This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Microsoft Defender Threat Intelligence (Defender TI) helps streamline security analyst triage, incident response, threat hunting, and vulnerability management workflows, aggregating and enriching critical threat information in an easy-to-use interface. At Microsoft Secure, we announced new features, including that Defender TI is now available to licensed customers within the Microsoft 365 Defender (M365 Defender) portal, placing its powerful threat intelligence side-by-side with the advanced XDR functionality of M365 Defender.
For Defender users, Defender TI will now be quickly accessible and easy to reference for swift context about threat actors and their tools and to launch advanced investigations into external threat infrastructure. Licensed users will see the following:
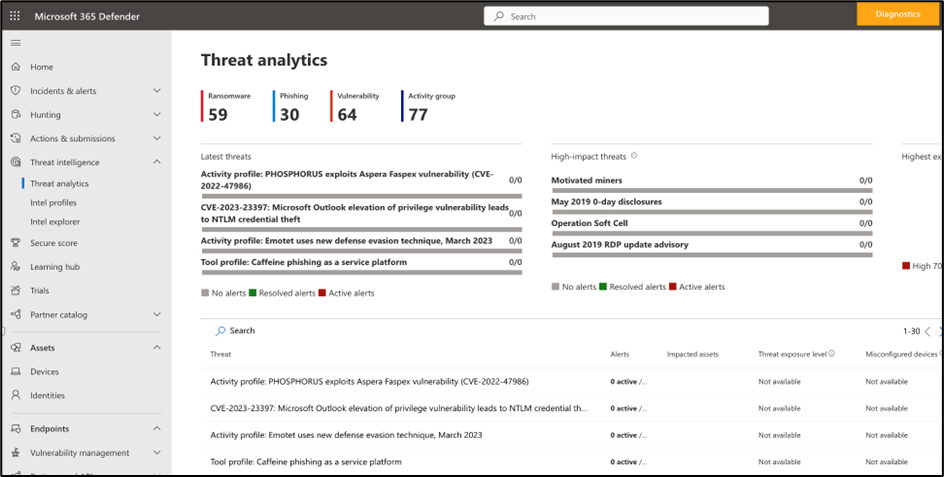
- Threat intelligence navigation blade tab: This new tab, along with threat analytics, has moved under threat intelligence navigation.
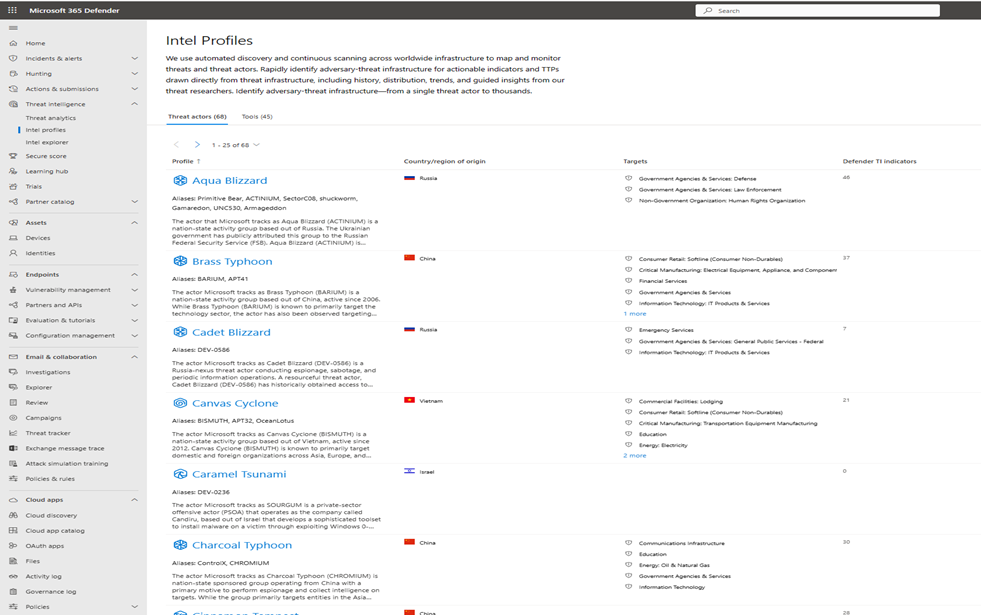
- Intel Profiles: These showcase everything Microsoft knows about threat actors. These include Indicators of Compromise (IOCs) and their tools, tactics, and procedures (TTPs).
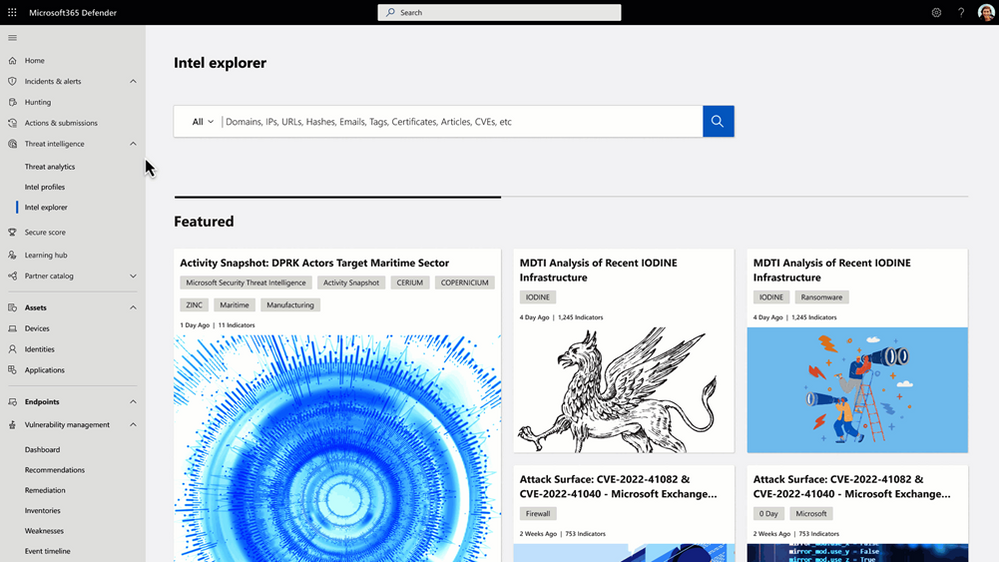
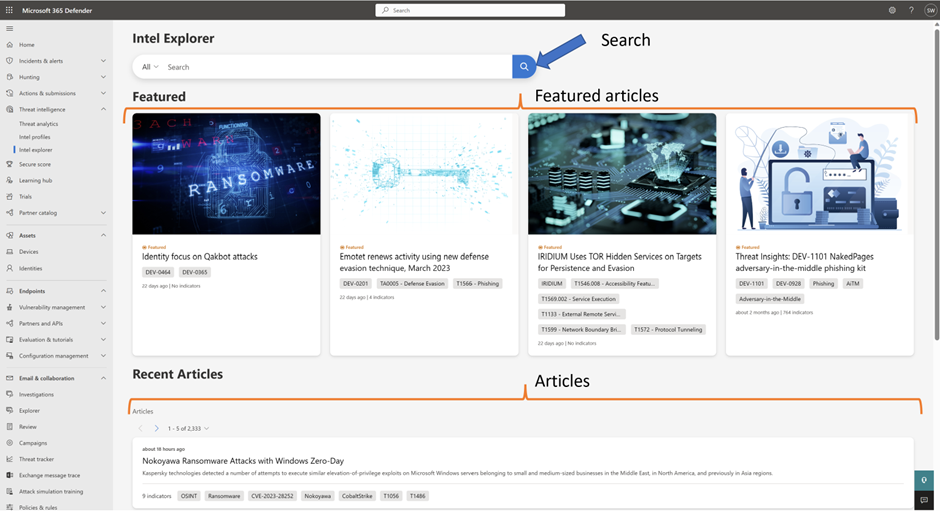
- Intel Explorer tab: This new tab enables pivots on Internet data to launch advanced investigations across Microsoft's continuously updated map of the entire Internet.
Figure: Microsoft Defender Threat intelligence is now available to license customers within the Microsoft Defender 365 portal
Users will note that the experience between the Defender TI standalone portal will differ slightly from what they see in M365 Defender. Namely, they will not see the ability to apply custom tags or project capabilities. Below, I will outline the main features that Defender TI users will see in M365 Defender.
New Threat Intelligence Navigation
Within the new Navigation Menu, users will get visibility of the Defender portal on the Threat intelligence blade. Once selected, they will be presented with the three key options: Threat analytics, Intel Profiles, and Intel Explorer (Defender TI Homepage).
Figure: New Threat Intelligence Navigation
Intel profiles
This section contains a list of approved Threat Actors and Tools identified and tracked by Microsoft. Security professionals can use Microsoft's Intel Profiles, indicators, and other associated markers to automate the defense of their organizations and track potentially malicious activity targeting their organization or industry. Intel profiles consist of two subgroups, Threat Profiles (including tracked dev-groups) and Tool profiles.
Figure Intel profiles on M365 Defender
Intel Explorer tab
Defenders can use the new Intel Explorer tab to learn about new security topics in the form of articles or research open-source intelligence:
- Homepage: This is the beginning; think of it as your home base.
- Search: This is the gateway to the vast amount of Microsoft security data available, which you can turn into intelligence.
- Featured Articles: These are key research publications that we find relevant based on our intelligence expertise. They're often shown with an image.
- Articles: These ensure every customer has data to hunt across all verticals and topics.
Figure: The New Intel explorer Tab for MDTI on M365 Defender
Use Cases
The following are practical threat-hunting and investigation use cases for defenders using Defender TI within M365D.
Use Case: Advanced hunting with Defender TI IOCs against the logs and Events within Microsoft 365 Defender
To demonstrate this scenario, we will compare identified IOCs from Defender TI, specifically the Host Pairs data set related to the widely recognized Phish kit named "Franken-phish" (Franken-phish: TodayZoo built from other phishing kits), and map this information to an advanced hunting query within M365 Defender. This approach can be replicated using IOCs from articles or Intel Profiles of threat actors and their associated tools. We have provided sample queries to aid in your hunting process, which can be found here:
In regard to the following use case, we shall proceed with 3 phases of action:
1. Identify the Dancevida Phish kit Host Pairs and Resolution information and download the IOC.
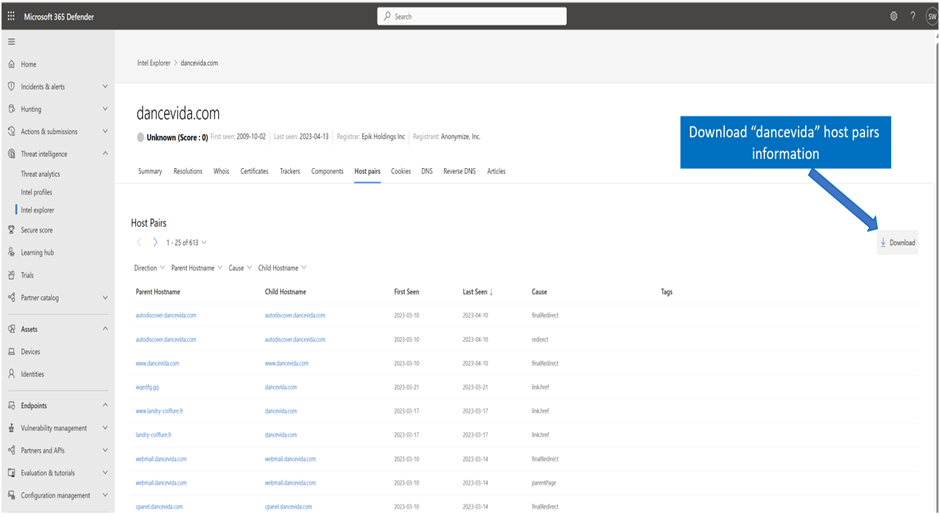
Proceed to the Intel Explorer blade and type in, and search 'Dancevida.com.' After the results appear, navigate to the Host Pairs tab and download the Host Pair information, which will generate a CSV file.
Figure: Downloading Dancevida.com host pair information
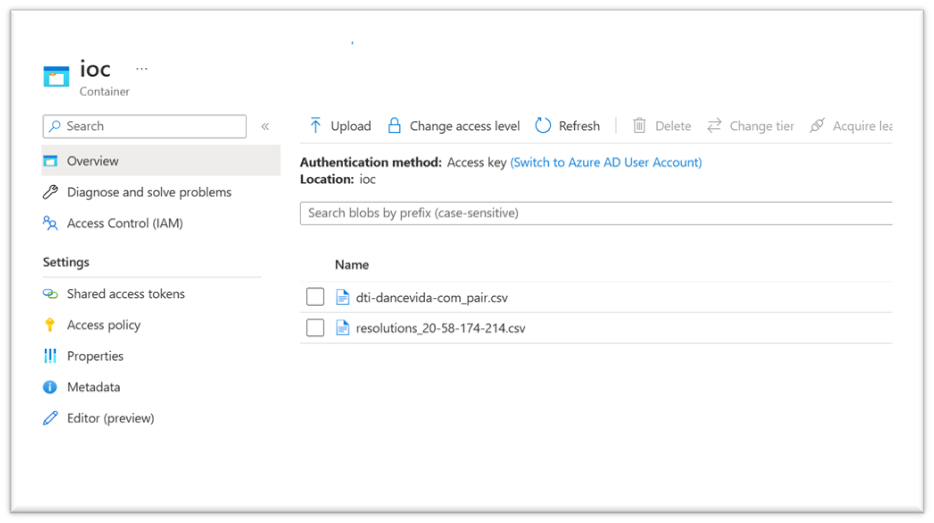
2. Upload IOC to a storage account\public GitHub
The Defender TI CSV file that has been exported must be uploaded to an Azure storage container that has a SAS URL token enabled. The SAS-generated access is only valid for a specific time period, which should be utilized for the advanced hunting process. After obtaining the URL access, the exported Defender TI data can be utilized in the advanced hunting feature within M365 Defender.
Figure: Uploaded Dancevida.com Host pairs Csv to Azure storage to generate SAS token
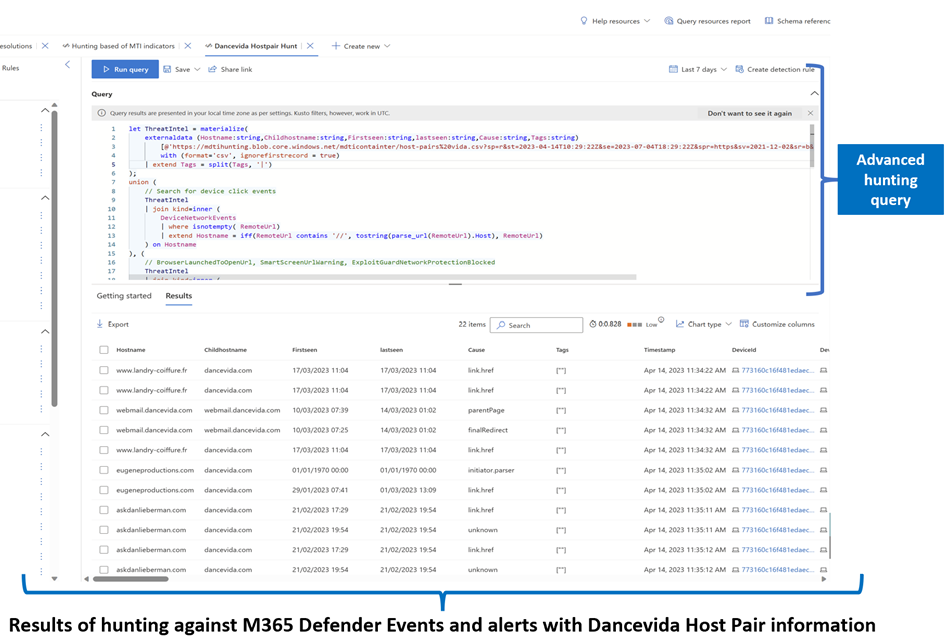
3. Using KQL Externaldata operator as correlation source and proactive hunting and enabling custom detection on M365 Defender (The following Query can be found in the Defender TI GitHub here)
We have four Kusto queries created for you to use as examples.
Kusto queries link: MDTI-Solutions/M365 Advance hunting queries at master · Azure/MDTI-Solutions (github.com)
|
DTI email based events: |
DTI device based events: |
DTI DNS queries from domain controller: |
DTI device based events for resolutions |
|
E-mails with URL embedded.
|
Search for device click events BrowserLaunchedToOpenUrl SmartScreenUrlWarning ExploitGuardNetworkProtectionBlocked Mark of the Web Referrer Mark of the Web DNS queries |
DNS queries
|
Search for device click events BrowserLaunchedToOpenUrl SmartScreenUrlWarning ExploitGuardNetworkProtectionBlocked Mark of the Web Referrer Mark of the Web DNS queries |
Users will need to modify these queries with the columns in the exported CSV file. Host Pairs was exported, but if you export any other data set, the column header will be different.
Figure: Advanced Hunting against M365 Defender events and alerts with DanceVida Host Pair information
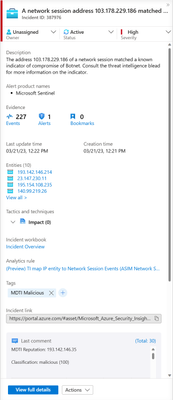
Once we executed the hunting query on M365 Defender, we noticed a correlation between the events data sourced from a device managed by M365 Defender and the exported Dancevida host pair information.
Use Case: M365 Defender Raw Event Detection
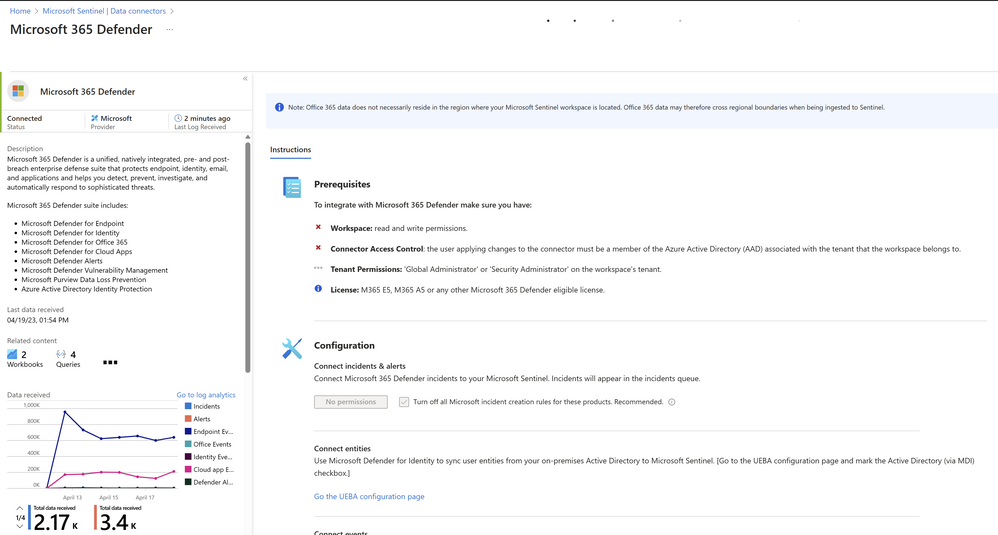
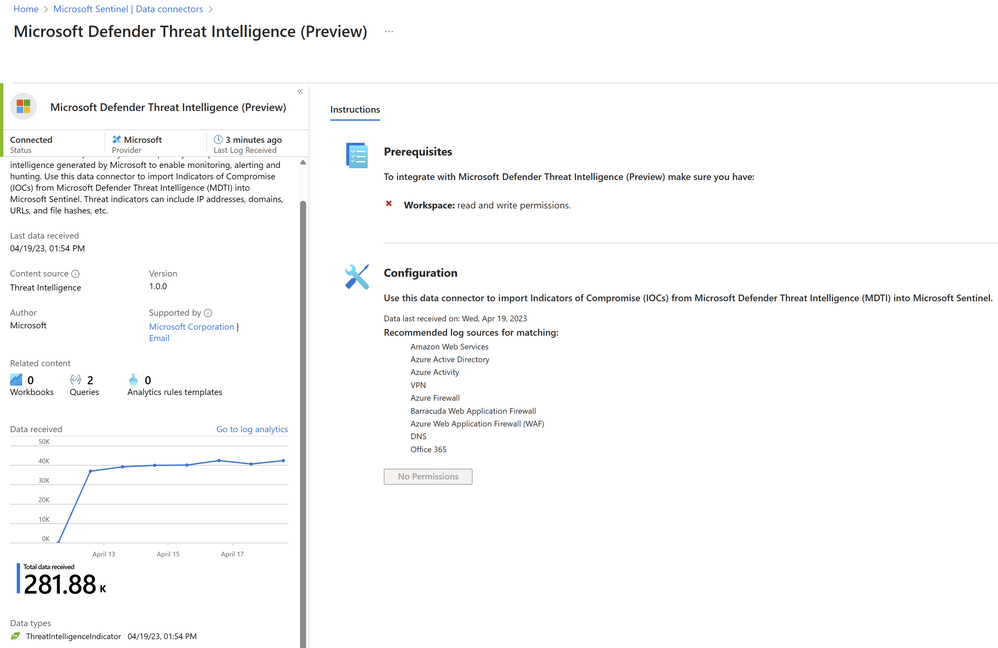
To demonstrate this use case, it is necessary to ingest M365 Defender raw events into Microsoft Sentinel through the M365 Defender Data connector. Furthermore, the user must also import Threat indicators from Defender TI by utilizing the new Defender TI Sentinel Data Connector. Following this, the user needs to execute TI correlation rules, which will compare the raw event tables of M365 Defender. Upon detecting a correlation, an incident will be generated in Microsoft Sentinel, which will incorporate the M365 Defender events and alerts. Let us go through these steps one by one:
1. M365D Raw events flow into Sentinel with the M365 Defender Data connector:
2. MDTI Feeds flow into Sentinel with MDTI Data connector:
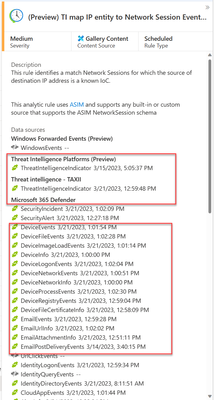
3. Manual TI correlation rule
On the Analytics page on Microsoft Sentinel, use the following rule "TI map entity to a network session event "to map the M365 Defender raw events with the Threat intelligence indicator table. Create and enable the rule:
Figure: TI mapping rule for M365 Events and Incident created in sentinel.
Sign Up for a Trial
- You can sign up for an MDTI Premium license trial here
- You can sign up for an MDTI API License trial here
MDTI Support
For any support-related issues regarding Microsoft Defender for Intelligence, please access this portal and select Security -> Microsoft Defender for Intelligence.
We Want to Hear from You!
Be sure to join our fast-growing community of security pros and experts to provide product feedback and suggestions and start conversations about how Defender TI is helping your team stay on top of threats. With an open dialogue, we can create a safer internet together. Learn more about Defender TI and try it today.