This post has been republished via RSS; it originally appeared at: Microsoft Search Blog articles.
Introduction
Have you ever needed a way to allow some users to access Microsoft Search in Bing, while excluding others? Perhaps you want to exclude users who haven’t yet taken an orientation session, or perhaps you want to roll out this feature in stages. Well, you’re in luck! In this article, you’ll learn how to do exactly that, using a feature known as Conditional Access. With it, you can easily deploy Microsoft Search in Bing to any set of users you choose.
Assuming that you have administrative permissions and a licensing option that enables Conditional Access to Microsoft Search, here’s how to use it to limit access to Microsoft Search in Bing to a specific subset of users. If you haven’t done this before, now is a good time to review best practices for conditional access to ensure that you don’t accidentally lock yourself out.
Verify Access
You should start by assigning a test user. Once you have a test account prepared, the first step is to verify that the test account can access Microsoft Search in Bing.
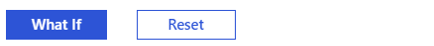
Open your browser and sign in with your test account to bing.com using the “Work or school account” option.
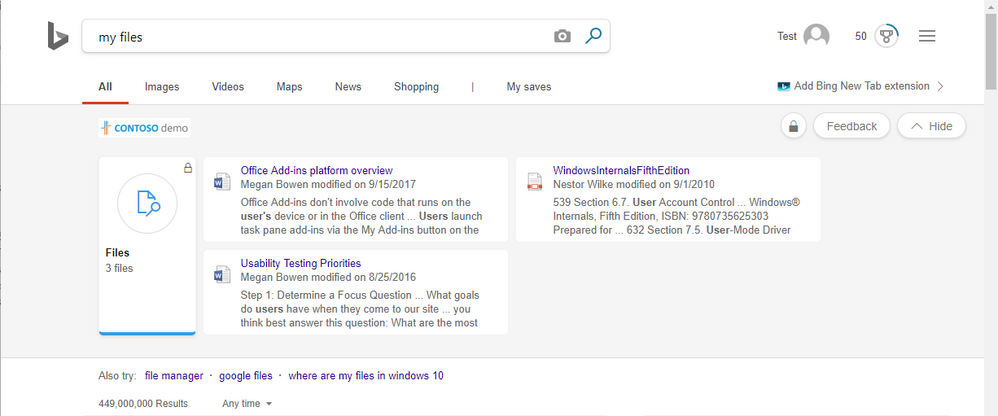
Type “my files” into the Bing search box to verify that Microsoft Search in Bing is working. You should see a result that looks something like this:
Success! You now know your test account can access Microsoft Search in Bing. Now, let’s exclude this account via Conditional Access.
Enable Conditional Access
Start by signing into the AAD admin center as a global admin, via the Microsoft Search in Bing - Getting Started From the Security menu, choose Conditional Access.
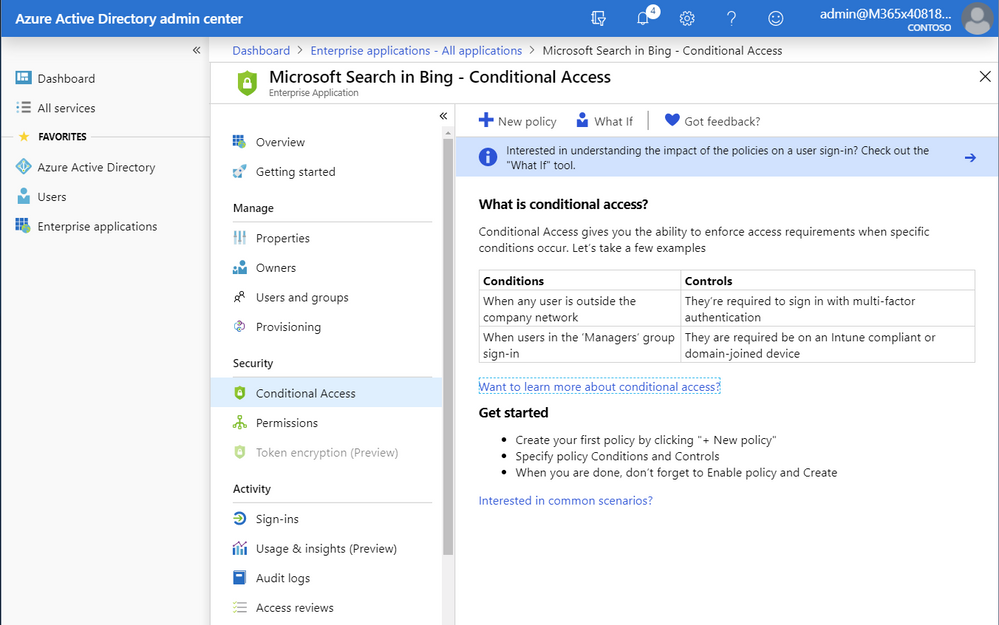
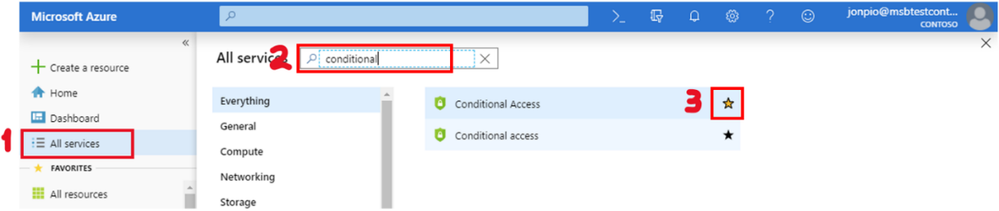
Tip: You can place Conditional Access (or any other frequently used resource) in the “Favorites” area of the left column by selecting “All services” and searching for the word “conditional”, then clicking the star next to the search result
Click New policy and give it a name.
- Let’s include our test user.
- Click Assignments > Users and groups
- Then, on the Include tab, Select Users and groups
- Select ‘test user’
- Then, switch to the Exclude tab and select your admin account
- Click Done when both selections have been made
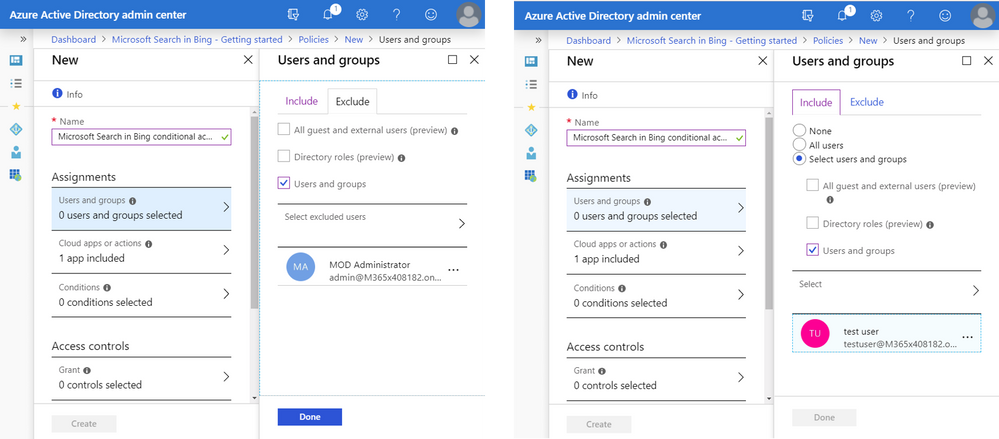
In the screenshot on the right of Figure 5, we’ve chosen to exclude the administrative account from this test policy—you don’t want to lock yourself out if you apply a policy like this to all users! Remember, a policy designed to block access won’t affect anyone who is excluded from the policy.
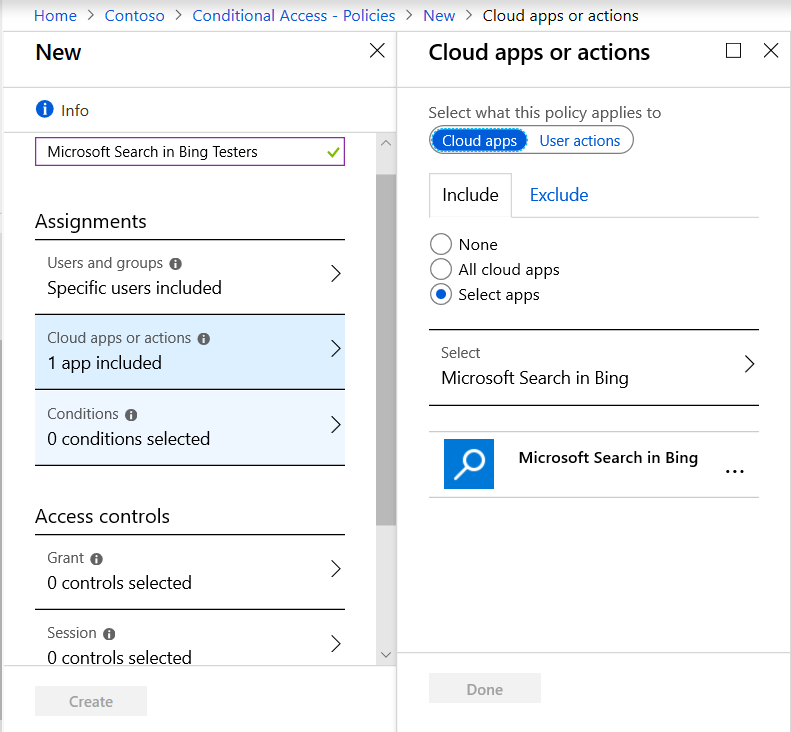
- The next step is to include the app or service we want our conditional access policy to apply to. In this case, it’s Microsoft Search in Bing. Verify that it is included under “Cloud apps or actions.”
You’re almost there! Now that you’ve selected the users who will and won’t be affected, and the app this policy applies to, you just have to tell the policy what to do when it’s in effect. In this case, you want it to “Block.” So, select Block from Access controls > Grant, then click Select.
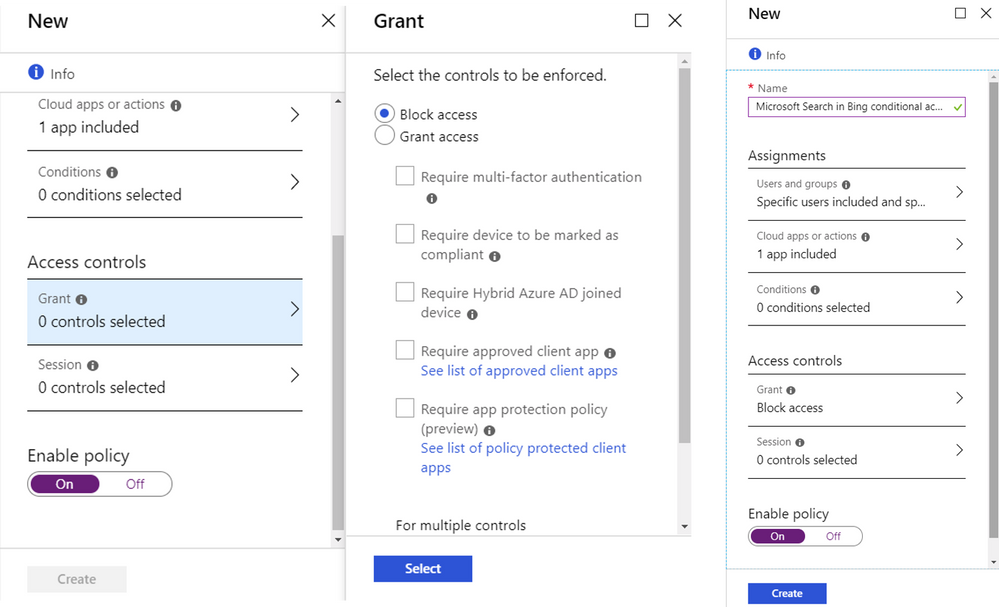
- When all of these steps are completed, click Enable policy ‘on’ and then click Create to create the new policy.
- After a brief validation step, you should see a “Validation Successful” message and the new policy appears under Policies. It’s time to test your new policy!
Test with the “What If” tool
The “What If” tool tests the impact of conditional access on a user when signing in under certain conditions. As the policy you created is designed to block access for “test user”, you start by selecting that user. Then, click “What If” to see what policies, if any, will affect this user.
If you’ve done everything right, you should see something like this:
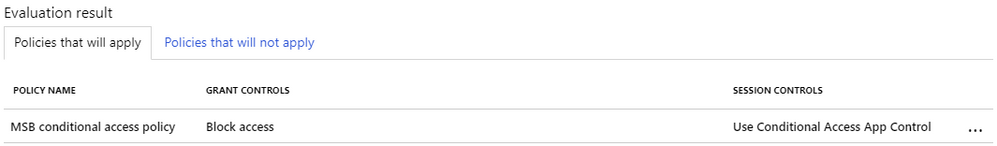
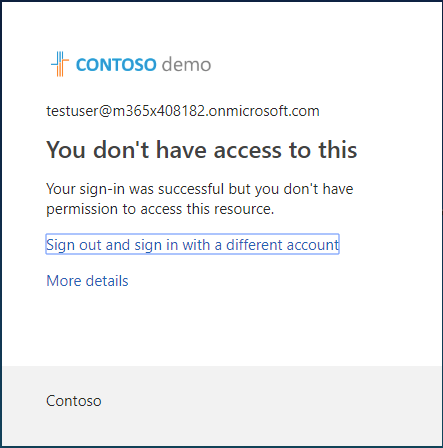
Congratulations! You have successfully enabled conditional access. You can verify this by attempting to access Microsoft Search in Bing with the test user account. You will find that it is indeed blocked from signing in at the Bing sign-in screen. (Regular web searches with Bing still work, however.)
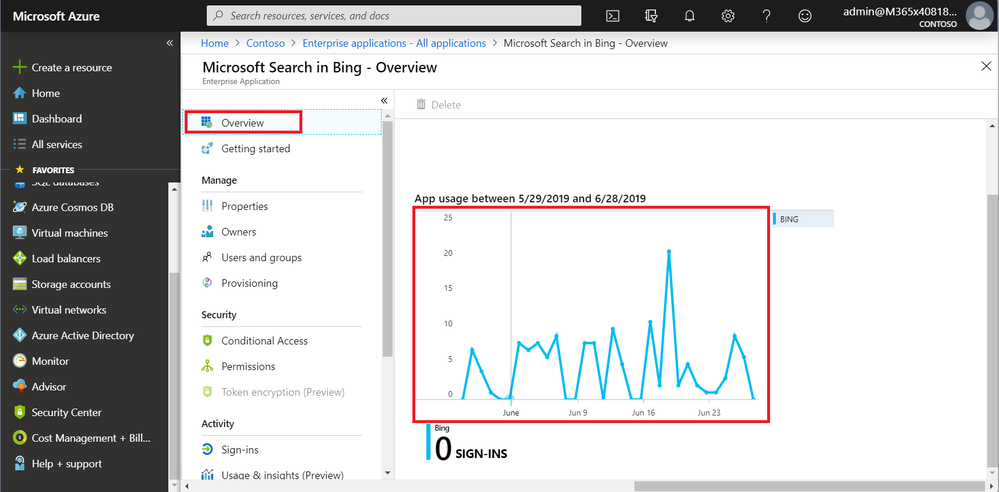
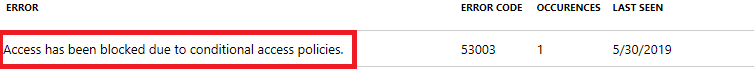
After any sign-in attempt has been made, the event is captured in the Sign-in events log. As an admin, you can access a complete list of sign-in events by clicking on the graph on the main Overview screen.
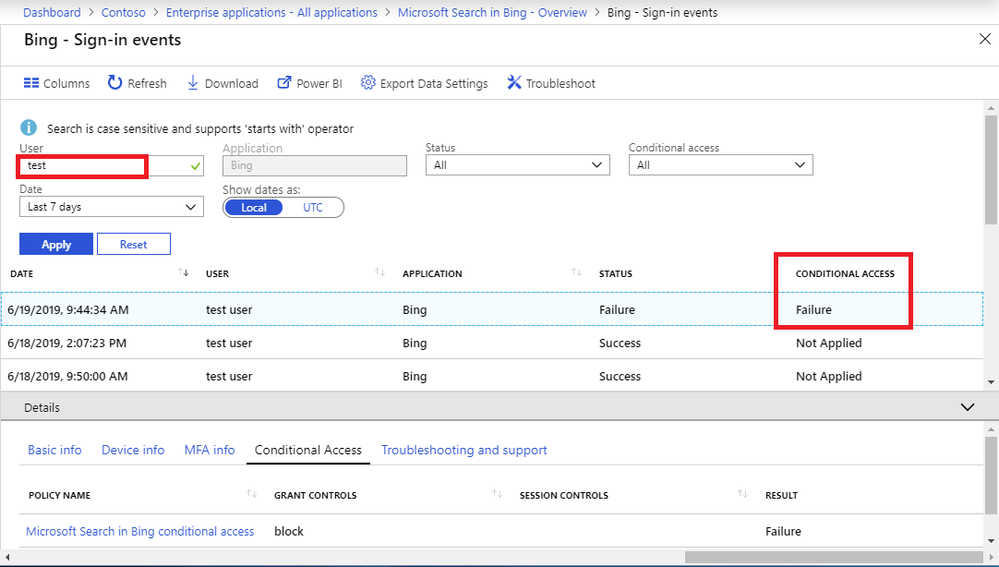
Let’s take a closer look at that ‘Failure’ event:
Deploy the Policy
Now you are ready to setup Conditional Access for actual users in your organization by applying this policy to their account.
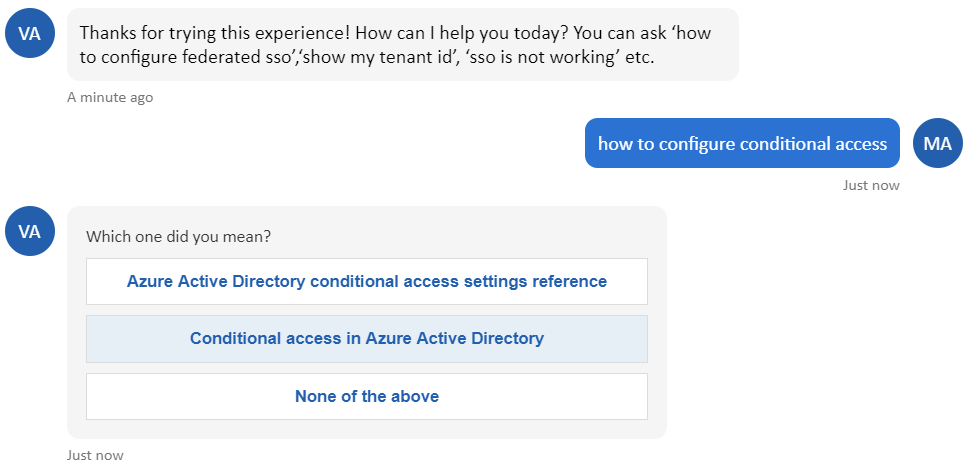
If you run into trouble, try typing a query such as “how to configure conditional access” into the “Virtual assistant” found in the Azure Active Directory admin center under Troubleshooting + Support.
For more information
See https://docs.microsoft.com/azure/active-directory/conditional-access/ for additional details.