This post has been republished via RSS; it originally appeared at: Healthcare and Life Sciences Blog articles.
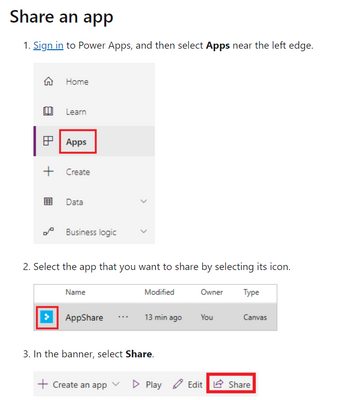
Providing access to a canvas application built on Power Apps is actually very easily done. Simply share the application to a security group, and all of those group members will have access to it.
https://docs.microsoft.com/en-us/powerapps/maker/canvas-apps/share-app
We can also leverage other components of the Microsoft cloud including the Power Platform itself to enable self-servicing of access along with workflows, and simple Forms based requests.
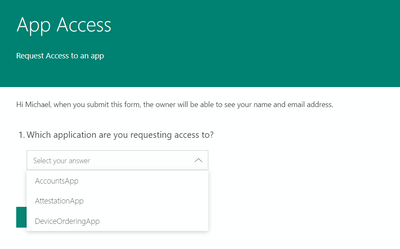
First, we can build a simple Microsoft Form that requires people to sign in and authenticate to the Form, and from there select the application they wish to access.
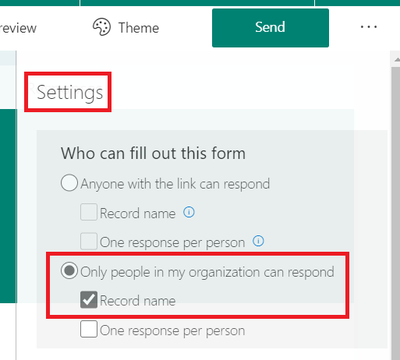
One key setting for this Form is requiring people to authenticate when accessing the Form. This ensures we can get the person’s identity to later add to an Azure AD security group.
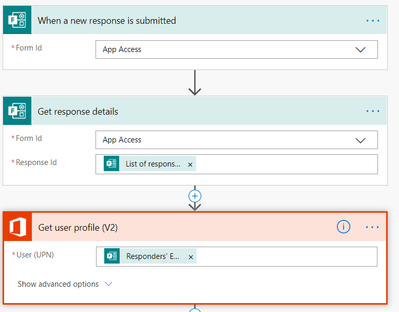
We can then use this Form response to kick off a Flow within Power Automate.
We can leverage the trigger for “When a new response is submitted” to gather information on the person submitting the response and to get the details on the app they are requesting access to.
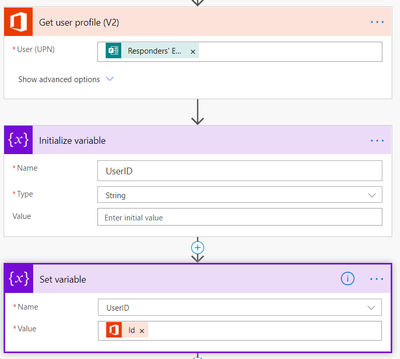
Using the “Get user profile” step allows us to translate the email address into a UPN to then translate the UPN into a GUID which is used to add the identity object to a security group.
The translation of converting the responder’s email to the GUID is handled with variables
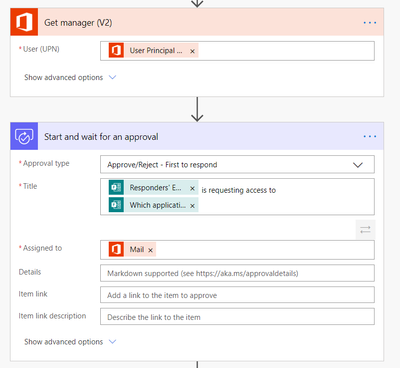
With that information we can now introduce additional workflow components such as Manager’s approvals or even automatic approvals
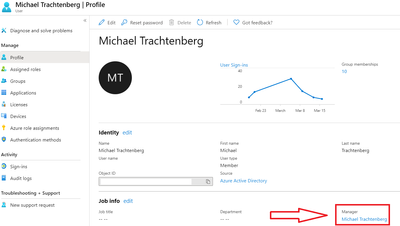
When using the manager approval process, the manager must be set within the Azure AD environment, otherwise you can use a generic or dedicated email address or person for approvals
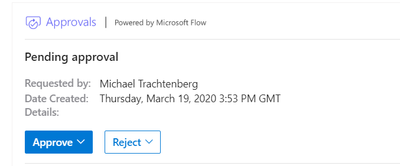
When the form is submitted the manager will then be prompted to grant access via a card in Teams or Outlook if desired
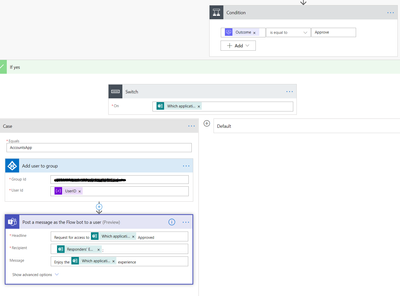
Assuming the request is approved, the rest of the Flow will review which application the responder is requesting access to and will add them to a correlating and designated AD group. That same AD group already should have the Power App shared with it.
Items to note here:
- The Azure AD connector is being used here to add the user to a security group
- The group ID requires a GUID that resides in Azure AD for that security group. This can be looked up earlier in the Flow and stored in a variable for more dynamic use
- The UserID we converted earlier is being used here
- A switch is being used to accommodate different applications that would then use different GUIDs and correlating security groups for each case
- Confirmation is being sent out regarding approved access
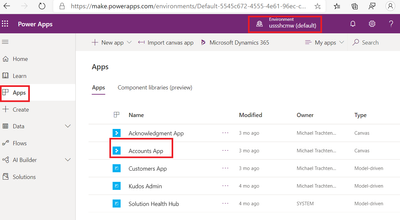
Once the workflow completes, and again assuming the Canvas App is already shared with that same security group, the responder will then see the application appear in their list of Apps in the respective Power Apps environment
It typically takes about 10-15 minutes for the application to show up following completion of the Power Automate Flow.
There is one additional consideration that should be reviewed when dealing with model driven Power apps. Model driven apps may also have a team and lower level security groups associated with them via a Dynamics Security group, especially if you want to have multiple roles associated with model driven apps. Think app data reader and app data editor.
For information on how to leverage the same Azure AD security group within the Dynamics security groups, see detailed information here: https://docs.microsoft.com/en-us/power-platform/admin/manage-teams This entire same process still applies, but be sure to link the Azure security group with the Dynamics Security group.