This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
In May 2021, Microsoft announced a new threat monitoring protection for SAP systems in Microsoft Sentinel. Since then, we’ve continuously increased our out-of-the-box, predefined content, and after you’ve deployed the solution in your Microsoft Sentinel workspace, 50 different analytics rules, watchlists, and workbooks are added. In this blog we’ll go over the different features supported by our new workbooks.
The main purpose of Microsoft Sentinel workbooks for SAP is to visualize and monitor data ingested via the SAP data connector. Workbooks provide a flexible canvas for data analysis, and for the creation of rich, visual reports in your Microsoft Sentinel workspace. Workbooks help you visualize your data from your workspace logs and combine them into unified interactive experiences. The SAP workbooks include one general workbook focused on the ABAP Security Audit log, and 3 other workbooks, which are use-case oriented. These workbooks are customizable templates: edit, remove, or add any chart or visualize anything.
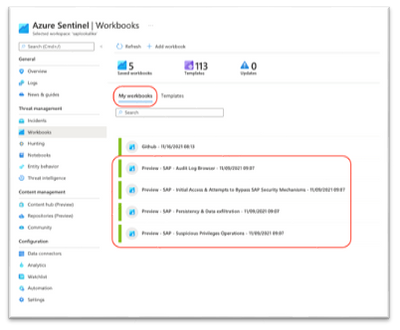
After deploying the SAP solution and the content hub, SAP workbooks are found in the My workbooks tab:
Our current SAP solution has four different workbooks:
1. SAP - Audit Log Browser
The Audit Log Browser is a workbook focused on the ABAP security audit log.
It gives users a general view about their SAP systems and helps them monitor all several aspects. Users can pick filtering parameters, such as a relevant system, or all systems, and the time scope for the workbook.
The SAP – Audit Log Browser workbook contains:
- Health Overview - an overview on the current activity in the system, including the user login, events by system, messages and ABAP programs.
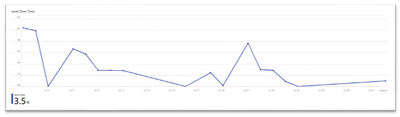
For example, the following image shows a time chart with the number of users login by bins of days.
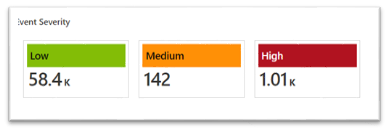
- Events - an overview about events in the system, including filters for severity and user, and showing the events over time. This page shows tiles for each severity (low, medium, high) and the count of the events. Pick a tile to filter events by the selected severity. For example:
- Multiple Logons by User - a list that shows the sign-ins from the same user from several terminals, within a scheduled time interval. For example: All events with <severity> severity by user <user> - a list of all events with the selected user and severity. For example:
- Events Over Time - a time chart showing events over time. We can identify an increase in our number of events that can be caused by a suspicious event that we should investigate. There's an option to choose the time frame - from three months back to 24 hours and even less.
2. The second workbook is named Initial Access & Attempts to Bypass SAP Security Mechanisms. This workbook focuses on two different use cases: Initial access and attempts to bypass SAP security mechanisms.
- Initial Access consists of techniques that use various entry vectors to gain their initial foothold within SAP system.
- Attempts to bypass SAP security mechanisms consists of techniques that attempt to bypass security mechanisms without being detected.
The relevant logs are:
- ABAP security audit log (ABAPAuditLog_CL)
- ABAP Table Data logging (ABAPTableDataLog_CL)
- SAP’s system log.
Users can choose parameters, such as the relevant system or systems, and the time scope for the workbook.
- Multiple Logons by User - a list that shows the sign-ins from the same user from several terminals, within a scheduled time interval. For example:
- Select a user to drill down to their current activity:
- Brute Force Attacks by User – a bar chart showing brute force attacks on a SAP system, according to failed sign-in attempts for the backend system (Count by user). For example:
Sensitive Actions
Sensitive actions include sensitive: transaction codes, ABAP programs, function modules.
These actions are configured by our customers as sensitive by the relevant watchlists:
- SAP - Sensitive Transactions
- SAP - Sensitive ABAP Programs
- SAP - Sensitive Function Modules
Solution workbooks include the following graphs for sensitive actions:
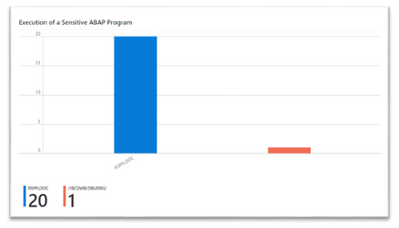
- Execution of a Sensitive ABAP Program - a bar chart that shows the count of executions for each sensitive ABAP program.
- Execution of a Sensitive Transaction Code - a bar chart that shows the count of executions for each sensitive transaction code. For example:
- System Configuration Change - a list of system configuration changes. For example:
3. The third workbook is Suspicious Privileges Operations - this workbook focuses on two different use cases: Persistency and Data exfiltration.
Persistency is a broad term used to describe an attack campaign in which an intruder, or team of intruders, establishes an illicit, long-term presence on a network.
Data exfiltration occurs when malware and/or a malicious actor carries out an unauthorized data transfer from a system.
The relevant logs for this workbook are:
- ABAP Audit Log (ABAPAuditLog_CL)
- ABAP Table Data Log (ABAPTableDataLog_CL)
- ABAP Spool Log (ABAPSpoolLog_CL)
- ABAP Spool Output Log (ABAPSpoolOutputLog_CL)
- Syslog
Users can select parameters, such as a relevant system (or all systems), and the time scope for the workbook.
ICF Services
An overview about ICF services, also known as internet communication framework services. The Internet Communication Framework is the layer between Internet Communication Manager (ICM), which sends and receives HTTP requests, and the SAP Web Application Server work process opening a door, an interface to the SAP system.
This workbook includes the following graphs:
- ICF Service by Operation - a stacked bar chart shows a bar for activated/deactivated services, split by service and the number of times it was activated/deactivated.
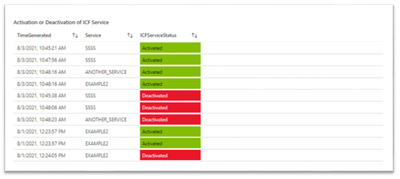
- Activation or Deactivation of ICF Service - shows a list of services with their current status. (Activated or deactivated)
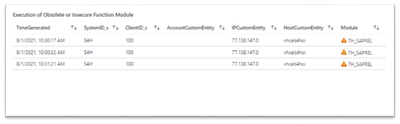
- Insecure Operations - insecure or obsolete operations are function modules or ABAP programs that are defined as insecure or obsolete in the following watchlists: SAP - Obsolete Function Modules and SAP - Obsolete Programs. This is a chart of execution of obsolete or insecure function modules - a list that shows all executions of obsolete or insecure function modules. For example:
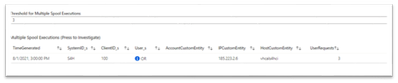
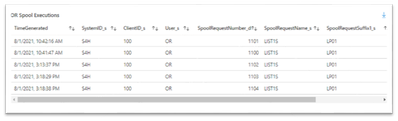
- Spool & Downloads - an overview on spool (printing) requests, spool outputs and downloads. This is a list of all multiple spool executions. Multiple is defined by user input in the Threshold for Multiple Spool Executions. Select a user to drill down to a list of their spool requests and time chart of their spool requests by time. For example:
4. The fourth workbook is Suspicious Privileged Operations - this workbook is focused on suspicious privileges operations. Suspicious privileges operations are sensitive authorizations (roles, profiles) given to users, or configuration changes of roles (adding or removing authorization objects). This workbook also monitors suspicious activity of sensitive privileged users.
The relevant logs are: ABAP Audit Log (ABAPAuditLog_CL) and ABAP Change Docs Log (ABAPChangeDocsLog_CL).
Users can select parameters, such as the relevant system or systems, and the time scope for the workbook.
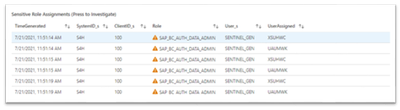
- Authorizations - an overview about users who are given sensitive authorizations, such as sensitive roles or sensitive profiles. This chart is for sensitive role assignments - a list that shows sensitive role assignments for users. For example:
Select a user to drill down to their current activity. For example:
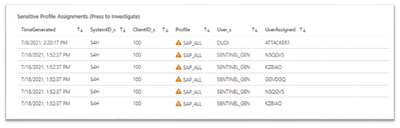
- Sensitive Profile Assignments - a list that shows sensitive profile assignments for users. For example:
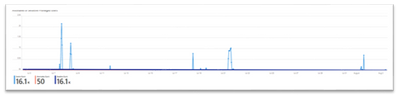
- Anomalies of Sensitive Privileged Users – a time chart that shows anomalies of sensitive privileged user events. For example:
- Changes in Authorizations - an overview about changes made in sensitive roles, including Roles Changes - a list of sensitive role changes. For example:
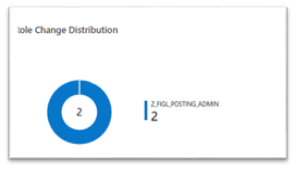
- Role Change Distribution- a pie chart that shows the distribution of sensitive role changes and the number of times it changed. For example:
Start Now!