This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
An increasing number of companies are opting to run their open source workloads on Azure, and thus ensuring the security of these workloads has been a top priority for the Azure Database for MySQL team. In our efforts to continuously enhance the security commitments we’ve made to our customers, we’re proud to announce several connectivity and network security improvements to the Azure Database for MySQL service.
General Availability of Private Link for Azure Database for MySQL
In January, we announced public preview of Private Link, and our customers provided great feedback. Today, we are happy to announce that Private Link for Azure Database for MySQL is now in general availability.
Private Link enables users to have private connectivity from a Microsoft Azure Virtual Network to Azure Database for MySQL. This feature creates a private endpoint that maps a private IP address from the Virtual Network to an Azure Database for MySQL instance.
From a security perspective, Private Link provides data exfiltration protection on the login path to Azure Database for MySQL. Additionally, it eliminates the need to add IP addresses to the firewall or VNet service endpoints rules on Azure Database for MySQL.
Private Link is built on best-of-class Software Defined Networking (SDN) functionality delivered by the Azure Networking team. Clients can connect to the private endpoint from the same Virtual Network, a peered Virtual Networking same region, or via VNet-to-VNet peering across regions. Additionally, clients can connect from on-premises implementations using ExpressRoute, private peering, or VPN tunneling.
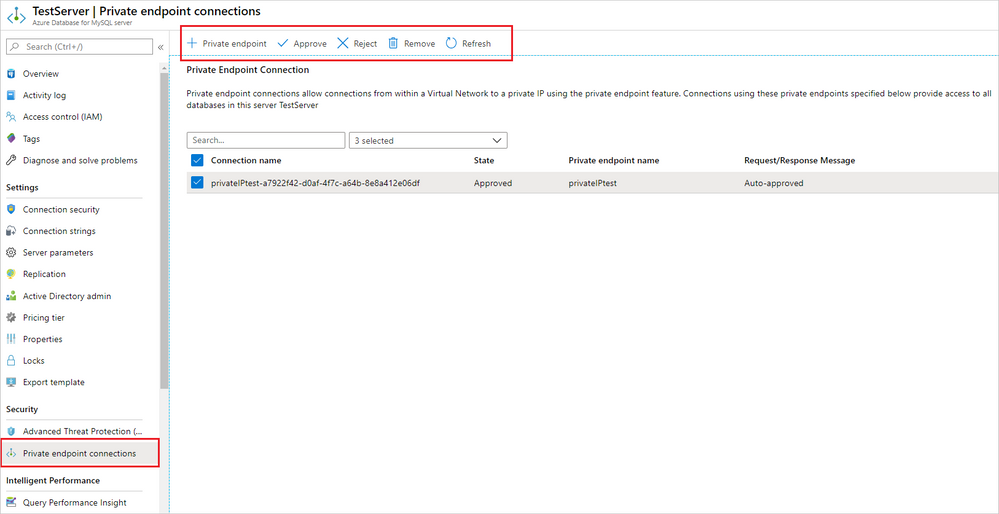
With general availability, we’ve incorporated a manual approval workflow for Private Link. Using this functionality, Private Link connection requests appear in Azure Database for MySQL as Pending. The DBA must manually approve the request before connections can be established. In manual cases, service consumers can also specify a message with the request to provide additional context to the service provider. For each Pending request, the service provider can select from the following options for all Private Endpoint connections: Approve, Reject, or Remove.
Security and governance enhancements
We’ve also made multiple improvements that allow customers to control connectivity settings for Azure Database for MySQL. These setting are at the server level, i.e., they apply to all databases created on a server. Note that when these settings are applied, they take effect immediately and may result in connection loss for clients if they do not meet the requirements for each setting.
- Ability to deny public network access
- Governance capability by enforcing Azure policies
- Advanced Threat Protection and Recommendations available in Gov clouds
Ability to allow or deny public network access
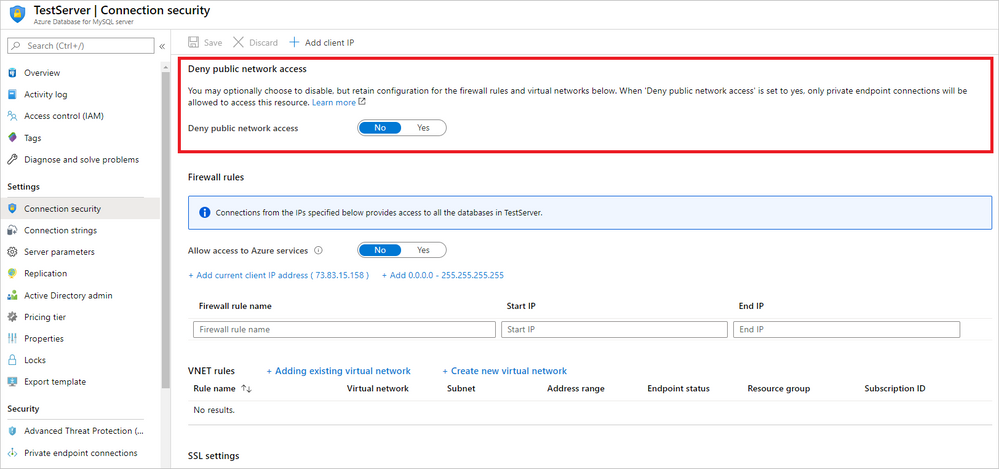
While Private Link allows access only via private endpoint, customers today can also use the public endpoints via firewall rules and VNet service endpoints for scenarios in which a mix of private and public connectivity is required. However, for customers who only want to rely on private endpoints for accessing their Azure Database for MySQL, we have provided the ability to allow or deny public network access.
When this setting is configured as ‘NO’, clients can connect to Azure Database for MySQL based on firewall or VNet service endpoint settings. When this setting is configured as ‘YES’, only connections via private endpoints are allowed to Azure Database for MySQL. Additionally, with the value set as ‘YES’, customers cannot add or update existing firewall rules or VNet service endpoint rules.
Note: This setting does not impact the SSL and TLS configurations for the Azure Database for MySQL instance.
Governance capability by enforcing Azure policies
Azure Policy is an Azure service that used to create, assign, and manage policies. These policies enforce different rules and effects on resources to ensure that they stay compliant with corporate standards and service level agreements. Azure Policy meets this need by evaluating resources for non-compliance with assigned policies, at the same time ensuring that all data stored by Azure Policy is encrypted at rest. We are glad to announce the integration of Azure Database for MySQL with Azure Policy to enforce these compliance requirements at scale.
We’ve created an Azure Policy GitHub repository that contains quick-start samples from the community. For more information about using these sample policies, see the article here.
Availability of Advanced Threat Protection (ATP) and Recommendation in US Government cloud
Advanced Threat Protection for Azure Database for MySQL offers a new layer of security that provides security alerts on anomalous activities, enabling customers to detect and respond to potential threats as they occur. Users receive an alert upon suspicious database activities, potential vulnerabilities, and anomalous database access and queries patterns.
The Recommendations feature gives daily insights about the database server to help customers optimize performance. These recommendations are tightly integrated with Azure Advisor to provide best practices directly within the Azure portal. Azure Advisors is a personalized cloud consultant that helps customers follow guidelines to optimize their Azure deployments.
We are happy to announce that customers in US Gov clouds can now leverage these platform capabilities to secure and optimize their database workloads.
Next steps
We hope that these improvements provide our customers with more options for securing connections to Azure Database for MySQL and meeting their organizations’ compliance requirements.
Be sure to try out this new functionality today, and send your questions and feedback to us here. We look forward to hearing from you!