This post has been republished via RSS; it originally appeared at: Intune Customer Success articles.
By: Chris Kunze – Senior Product Manager | Microsoft Intune
Least-Privilege Administrative Models are security best practices where users only have the access, they need to perform a given task. This helps prevent unauthorized or accidental changes, data breaches, and compliance violations. With Microsoft Intune, there are a couple of ways you can achieve least-privilege admin access.
- Create a just-in-time (JIT) policy with Azure AD Privileged Identity Management (PIM) for the Azure Active Directory (Azure AD) built-in “Intune Administrator” role and assign it an administrator account.
- Create a granular permission control with Intune Role Based Access Control (RBAC).
Although these two options provide least-privilege admin access, JIT access with PIM is only applicable to the Azure AD built-in “Intune Administrator” role. With granular permission control using RBAC, you’re able to set up a least-privilege, role-based administrator in Intune but were previously unable to get JIT access control for Intune RBAC, until now. Privileged Identity Management (PIM) for Groups gives admins the ability to provide users with just-in-time membership and ownership of the group. We encourage customers to try it and provide feedback.
Intune just-in-time RBAC access with Azure AD PIM for Groups
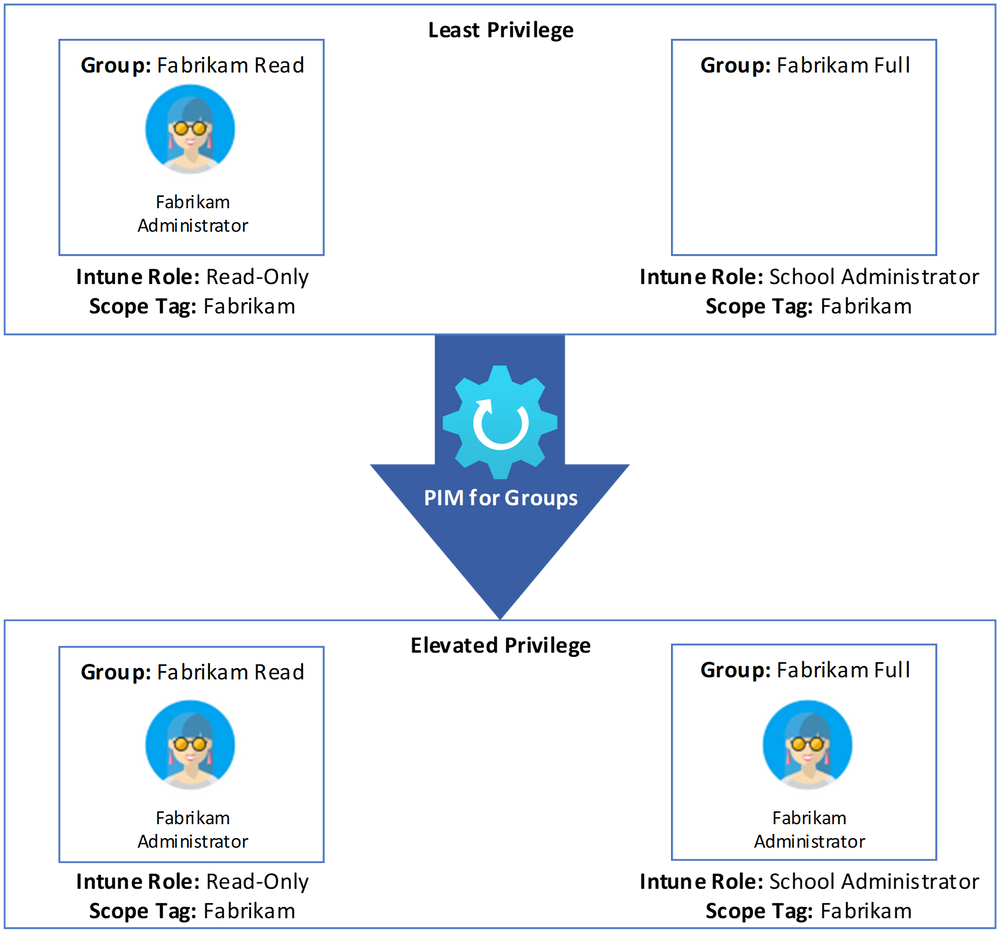
The Least-Privilege Administrative Model for Intune gives users just-in-time privileged access to Intune. This article discusses how to give users just-in-time privileged access to Intune RBAC by using PIM for Groups. In this scenario, administrators will be given minimal (Read-Only) permissions in Intune RBAC and will be assigned elevated access (Full) when needed using PIM for Groups.
For this example, there are : Fabrikam Read and Fabrikam Full. The administrator, Fabrikam Administrator, is a member of the Fabrikam Read group. There are no members in the Fabrikam Full group. The groups will be configured using PIM for Groups so any member of the Fabrikam Read group can be added to the Fabrikam Full group. Finally, the roles will be configured in Intune so that the Fabrikam Read group will have “Read-Only” access and the Fabrikam Full group will have elevated privileges (School Administrator, in this example).
Demo
The following demo shows how to configure Intune JIT admin access, the device configuration experience with least-privilege rights, the process of requesting elevated privilege, and the device configuration experience with elevated privilege.
Step 1: Creating the groups in Intune
To begin, we’ll create the two groups needed for this implementation in the Microsoft Intune admin center (Groups > All groups). For our example, the first group, Fabrikam Read, is a standard group with assigned membership and Fabrikam Administrator has been added as a member to this group. Note that it’s possible to use existing groups if you already have them set up.
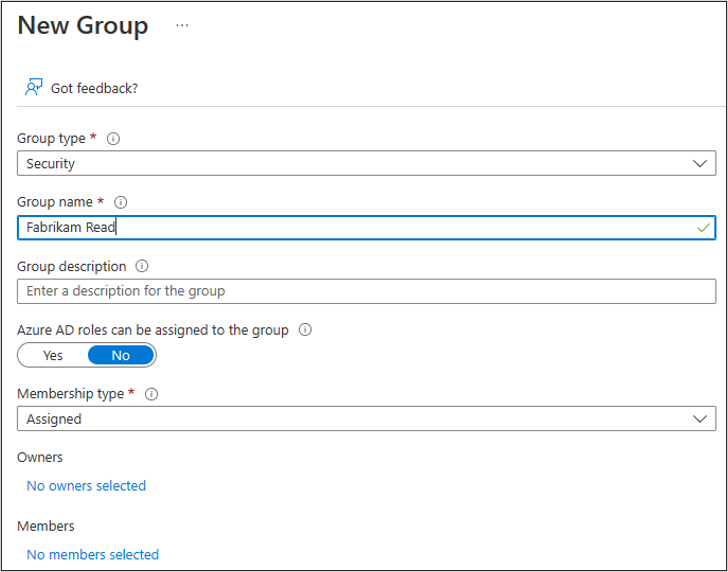
The second group will be the PIM for Groups. For our example, this is the Fabrikam Full group. When creating the PIM for Groups managed group, it can be either role-assignable or non-role-assignable. A role-assignable group is one that can be assigned to a role in Azure AD. Use role-assignable groups so that only the Global Administrator, Privileged Role Administrator, or the group Owner can manage the group to help prevent an admin from elevating to a higher privileged role without going through a request and approval procedure.

A user (Fabrikam Administrator) can be added as a member of the first group (Fabrikam Read). There won’t be members in your second (managed) group (Fabrikam Full).
Step 2: Configure the managed group in Azure AD
To configure the managed group, go to the Microsoft Entra admin center.
- Under Identity Governance, select Privileged Identity Management.
A screenshot of the navigation menu in the Microsoft Entra admin center with the Privileged Identity Management option highlighted.
- On the Privileged Identity Management (PIM) page, select Groups (Preview).
A screenshot of the navigation menu for Privileged Identity Management with the Groups (Preview) option highlighted.
- Select Discover groups.
A screenshot of the Groups (Preview) page in Privileged Identity Management with the Discover groups option highlighted.
- Search for and select the managed group (Fabrikam Full) and then select Manage groups.
A screenshot of the example Fabrikam Full managed group option selected on the Groups – Discovery page and Manage groups option.
- Click OK to onboard the group. The group is now ready to be configured. Select the group, and under Manage, select Assignments.
A screenshot of the example Fabrikam Full group Assignments pane.
- Select Add assignments. For Select role, choose Member and in Select members, choose the first group we created (Fabrikam Read).
A screenshot of the Add assignments pane showing the example Fabrikam Read group selected for the Selected members option.
- For Assignment type, click the Eligible option to require members to perform an action to get added to the group. This assignment will need to be reviewed at least annually.
A screenshot of the Add assignments pane showing the Eligible option selected.
- Once the assignment is created, select Settings to choose how long the group membership will last and how a user can be approved.
A screenshot of the Assignments pane showing the Settings option and the new group (Fabrikam Read) designated as the Member.
- For the member role, specify the Activation maximum duration (hours) and whether authentication is required upon activation.
- Select any or all of the options to require justification, ticket information, or approval upon activation.
For our example, I set the Activation maximum duration to 4 hours and required approval of someone from the PIM Manager Group (group that includes members who can approve the request) to activate. I chose not to require multi-factor authentication (MFA) or Azure AD Conditional Access authentication context, which would’ve required the membership being activated only from an organization-owned device or other Conditional Access policies.

Specify any settings in the Assignment and Notification tabs, as needed. For our example, I chose to leave the defaults selected.

Step 3: Assign Roles in Intune
Now that the member is set up in Azure AD, we need to configure settings in Intune.
- In the Intune admin center, navigate to Tenant administration > Roles.
- Select the desired least privilege role. In this example, I chose Read Only Operator.
- In the Role, go to Assignments and assign the first group we created and then add the scope tag on their respective tabs on the page. In our example, this would be the Fabrikam Read group and Fabrikam scope tag.
- Be sure not to select the managed (Fabrikam Full) group.
- Click Save once you verify the assignment settings on the Review + create tab.

Following the same process, I assigned the role School Administrator to the managed Fabrikam Full group.
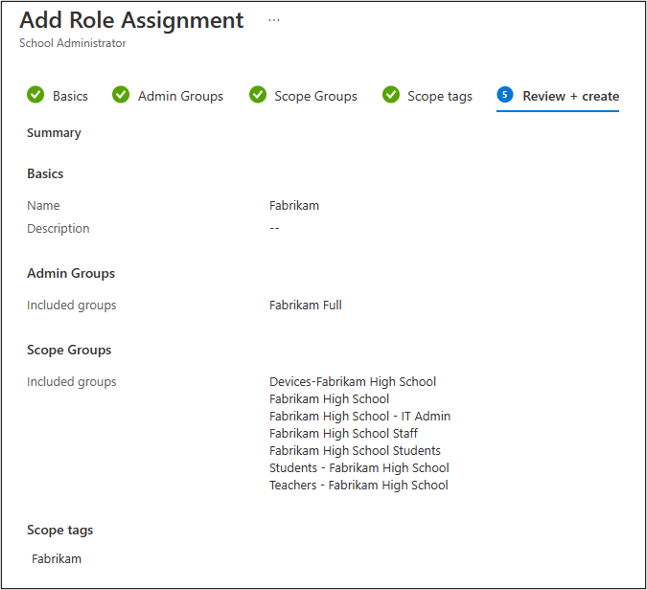
After the role assignment settings are completed, the members of the least-privilege group (Fabrikam Read group) will be able to request elevated privileges by requesting to be temporarily added to the managed group (Fabrikam Full group). If the administrator does not explicitly cancel the request, the changes will be reverted after the established maximum duration hours (4 hours in this example).
Conclusion
Hopefully this walkthrough and demonstration on how to use JIT policy with Azure AD Privileged Identity Management (PIM) for Groups feature helps you create your own administrator role that has just-in-time privileged access to Intune.
If you have any questions, please let us know in the comments or reach out to us on Twitter @IntuneSuppTeam.
