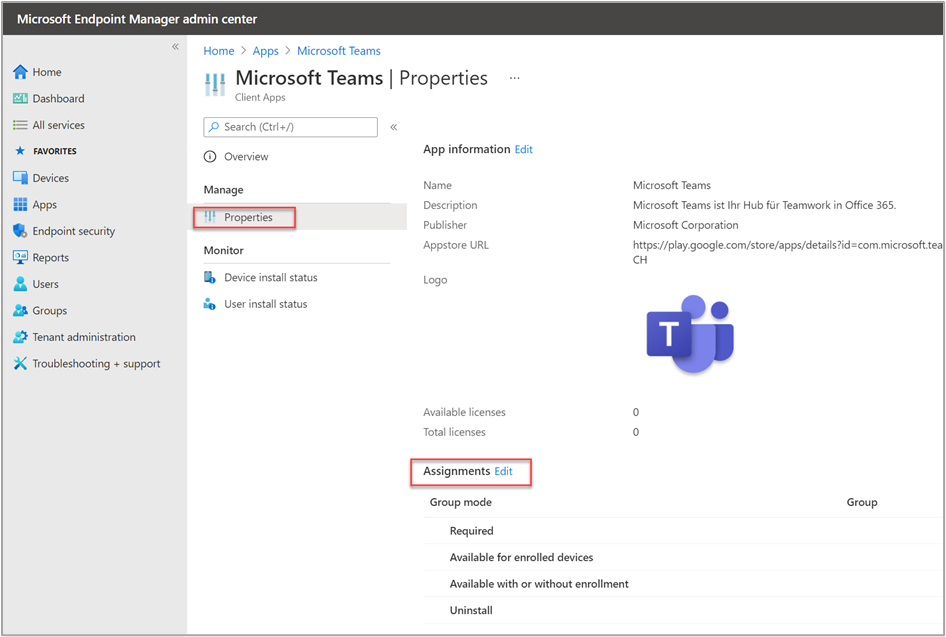
Under Required, we select Add Group and then select the group we previously created for the Galaxy XCover Pro devices, "A_SM_XCover_MU". We select Review + save to finish the assignment.
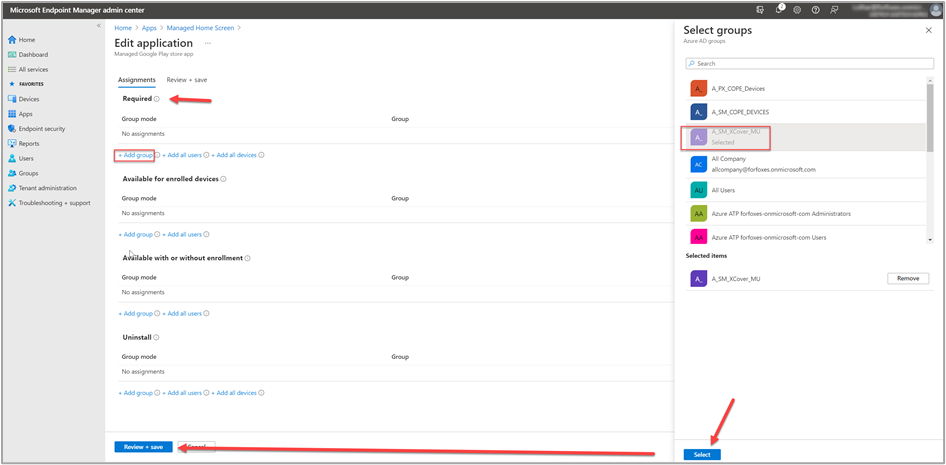
Finally, we repeat these steps to assign the Managed Home Screen app to same device group.
Create an app configuration policy
We need to create a new app configuration policy to set up Managed Home Screen specifics.
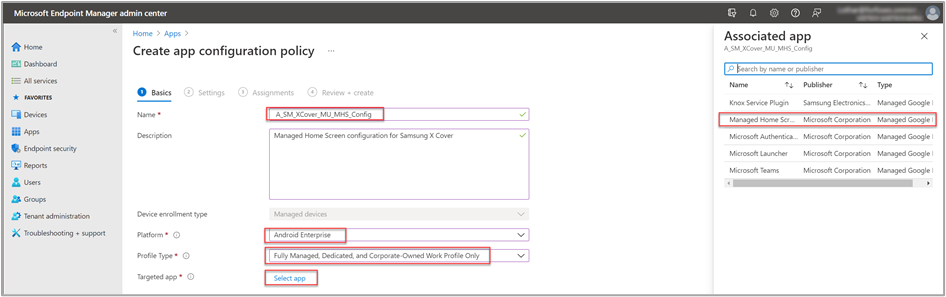
In the Microsoft Endpoint Manager admin center, we go to Apps > App configuration policies and select Add > Managed devices. We name the policy "A_SM_XCover_MU_MHS_Config" and select the platform Android Enterprise and the profile type Fully Managed, Dedicated, and Corporate-Owned Work Profile Only. For the targeted app, we select Managed Home Screen from the Associated app tab.
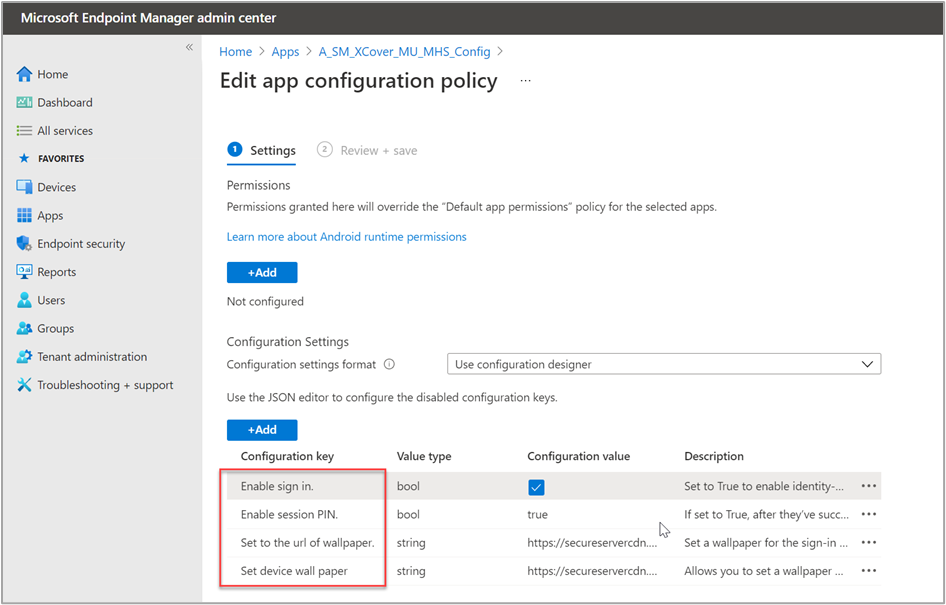
We can use the configuration designer to search for and add specific values we want to configure.

We added the settings Enable Sign in, to require Azure AD users to sign in, and Enable Session PIN, which is a device PIN that is valid until the session is closed and the user logs off. We added wallpaper settings as additional values, however these are not necessary for this example.
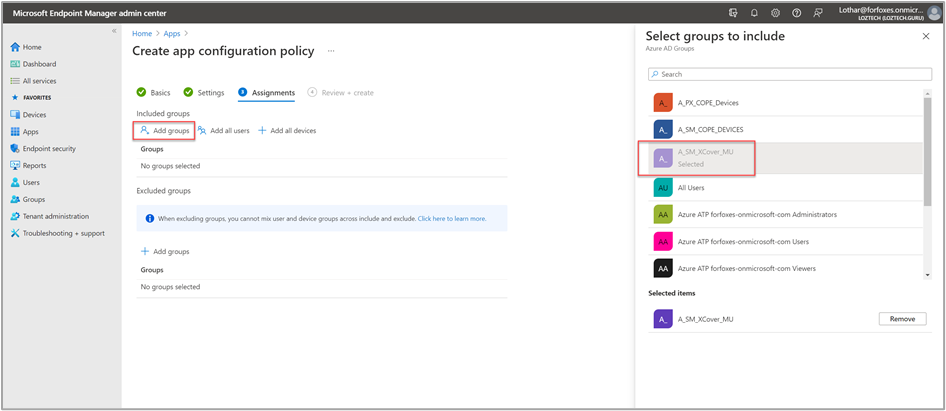
In Assignments, we assign the policy to the device group we created earlier.
Create a device configuration profile
The next activity is to configure the kiosk settings for the devices. To do this, we need to create a device configuration profile. We go to Devices > Configuration profiles > Create profile. We select Android Enterprise as the platform and Device restrictions as profile type.
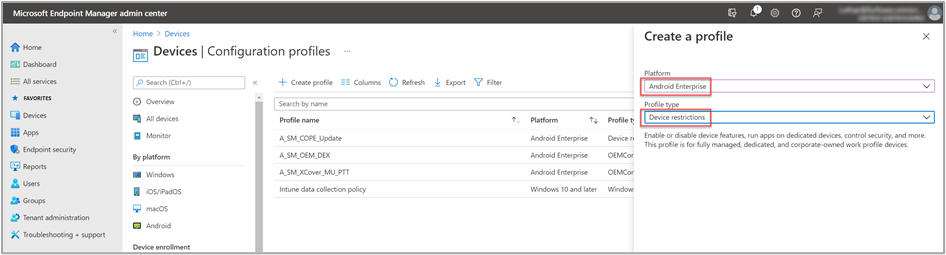
In the Basics tab, we name the profile "A_SM_XCover_MU_MHS_Kiosk_Config" and add a short description, which is optional.
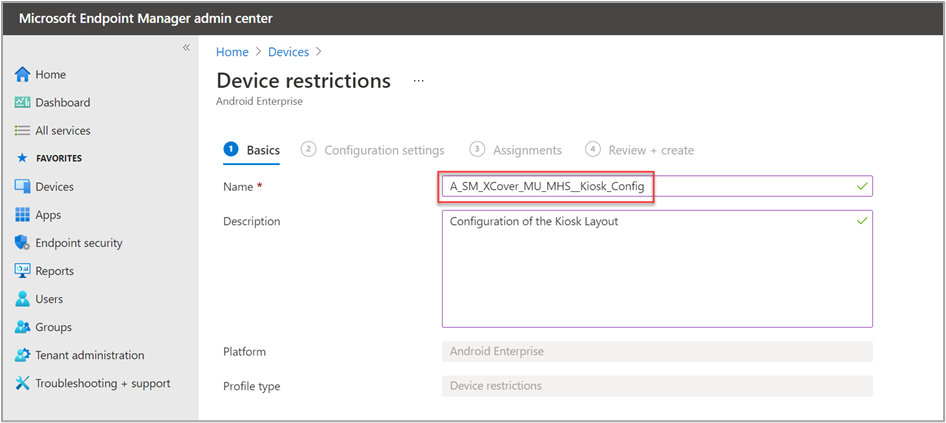
In the Configuration settings tab, we select Dedicated device as the enrollment profile type. For Kiosk mode settings, we choose Multi-app to configure our device to allow more than one app on the screen.
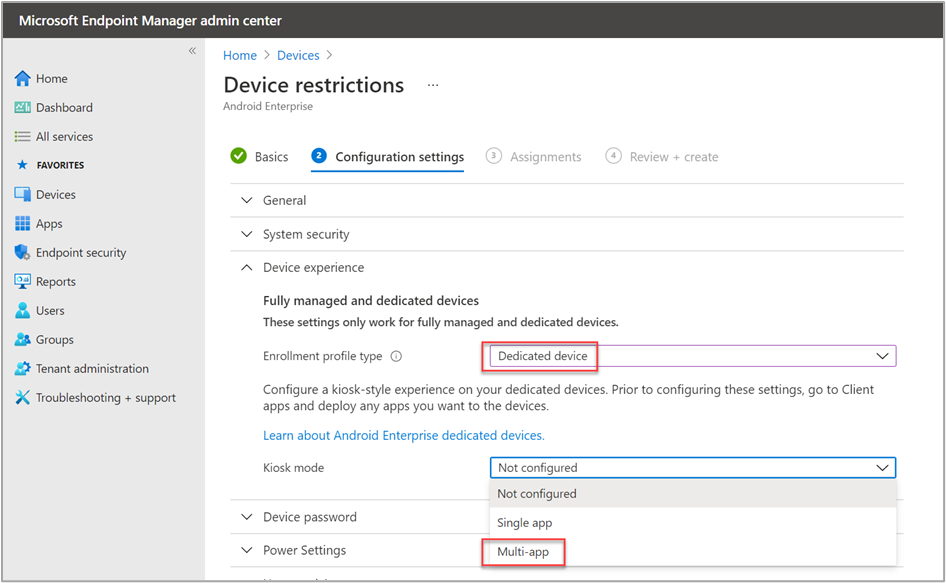
With a custom layout, we can pick the format that suits our multi-app device best. To do this, we enable the Custom app layout setting and choose a grid size of 3x4 for our example.
The next step is to specify where the apps should appear. We add the Teams app to a grid location.
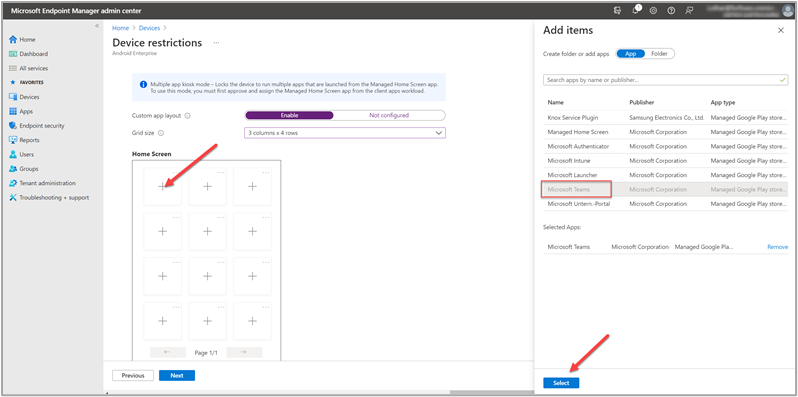
Next, we continue to the Assignments tab to assign the device restrictions to the Galaxy XCover Pro device group, as we did in previous sections. Then we review and create the new profile.
Create an OEMConfig profile
The last policy definition in Intune we need is an OEMConfig policy to assign Teams PTT functionality to the hardware button of the Samsung XCover Pro device.
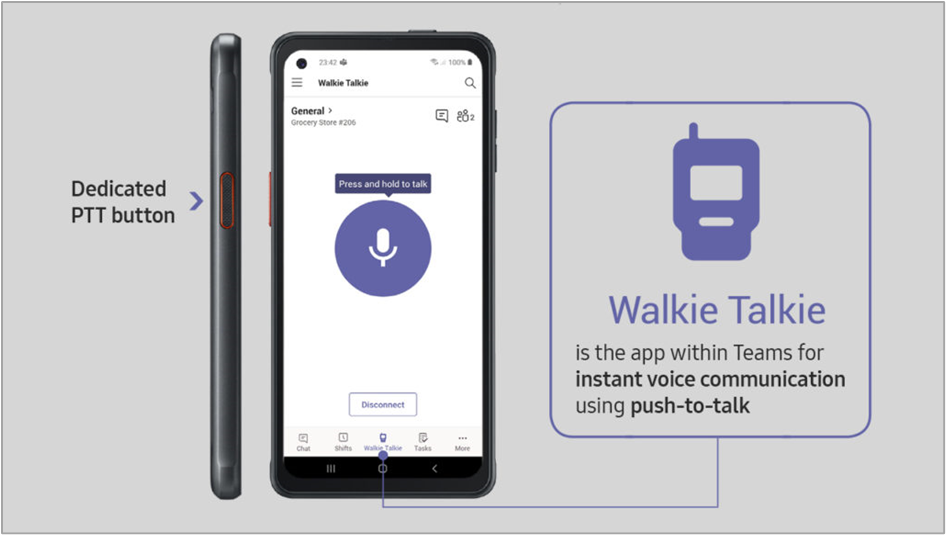
(Source: How to use Microsoft Teams Walkie Talkie on your Galaxy XCover Pro | (samsung.com)).
First, we need to create an OEMConfig profile in Intune. To get started, we create a new configuration profile for the Android Enterprise platform and type OEMConfig.

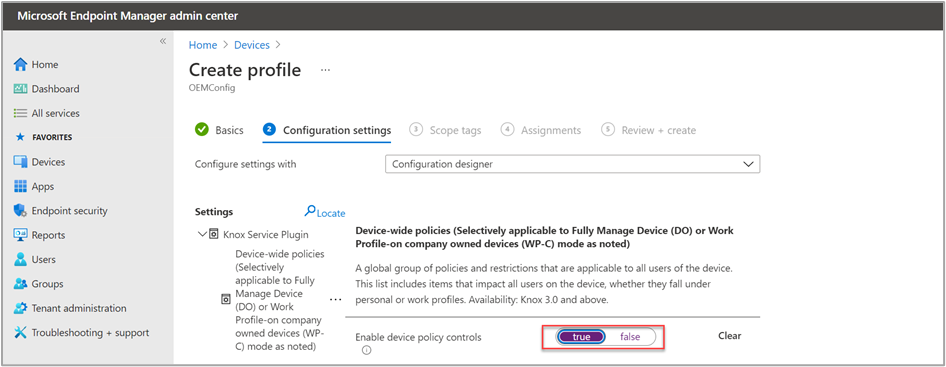
Next, we name the new profile "A_SM_XCover_MU_PTT" and add an optional description. To process the OEMConfig settings, we choose the Knox Service Plugin as our OEMConfig app.

Now we can edit the relevant OEMConfig setting in the configuration designer. We set Enable device policy controls to true.
Next, we define a profile name within the Knox Service Plugin, "PTT Config for MS Teams", and add our KPE Premium license key. We select Configure to see additional, device-wide settings.
Note: Alternatively, you can use the Locate search link to find settings quicker.
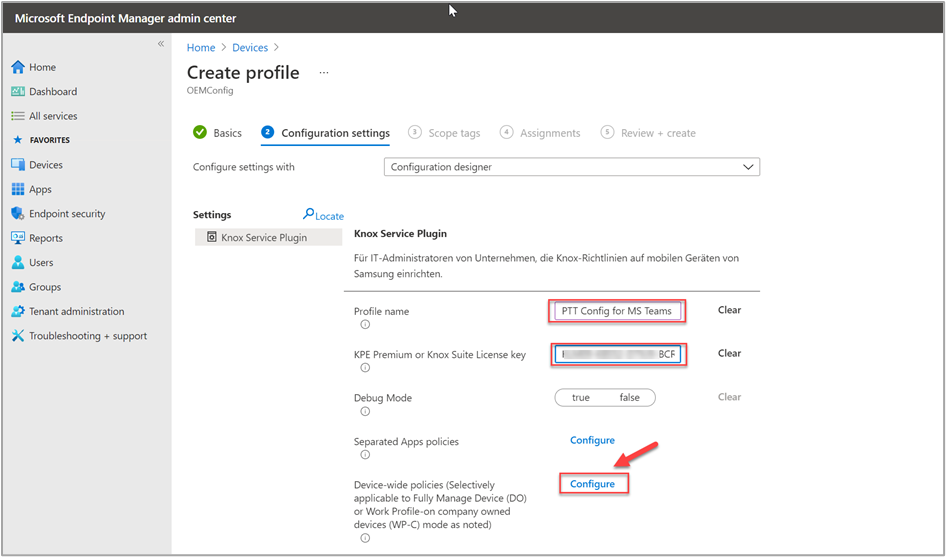
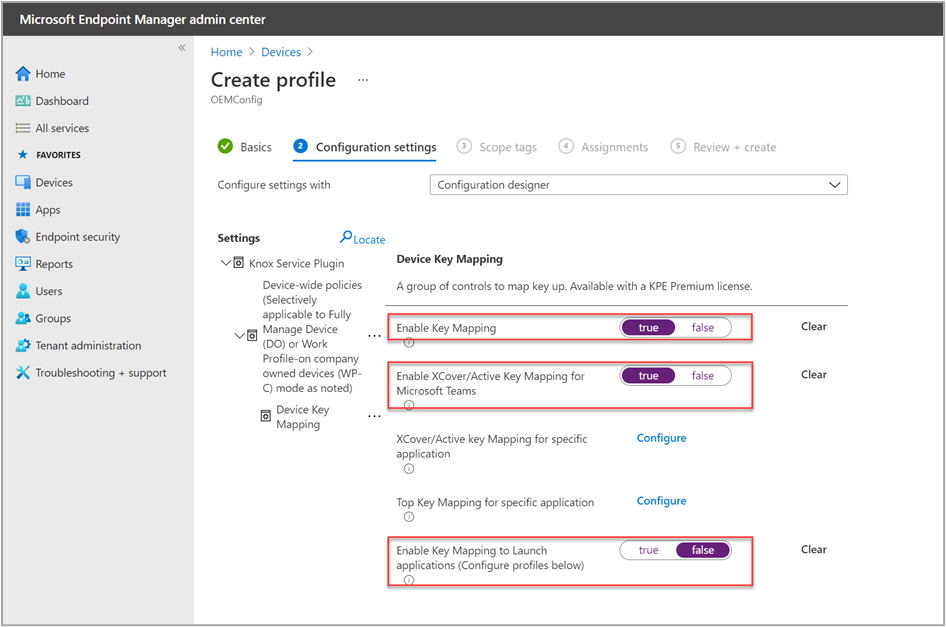
Next to the Device key Mapping option, we select Configure.

In the device Device Key Mapping section, we configure three parameters. First, Enable Key Mapping must be set to true. The second setting, Enable XCover/Active Key Mapping for Microsoft Teams, also must be set true to link Teams to the hardware button. And lastly, Enable Key Mapping to Launch applications must be set to false (to disable this feature).
For information on using the Knox Service Plugin to map the XCover Pro key to Teams, see Microsoft Intune: Map key for Walkie Talkie | (samsungknox.com).
In the Assignments tab, we assign this profile to the device group as we did in earlier sections. We have configured everything we needed in Intune. Now we will continue to our Teams configuration.
Add the Walkie Talkie app
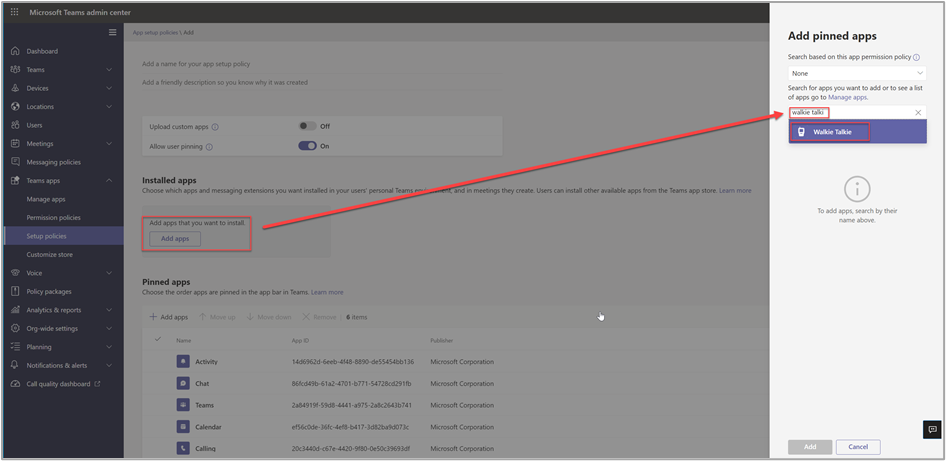
The Walkie Talkie function is not enabled by default in Microsoft Teams. To enable it for your users, you need to use the admin center. You'll need a Teams policy that targets the right group of users, e.g., all frontline workers (your company might have an existing Teams policy you can use). To add the Walkie Talkie function, you add the app (Add apps) to the policy. Then, pin app for easier discovery.
When the user logs on to the device and starts Teams, they see a list of channels to choose from. When the user starts the Walkie Talkie app, they select the channel they want to use. After that, the user can either push the Walkie Talkie button in the app or the hardware button on the XCover Pro device.

Note: If the Walkie Talkie app is assigned to the hardware button, users can communicate with Walkie Talkie even if the device screen is off.
The following video shows the use of a dedicated device with Walkie Talkie enabled.
Now that you have a better understanding of how to enable Microsoft Teams Walkie Talkie on Galaxy XCover Pro devices in Microsoft Intune, you can help your company take advantage of this convenient technology. If you have any questions, reply to this post or reach out to @IntuneSuppTeam on Twitter.
