The aim of the workbook is to consolidate many data sources into one report.
I’ve called the workbook Azure Security Reporting (but you can use whatever name makes sense to you, when you import it).
There is a lot of great data surfaced by Azure Resource Graph (ARG) and Log Analytics, I have laid this out into four Tabs on the workbook.
This download isn’t from the main Sentinel Github for Workbooks as it covers many technologies. Please download the Workbook and read the import instructions (in the readme) on my Github
Data sources:
- SecurityAlert – The table in Log Analytics (used by ASC and Azure Sentinel)
- Securityresources – Azure Resource Graph
- Advisorresources – Azure Resource Graph
The four tabs explained, Alerts, Compliance, Qualys and Advisor
Note: ARG uses data from api calls, so there is no timefilter, therefore you may see more data in these reports than in the filtered views provided by ASC or Azure Advisor for example.
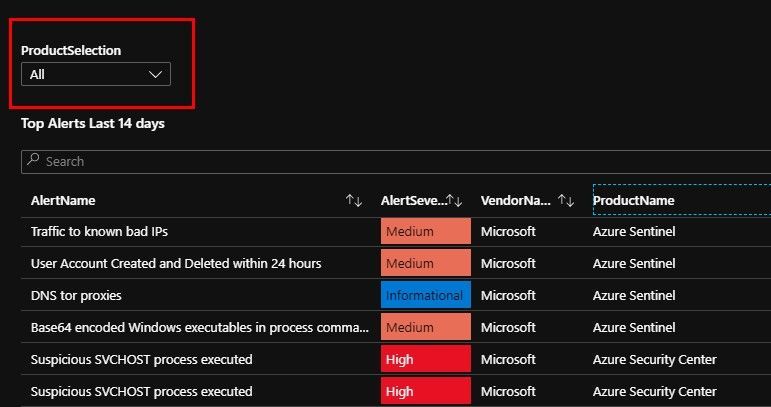
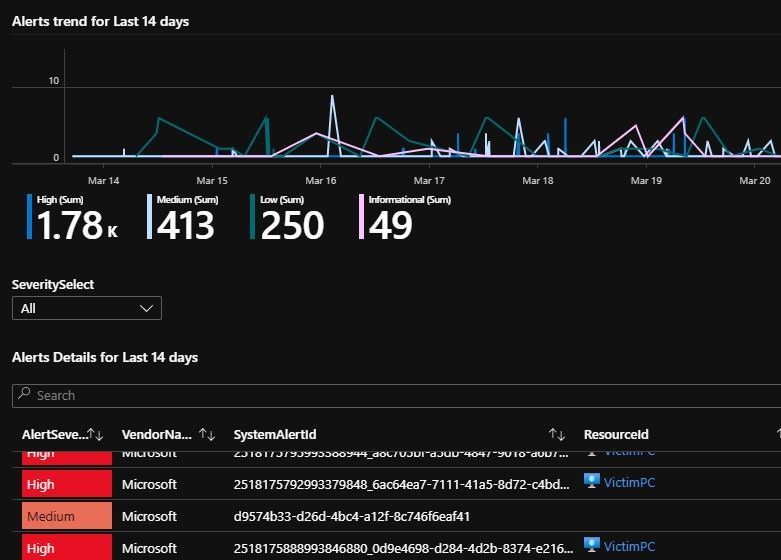
Tab1: Alerts and Incidents
Today this covers the Security Alerts you usually see in ASC and Sentinel (more on Incidents in a follow-up post).
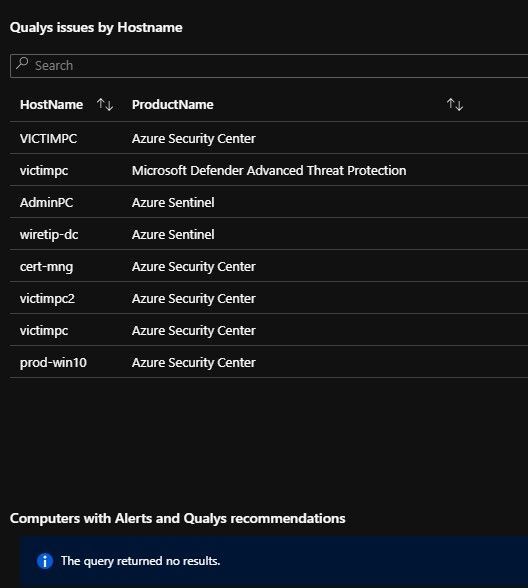
Please note the [Product selection] filter drop-down (this is useful on this page to filter by the Security Products you have, and it’s also used again in the “Qualys issues by Hostname” report.
If you are unsure select ALL
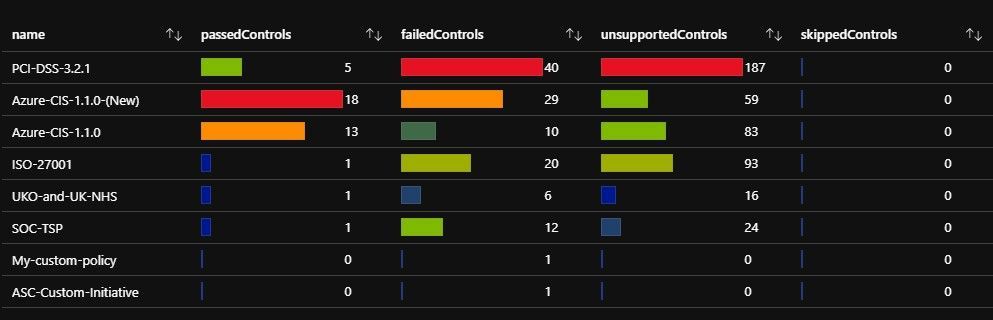
Tab2: Compliance
This tab relies on data from Azure Security Center from the Standard Tier, so you will need ASC Standard for this Tab to produce any data.
https://docs.microsoft.com/en-us/azure/security-center/security-center-compliance-dashboard
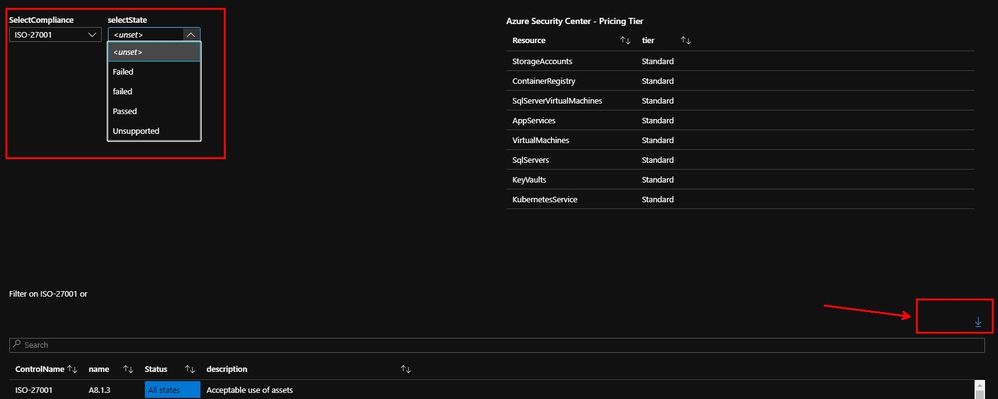
The above shows the compliance controls and assessments. You can select a filter for the compliance (all the supported or custom ones) e.g. ISO27001 and the state e.g. Failed.
This isn’t something you can do in the ASC portal, and I added a free form search bar, so you can use that to find other details.
You can also export this data to Excel (see the arrow in the bottom right corner of image 2).
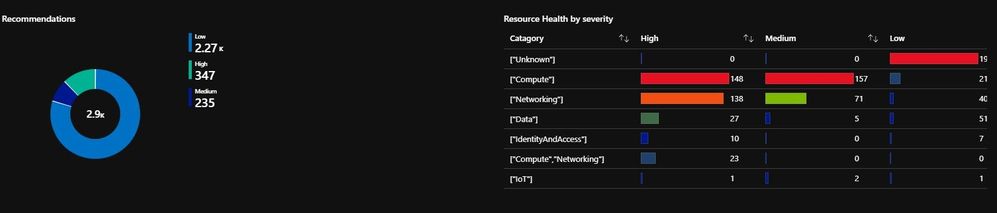
I have also re-created the recommendations view you see in ASC (as closely as possible, I have Networking in the list as an addition).
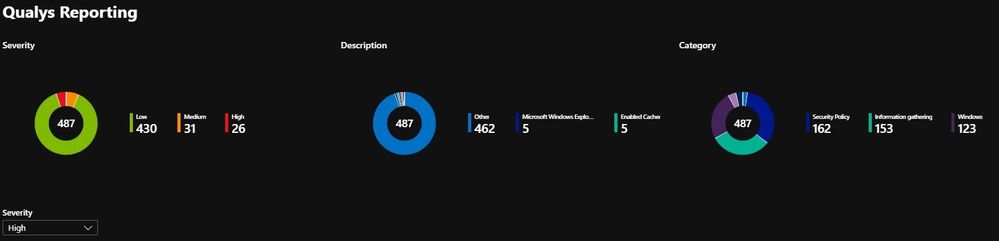
Tab3: Qualys
This tab relies on data from Azure Security Center from the Standard Tier.
The vulnerability scanner included with Azure Security Center is powered by Qualys. Qualys’s scanner is the leading tool for real-time identification of vulnerabilities in your Azure Virtual Machines. It’s only available to users on the standard pricing tier. You don’t need a Qualys license or even a Qualys account – everything’s handled seamlessly inside Security Center.
Source: https://docs.microsoft.com/en-us/azure/security-center/built-in-vulnerability-assessment
This part of the report starts of with a summary for Severity, Description and Category. Again, I have provided a drop-down filter, on Severity – would Category be a useful filter as well?
The final two reports check for Qualys recommendations that relate to a host (Computer), I then merge the prior two outputs to show “Computers that have Alert AND a Qualys recommendation” Thanks for the idea @Ofer!
This correlates a Computer to a Security tool like Azure Security Center or Azure Sentinel (or any you have in your list), where we also have a Qualys recommendation.
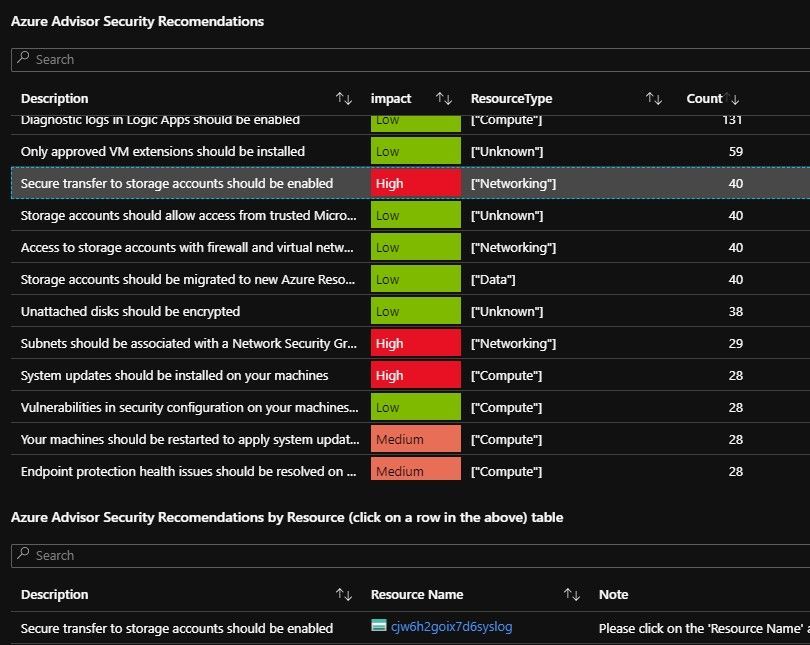
Tab4: Advisor
Azure Advisor is often overlooked data, especially the cost saving recommendations! Azure Advisor now offers (or includes) Security recommendations
Quickly and easily optimize your Azure deployments. Azure Advisor analyzes your configurations and usage telemetry and offers personalized, actionable recommendations to help you optimize your Azure resources for high availability, security, operational excellence, performance, and cost.
Source: https://azure.microsoft.com/en-us/services/advisor/ and https://docs.microsoft.com/en-us/azure/advisor/advisor-security-recommendations
The first set of reports are the ones you see in Azure Advisor, but you can scroll down for the Security recommendations section.
Summary: I hope you find this Workbook useful to detect Security information and to consolidate various sources in one place.
Feedback is very welcome (and your ideas) and I have plans to add more capabilities in the future, especially more correlation between the various data sources.
Thanks to Alp Babayigit for the initial idea and use case for this Workbook.
Thanks Clive