This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Before we start, please not that if you want to see a table of contents for all the sections of this blog and their various Purview topics, you can locate the in the following link:
Microsoft Purview- Paint By Numbers Series (Part 0) - Overview - Microsoft Tech Community
Disclaimer
This document is not meant to replace any official documentation, including those found at docs.microsoft.com. Those documents are continually updated and maintained by Microsoft Corporation. If there is a discrepancy between this document and what you find in the Compliance User Interface (UI) or inside of a reference in docs.microsoft.com, you should always defer to that official documentation and contact your Microsoft Account team as needed. Links to the docs.microsoft.com data will be referenced both in the document steps as well as in the appendix.
All of the following steps should be done with test data, and where possible, testing should be performed in a test environment. Testing should never be performed against production data.
Target Audience
The Information Protection section of this blog series is aimed at Security and Compliance officers who need to properly label data, encrypt it where needed.
Document Scope
This document is meant to guide an administrator who is “net new” to Microsoft E5 Compliance through.
We will be covering the auto-labeling of data at rest.
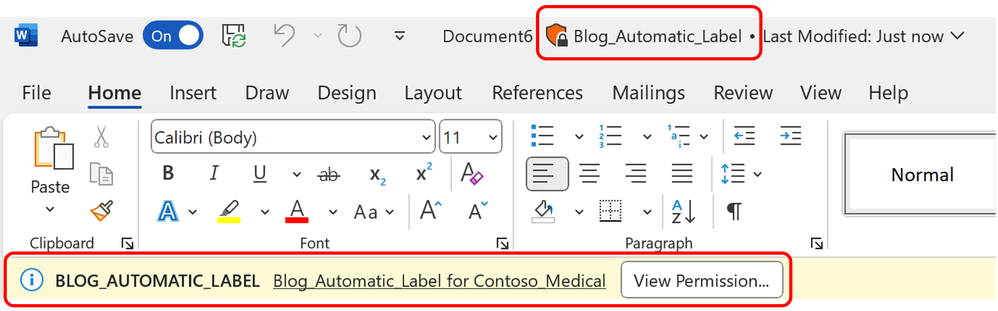
It is presumed that you already have a Sensitive Information Type that you want to use in your Information Protection policy. For the purposes of this document, I will be using a previously created Data Classification called “Automatic_Label_Contoso_medical”. The keyword I am tracking within that data classifier is “Contoso_medical”. I am doing this to avoid labeling any files by accident by using an out-of-the-box classifier. For information on how you create your own data classifier, refer back to “Part 1 – Sensitivity Information Types” of this blog series.
This document is only meant to be an introduction to the topic of multiple Sensitivity labels. Always refer back to official Microsoft documentation or your Microsoft account team for the latest information.
Out-of-Scope
This document does not cover any other aspect of Microsoft E5 Purview, including:
- Data Classification
- Data Protection Loss (DLP) for Exchange, OneDrive, Devices
- Data Lifecycle Management (retention and disposal)
- Records Management (retention and disposal)
- eDiscovery
- Insider Risk Management (IRM)
- Priva
- Advanced Audit
- Microsoft Cloud App Security (MCAS)
- Information Barriers
- Communications Compliance
- Licensing
It is presumed that you have a pre-existing of understanding of what Microsoft E5 Compliance does and how to navigate the User Interface (UI).
For details on licensing (ie. which components and functions of Purview are in E3 vs E5) you will need to contact your Microsoft Security Specialist, Account Manager, or certified partner.
Overview of Document
- Create a Sensitivity Label
- Verify automatic policy is published
- Publish your automatic Sensitivity labeling policy
- Changing between Simulation and “Enabled” mode
- Reporting on simulations of label application
- Test the Sensitivity Label is applied to existing files
- Test the Sensitivity Label is applied to existing emails
Use Case
- Applying Sensitivity labels to data at rest in OneDrive, SharePoint sites, Teams Sites, and Exchange mailboxes.
Definitions
- Sensitivity Label – a metadata tag
- Publish Label – making the metadata tag available to your tenant
- Policy – The monitoring and applying of Sensitivity labels through the Microsoft tenant
Notes
- Remember it can take 24-48 hours for a new Sensitive Information Type (SIT) to start to be found in your tenant. So create your SIT ahead of time and place it in Exchange mails and SharePoint/Teams sites, and OneDrive for your testing.
- Types of labels:
- Automatic labels are applied to data at rest.
- Default labels are applied to data upon creation (and based on what is in the file/email).
- Recommended labels do not label data, but appear when a specific piece of Sensitive Information Type (ex. Contoso_Medical) are added to a file/email. It is up to the user to apply or not apply the recommended label.
.
- Here are some very important things to note about Simulation vs “Enabled” automatic labeling policies.
- Automatic labeling policies should be thoroughly tested in your dev tenant and you should work with your data security team (or equivalent) should be consulted when using labels, especially automatic labeling.
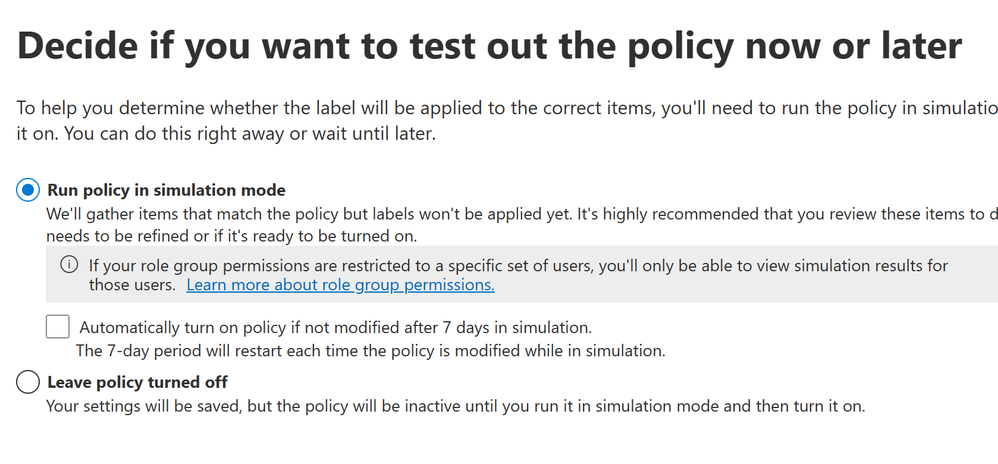
- Here is a screenshot of the enablement mode (simulation, off, on) that will be referred to several times in this blog.
- When in doubt, run the default of Run policy in simulation mode.
- If you want to apply a label in your dev tenant, you will need to check the box next to Automatically turn on policy if not modified after 7 days in simulation. I recommend you only do this in a dev tenant and after much consideration.
- If you want to do this in production, I recommend:
- you consult with your Microsoft support team or certified Microsoft partner be certain know you have thoroughly defined your relevant a) data classification, b) taxonomy, and c) ramifications of applying sensitivity labels to your production data.
- For this blog, I will be enabling automatic labeling so I can demonstrate labels being applied to files and emails in my demonstration tenant.
Pre-requisites
- You have read Parts 0, 1 and 2 of this blog series
- You have a Sensitive Information Type (SIT) that will be tied to this automatic label.
- Populate emails and files with your test information several days before you create your policies. In my environment, I am testing with the phrase “Contoso_Medical”. This will be important during the simulation and testing done later in this blog.
Part 1 – Create an automatic Sensitivity label
We will first set up our automatic label.
- Give the label a name and description (and color marker, if you wish). Then click Next.
- For the Scope, select Items and be sure that Files and Emails are selected. Then click Next.
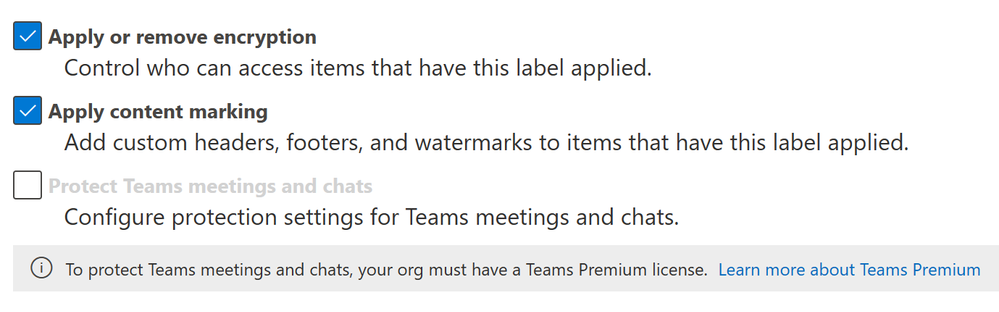
- Under the Items section of the wizard, select Apply or remove encryption and Apply content marking, then click Next.
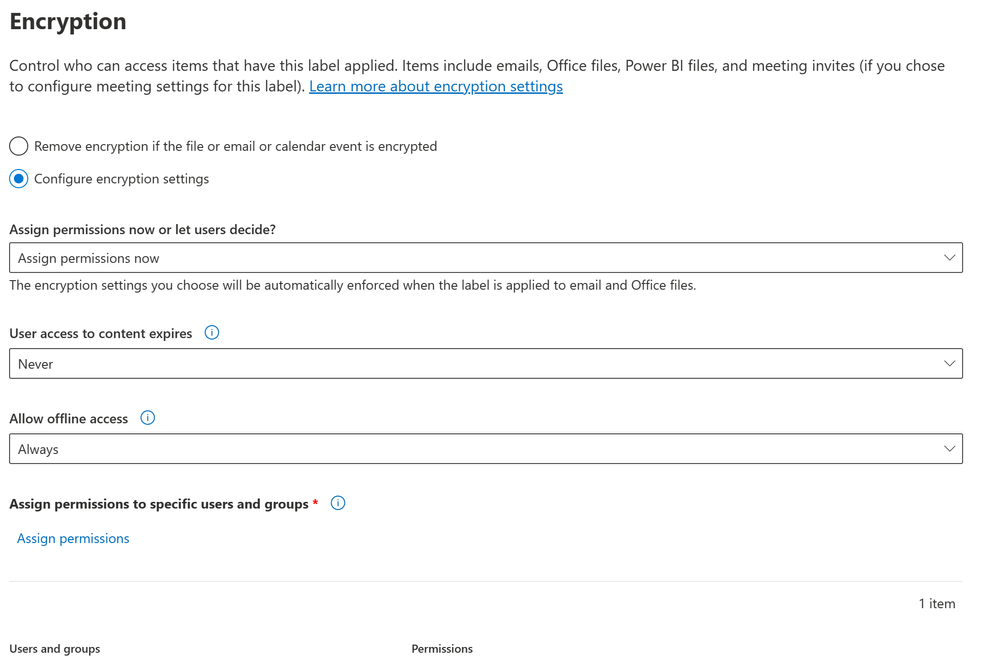
- We now arrive at Encryption. Click Configure encryption settings.
- Under Assign Permissions now or let users decide? and chose Assign permissions now. Leave the rest of the settings at the default.
- under In Assign permissions to specific users and groups, click Assign permissions. For the purpose of this blog, I will click Add all users and groups in your organization, click Save.
- Click for Apply content watermarking, I like to use the header option as it is the easiest because it is at the top of each electronic page.
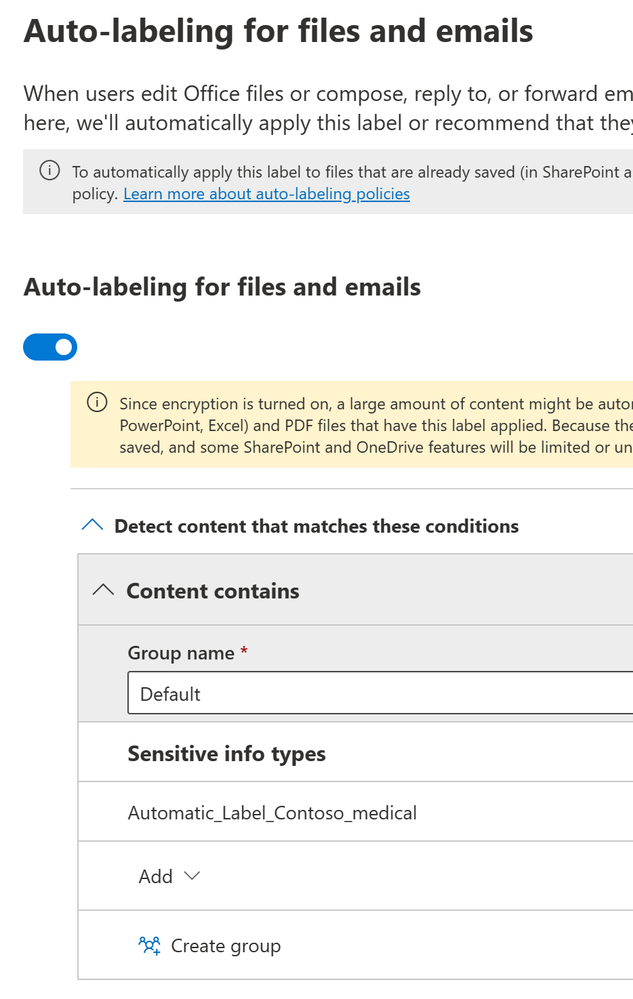
- Next, we will Enable auto-labeling for files and emails.
- At the top of this page, for the Content contains, we will select the SIT that we created previously. In my case, I am using the “Recommended_Label_Contoso_medical”. The keyword I am tracking within that data classifier is “Contoso_medical”.
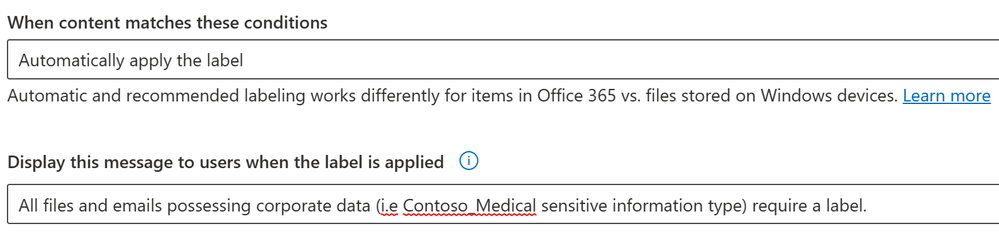
- At the bottom of this page, for the When content matches these conditions select Automatically apply the label.
- Note – this is the proverbial switch that needs to be flipped for a label to enable Recommend vs. Automatic vs Default labels.
- We also want to provide an explanation in Word, Excel, etc. for the users. So in the field Display this message to users when the label is applied, type the message you want your user to see when the label is recommended. Then click Next.
- On the protection settings for Groups and Sites, we will not be enabling anything as they are not applicable for this label and policy. Accept the defaults and click Next.
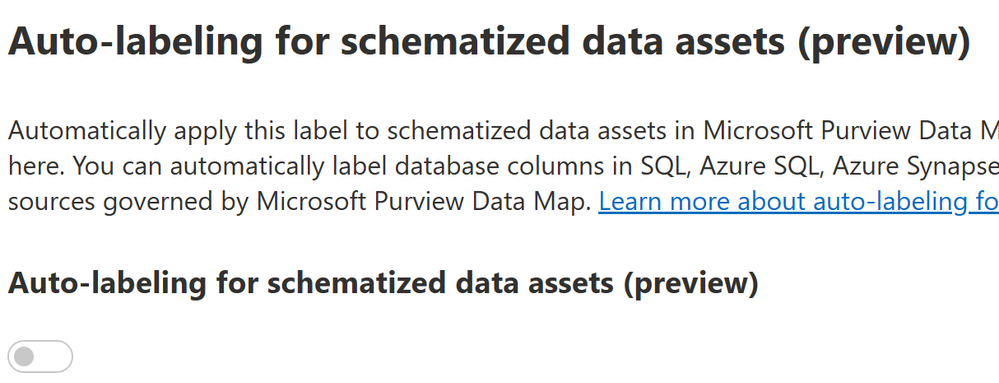
- On the schematized data assets, we will leave this at the default of Off. Click Next.
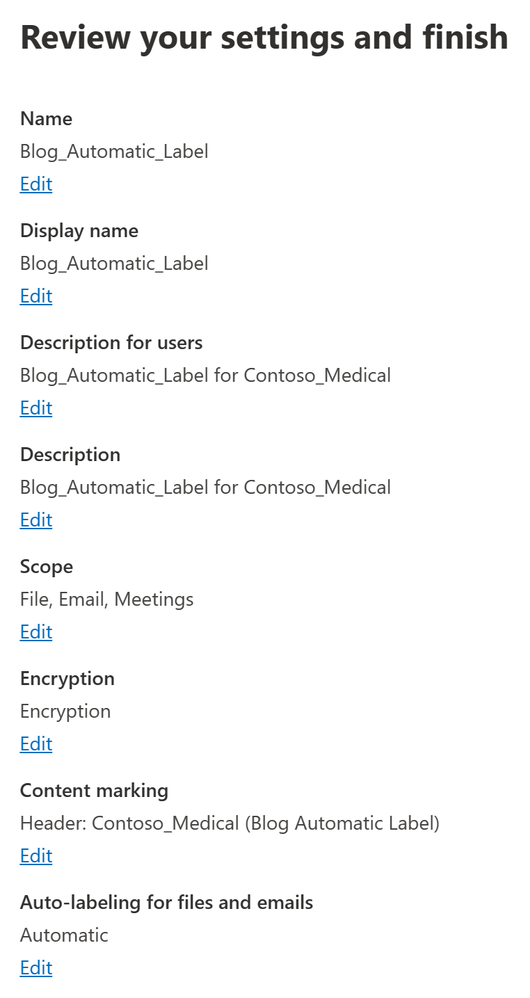
- Review your label and click Create Label.
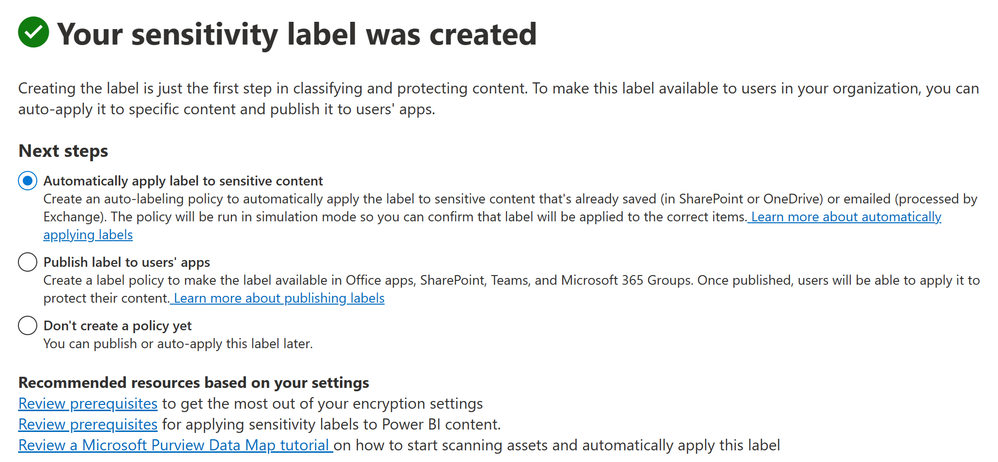
- Under Next steps, select Automatically apply label to sensitive content.
- Note – If you select Publish label to user’s apps, you’ll have to follow the steps in the “Publish your automatic label” section below.
- Click Done and then Create Policy and then Close.
Part 2 – Verify Automatic policy is published
If at the “Create your automatic label section above”, you clicked, Automatically apply label to sensitive content, proceed to the test label on new file/email sections below.
If you did NOT click Automatically apply label to sensitive content above, then go to the “Publish your automatic policy” section below.
If you are not sure, if you policy was created, you can find that out by doing the following.
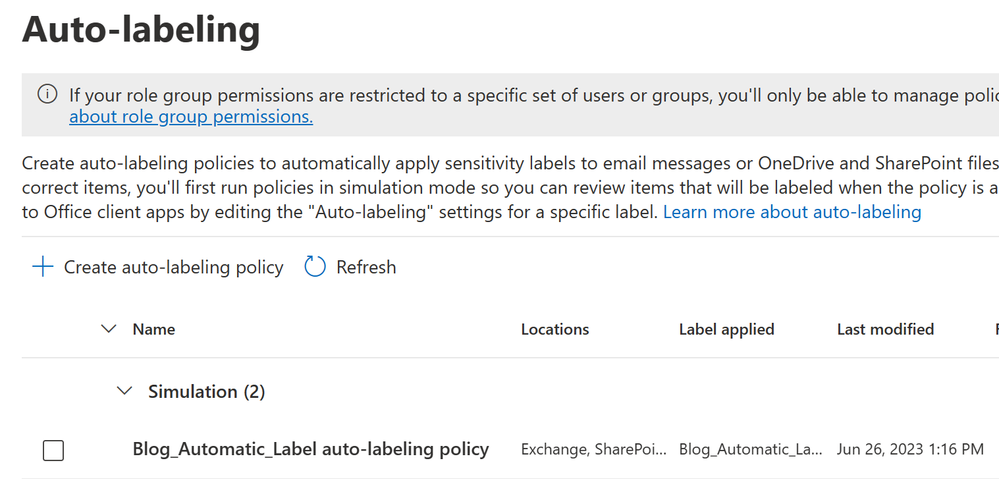
- Go to Information Protection –> Auto-labeling.
- Under Simulation, you should find the policy created on the last step of creating your label.
Part 3 – Publish your automatic Sensitivity label (if needed)
If needed, you can set up your automated labeling policy. You do this by doing the following:
- Go to Information Protection –> Auto-labeling.
- Click Create auto-labeling policy.
- On the first step of the wizard, select Custom -> Custom policy. Then click Next.
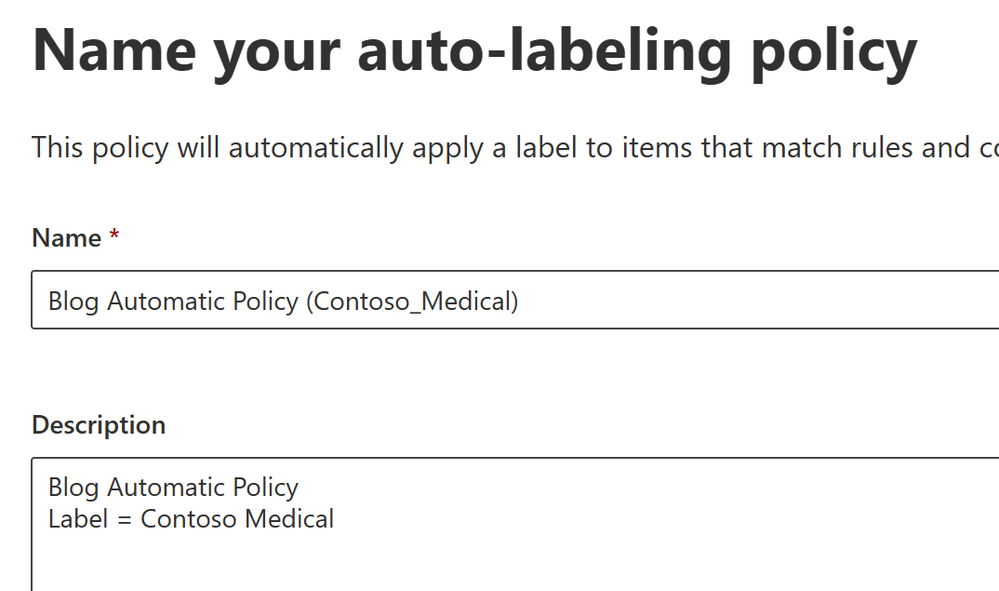
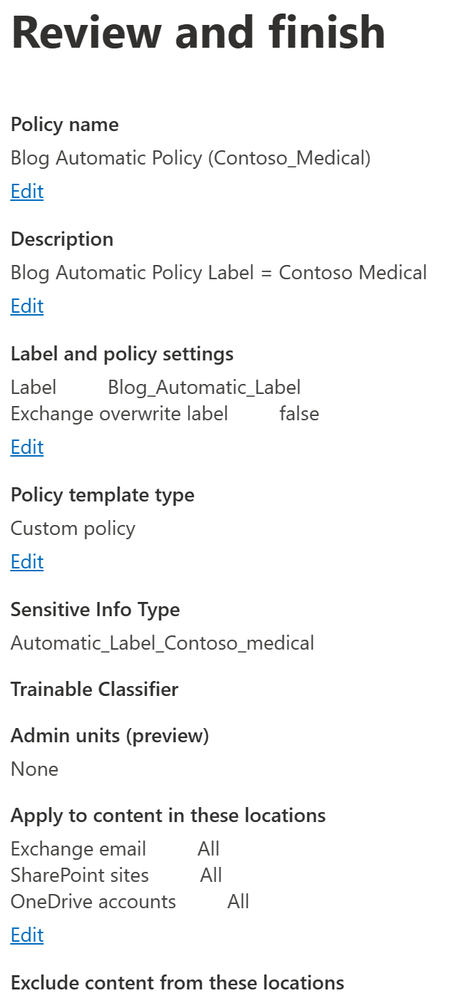
- Give the policy and name and click Next.
- In the next step of the wizard, you can assign a specific administrative team to manage this policy. We will not be doing that in this blog. Click Next.
- Next, choose the locations and where this automatic policy will be applied. These locations include Exchange (for users or groups), SharePoint (and Teams) sites, and OneDrive (for users or groups). As I am in a test tenant, I will accept the defaults. I recommend you narrow your locations to a test user(s) or SharePoint sites for your initial testing.
- For the next step, I will accept the Common rules. Feel free to explore the advanced rules on your own. Click Next
- Now we will create a rule with to go with our automatic label above. Click New rule.
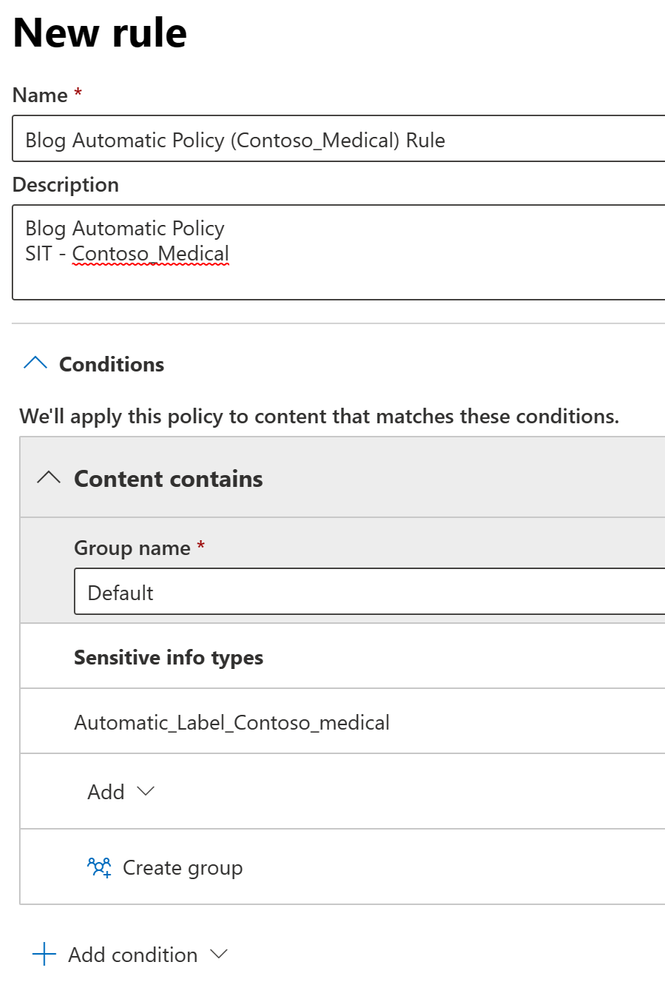
- Give your rule a name, description, and add a condition. I’ll be using the Sensitive Information Type I created previously (Automatic_Label_Contoso_Medical). When you are ready, click Save and then click Next.
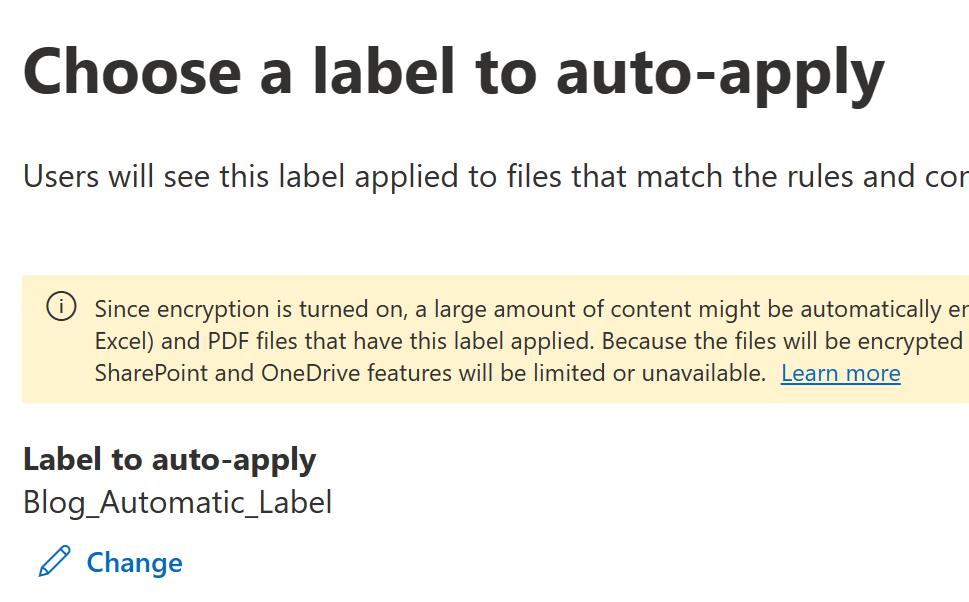
- Next, choose a label to be applied. To do this, click a Choose a label, chose a label and click Save.
- When you are satisfied, click Next.
- Under additional settings, accept the defaults and click Next.
- The next step is to either turn on or off the policy. I will leave the default of Run policy in simulation mode. When you are ready click Next.
- Review your automatic policy and click Create policy and then click Done.
- You are now ready to move to the testing phase of this blog.
Part 4 – Changing between Simulation mode &. “Enabled” mode
Do the following to change from simulation mode to “enabled” mode or vice versa.
- Go to Information Protection –> Auto-labeling.
- Under Simulation, you should find the policy created on the last step of creating your label.
- Select the Edit policy.
- In the wizard, go to Policy Mode (on the left).
- When you are ready click Next.
- When you have made the change you want, click Next, review your automatic policy and click Create policy and then click Done.
Part 5 –Reporting on simulations of automatic labeling
To know what files/emails would be labeled if your automatic labeling policy had actually run, you will need to go to the following location.
Note – Remember that it can take several days for your tenant to start reporting back on existing data matching your policy. This is due to back data processing and indexing that we will not discuss at this time.
- Go to Information Protection –> Auto-labeling.
- Under Simulation, you should find the policy created above. Open your policy.
- At the bottom of the policy, you will see results for files and emails that will match your policy.
Note #1 – You should pre-populate your test SharePoint sites, OneDrive sites with data that possess your SIT data (ex. “constoso_medical”).
Note #2 – For emails, you need to send those after your policy is created for them to be seen by your automatic labeling policy.
- Before we can apply our “test” automated labels against the data in our tenant, we have to enable our policy. Do this by clicking Turn on policy as seen in the screenshot above.
- Now move to the next section.
Part 6 –Test label on new file
Before we start our file and email tests, remember that labels and policies can take a while to replicate throughout your tenant. One hour is usually a good amount of time to wait, but it might be quicker or slower to populate based on several variables in your tenant we will not cover at this time. With that understanding, let us move on to our testing.
- Because Automatic labeling takes place on cloud work loads at this point in time (not on endpoint devices), we will do our testing against a file(s) created on a OneDrive or SharePoint Site (related to your test locations mentioned above ins Part 3).
- Create a new Word, Excel or PowerPoint document. I will create a Word document.
- Type in the Sensitive Information Type that you have associated with your recommended Sensitivity label (I am using the compound word “contoso_medical”) and save your file.
- Wait a few minutes for the automatic labeling to run on the backend in the cloud.
- Reopen the file in your browser. At the bottom you should see your label next to a padlock icon.
- If you then open that file in your local version of word, you will see the label information marked in 2 locations.
- This is the end of the file testing.
Part 7 –Test label on new email
We will now test this automatic label against a newly created email.
- Open Outlook.
- Create a New Email.
- Type in the Sensitive Information Type that you have associated with your recommended Sensitivity label (I am using the compound word “contoso_medical”) and send it to/from your test user (See my example email below).
- Note – If you have a default label configured like I do, you might see that on the left of your From/To/CC/BCC fields. As this is the easiest way to see a change in your label, let us look at an example.
- Once you receive the email, you should see something similar the following in your Inbox/email Preview panel (or when you open your email).
- This is the end of the email testing.
Appendix and Links
Note: This solution is a sample and may be used with Microsoft Compliance tools for dissemination of reference information only. This solution is not intended or made available for use as a replacement for professional and individualized technical advice from Microsoft or a Microsoft certified partner when it comes to the implementation of a compliance and/or advanced eDiscovery solution and no license or right is granted by Microsoft to use this solution for such purposes. This solution is not designed or intended to be a substitute for professional technical advice from Microsoft or a Microsoft certified partner when it comes to the design or implementation of a compliance and/or advanced eDiscovery solution and should not be used as such. Customer bears the sole risk and responsibility for any use. Microsoft does not warrant that the solution or any materials provided in connection therewith will be sufficient for any business purposes or meet the business requirements of any person or organization.