This post has been republished via RSS; it originally appeared at: Intune Customer Success articles.
Hi everyone, today we have a post by Intune Support Engineer Mingzhe Li. In this post, Mingzhe takes a look at Deploying Hybrid Azure AD-joined devices by using Intune and Windows Autopilot from an end-user's perspective. This is a must-read if you’re planning to implement this feature.
=====
The purpose of this post is to provide an easy, end-to-end guide on setting up hybrid Azure AD joined devices using Windows Autopilot with Microsoft Intune. When working on this topic as a Support Engineer, many customers ask me for a simple tutorial with as many screenshots as possible. Furthermore, my customers would like to know more about the technical workflow of the enrollment process and what log files to investigate. In response to that, I decided to write this article with the hopes that it will help you too and make getting this setup as easy as possible.
This article will describe the end-user experience during the Autopilot process. It will also explain what IT admins can monitor on the Intune portal to verify the status of the enrollment process.
End-user experience
Now we can power-on our target device and go through the enrollment process step by step. The Autopilot profile will only apply if the device is in ‘out of the box’ state. If the device is already in use and you want to enroll it into Intune with Autopilot, the computer needs to be reset. After you start-up the machine, the OOBE (out of the box experience) phase for the device will start:
Make sure with your network team that the device can find and contact the domain controller and has Internet access.
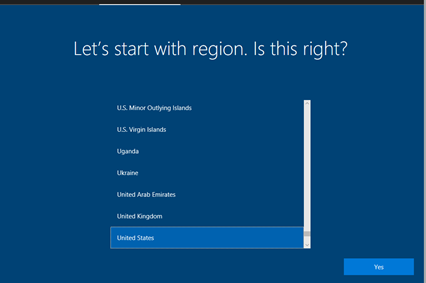
Now follow the instructions until the screen below:
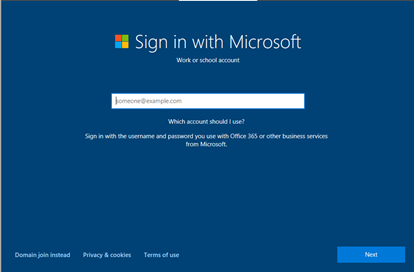
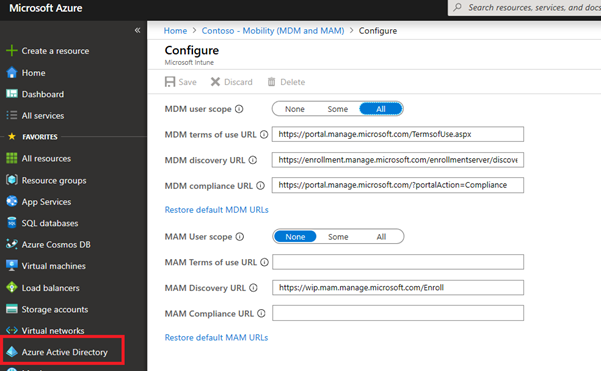
You need to type in an Azure AD account which will enroll the device into Intune. Make sure that the account has a proper Intune license assigned. The account also must be part of the MDM scope in the Auto-enrollment settings:
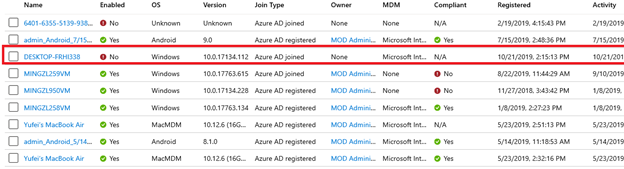
The device will now be prepared and download the Autopilot profile. On the Azure AD portal, we can already see the device name changed from the previous serial number to the device hostname:
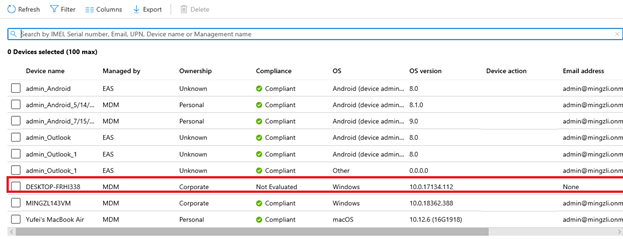
On Intune, we can see that a new device entry appeared:
This means that the device successfully received the Autopilot enrollment profile and the machine is already enrolled into Microsoft Intune. At this point in time, the device is not joined to your local Active Directory domain yet.
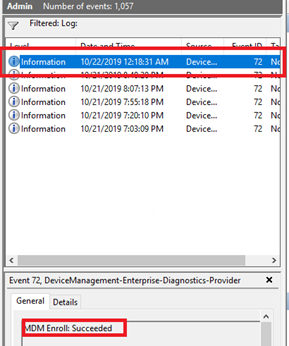
Tip: Press Shift + F10 and run command eventvwr to open Event Viewer. We can check the progress by reviewing the log files:
Application and Services Logs -> Microsoft -> Windows -> DeviceManagement-Enterprise-Diagnostics-Provider -> It includes all log entries regarding Intune MDM events. It should display that MDM enroll is succeeded:
Application and Services Logs -> Microsoft -> Windows -> Provisioning-Diagnostics-Provider -> Autopilot -> This log includes all Autopilot-related log entries.
Troubleshooting Tip:
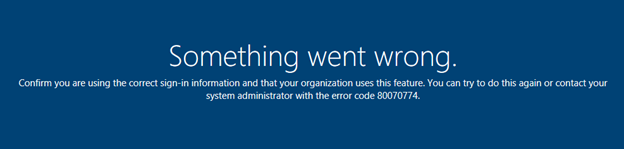
If you see the below error, it means that your device is not able to connect to your Domain Controller:
The error could also mean that the Windows device is not meeting the minimum OS requirements. For Windows Autopilot, the device OS must be on Windows 1809 or higher.
Another possibility to overcome the error is to temporarily deactivate the device-based policies deployed to the Autopilot machines. We made the experience that the error might occur if the deployment of configuration policies failed, e.g. BitLocker-related policies.
You can further refer to https://docs.microsoft.com/en-us/intune/enrollment/troubleshoot-windows-enrollment-errors for more troubleshooting guidance.
This video shows you how you can collect the full set of enrollment logs during OOBE phase:
https://www.youtube.com/watch?v=ry88Vur6dhE&feature=youtu.be
If issues can’t be resolved, we can always try to reset the device by pressing Shift + F10 and then running sysprep /generalize /oobe /reboot.
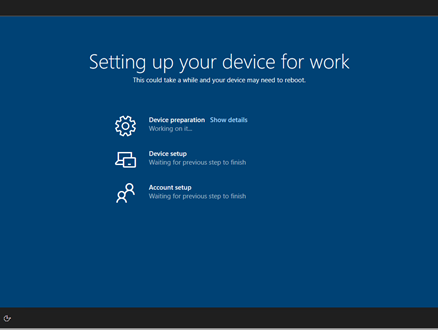
If everything goes smoothly, the device will reboot and the ESP (enrollment status page) will appear:
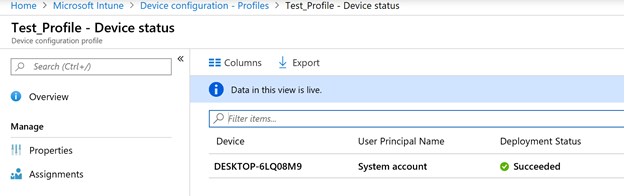
On Intune portal, we can see domain join profile is deployed successfully:
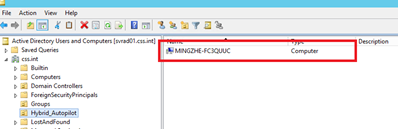
On the Domain Controller within Active Directory Users and Computers, we can see that the device is domain joined now:
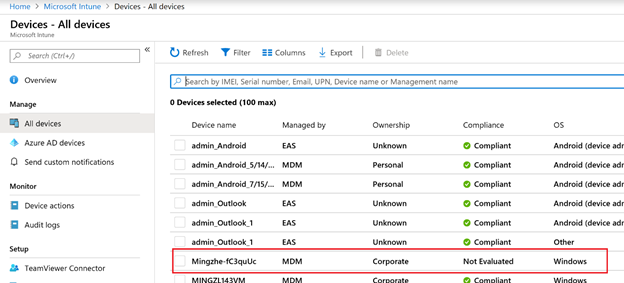
On Intune portal, the device name has now changed to the correct prefix defined in the domain-join profile:
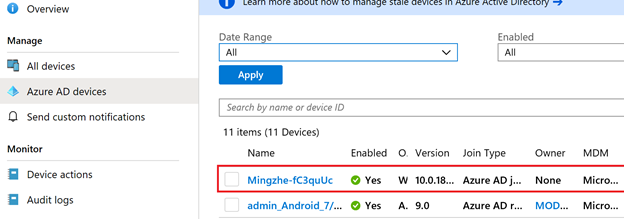
Same happens with the device in Azure AD device list:
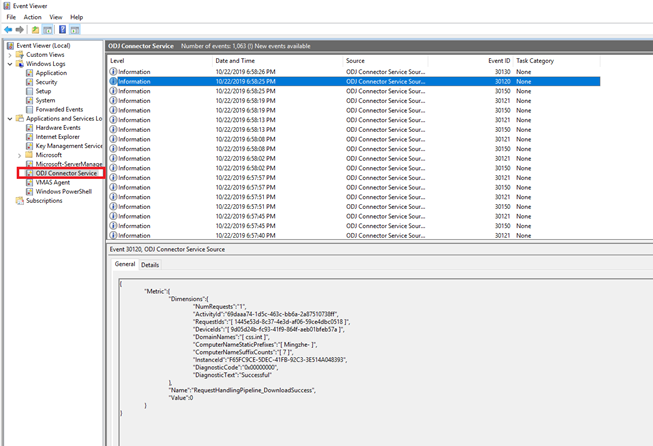
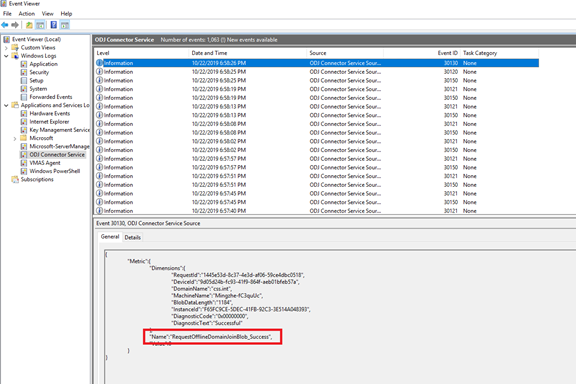
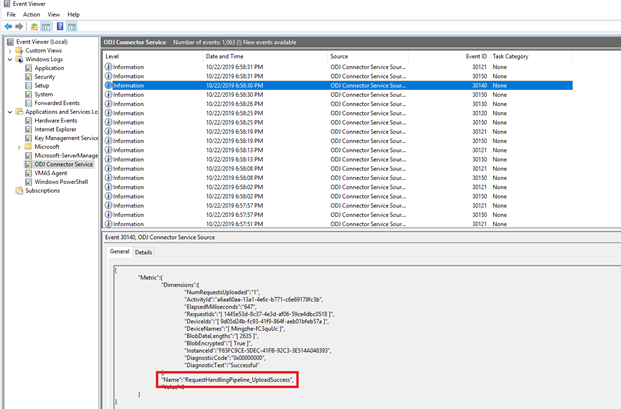
On the Intune Connector server, we can see below entries in the event logs (Applications and Services Logs -> ODJ Connector Service) which indicates that the connector received the domain join information (via blob file) successfully from Intune:
Below log entry indicates that the blob file was processed successfully:
Below entry indicates that the blob information has been sent successfully to the domain controller for domain join:
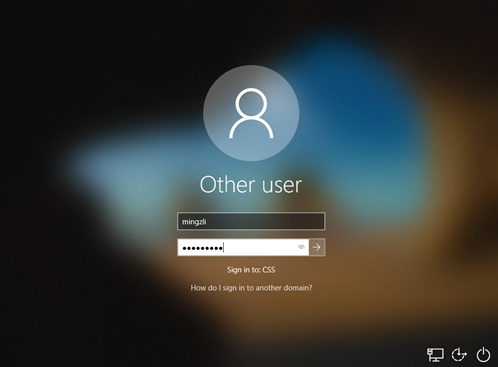
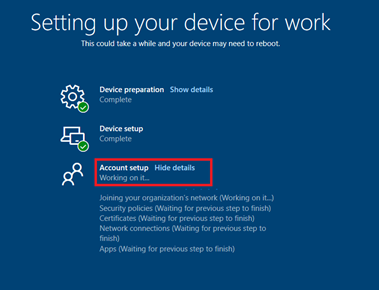
Once device preparation and device setup finishes, we will see below screen asking us to sign-in. Use the same account you used to sign-in before, but this time in domain\username format:
Follow the instructions and wait until the process finishes. Device will now continue with Account setup and perform the hybrid AAD join:
Note that the hybrid join can take up to 40 mins.
Tip: Note that if one of the items (e.g. Security Policies or Certificates) fail to apply, Intune will retry the deployment until it succeeds. This could potentially result to a time-out of the ESP and subsequent policies will not be applied anymore.
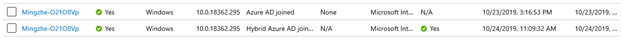
After all the steps are finished, we can see that the device is hybrid Azure AD joined:
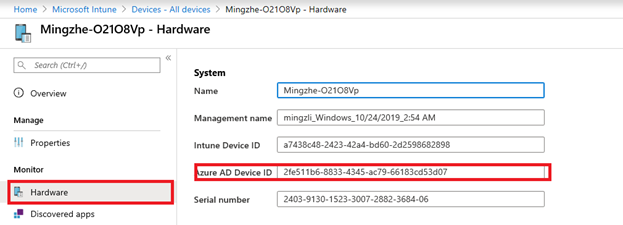
The same device has now two entries in Azure AD which is expected behavior. However, the Intune device is associated with the hybrid joined device in Azure AD. This can be confirmed when we compare the associated Azure AD device ID:
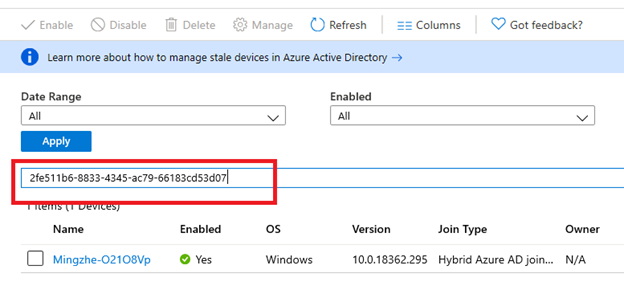
Type in the ID in the Azure AD device list and you will find the hybrid joined device:
Mingzhe Li
Intune Support Engineer

Hi,
We have followed all the steps and it seems that we have everything as shown in your publication, the only issue is that the laptop enrolled for hybrid is stuck in the last part in the account configuration and I wonder if this has something to do, in the ODJ Connector Service I have an event with this message:
{
“Metric”: {
“Dimensions”: {
“InstanceId”: “8B56CD7F-4C33-431A-AEBE-4CD1FE2B9961”,
“DiagnosticCode”: “0x00000000”,
“DiagnosticText”: “Successful”
},
“Name”: “RequestHandlingPipeline_Download_NoWork”,
“Value”: 0
}
}
I suggest asking your question at the source article:
https://techcommunity.microsoft.com/t5/intune-customer-success/end-user-experience-deploy-hybrid-azure-ad-joined-devices-by/ba-p/1133748