This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
Microsoft Sentinel is a cloud native SIEM that offers robust capabilities to detect and hunt for actionable threats. Microsoft Sentinel provides various ways to import threat intelligence data and use it in different parts of the product like hunting, investigation, analytics, workbooks etc. Some of the ways to import rich threat intelligence data into Microsoft Sentinel include the Threat Intelligence - TAXII data connector, Threat Intelligence Platforms (TIP) connector and import of indicators through a flat file.
Microsoft Sentinel was one of the early adopters of STIX/TAXII as the preferred way to import threat intelligence data. Microsoft Sentinel “Threat Intelligence -TAXII” connector uses the TAXII protocol for sharing data in STIX format. This data connector supports pulling data from TAXII 2.0 and 2.1 servers. The Threat Intelligence – TAXII data connector is essentially a built-in TAXII client in Microsoft Sentinel to import threat intelligence from TAXII 2.x servers.
Today we are announcing the availability of the ReversingLabs TAXII Server which allows you to get threat intelligence data from ReversingLabs into Microsoft Sentinel using the Threat Intelligence – TAXII Data Connector.
ReversingLabs + Microsoft Sentinel Solution
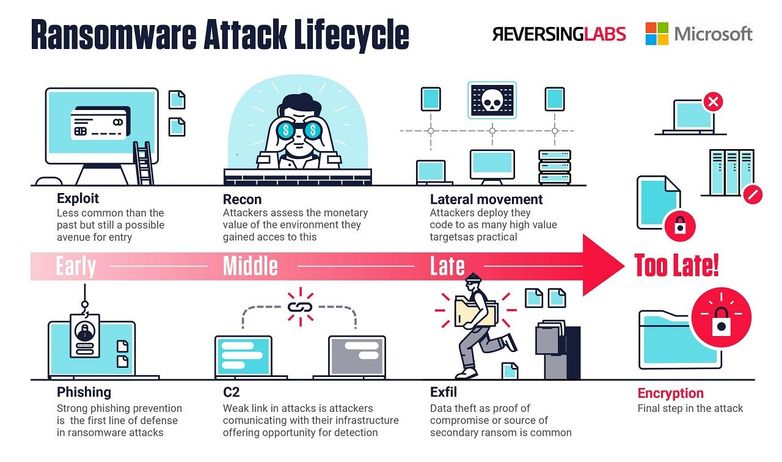
The ReversingLabs and Microsoft Sentinel integration makes it easy to gain deeper visibility and advanced context of IOCs on Ransomware groups and the malware they use to conduct their operations — providing an early stage detection and protection strategy for your organization. Using data from the ReversingLabs Ransomware feed, Microsoft Sentinel users can proactively protect against threats with automated intelligence in real-time. ReversingLabs is one of the most comprehensive, automated IOC solution, powered by ReversingLabs’s data lake of malware files, machine learning detection based on file and URI patterns, harvesting large data sets of good and malicious files using advanced static analysis processing, reputation analysis, providing you with a deeper, enriched, and highly organized MITRE ATT&CK tagged sorted dataset of operational threat intelligence.
Microsoft Sentinel benefits with ReversingLabs Ransomware Feed:
Incident response security teams can automatically triage alerts by receiving IOCs from ReversingLabs (machine-to-machine) and gain unparalleled context with essential explanations of IOCs (URLs/URIs, IPs, File Hashes, Domains, etc.). Malware researchers can hunt for malicious indicators of compromise in their organizations network by conducting deep analysis of malware used by Ransomware Groups, Affiliates, and RaaS operators. Users can then pivot to the ReversingLabs TitaniumCloud, A1000, and TitaniumScale Product Suite to further investigate threat actors and contexts in order to protect their organization’s most critical assets and continue to mature their security operations.
Connecting Microsoft Sentinel to ReversingLabs TAXII Server
To connect Microsoft Sentinel to ReversingLabs TAXII Server, obtain the API Root, Collection ID, Username and Password from ReversingLabs. To obtain access to ReversingLabs via Microsoft Sentinel, please contact ReversingLabs at “sales@reversinglabs.com”.
For more details on how to configure the TAXII data connector in Microsoft Sentinel, please refer to the following documentation.
Put ReversingLabs threat intelligence to use in Microsoft Sentinel
Once the threat intelligence from ReversingLabs is imported into Microsoft Sentinel, you can use it for matching against log sources. This can be done using the out-of-the-box analytic rules in Microsoft Sentinel. These completely customizable analytics rules used to match threat indicators with your event data all have names beginning with, ‘TI map’.
To learn how to enable and create analytic rules, follow the steps mentioned in this documentation.
You can also create customized dashboards using Workbooks in Sentinel to get a deeper understanding of the threat landscape covered by the ReversingLabs feed.
Hope this article has helped you understand the advantages of importing the ReversingLabs Ransomware feed into Microsoft Sentinel and use it to protect your organization against known Ransomware Groups.