Azure App Services has an interesting feature, “Dynamic IP Restriction” which can be used for protection against attacks such as Distributed Denial of Service.
Restrictions can be imposed on the App Service, to deny access based on
- The number of concurrent requests made.
- The number of requests made in certain interval of time.
These settings can be configured either in the application web.config or applicationHost.xdt of the Azure App Service.
The Site Extension “Dynamic IP restriction for App Services” provides an User Interface to update the settings.
Steps to install the site extension:
- Navigate to the “Site Extensions” tab from the Kudu site of the App Service.
- Choose Gallery and search for “DIPR”
- Click on “+” icon to install the extension.
- Restart the App Service post installation of the extension.
The following tags should be added in the <security> tag of the web.config file to setup Dynamic IP restriction
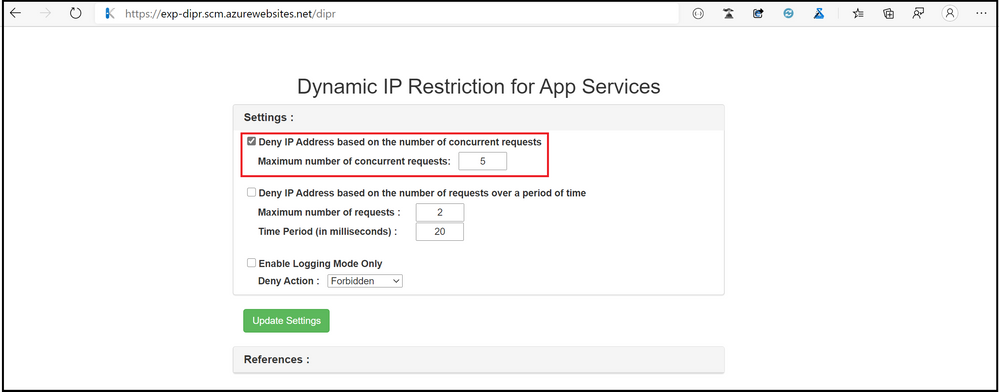
- Based on the number of concurrent requests:
- Configuration:
<system.webServer>
<security>
<dynamicIpSecurity denyAction=”Forbidden”>
<denyByConcurrentRequests enabled=”true” maxConcurrentRequests=”5″ />
</dynamicIpSecurity >
</security>
</system.webServer> - User Interface :
- Configuration:
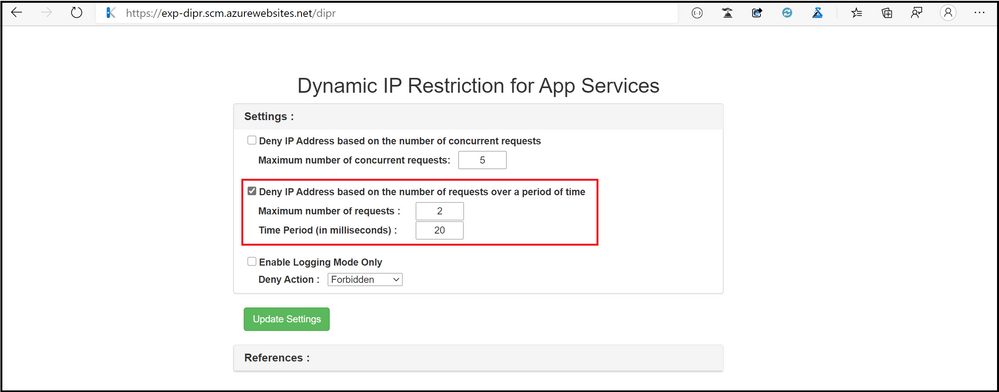
- Based on the number of requests received, in a specific interval of time:
- Configuration:
<system.webServer>
<security>
<dynamicIpSecurity denyAction=”Forbidden”>
<denyByRequestRate enabled=”true” maxRequests=”2″ requestIntervalInMilliseconds=”200″/>
</dynamicIpSecurity >
</security>
</system.webServer>
- User Interface :
- Configuration:
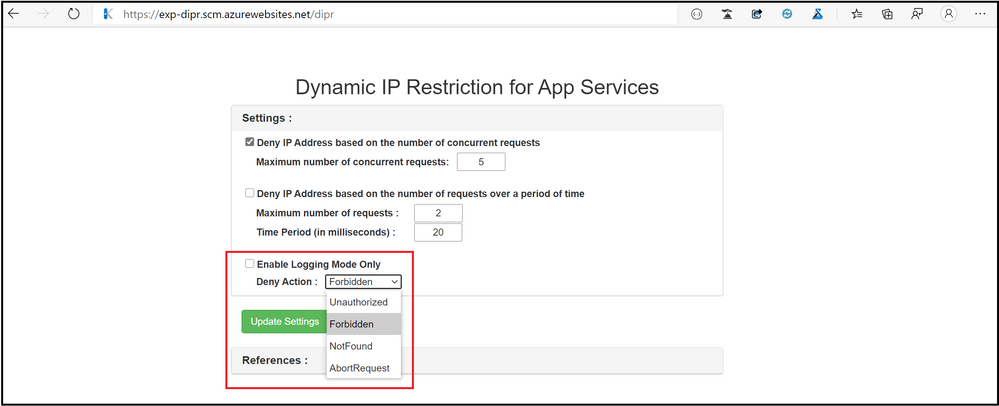
The error returned when the access to the App Service is restricted can be customized using the denyAction attribute of the dynamicIpSecurity element.
The following values can be set:
- AbortRequest : returns HTTP status code 0
- Unauthorized : returns HTTP status code 401
- Forbidden : returns HTTP status code 403 (default setting)
- NotFound : returns HTTP status code 404
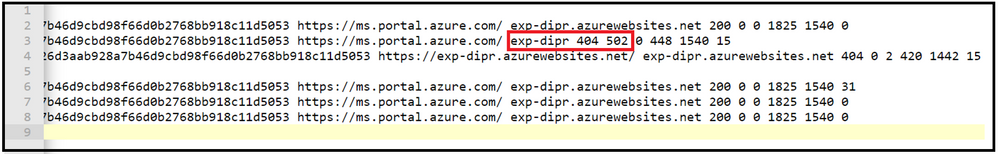
Please note that the sub-status code for the request will be 502 if the request goes through Dynamic IP restrictions.
Example :
<security>
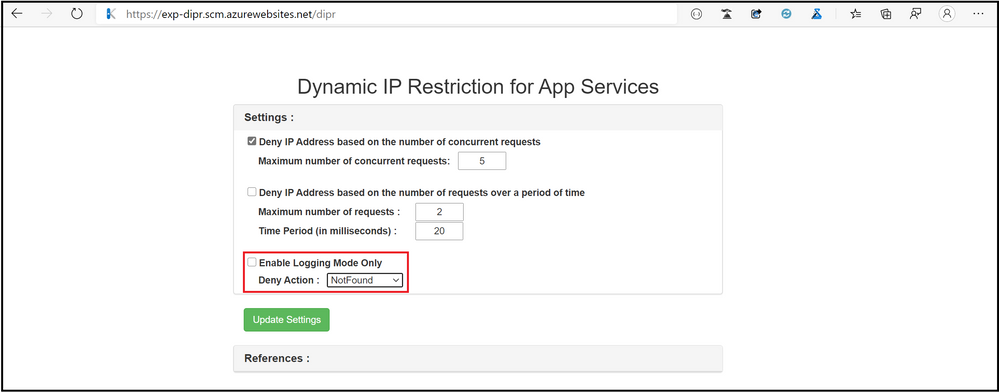
<dynamicIpSecurity denyAction=”NotFound”>
<denyByRequestRate enabled=”true” maxRequests=”2″ requestIntervalInMilliseconds=”20″/>
</dynamicIpSecurity >
</security>
</system.webServer>
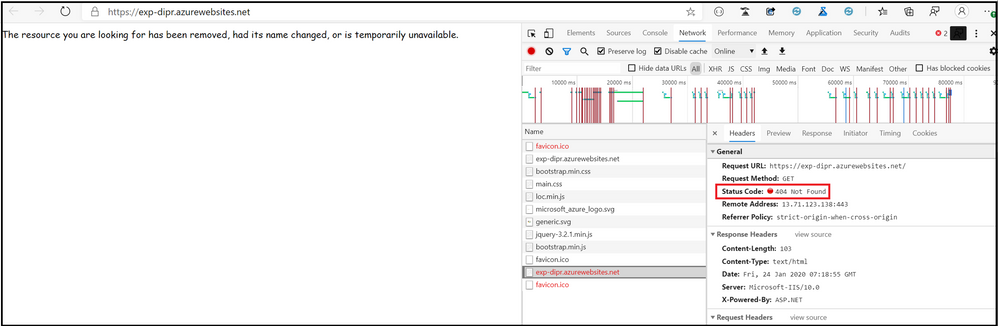
When the above snippet is used, and the App Service receives more than 2 requests from the same IP address in an interval of 20 milliseconds, we receive the response HTTP 404 “Not found”
From Webserver Logs, we can see that the sub-status code is 502
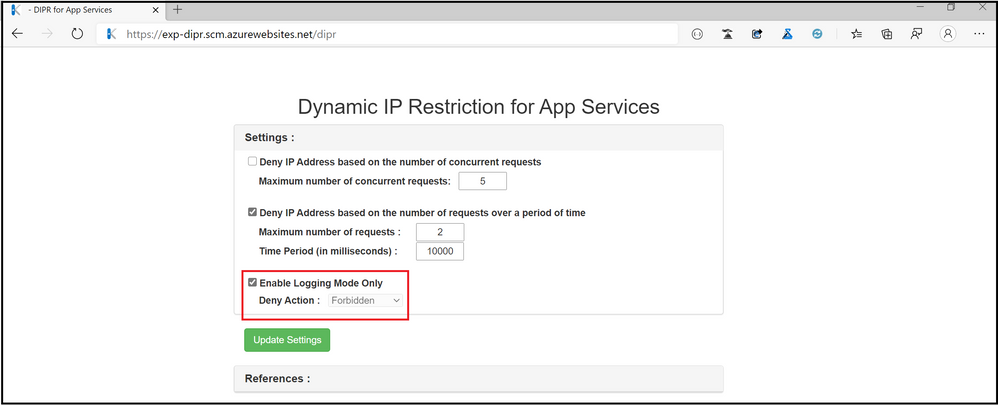
It is also possible to just monitor the request without actually performing the action on the request. To achieve this set enableLoggingOnlyMode to True , in dynamicIpSecurity element.
<security>
<dynamicIpSecurity enableLoggingOnlyMode=”true” >
<denyByRequestRate enabled=”true” maxRequests=”2″ requestIntervalInMilliseconds=”10000″/>
</dynamicIpSecurity >
</security>
</system.webServer>
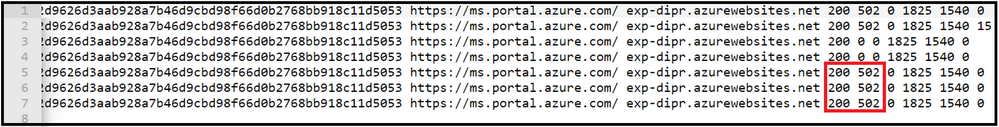
We observe that the status and sub-status code for the requests as HTTP 200.502
Note:
- The Site Extension considers the Dynamic IP Restrictions configured in web.config file and applicationHost.xdt file.
- The changes made through the User Interface are reflected in applicationHost.xdt file only and would require a restart of the App Service.