This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Introduction
In this blog, I discuss the importance of proactive security posture management, how security teams can be organized for security posture management, how roles and responsibilities can be divided among the teams. I further discuss what a person with proactive security posture responsibilities needs to do and how to do it by leveraging Microsoft Defender for Cloud’s Attack Path capabilities.
Security Posture Management
when it comes to reduce the attack surface. The Cloud Security Posture Management team needs to t. This will require more investments in proactive measures that can anticipate potential attacks. Having a proactive approach will help prevent risks from brewing into bigger problems and facilitate better culture and communication between Devops and security teams, so that Open SSL vuln. type of issue wouldn't happened as often.
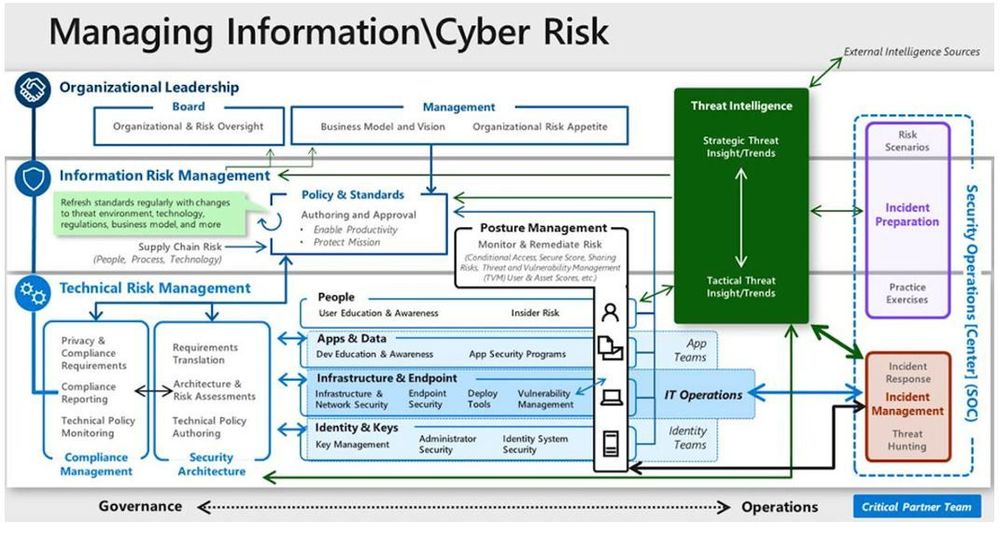
Enterprises may have different approaches for organizing security functions and assigning roles and responsibilities. In the article How to organize your security team: The evolution of cybersecurity roles and responsibilities, Microsoft suggests the following functions to represent a fully populated enterprise security team:
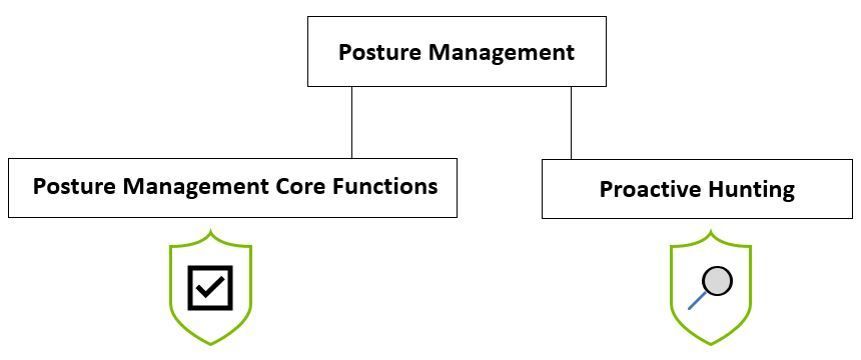
Posture Management in this diagram is shown as a function that cross many areas. Since this function is evolving, it might be the responsibility of a dedicated team, or it might be provided by other teams. The diagram below has an example of how Posture Management teams can operate to have a bigger impact in the overall security posture of their cloud workloads:
Posture Management Core Functions should be able to assign dedicated team members that can perform the following roles and responsibilities:
- Posture Management Core Functions
- Track Secure Score improvement overtime.
- Create Governance rules and assign remediation tasks to workload owners.
- Track existing tasks to see what’s on time and what’s not and if there are “red” ones to address.
- Ensure that all lessons learned are shared with the Cloud Governance Team so they can create guardrails in the beginning of the pipeline to avoid workloads that are not using security best practices be provisioned.
- Proactive Hunting (although the term Hunting is usually used for Threat Hunting, this function is more related to SOC activities as shown in the first diagram)
- Proactively use the Attack Paths to ensure all critical paths are remediated.
- Proactively use Cloud Security Explorer to hunt for new vulnerabilities and misconfigurations in the environment.
- Proactively fine-tune the recommendations with specific insights (for example: disk encryption for VMs or storage encryption but you want to start with those that have internet exposure or have specific or any vulnerabilities)
While this is a proposal breakout of tasks and responsibilities, nothing stops you from having all those tasks belonging to a single team and assigning those tasks to different team members. It is up to you and your organization’s needs how you will manage this. The important aspect to remember is that you need to tackle all tasks to ensure that you are not only continuously remediating security recommendations but also proactively finding areas of improvement in your overall cloud security posture.
Proactive Hunting
Members of the CSPM Hunting Team have one main goal to accomplish: proactively hunt for points of entries to reduce the attack surface and decrease the likelihood of compromise. Keep in mind that points of entries can be external (publicly accessible through the Internet), but also internal (when dealing with internal malicious actors).
Identifying potential points of entry
To proactively hunt for points of entries and reduce the attack surface, security posture managers can start their day by visiting the Microsoft Defender for Cloud Attack Path dashboard and reviewing the total attach paths. Below is a screen shot showing an example of the Attack path dashboard:
One of the main advantages of the Attack Path is that it looks for points of entries and lateral movement not only in Azure, but also in AWS and GCP. If you don’t have Defender for Cloud monitoring your multicloud environment, make sure to visit the following resources to learn how to configure:
Each attack path represents a scenario that you should be aware, and this scenario has the following breakdown:
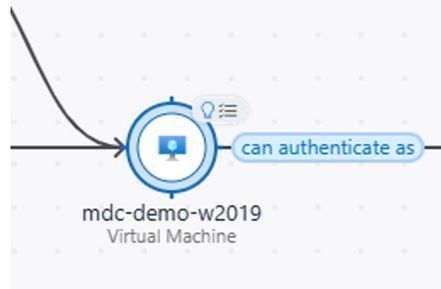
By reading the scenario, you immediately know that you have one public point of entry, that can be used to exploit the target (VM) due to the high severity vulnerabilities that are open on that VM. Once there, the threat actor has a communication path that can lead to read access in another target (Key Vault). Now the full picture of this attack path appears once you click on it, and you have the full analysis of the potential attack that can take place, as show below:
With this visualization you can clearly see what can potentially happen. As you look at this path, noticed that some elements contain a light bulb with a list on top of it, as shown below:
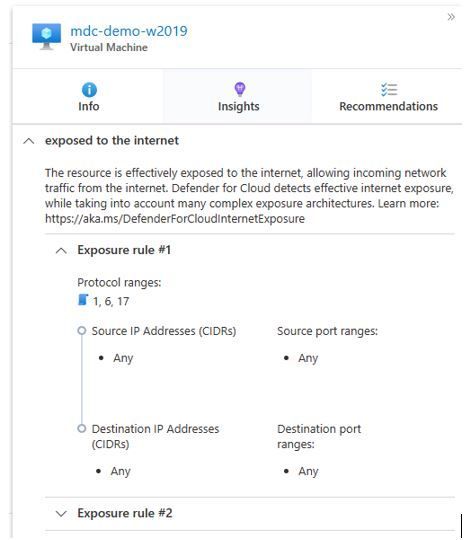
This means that once you click on this object you will see extra insights as well as the recommendations associated with this workload, as shown below:
Now the team has a complete picture of:
- Which resource can potentially be compromised.
- Why this resource is exposed.
- What are the open recommendations that must be addressed and actions that could be taken.
With this information, one of the team members can start working on the remediation of this resource using the remediation steps associated with the recommendations.
Proactive hunting vulnerable workloads
Another activity that the CSPM Hunting Team needs to do is to ensure that they are at least one step ahead of threat actors. To do that, they need to ensure that they are proactively working to identify potential areas of compromise.
For example, one Proactive Hunting team member read an article about a crypto mining campaign that targets specifically Kubernetes environments. According to his research, there was a learning about what differs this attack from other crypto mining attacks is its scale: within only two hours a malicious container was deployed on tens of Kubernetes clusters. Threat actors can exploit Kubernetes environment by scanning the Internet to try to find exposed dashboard, upon gaining access to a single container in the cluster they can use the internal networking of the cluster for accessing the dashboard and legitimate browsing to the dashboard using cloud or cluster credentials (note: this attack campaign was first documented here). A simple mitigation for this is to ensure that role-based access control is used on Kubernetes services.
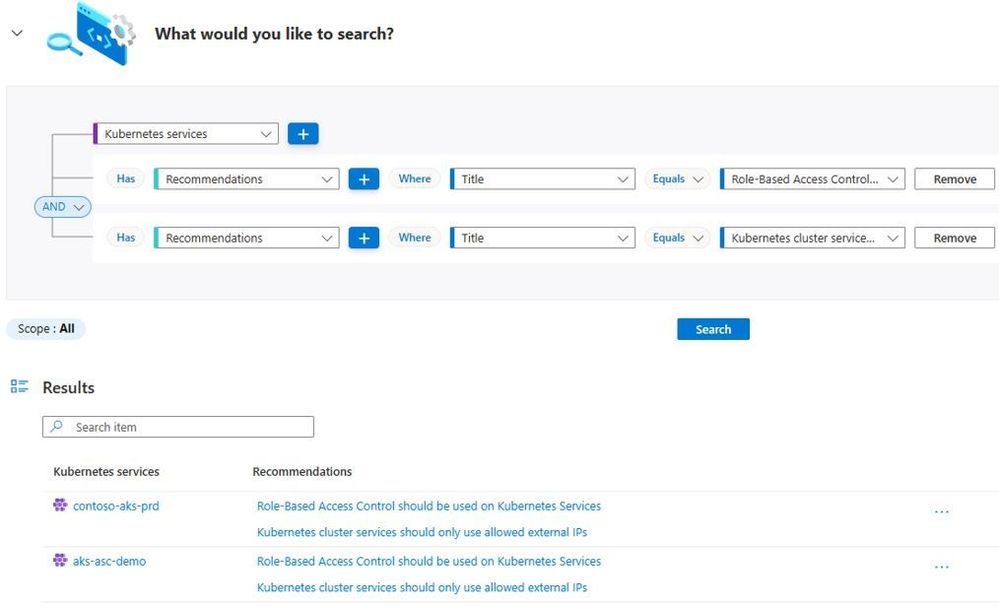
The team member now wants to create a custom search to see if there are Kubernetes services that are not using RBAC and if the external access to those Kubernetes are not hardened via IP Address. To accomplish this in a matter of seconds, the team can use the Cloud Security Explorer, and create a custom search as shown below:
With this custom search the team was able to quickly identify the workloads that could be potentially compromised by this attack campaign. Now they just need to click on the recommendation and remediate.
Conclusion
The threat landscape is continuously evolving, and organizations must prioritize security hygiene to ensure they are decreasing the attack surface of their workloads. To do that, it becomes imperative to use a proactive approach for cloud security posture management, and Microsoft Defender for Cloud brings the capability to do that across a multicloud environment in a fast and comprehensive manner.
Additional Resources
If you are using Attack Path and Cloud Security Explorer and want to share your feedback with the Defender for Cloud Team, please e-mail us directly from here. You can also use the resources below to learn more about these capabilities:
- Cloud security explorer and Attack path analysis (Video)
- Identify and remediate attack paths
- Microsoft Defender for Cloud Security Posture Management
Reviewers
Meital Taran- Gutman, Principal GPM (Defender for Cloud)
Denis Mizetski, Principal PM Lead (Defender for Cloud)
Mekonnen Kassa, Principal GPM (CxE Defender for Cloud)
Thomas Zou, Product Marketing Manager (Defender for Cloud)