This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
This post presents a shared effort which includes
Security orchestration, automation, and response (SOAR) primarily focuses on threat management, security operations automation, and security incident responses. Microsoft Sentinel provides not only a rich set of SOAR capabilities but also, a wide variety of SOAR OOTB (out-of-the-box) content and solutions, to readily integrate Microsoft Sentinel with any product or service in any environment. These solutions include Azure custom logic app connectors aka SOAR connectors, and playbooks that helps with automated incident management, enrichment, investigation and more SOC enablement scenarios adding to our set of automation playbooks announced earlier. We are launching 14 new solutions which adds 14 SOAR connectors and another 25+ playbooks to expand our SOAR capabilities in Multicloud SOAR, Vulnerability enrichment, Incident management, migration, and threat intelligence categories. With this, there are 330+ playbooks available in Microsoft Sentinel content hub either in the 50+ SOAR solutions or as standalone playbooks.
Get Started:
These solutions can be installed on-demand as per use cases from Content hub which currently has a rich set of 250+ solutions and 240+ standalone content. In the search box type the name of the solution, select the needed solution from the list and click install.
New Microsoft Sentinel SOAR Solutions Categories
MultiCloud SOAR
SOAR integration capabilities in this area make it easy to interact with multi-cloud entities form within Microsoft Sentinel. Key new integrations in this space include the following:
AWS IAM
The Amazon Web Services (AWS) Identity and Access Management (IAM) Solution for Microsoft Sentinel allows management of identity resources in AWS via playbooks that uses the AWS IAM API.
SOAR Uses cases supported:
- Add User Tags
- Delete Access Keys
- Enrich incidents
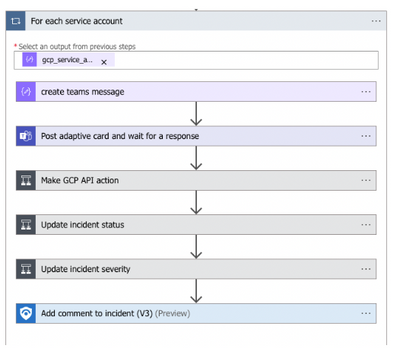
GCP IAM
The Google Cloud Platform Identity and Access Management (IAM) solution provides the capability to ingest GCP IAM logs into Microsoft Sentinel using the GCP Logging API. Refer to GCP Logging API documentation for more information.
SOAR Use cases Supported
- Disable service account
- Disable service account key
- Enrich Service account info
Vulnerability incident enrichment
SOAR integration capabilities in this area not only make it easier to enrich incidents but also to prioritize incidents based on affected asset, perform remediation steps like running vulnerability scans and more
Qualys VM
The Qualys Vulnerability Management solution for Microsoft Sentinel enables ingestion of host vulnerability detection data into Microsoft Sentinel. With the new SOAR playbooks analysts can perform actions like running scans of assets and capturing reports.
SOAR use cases supported
- Get asset details
- Get asset by CVEID (Common Vulnerabilities and Exposures ID)
- Get asset by Open port
- Launch VM (Vulnerability Management) scan
InsightVM Cloud API (Rapid7)
The Rapid7 Insight platform brings together Rapid7’s library of vulnerability research, exploit knowledge, global attacker behavior, Internet-wide scanning data, exposure analytics, and real-time reporting to provide a fully available, scalable, and efficient way to collect your vulnerability data and turn it into answers.
SOAR use cases supported
- Enrich incident with asset info
- Enrich vulnerability info
- Run VM scan
Enrichment and Threat Intelligence
SOAR integration capabilities in this area help analysts to decide if the Incident is True positive or False positive based on the added enrichment and inform remediation steps
OpenCTI
The OpenCTI solution for Microsoft Sentinel enables you to ingest threat intelligence data from OpenCTI platform into Microsoft Sentinel. It not only enriches Microsoft Sentinel incidents but also adds indicators to OpenCTI.
SOAR use cases supported
- Create Indicator
- Enrich incident
- Get Indicator stream
- Import to Sentinel
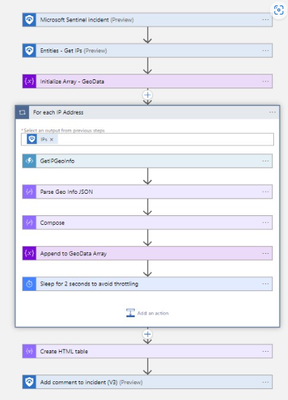
Neustar IP GEO Point
The Neustar IP GeoPoint Solution for Microsoft Sentinel contains playbook which allows easy IP address lookup to enrich Microsoft Sentinel's incident and helps auto remediation scenarios.
SOAR use case supported
- Get IP Geo Info
Checkphish by Bolster
The Bolster’s phishing and scam protection service provides accurate detection and takedown of phishing and scam sites. This sentinel solution contains playbooks which help to identify phishing sites which help analysts' faster investigation by enriching sentinel incident.
SOAR use case supported
- Get URL scan results
Elastic Search
Elastic Search is a distributed, RESTful search and analytics engine capable of addressing a growing number of use cases. As the heart of the Elastic Stack, it centrally stores your data for lightning-fast search, fine‑tuned relevancy, and powerful analytics that scale with ease. This Microsoft Sentinel Solution contains playbooks to help enrich Microsoft Sentinel incidents by querying elastic search on demand or as and when the incident occurs.
SOAR use case supported
- Enrich incident
Minemeld
The Minemeld solution for Microsoft Sentinel has SOAR Connector and Playbooks, which not only enriches the Microsoft Sentinel incident using Minemeld indicators data but also helps to add indicators to Minemeld platform if needed.
SOAR use case supported
- Create indicator
- Enrich incident
AbuseIPDB
The AbuseIPDB solution for Microsoft Sentinel allows you to check the reputation of IP addresses in log data and perform automated actions like enriching a Microsoft Sentinel incident by IP reputation information, add blacklisted IP addresses to Threat Intelligence Indicator table and reporting IPs to Abuse IPDB based on a user response in Teams.
SOAR use case supported
- Enrich incident by IP info
- Report IP to Abuse IP DB
- Deny list to Threat intelligence
URLhaus
The URLhaus solution for Microsoft Sentinel allows enriching incidents with additional information about file hashes, Hostname and URL using feeds and lists from URLhaus.
SOAR use case supported
- Check host and enrich incident
- Check hash and enrich incident
- Check URL and enrich incident
Incident Management
Microsoft Sentinel has incident management capabilities with advanced investigational features to enable SOC workflows. Having integration capabilities in this area helps MS sentinel customers to integrate seamlessly with 3rd party ITSM tools and collaborate across the wider org
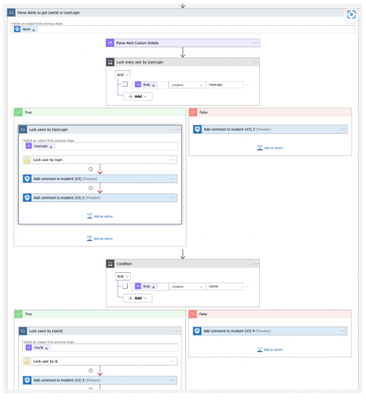
The Hive
TheHive solution provides the capability to ingest common The Hive events into Microsoft Sentinel through Webhooks. The Hive can notify external system of modification events (case creation, alert update, task assignment) in real time. When a change occurs in The Hive, an HTTPS POST request with event information is sent to a callback data connector URL. Refer to Webhooks documentation for more information.
SOAR use case supported
- Create alert
- Create Case
- Lock User
ServiceNow
The ServiceNow solution for Microsoft Sentinel makes it easy to synchronize incidents bidirectionally between Microsoft Sentinel and ServiceNow IT Service Management (ITSM) and Security Incident Response (SIR) systems. More details can be found in the new Microsoft Sentinel – ServiceNow bi-directional sync solution blogpost.
Remediation and response
SOAR integration capabilities in this area help in taking automated remediation actions to block malicious activity on time
Fortinet FortiWeb Cloud
The Fortinet FortiWeb Cloud solution for Microsoft Sentinel provides an automated approach for SecOps analysts to remediate attacks at application level by blocking suspicious IP and URL and empowers to gather threat intelligence data for malicious IP activity
SOAR use case supported
- Block IP / URL
- Incident enrichment
Threatx WAF
The ThreatX solution for Microsoft Sentinel provides an automated approach for analysts to remediate the attacks happening at application level by blocking the suspicious Ip and URL and empowers them to gather the threat intelligence data for the malicious Ip activity.
SOAR use case supported: -
- Block IP / URL
- Incident enrichment
Closing
Try out these Microsoft Sentinel SOAR solutions and share your feedback via any of the channels listed in the resources.